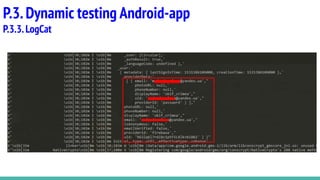
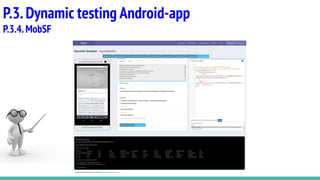
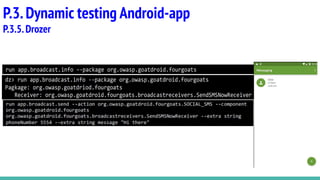
This document provides an overview of methodology and tools for testing the security of Android applications. It discusses static testing tools like MobSF, AndroBugs, QARK and VCG scanner that can analyze Android app code without executing the app. It also covers dynamic testing tools like BurpSuite, Inspeckage, LogCat, MobSF and Drozer that allow analyzing an app's behavior while it is executing. The document provides descriptions and links for each tool to help understand their capabilities and how they can be used for Android pentesting.