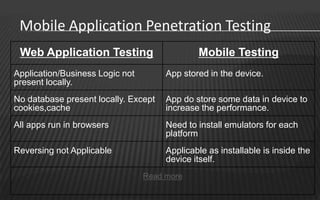
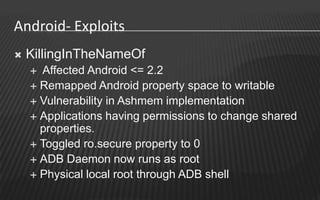
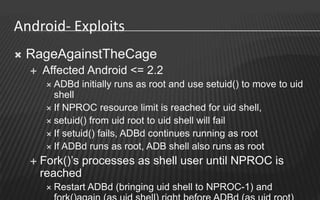
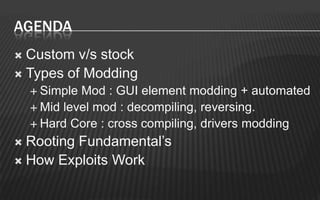
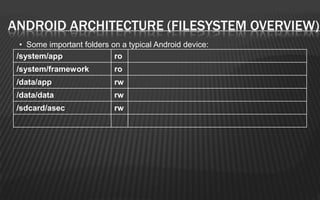
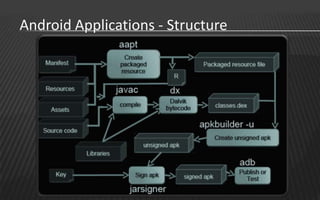
This document provides an overview of a two-day training on Android hacking and security. Day 1 covers Android architecture basics, development, and penetration testing fundamentals. Topics include the operating system, file system, security model, application components, and setting up a penetration testing lab. Day 2 covers more advanced topics like malware analysis, common exploits, custom ROM development, and forensics. The document outlines the agenda and key learning points for each topic.









![Android Applications – Building a sample app
[THE COMPONENTS]
• Activities • Responds to broadcast intents
• UI component for one focused task. • Must be declared in manifest/code
• Usually a single screen in your app.
• Stack-based lifecycle • Content Providers
• Manages Persistent Data
• Services • Publishes it to other apps
• Long-lived worker code. No UI.
• Can be connected to using Binder. • Shared Preferences
• Persistent data stored as name-value
• Intents pairs
• Mechanism for IPC.
• Defined using an Action/data pair • Uses-Permissions
• Describes permissions used by your app
• Intent Filters
• Describes what intents a comonent can • Permissions
handle • Restricts access to your components
• Registers activities/services/receivers.](https://image.slidesharecdn.com/androidvillagenullcon2012-120223044213-phpapp01/85/Android-village-nullcon-2012-15-320.jpg)
![Android Applications – Building a sample app
[GUI BUILDING]
• Layouts are defined in XML (similar to Swing)
• In Android, we implement the Activity interface in Java.
• We need to overwrite a single function, i.e. onCreate()
• XML layouts are later expanded into Java to generate a UI.
• This is done using setContentView(Reference.to.the.XML.file)
• Any controls defined in your XML layouts can be referred to in Java by their ids
using the findViewById() function.
• For each view, a set of event listeners and responders can be defined.](https://image.slidesharecdn.com/androidvillagenullcon2012-120223044213-phpapp01/85/Android-village-nullcon-2012-16-320.jpg)
![Android Applications – Building a sample app
[COMMON ERRORS]
• Build path error.
• AAPT unable to parse
• Invalid Imports
• Component unimplemented in manifest
• Attempting to access without taking the required permissions
• Expired debug certificate](https://image.slidesharecdn.com/androidvillagenullcon2012-120223044213-phpapp01/85/Android-village-nullcon-2012-17-320.jpg)