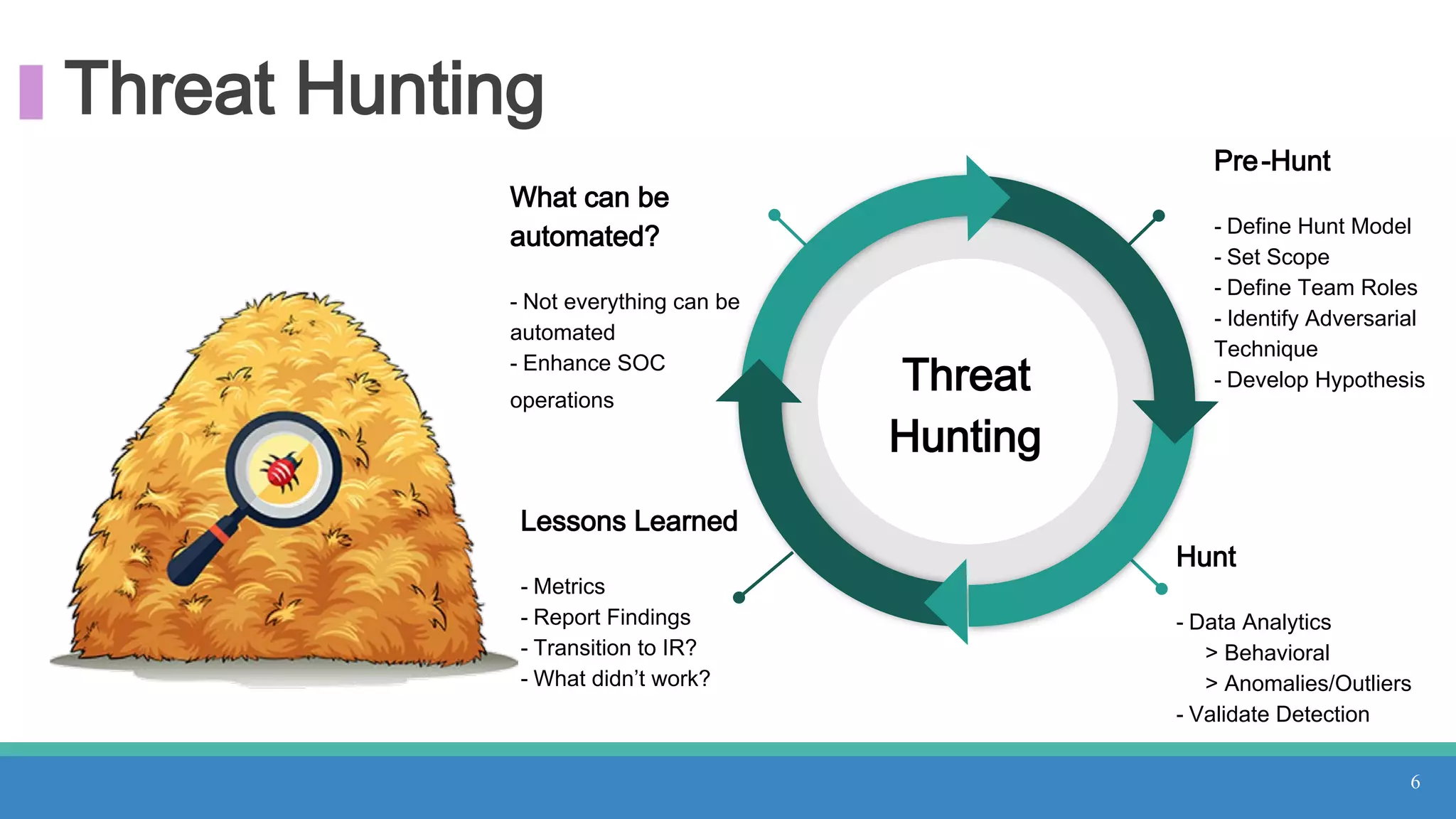
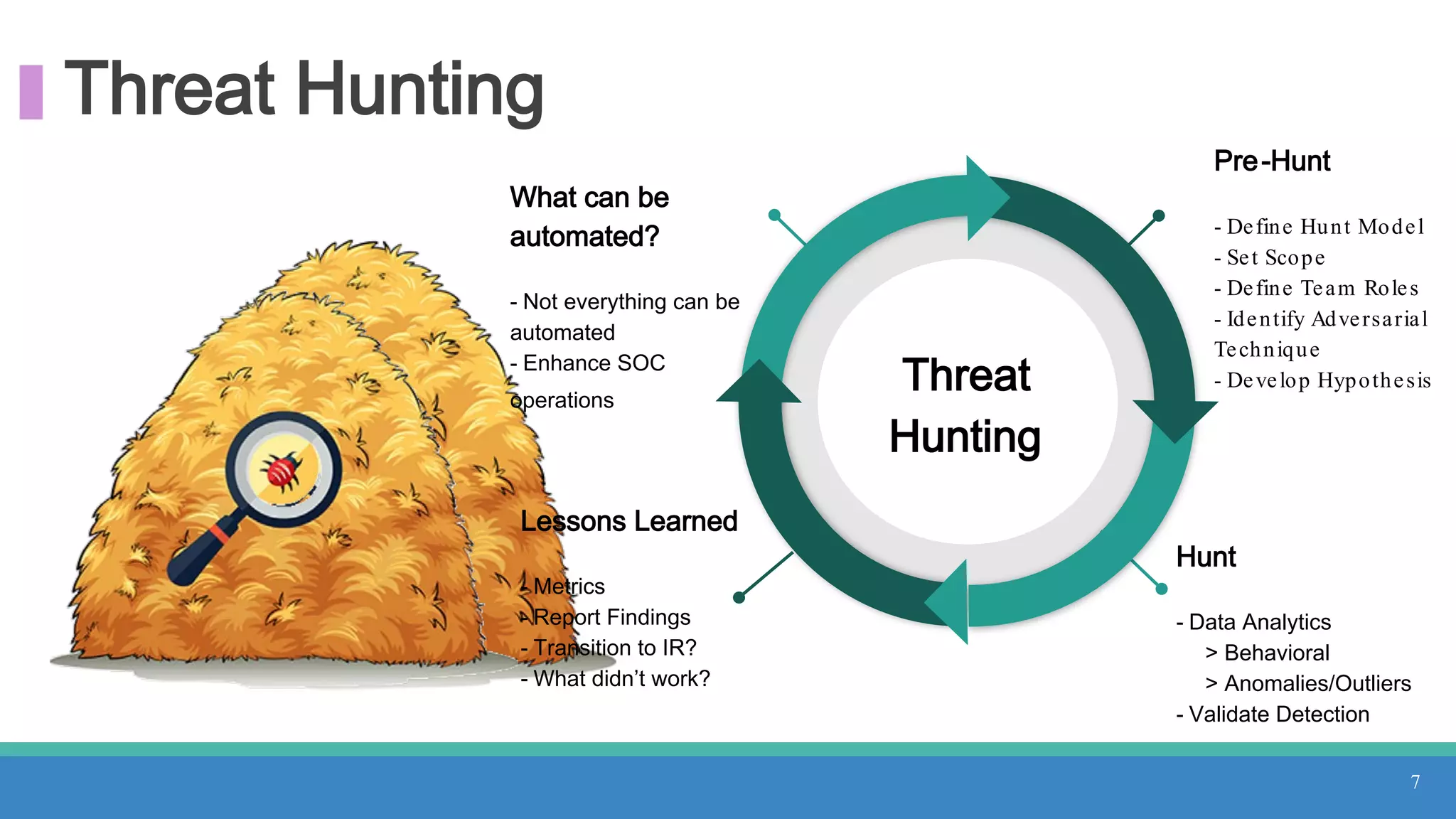
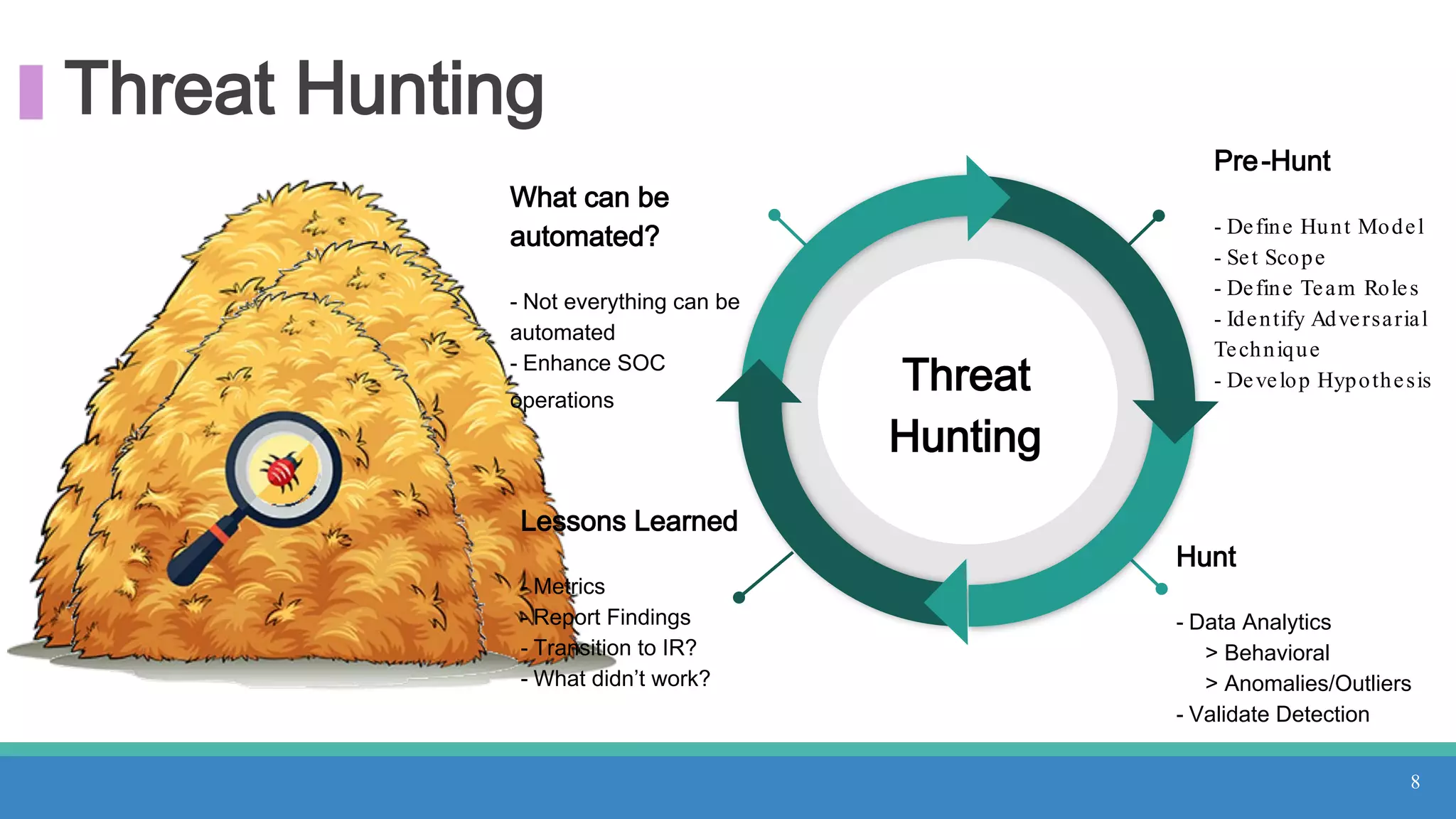
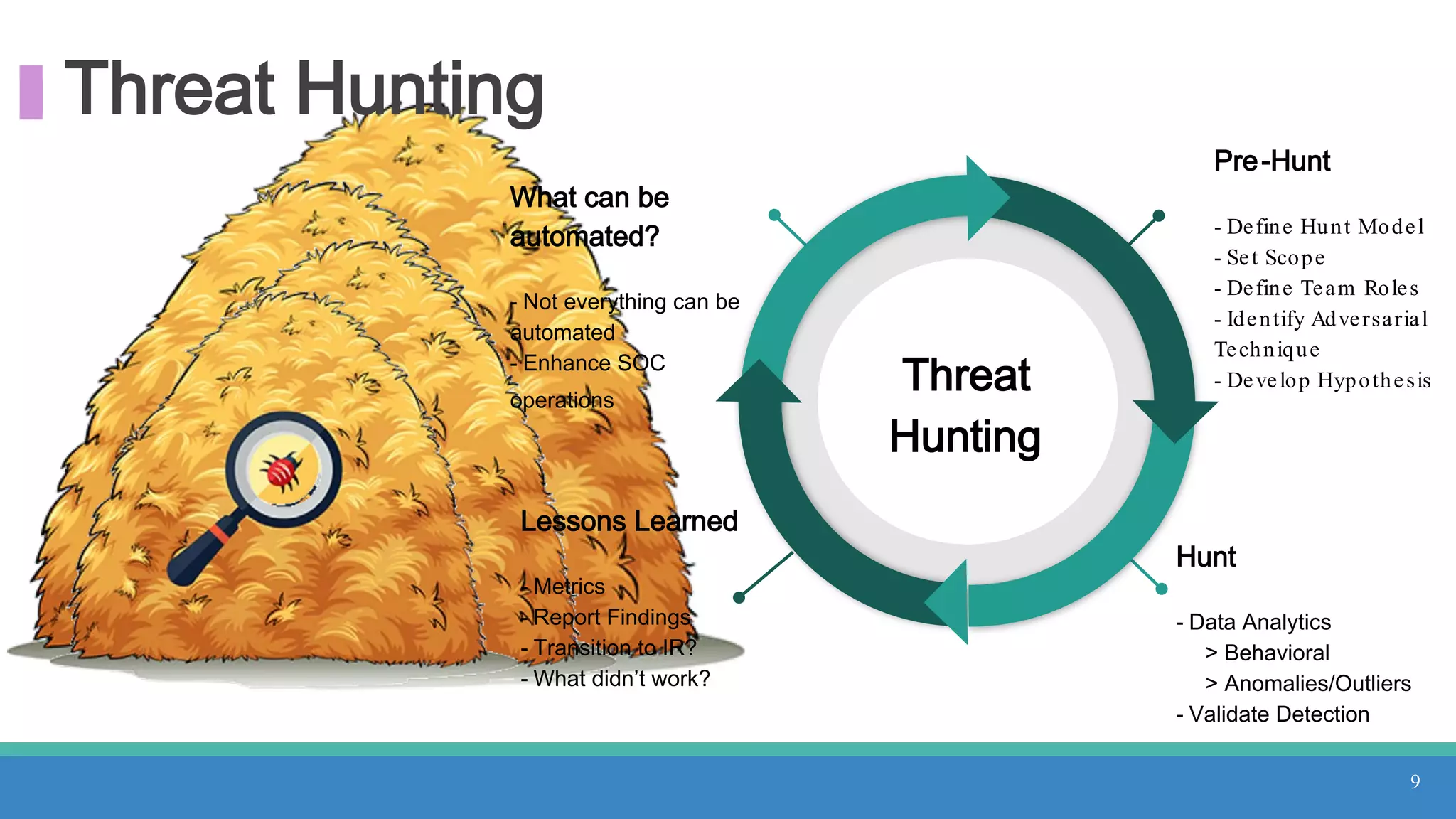
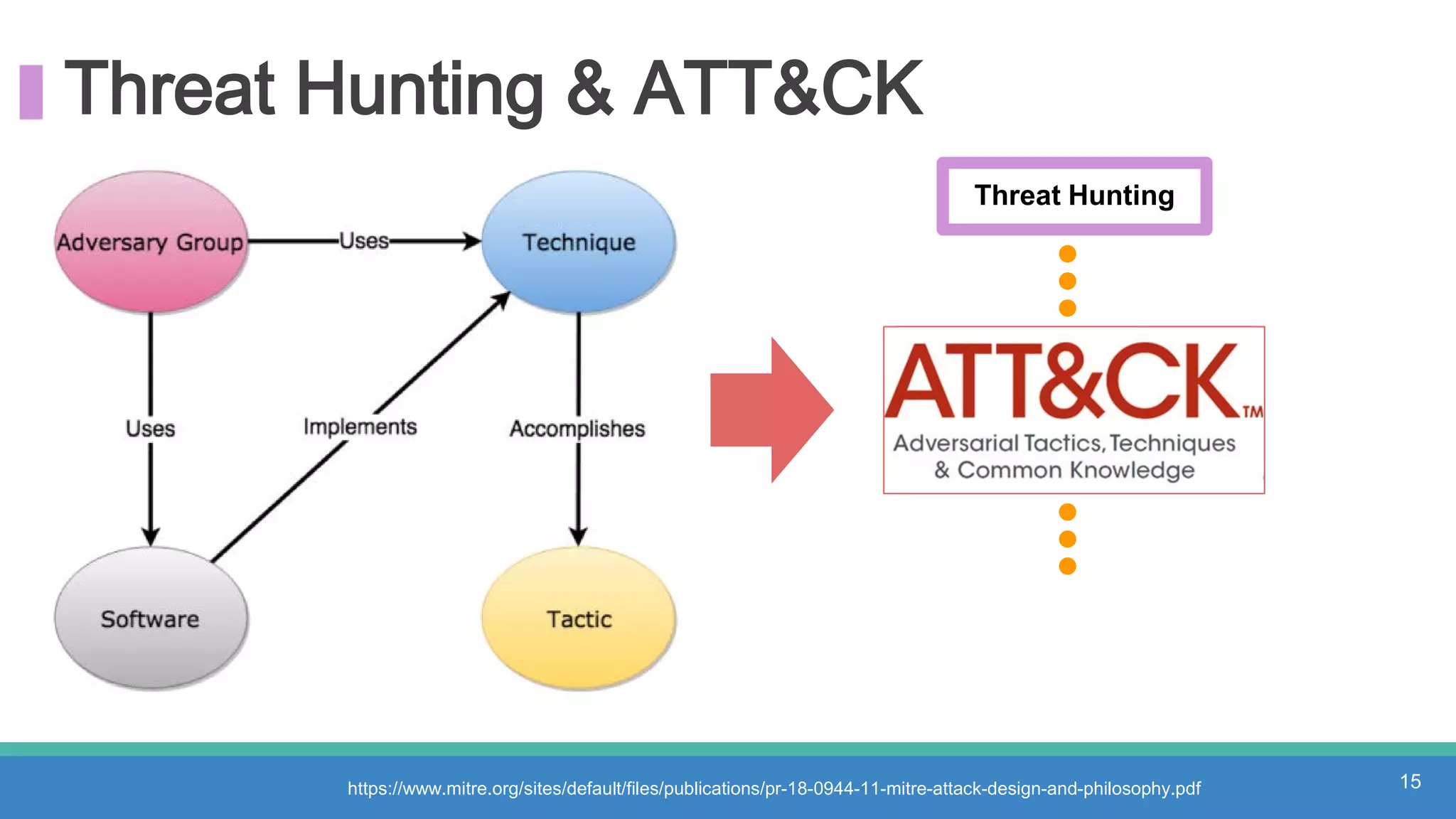
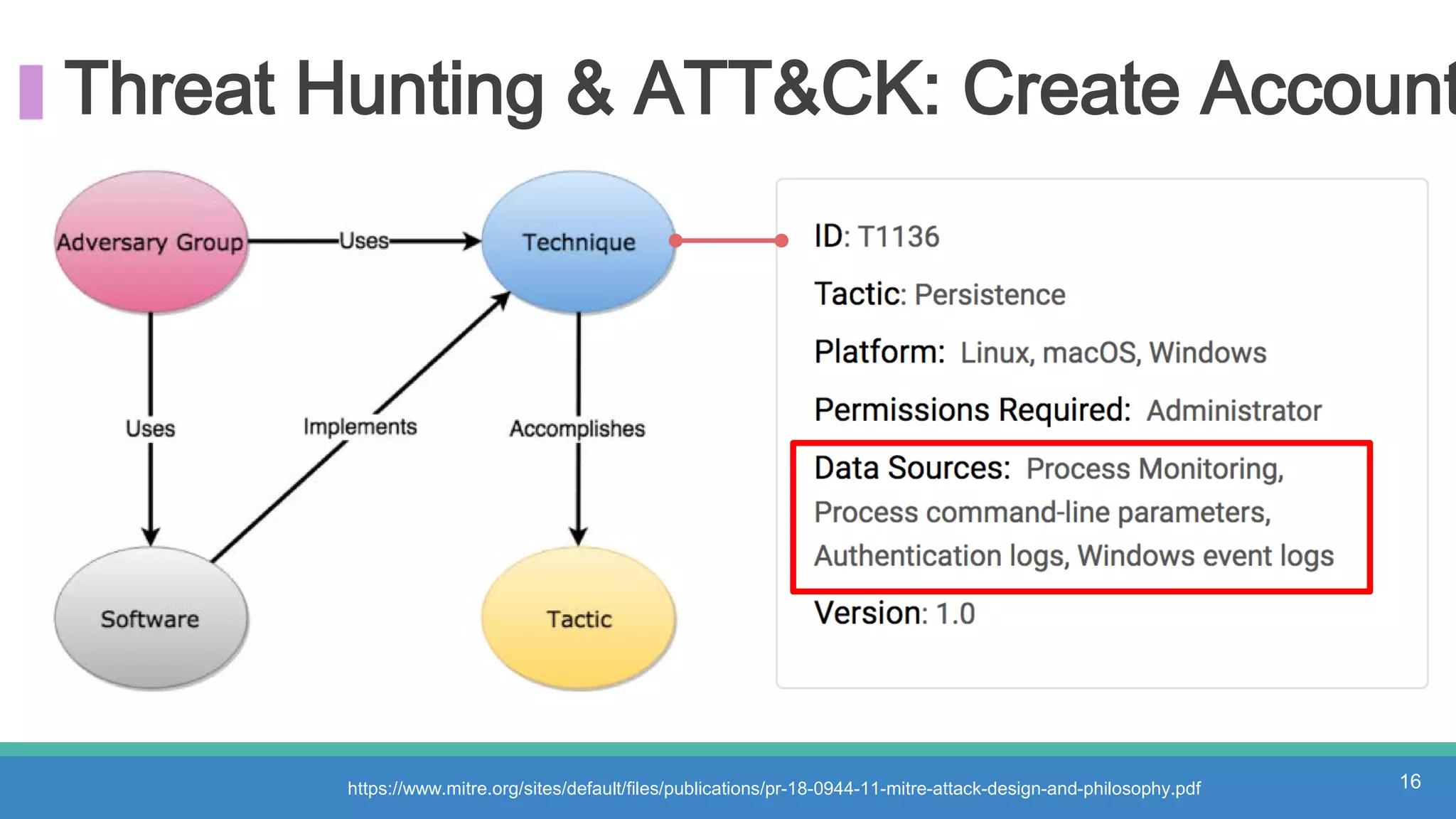
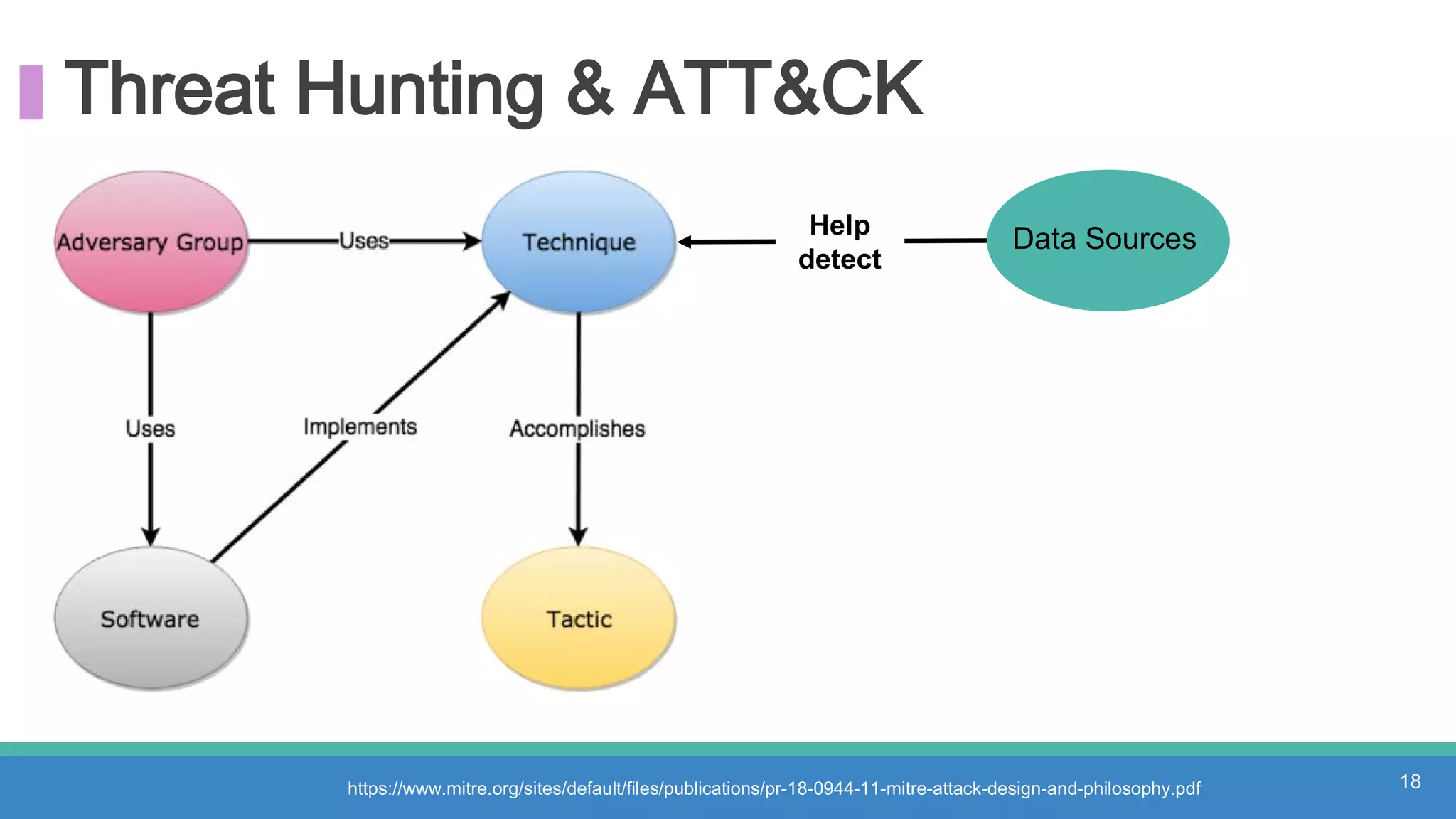
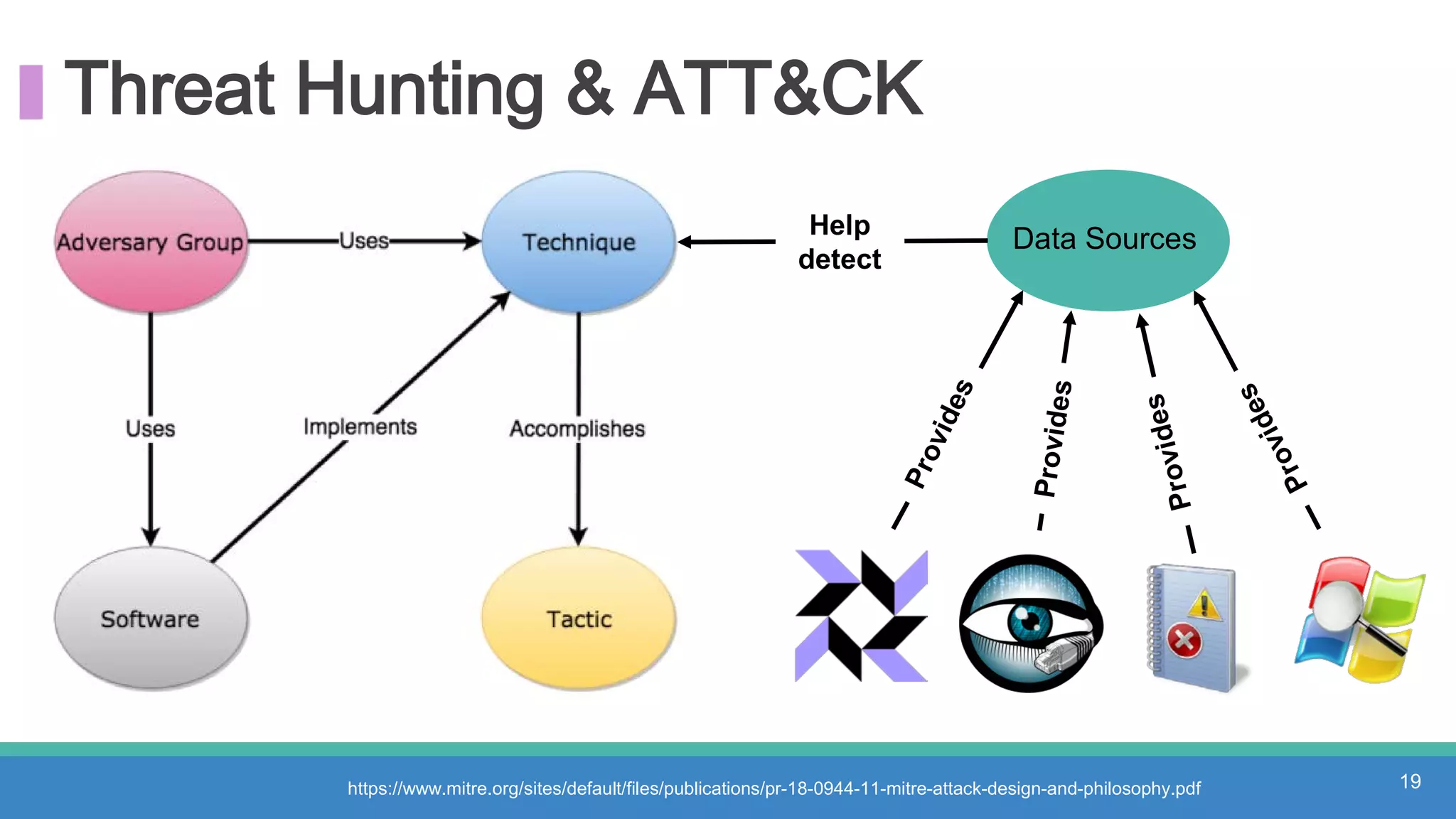
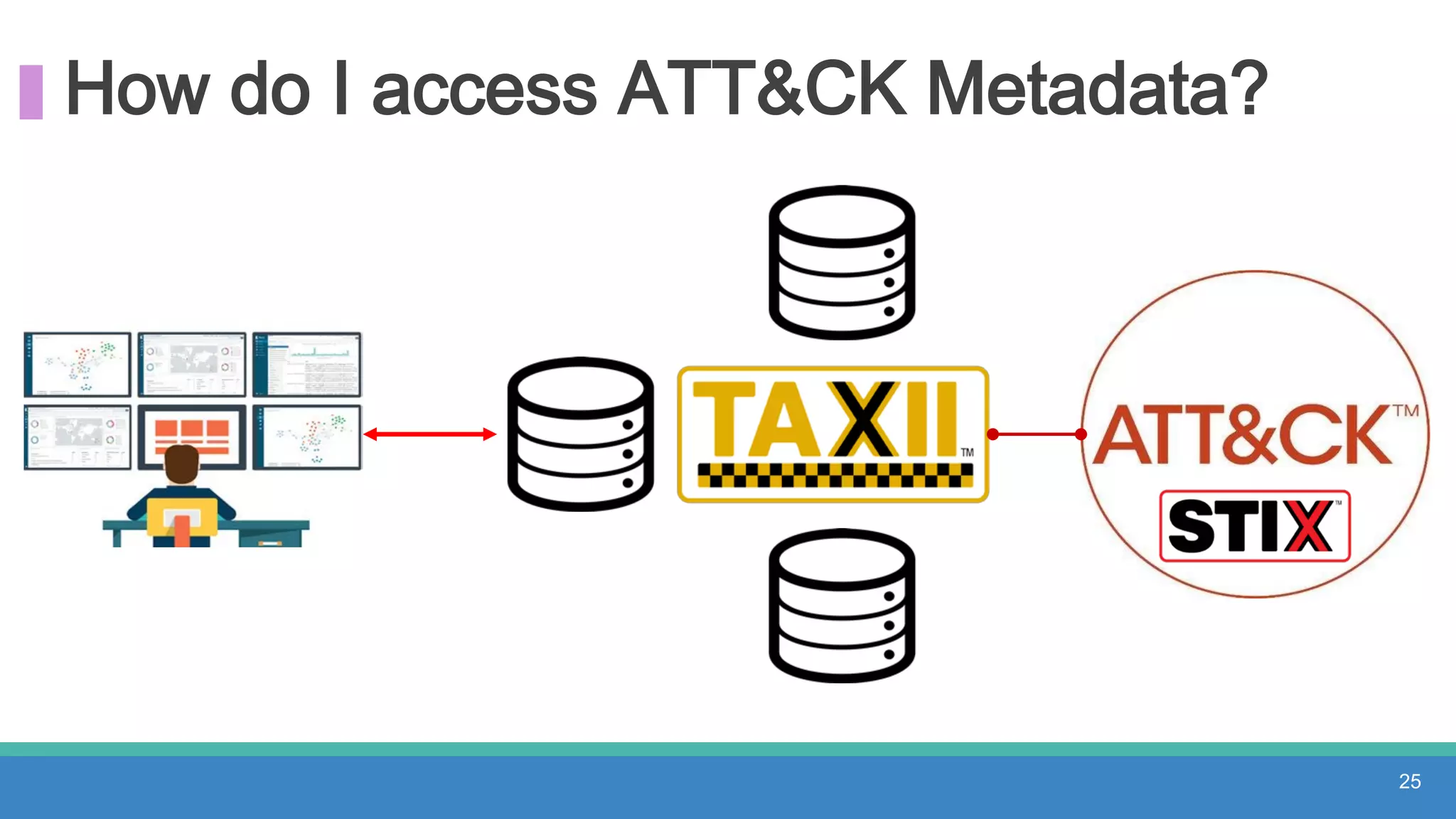
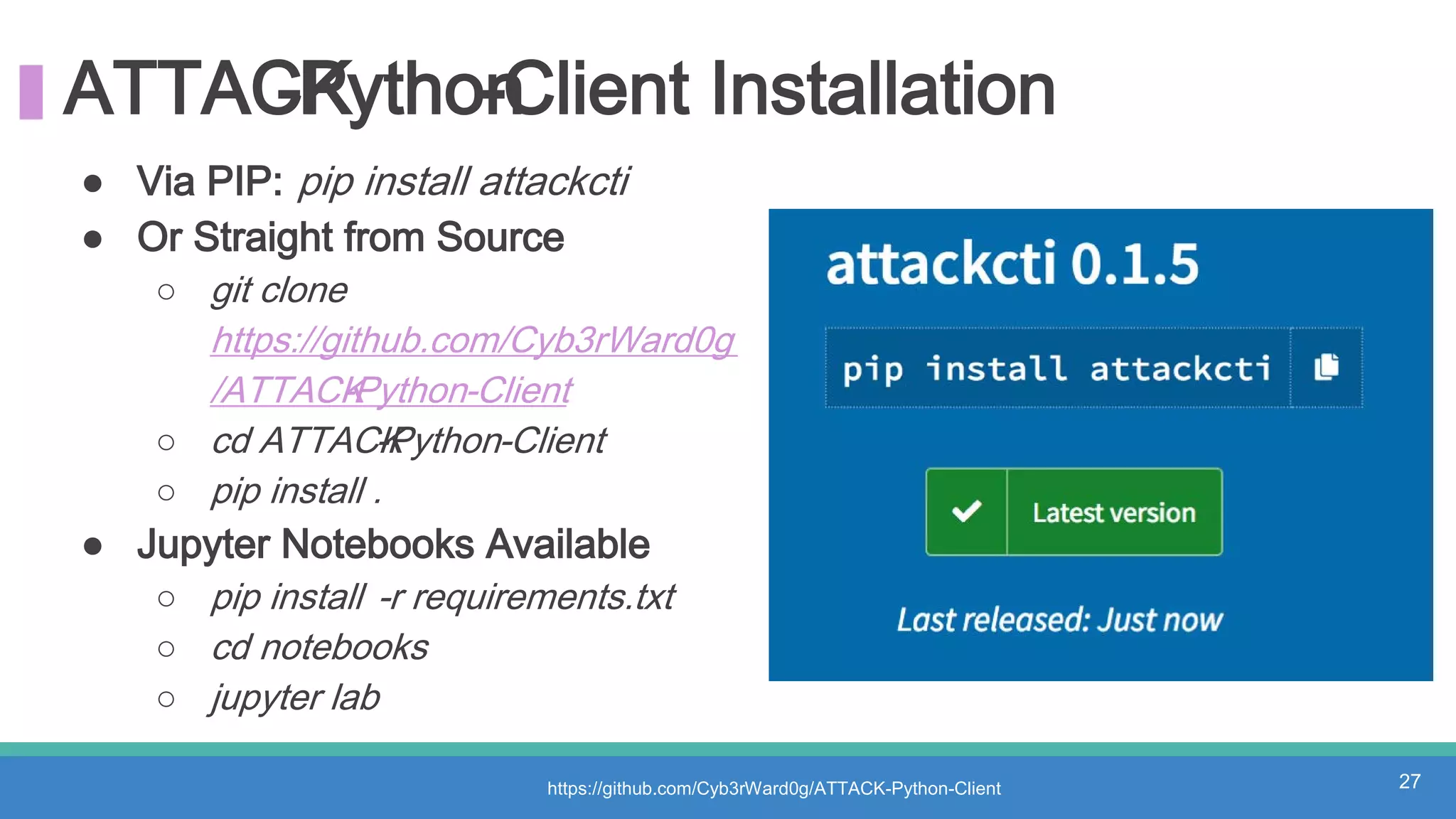
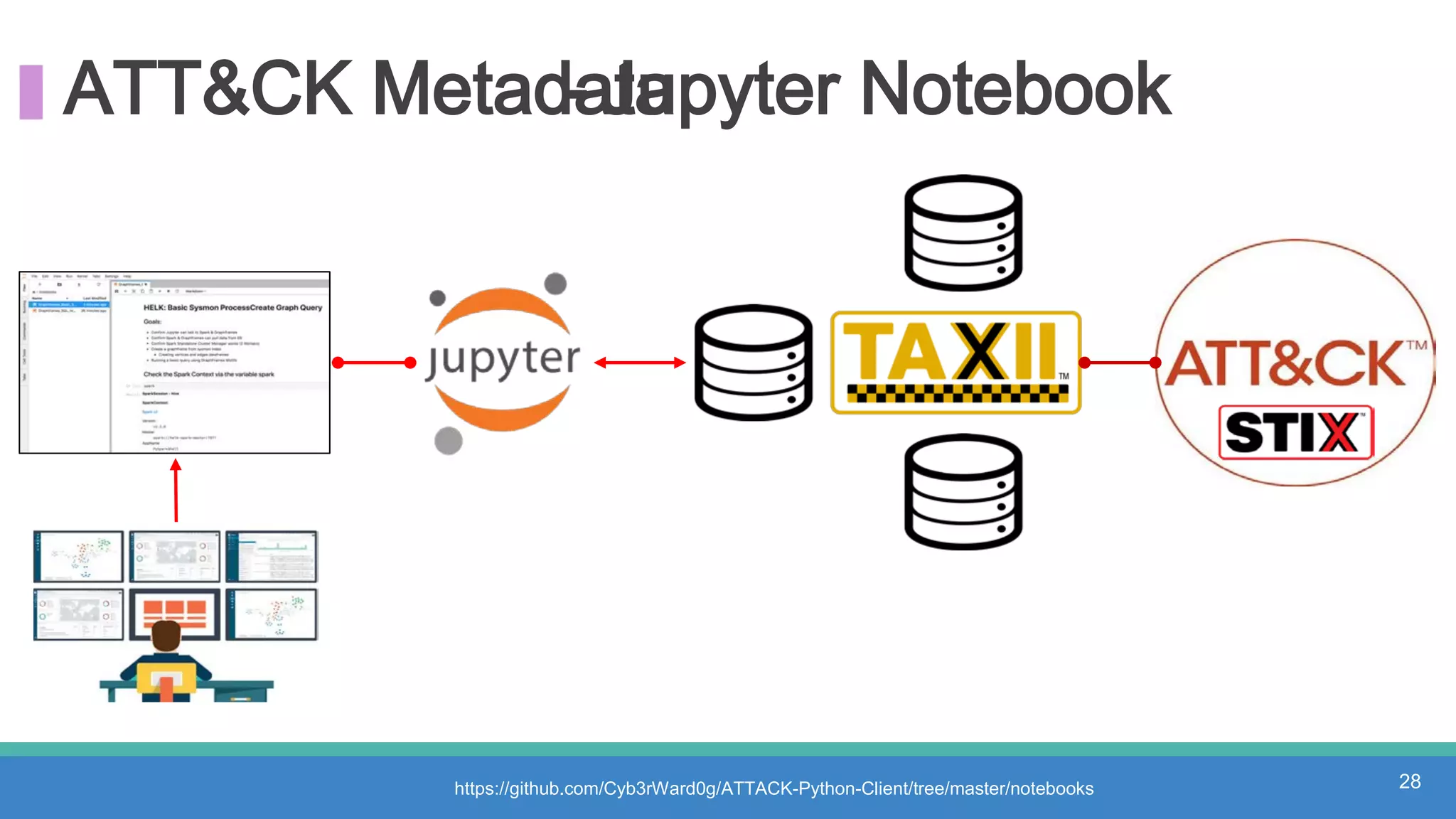
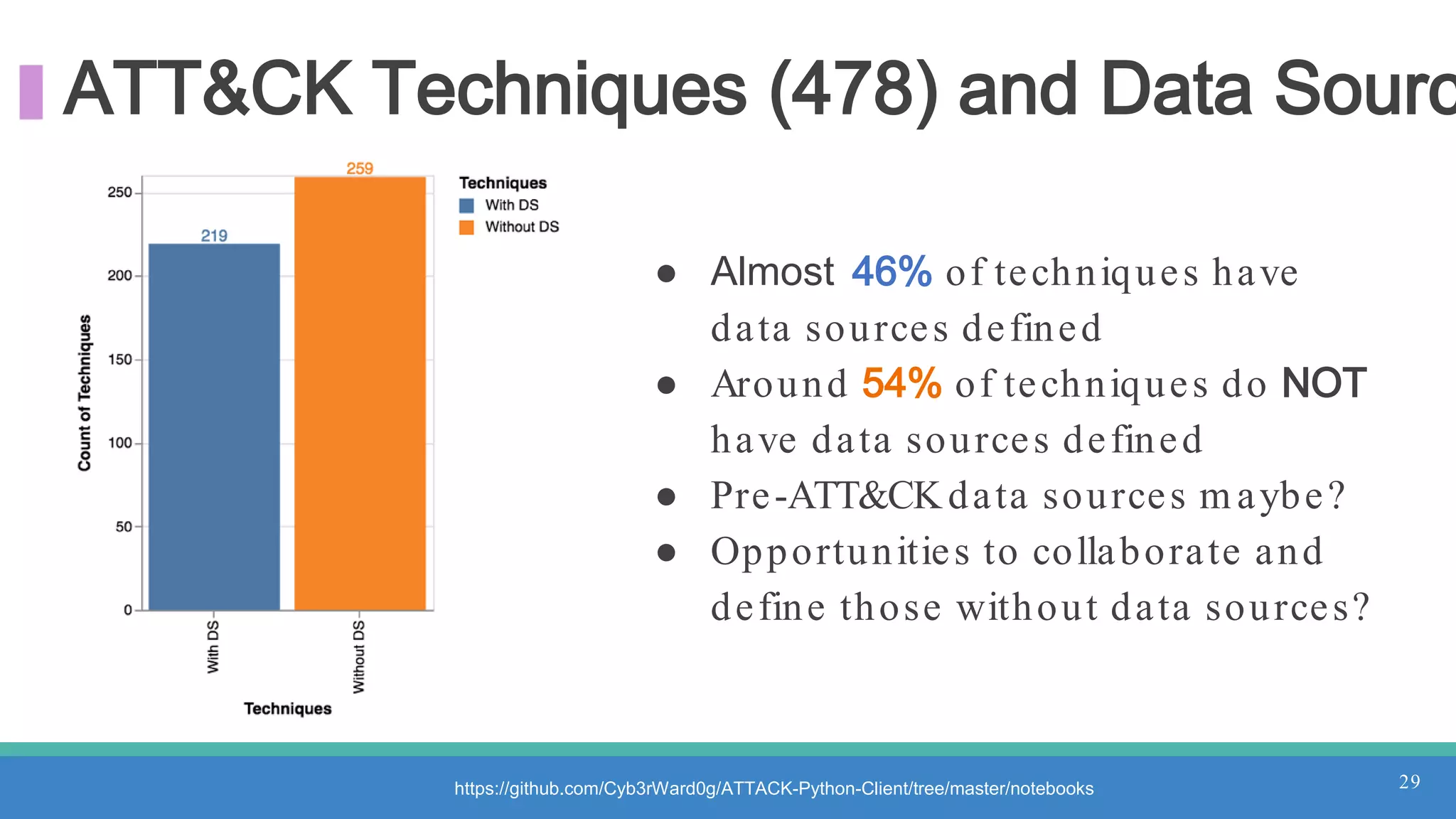
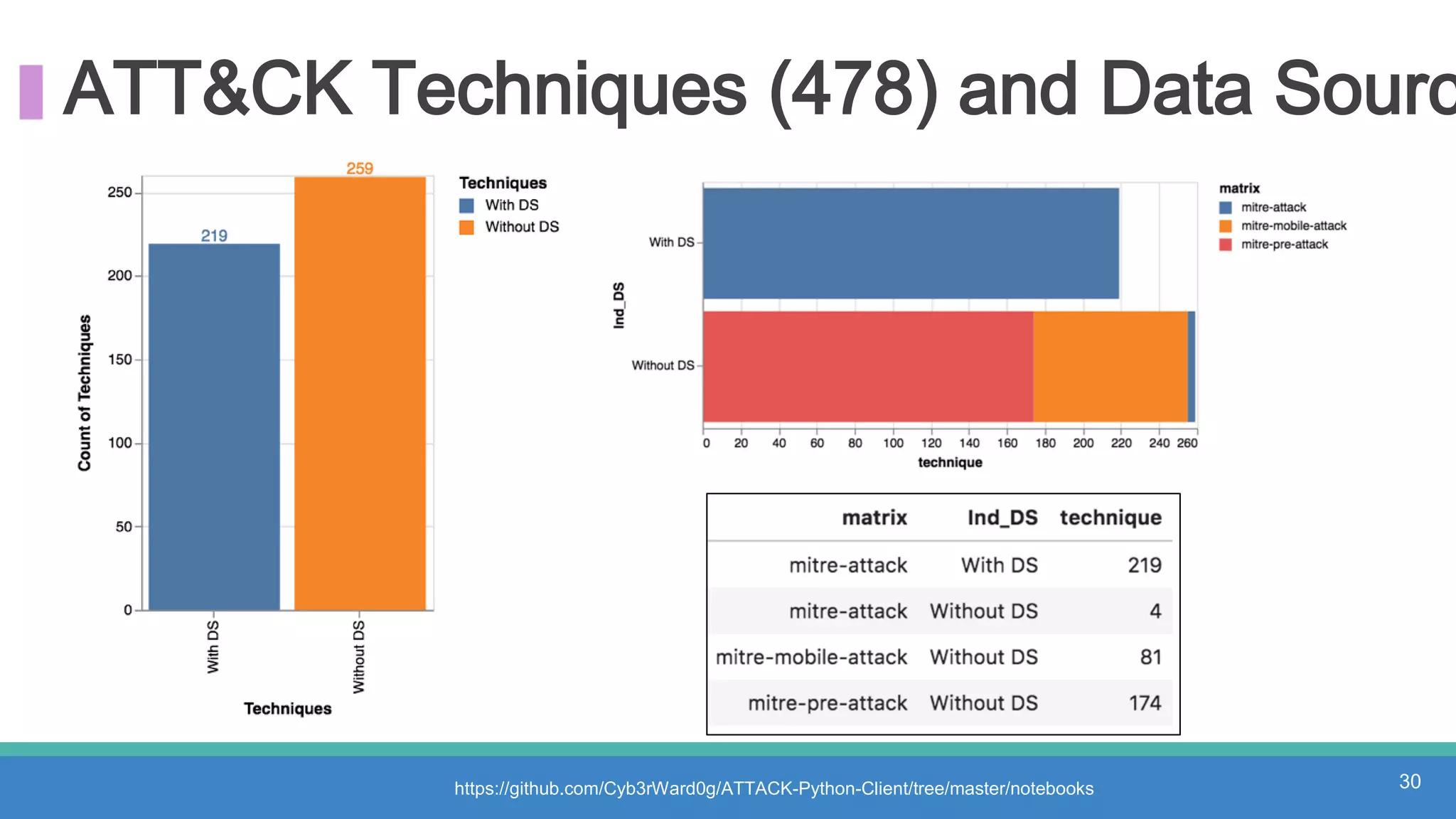
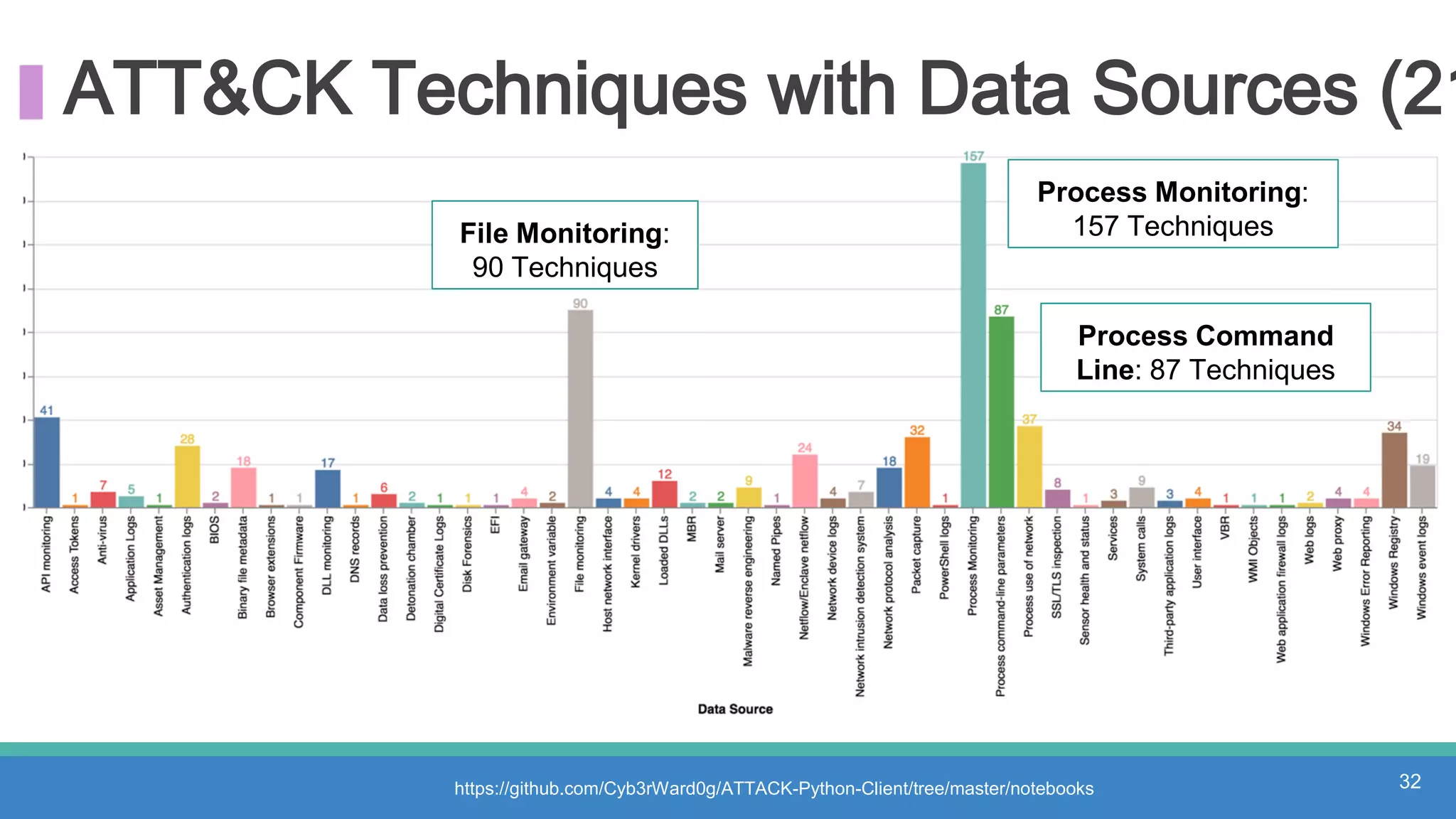
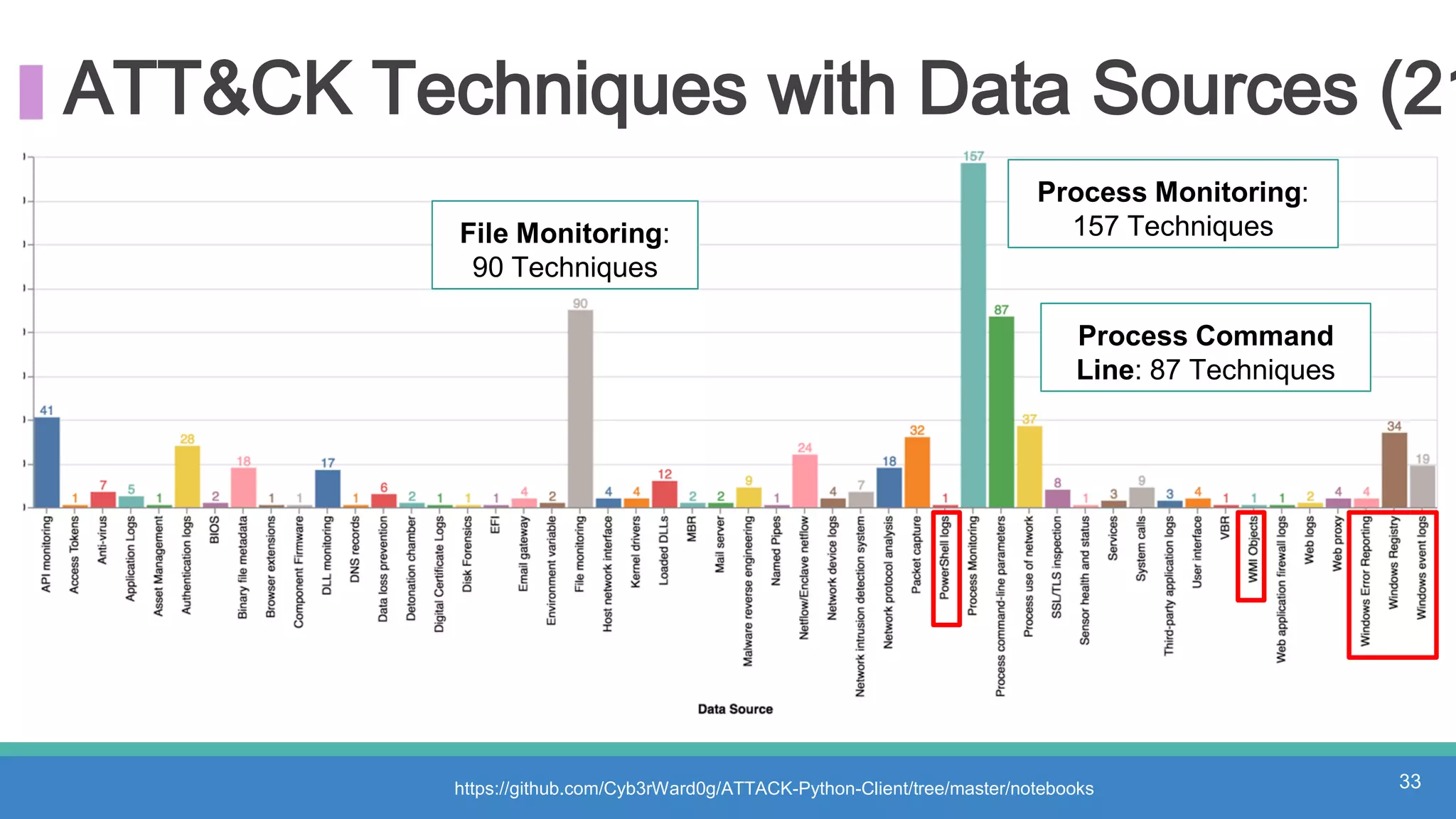
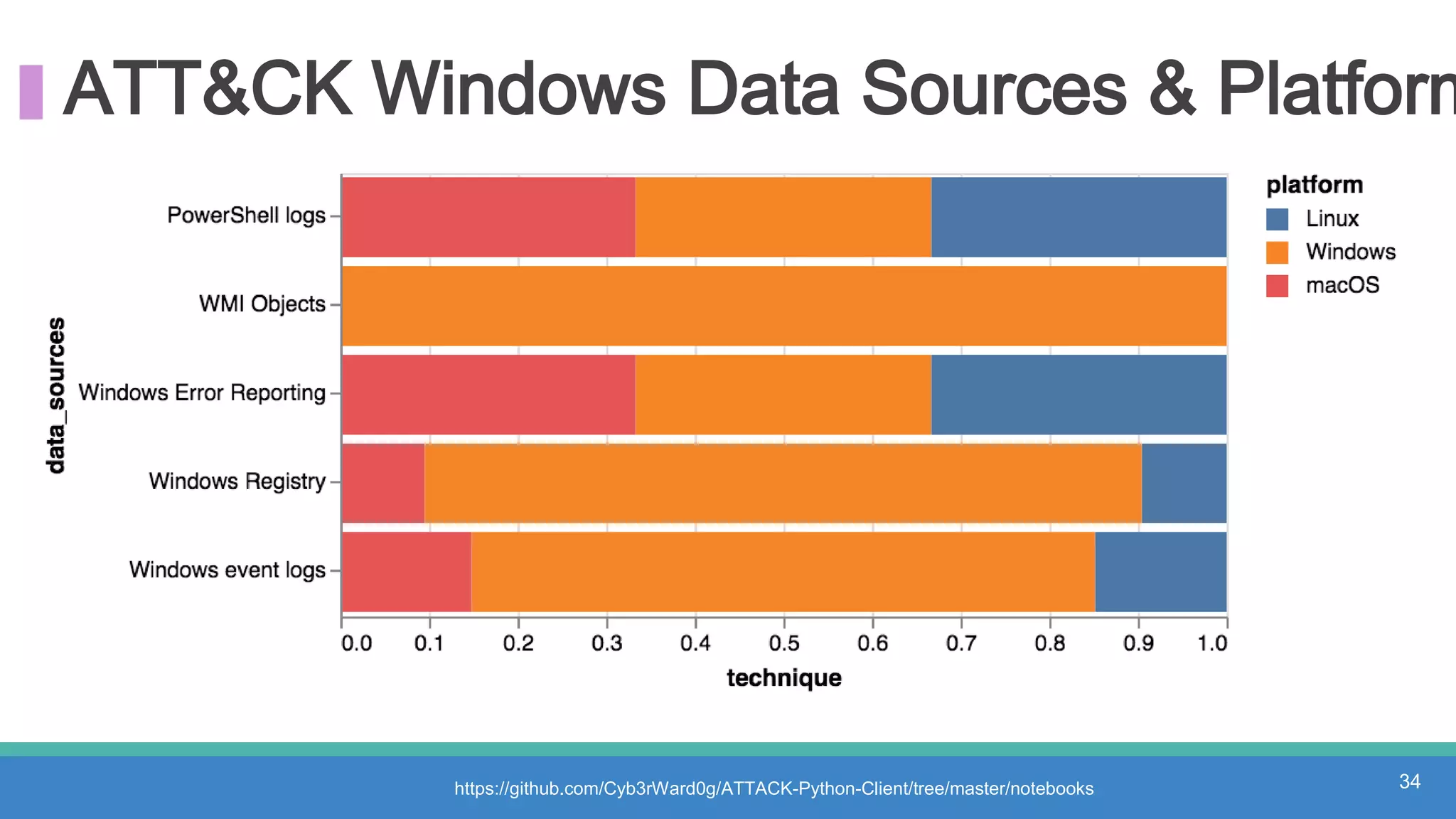
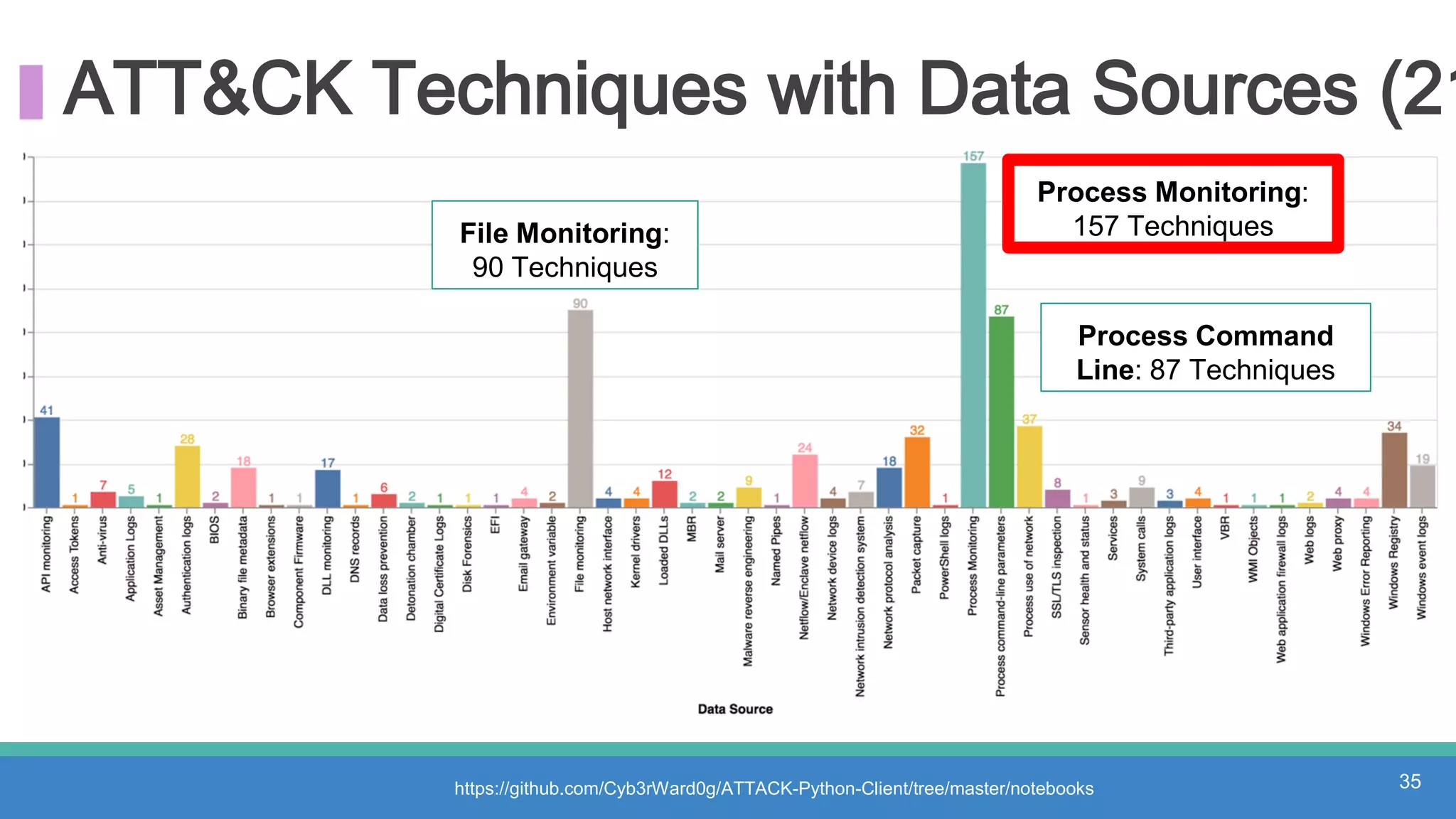
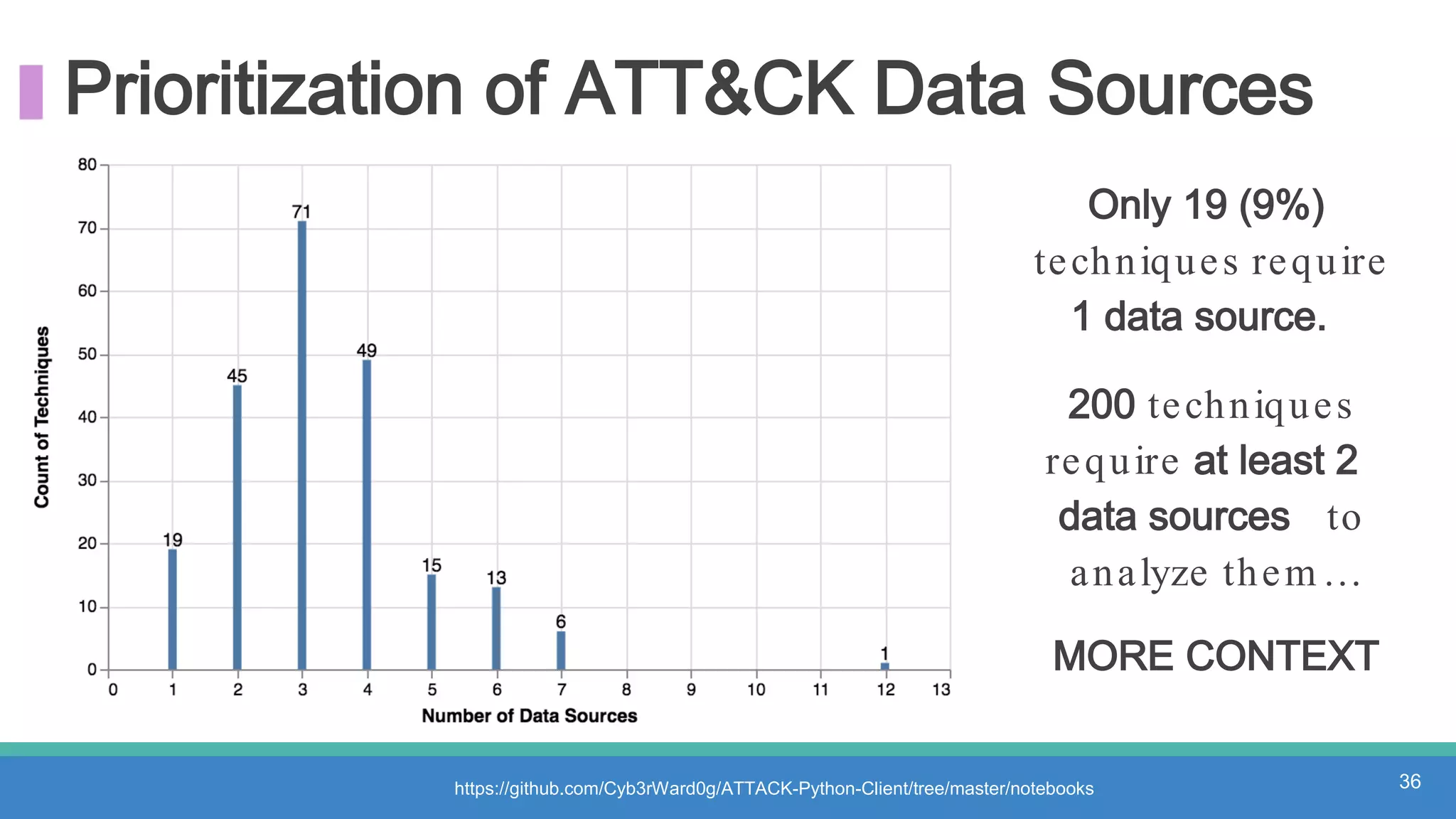
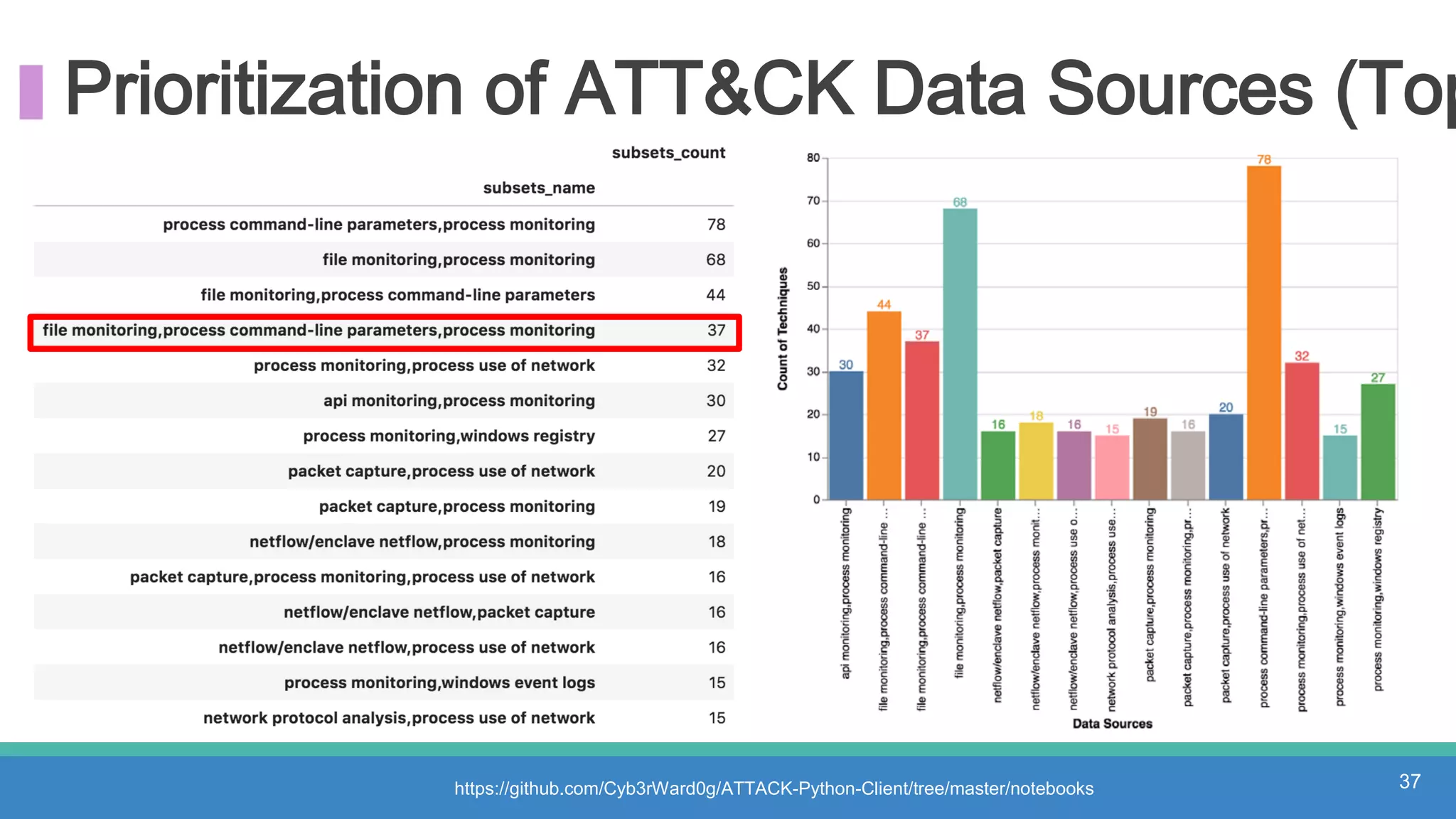
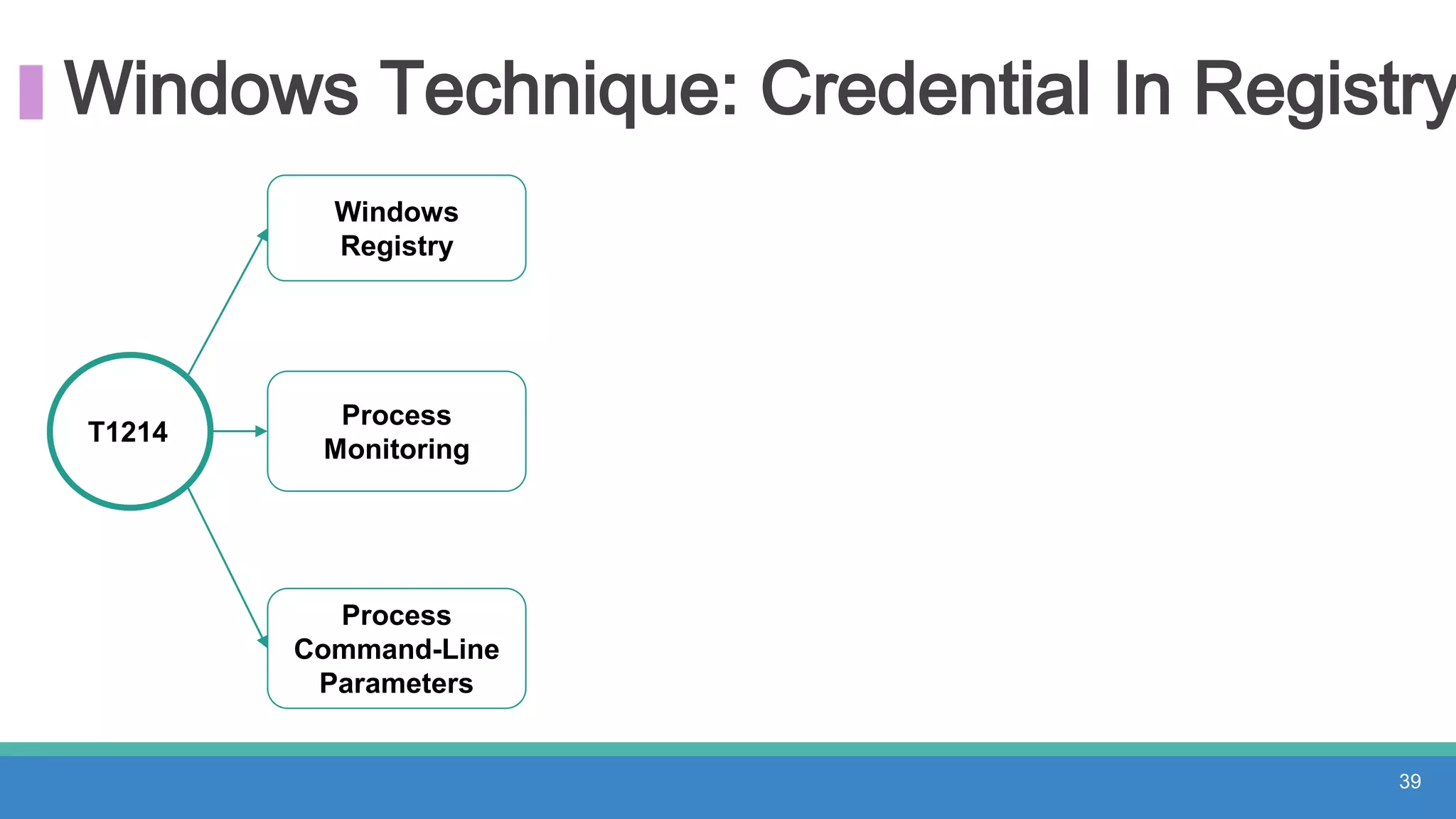
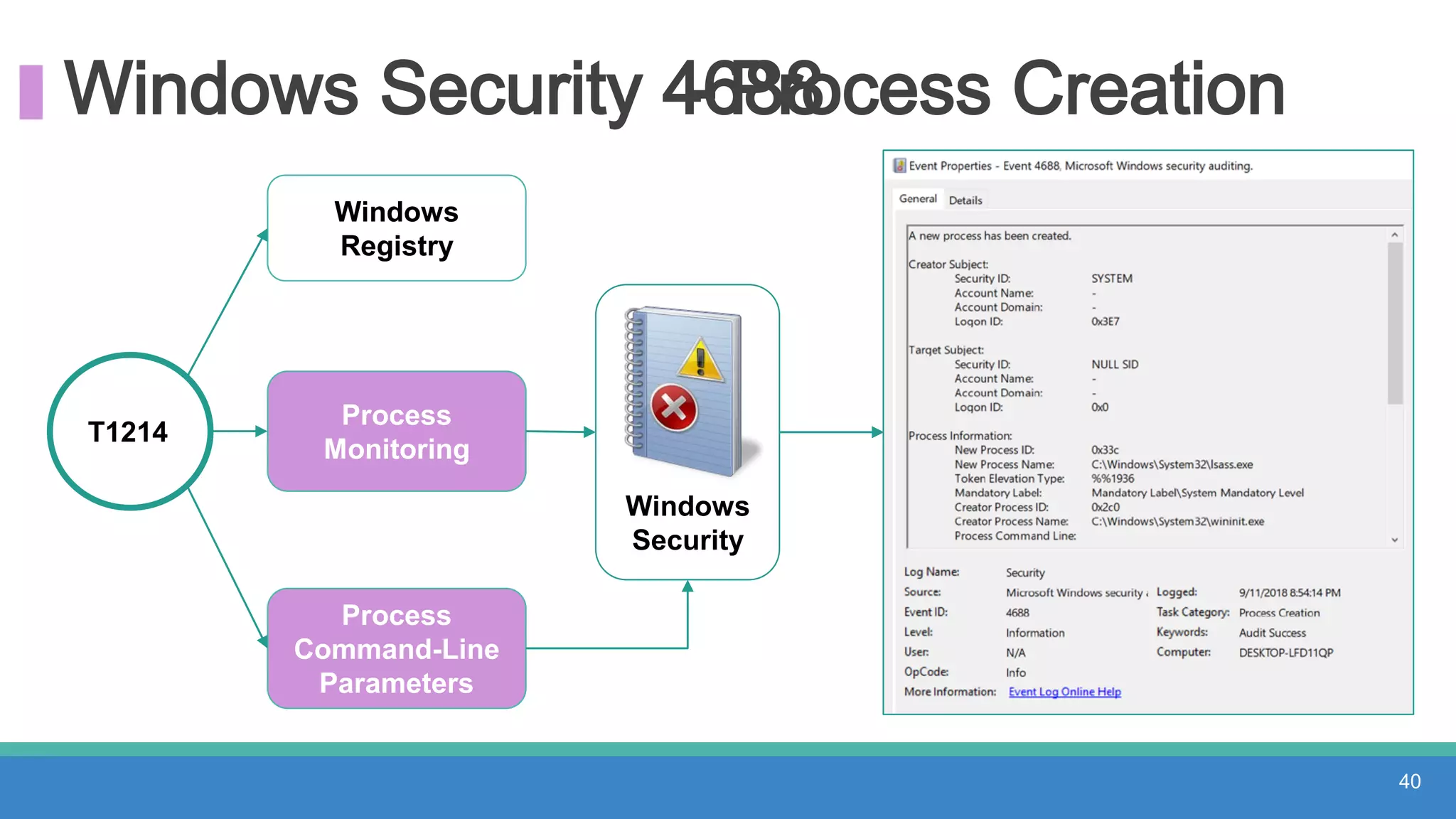
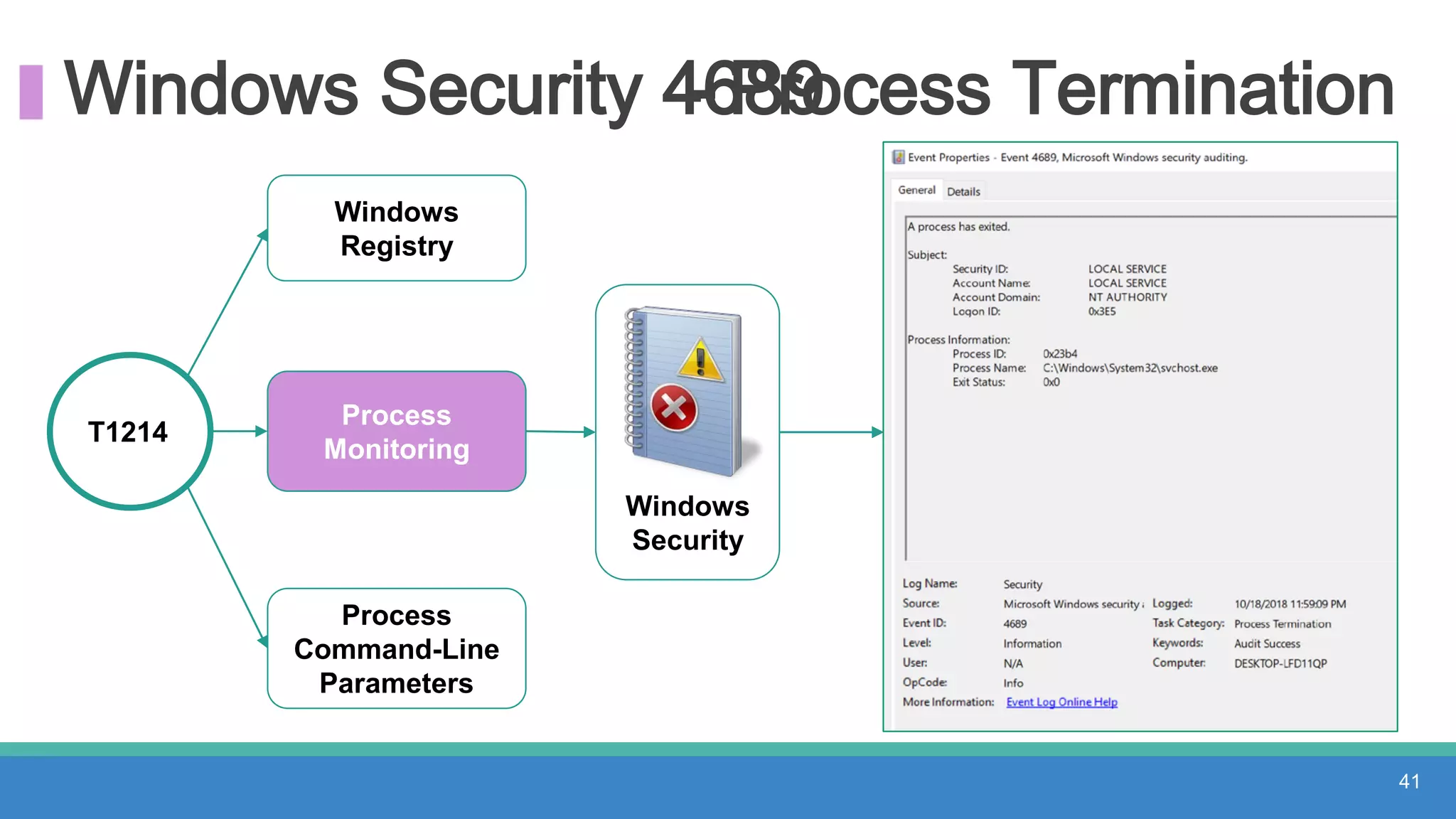
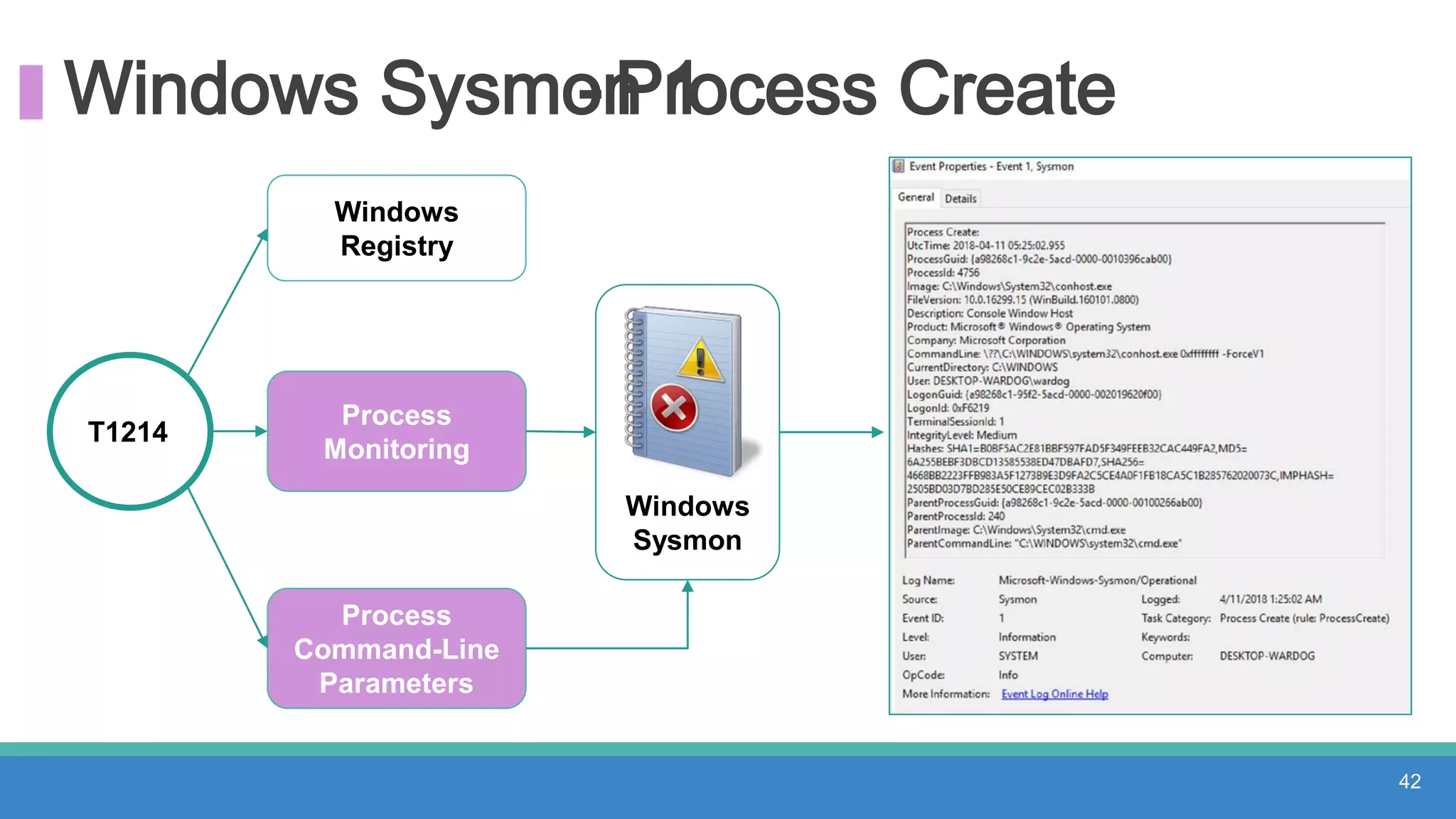
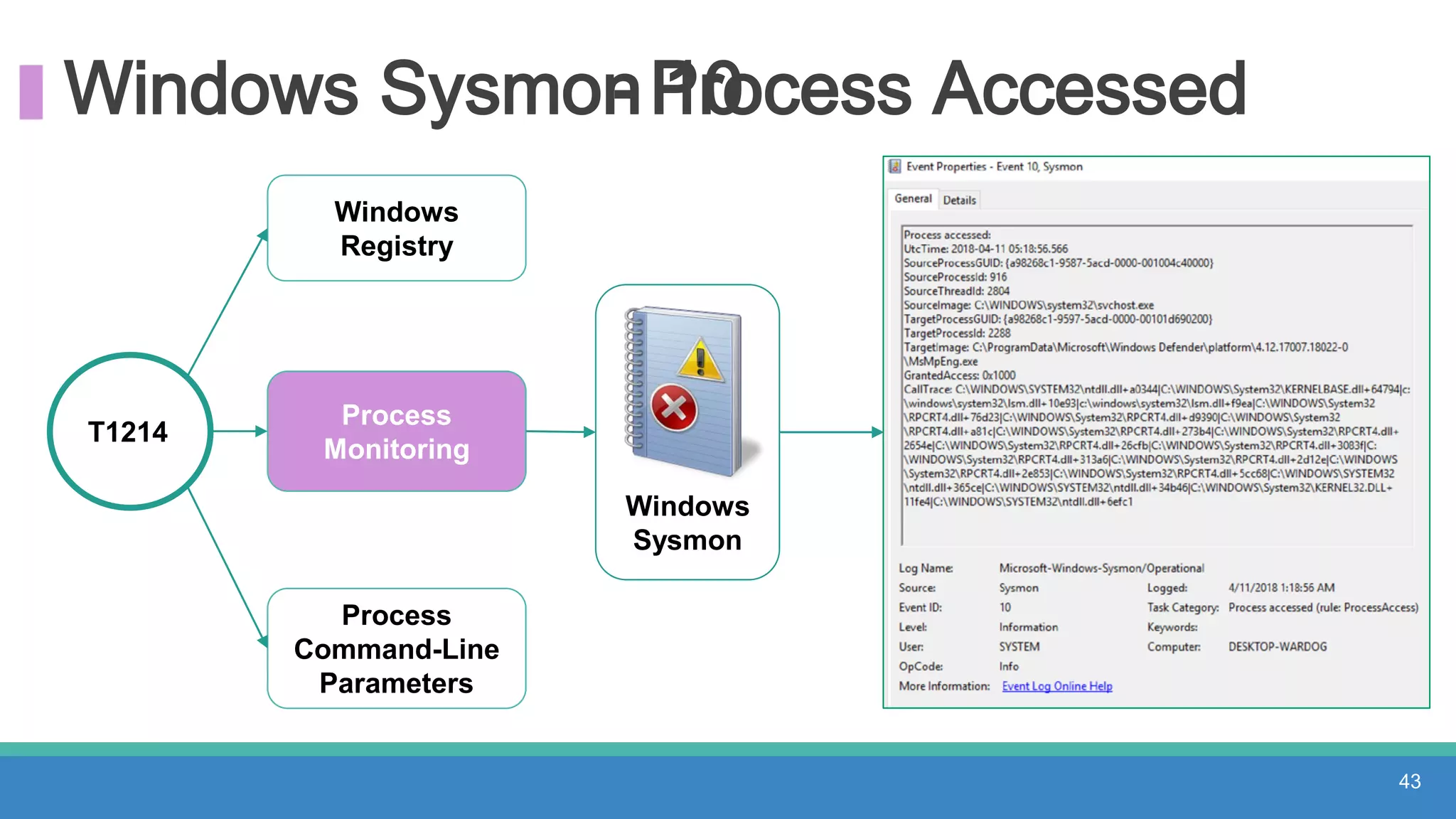
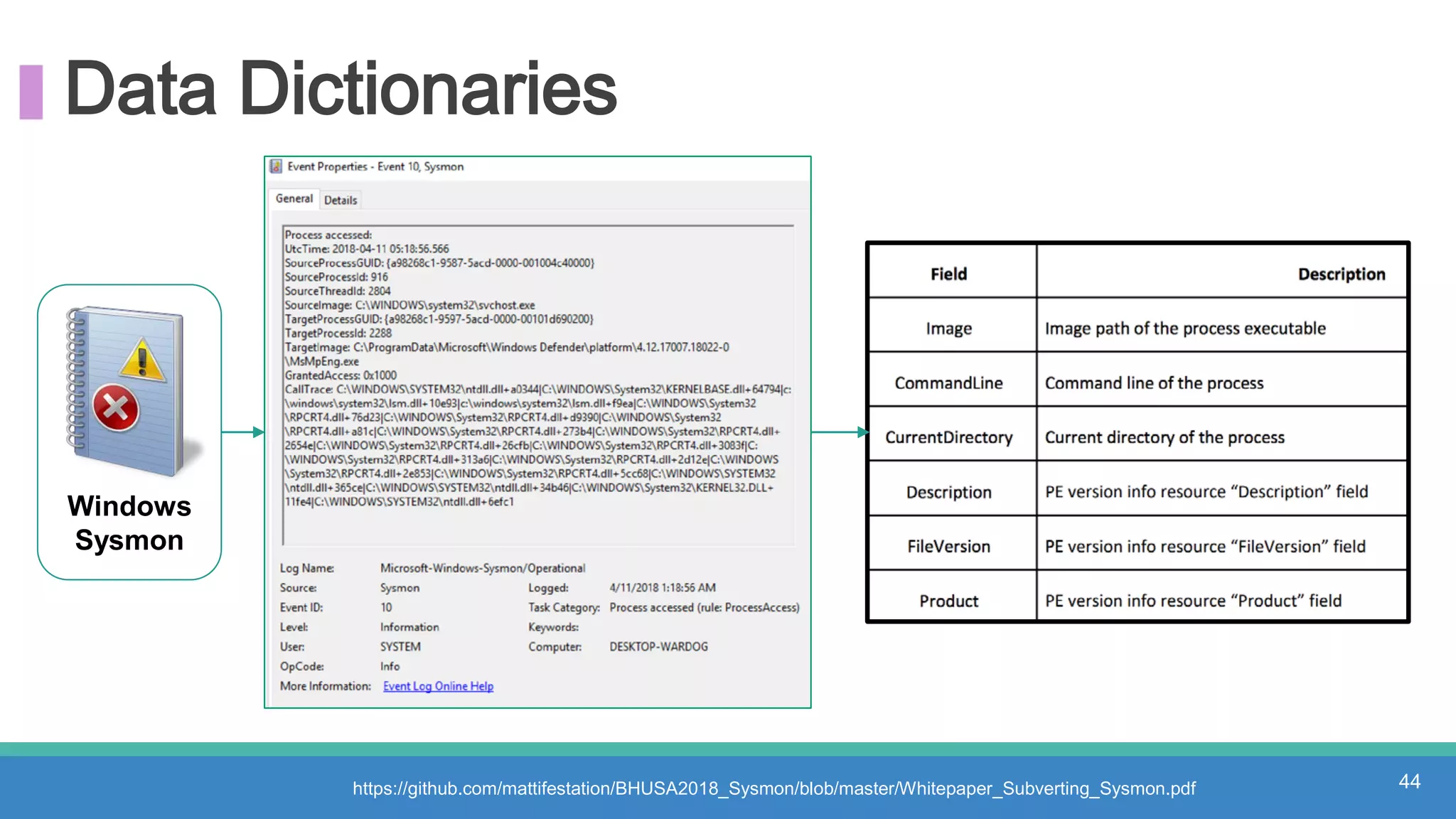
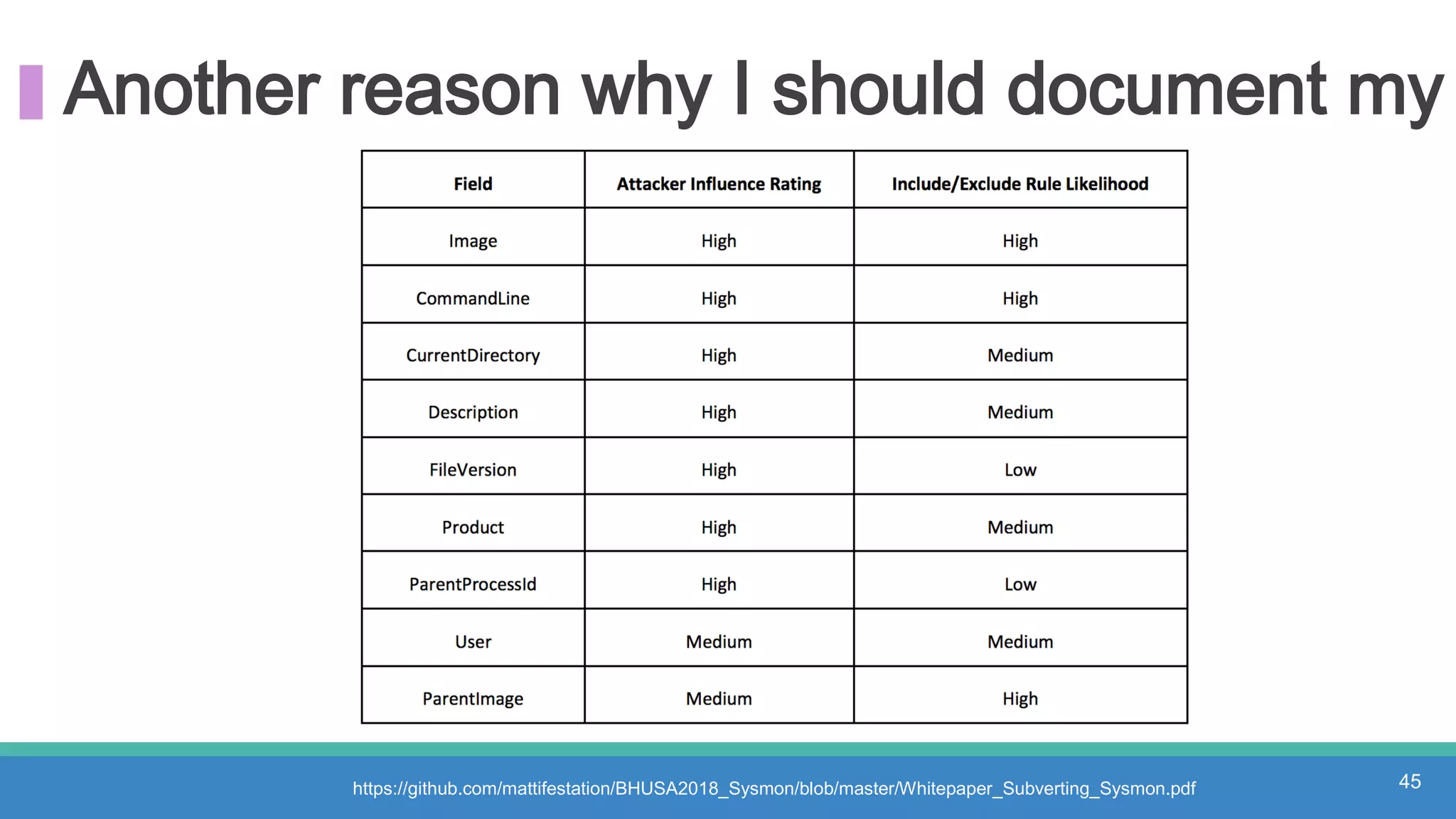
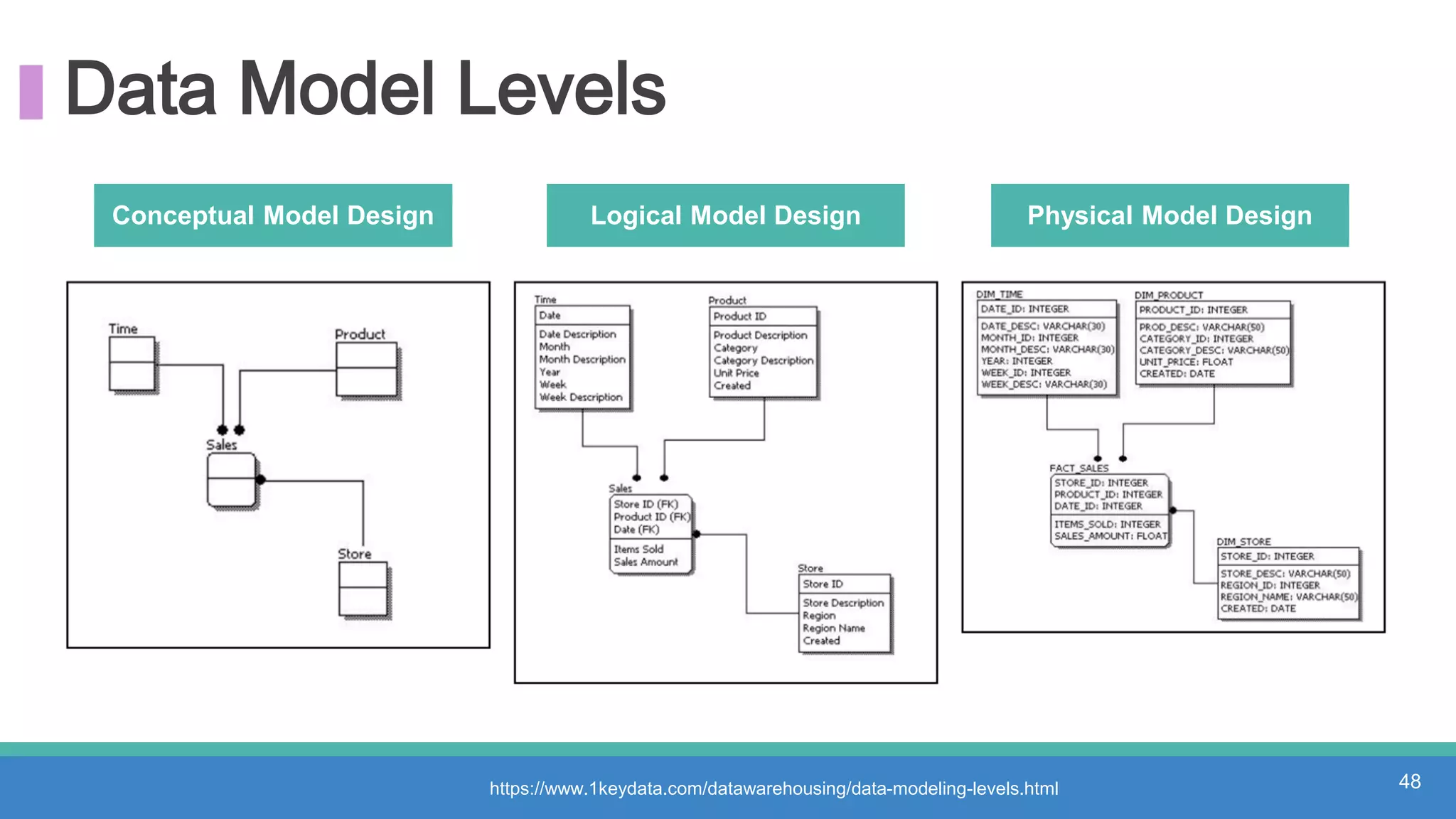
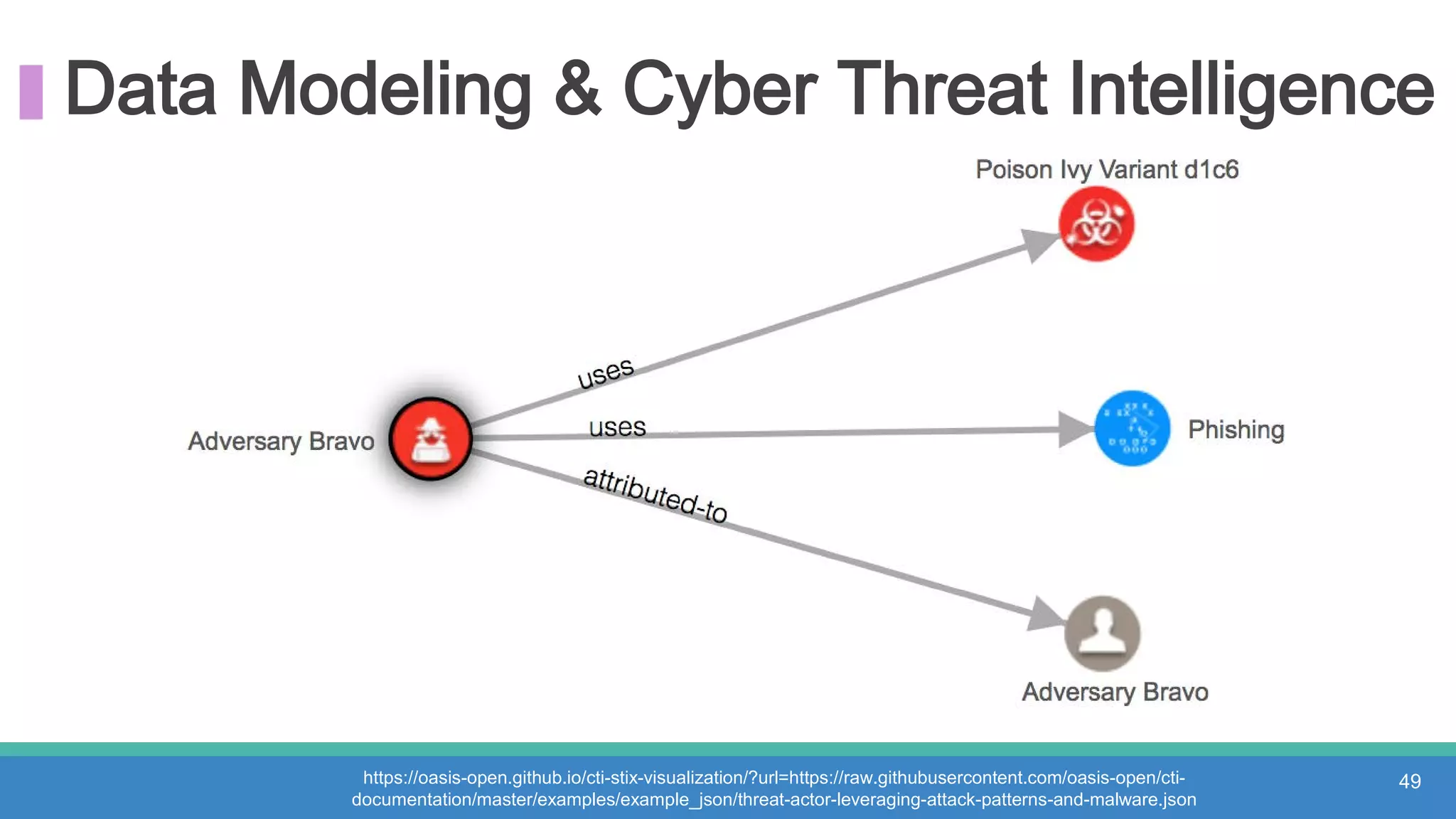
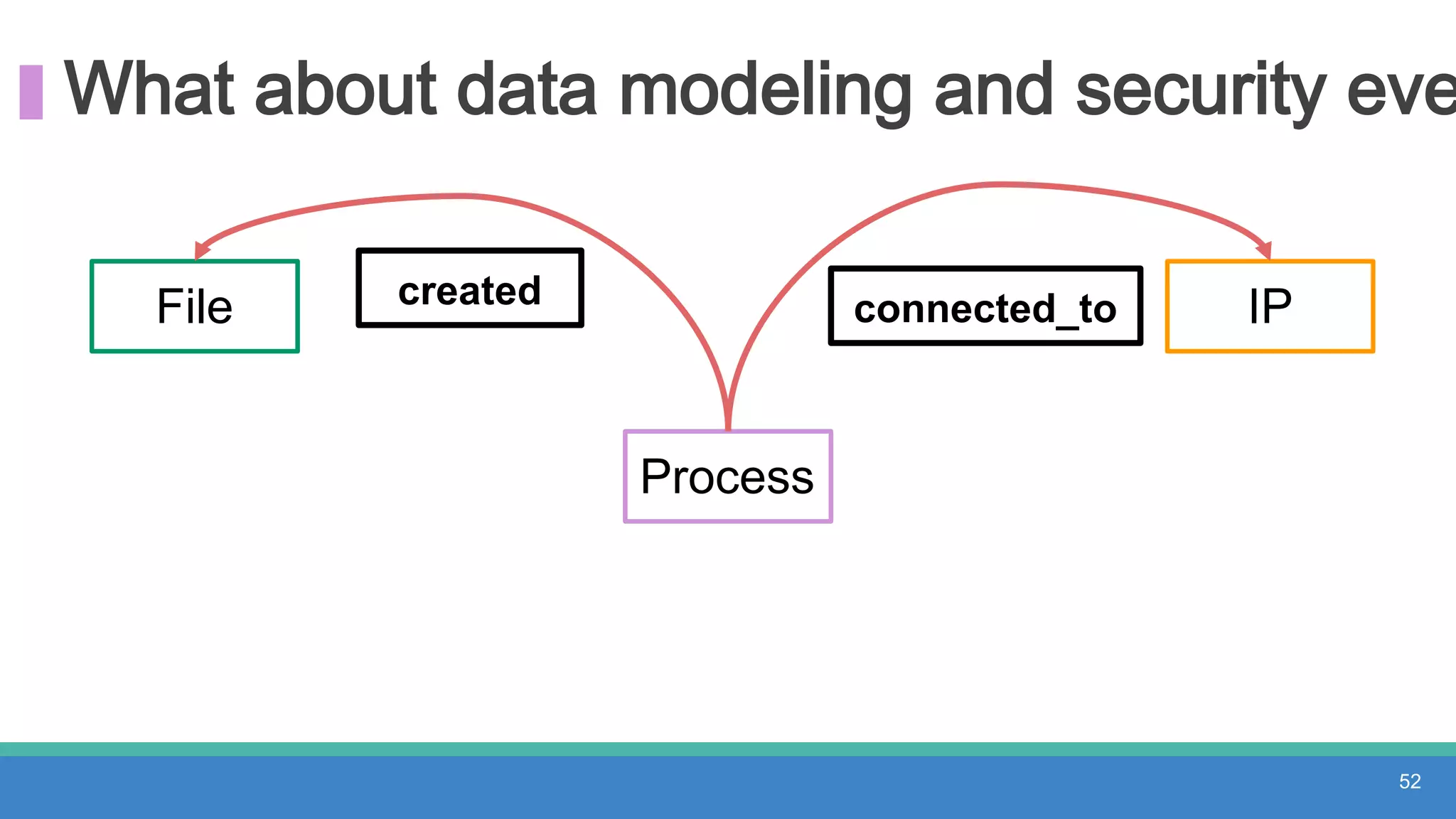
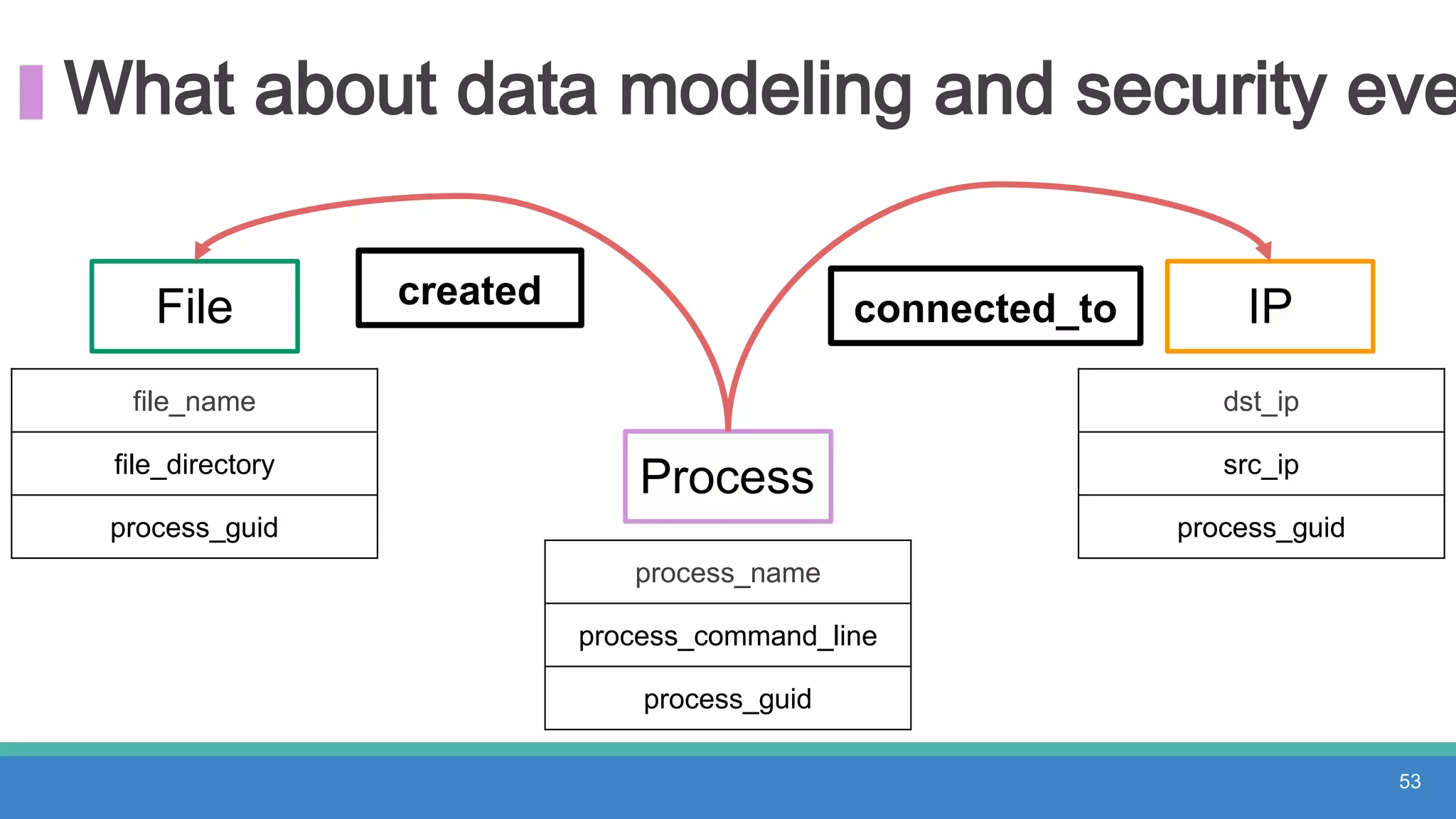
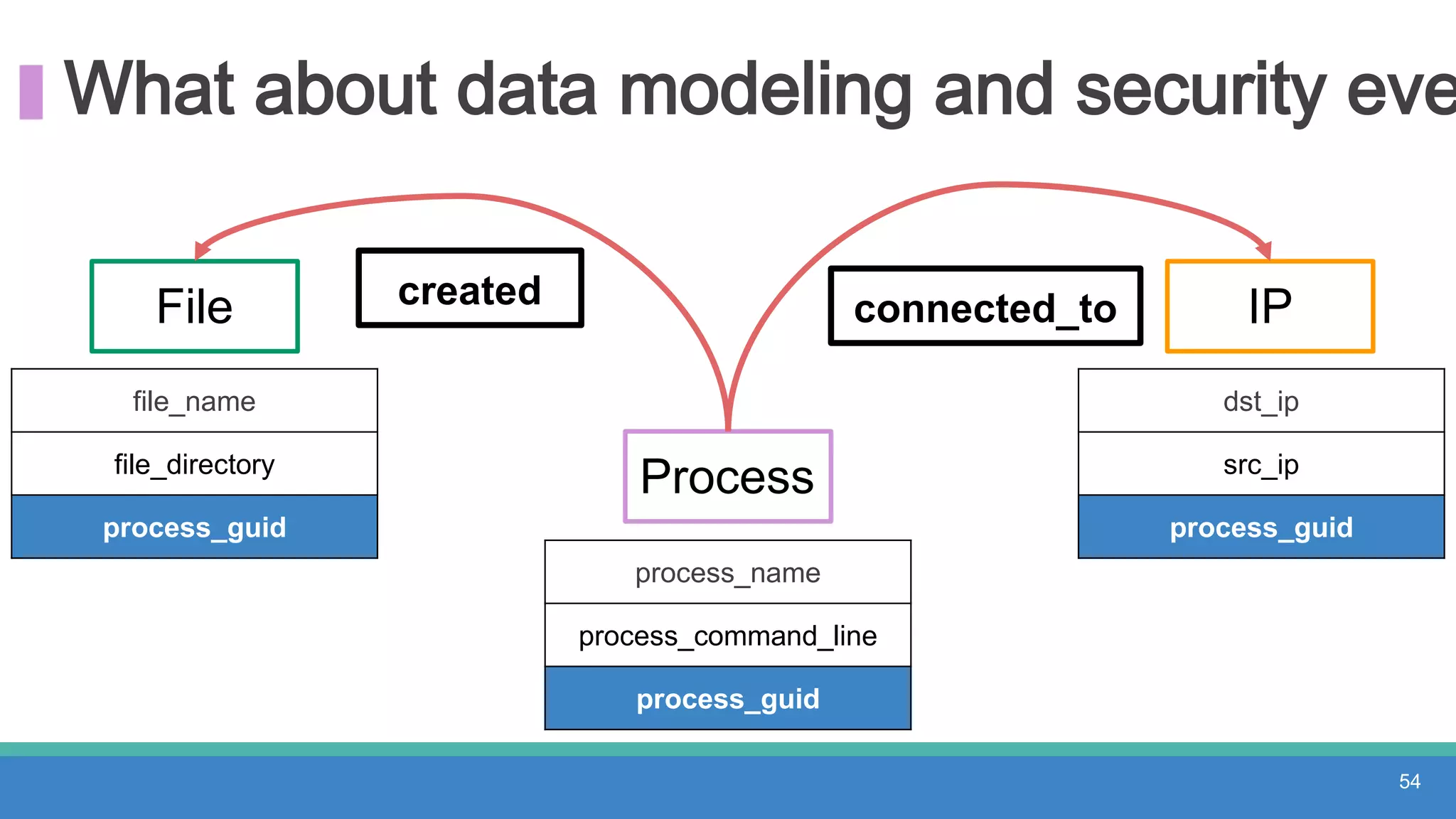
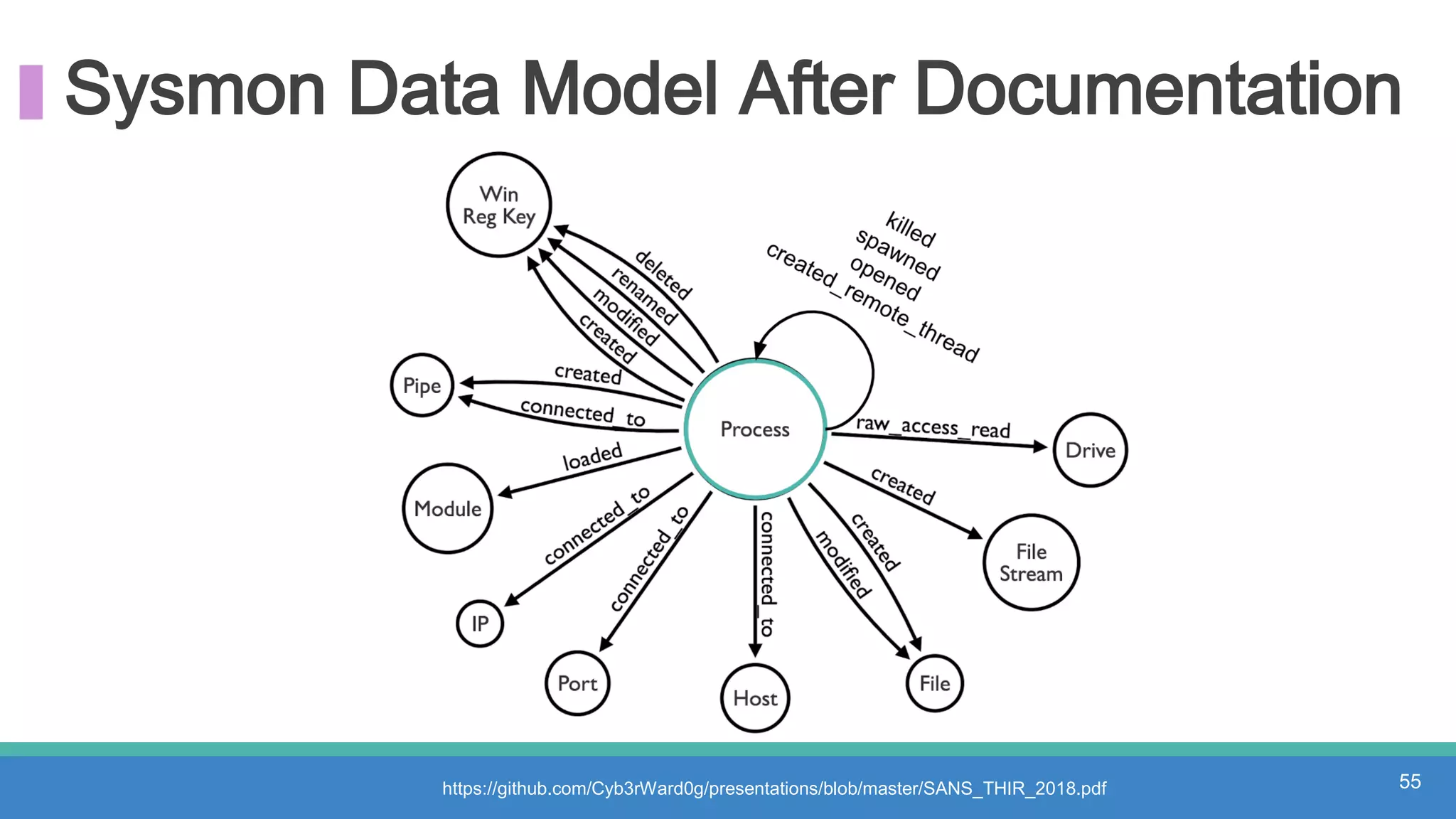
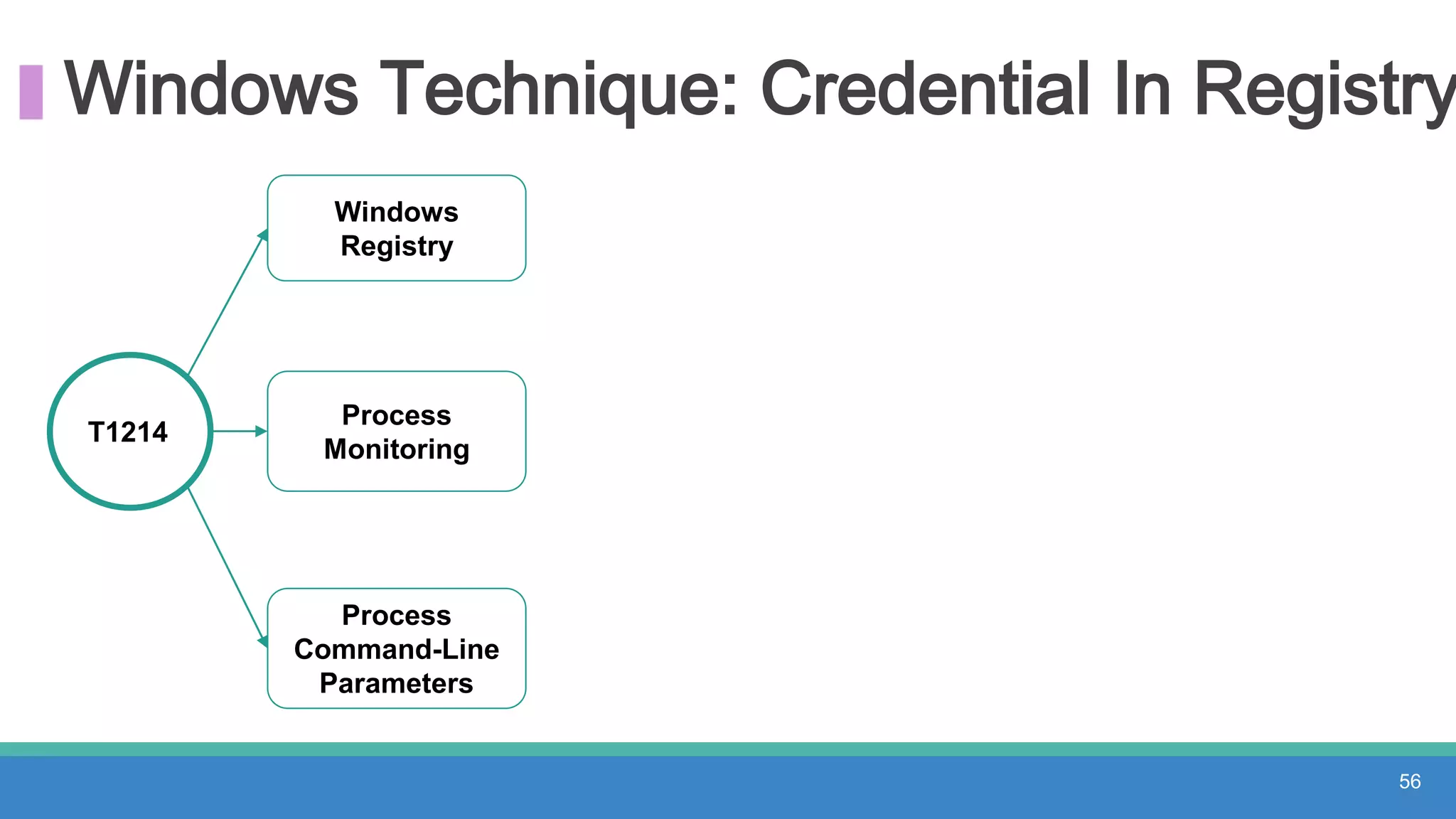
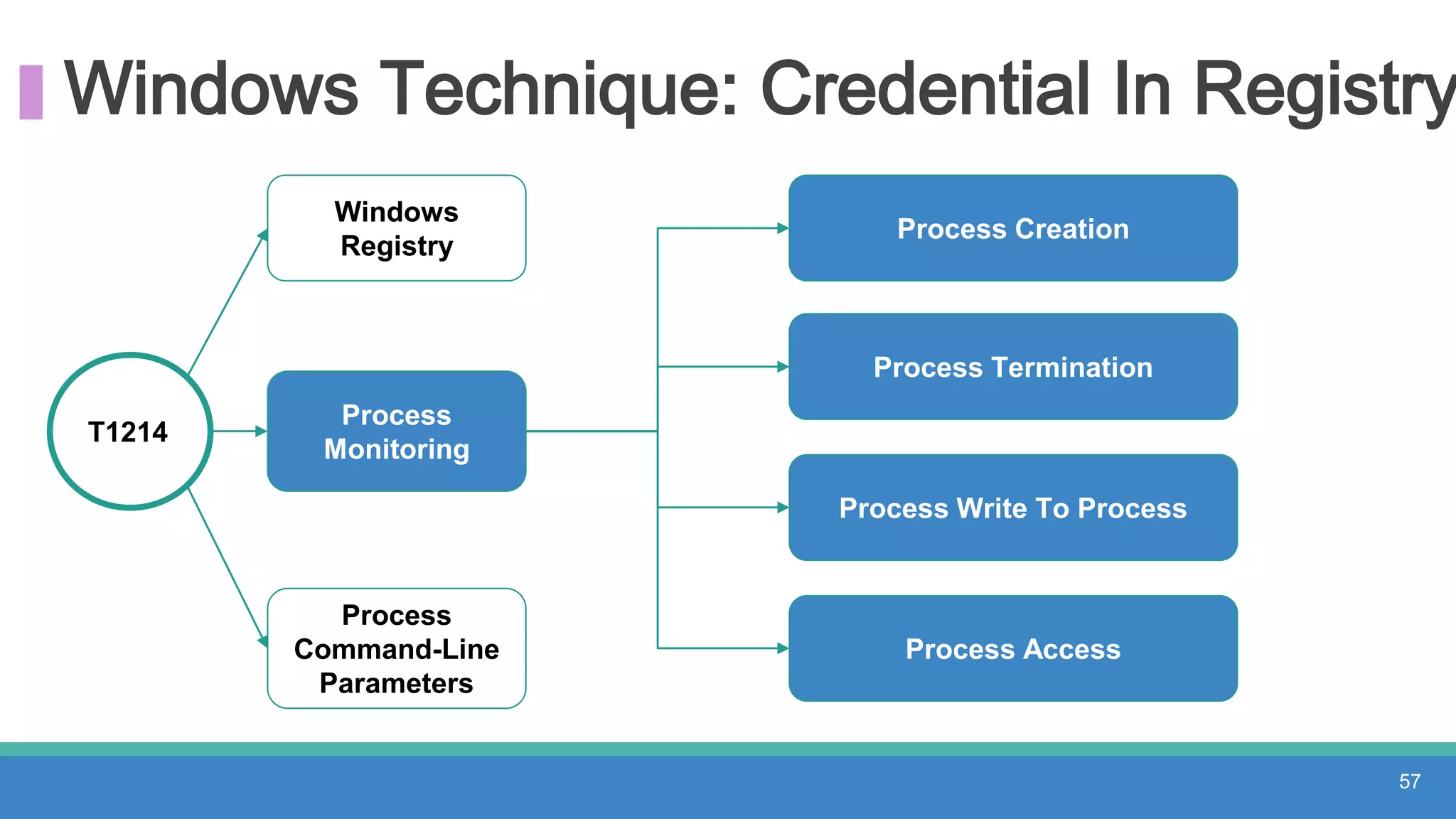
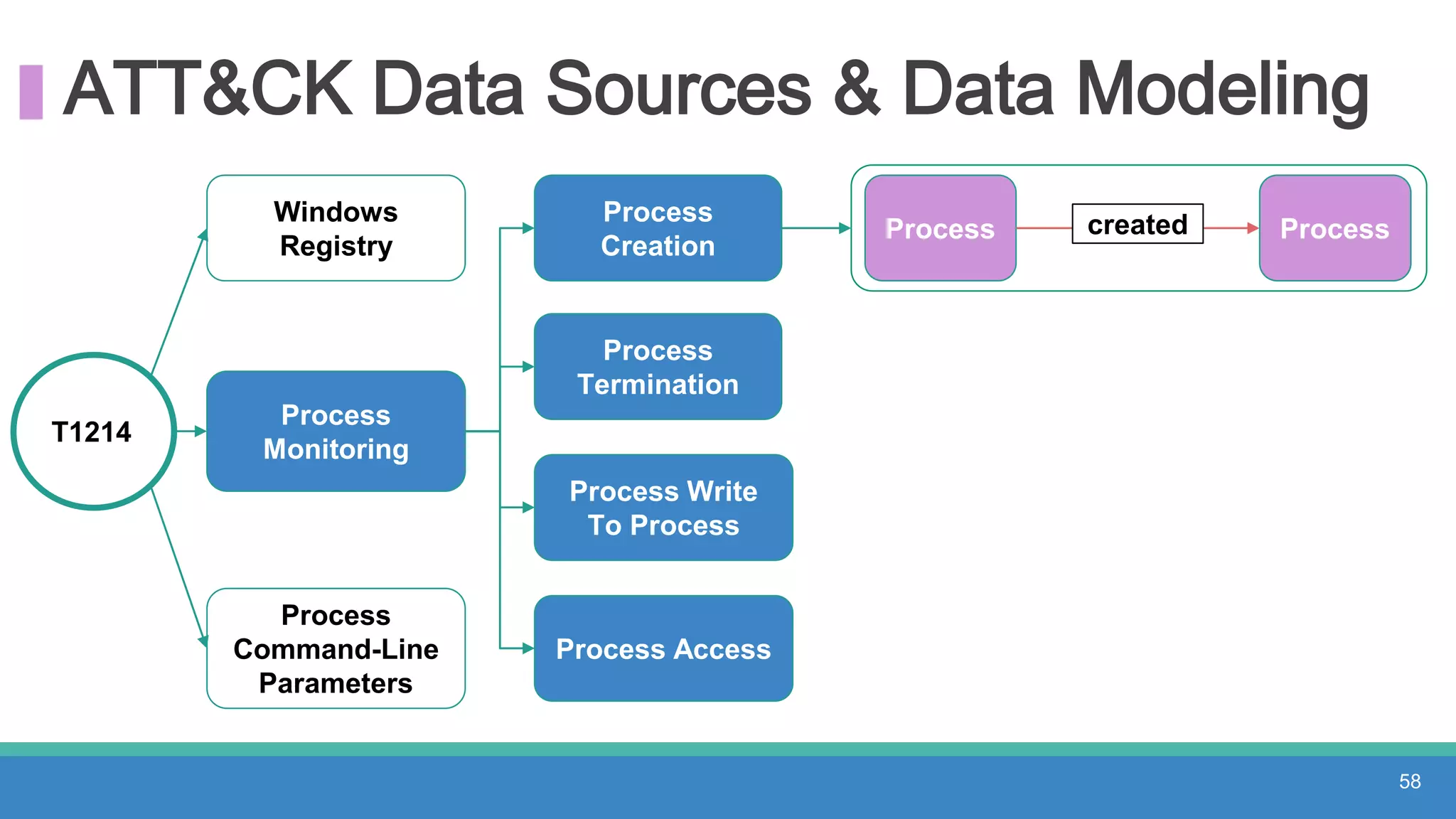
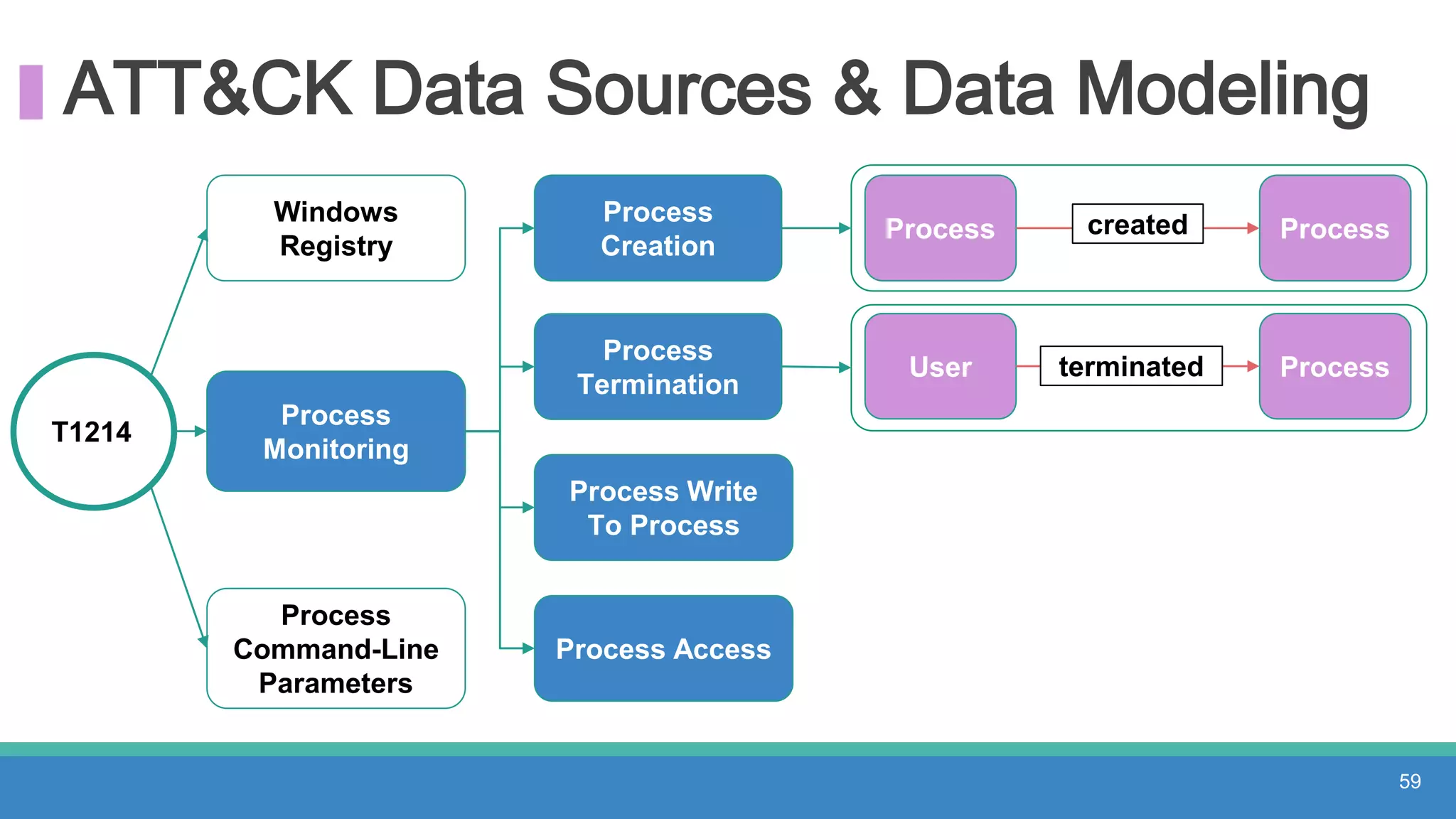
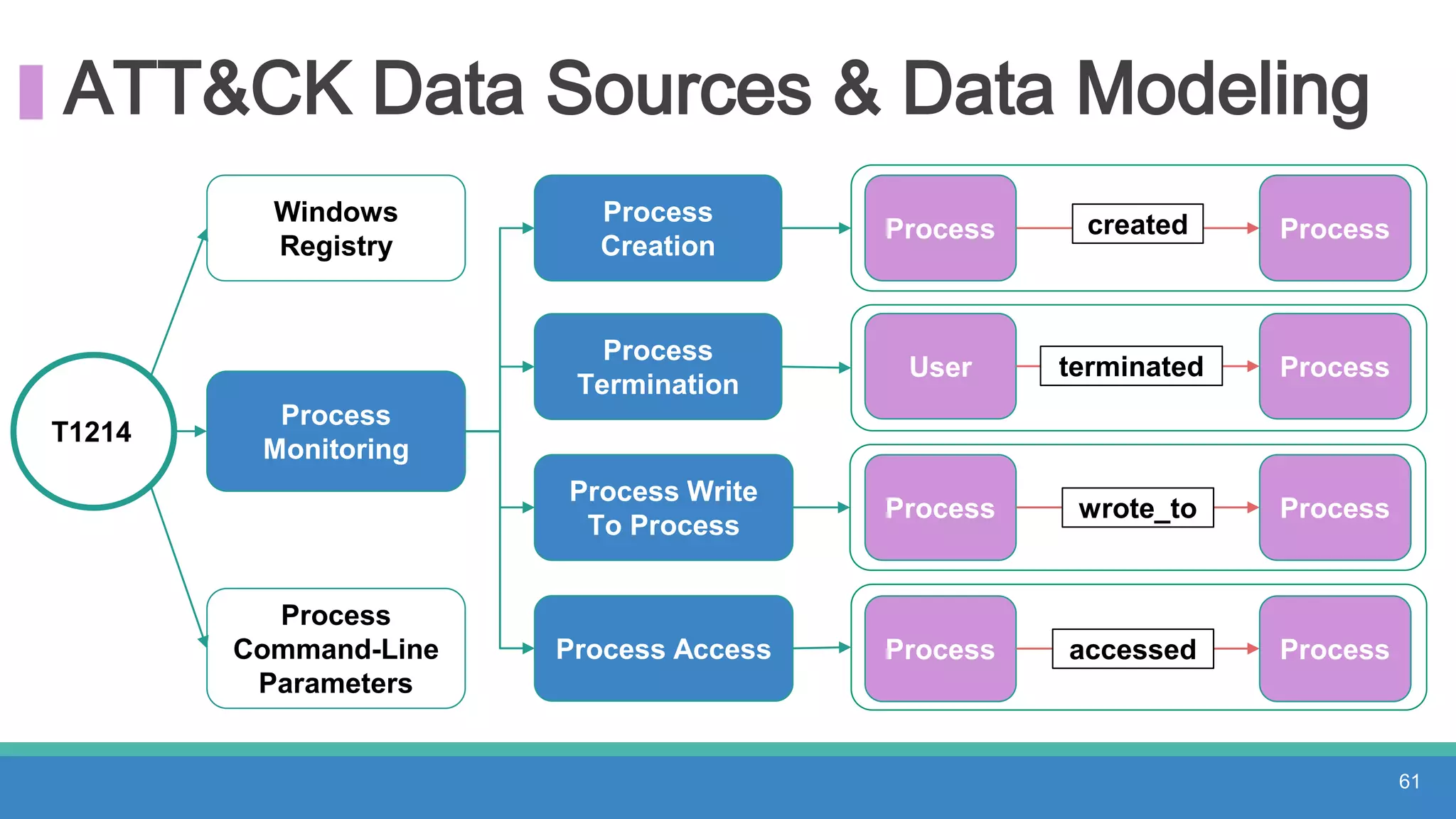
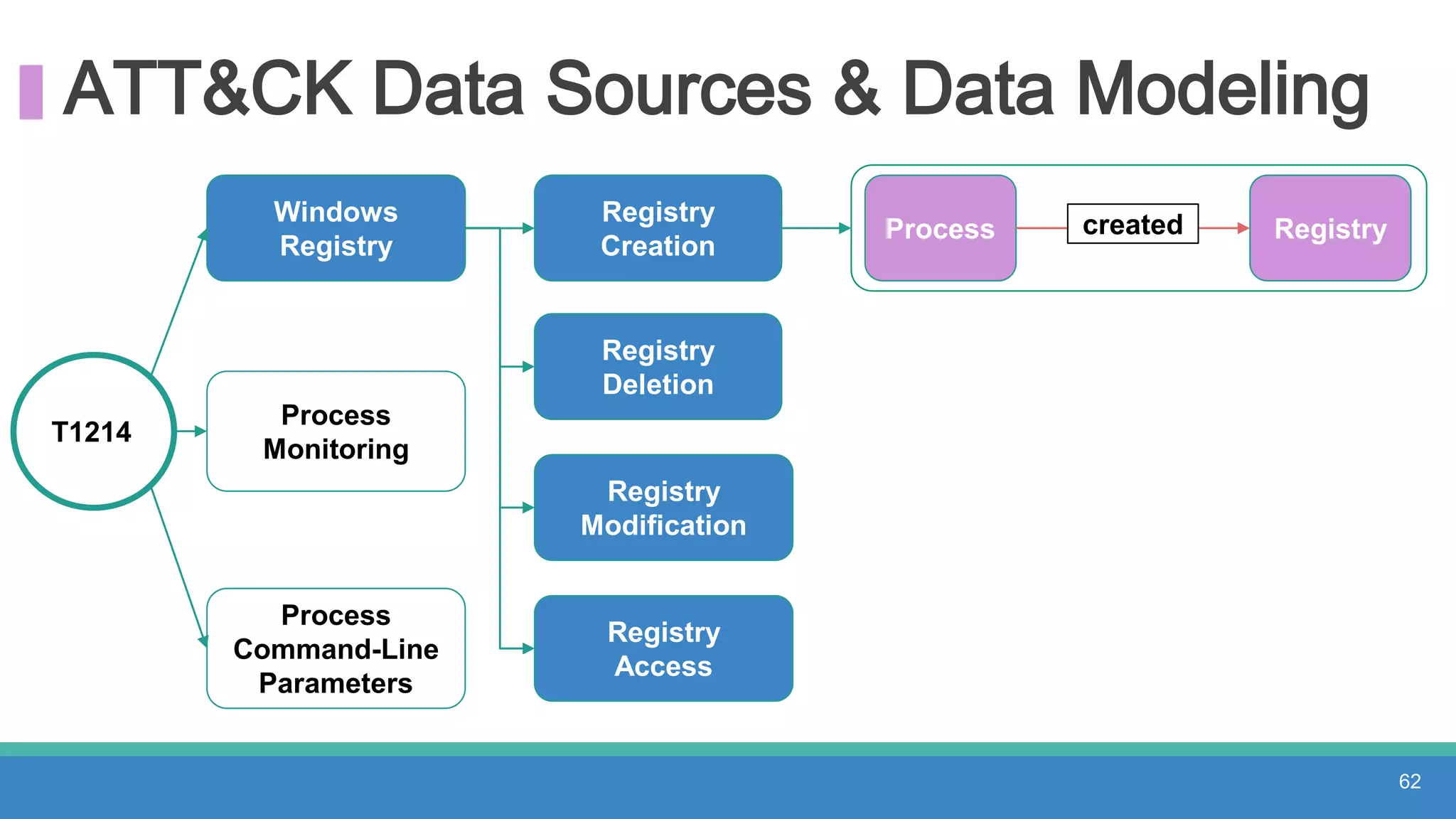
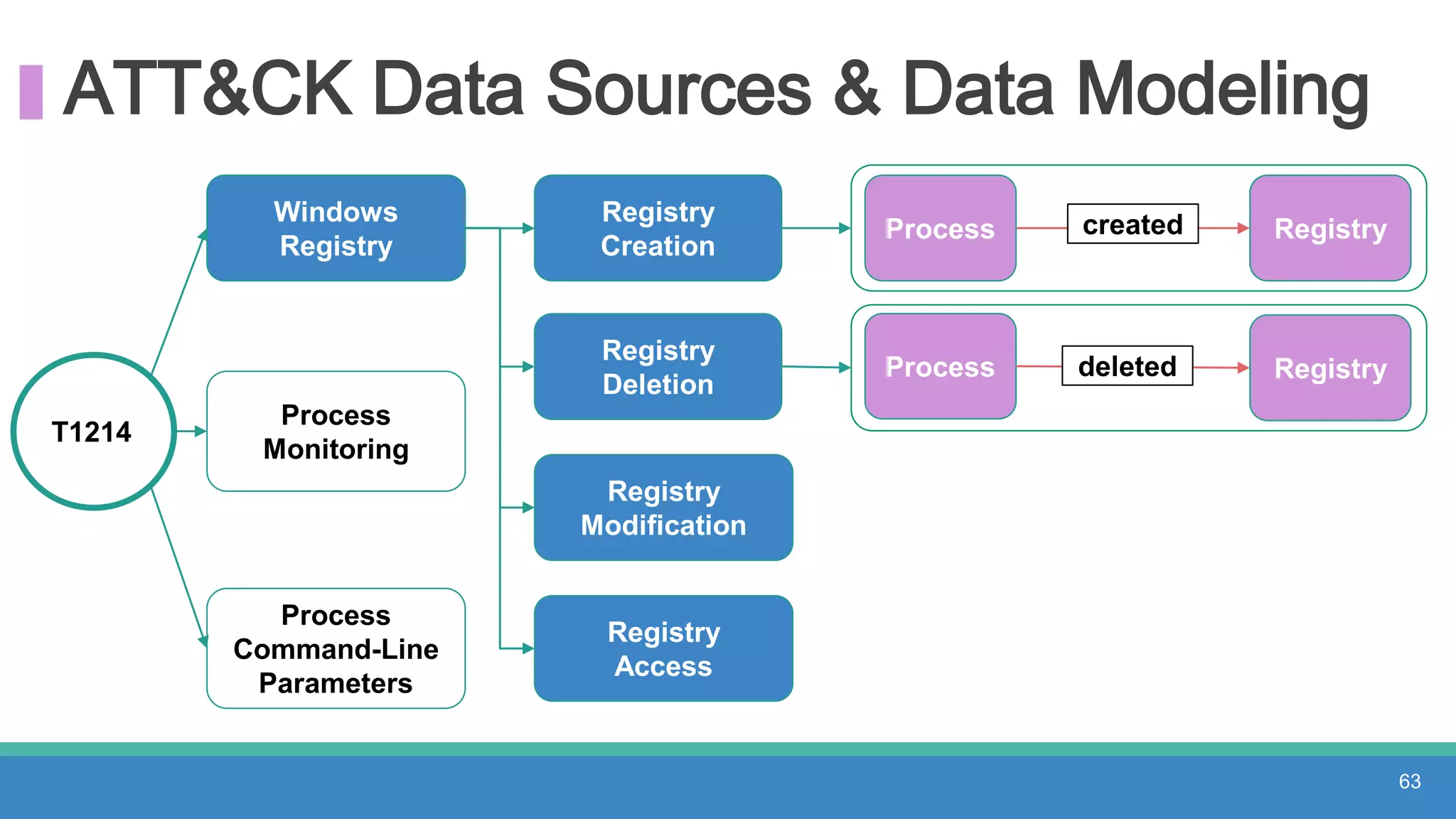
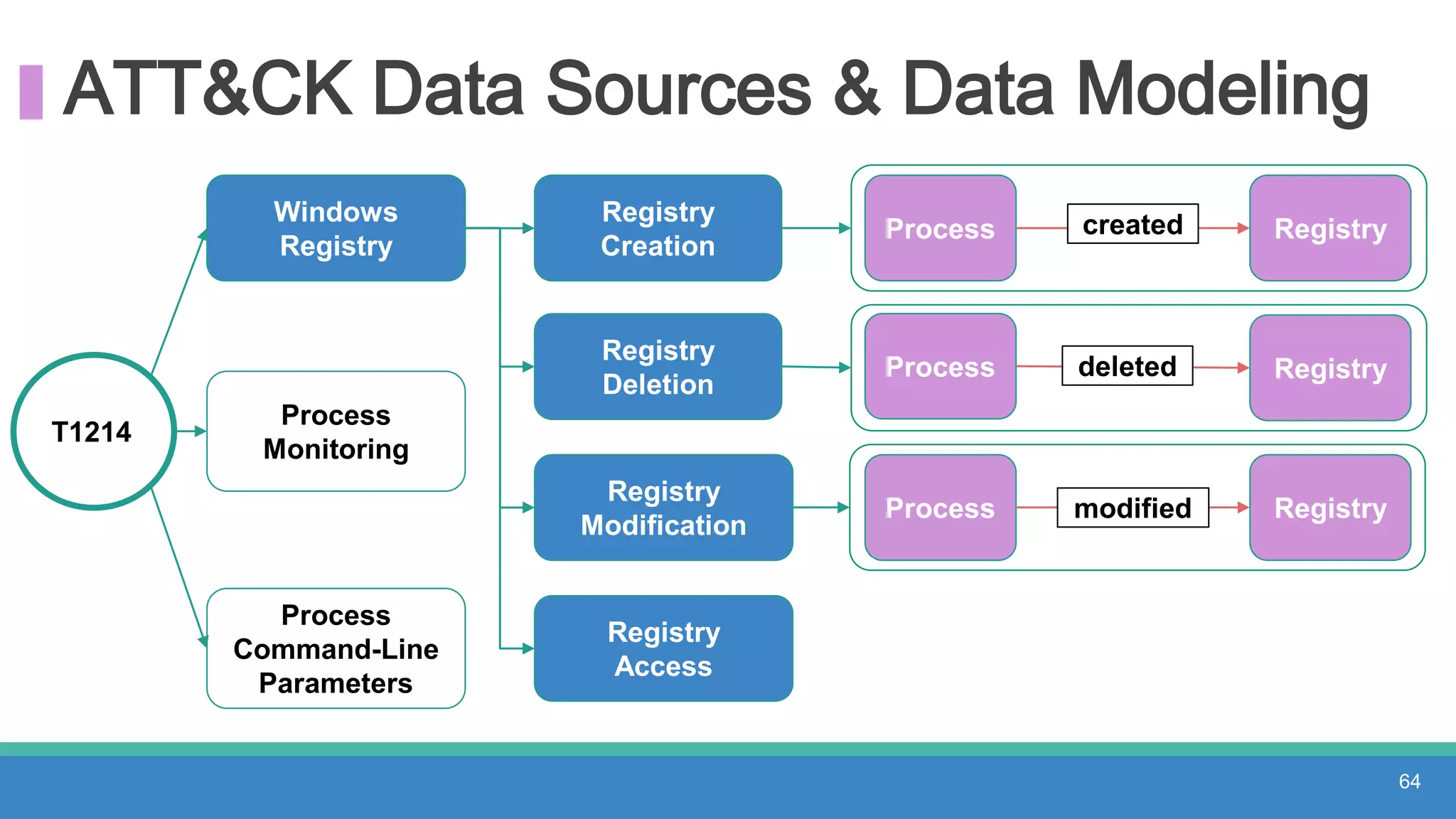
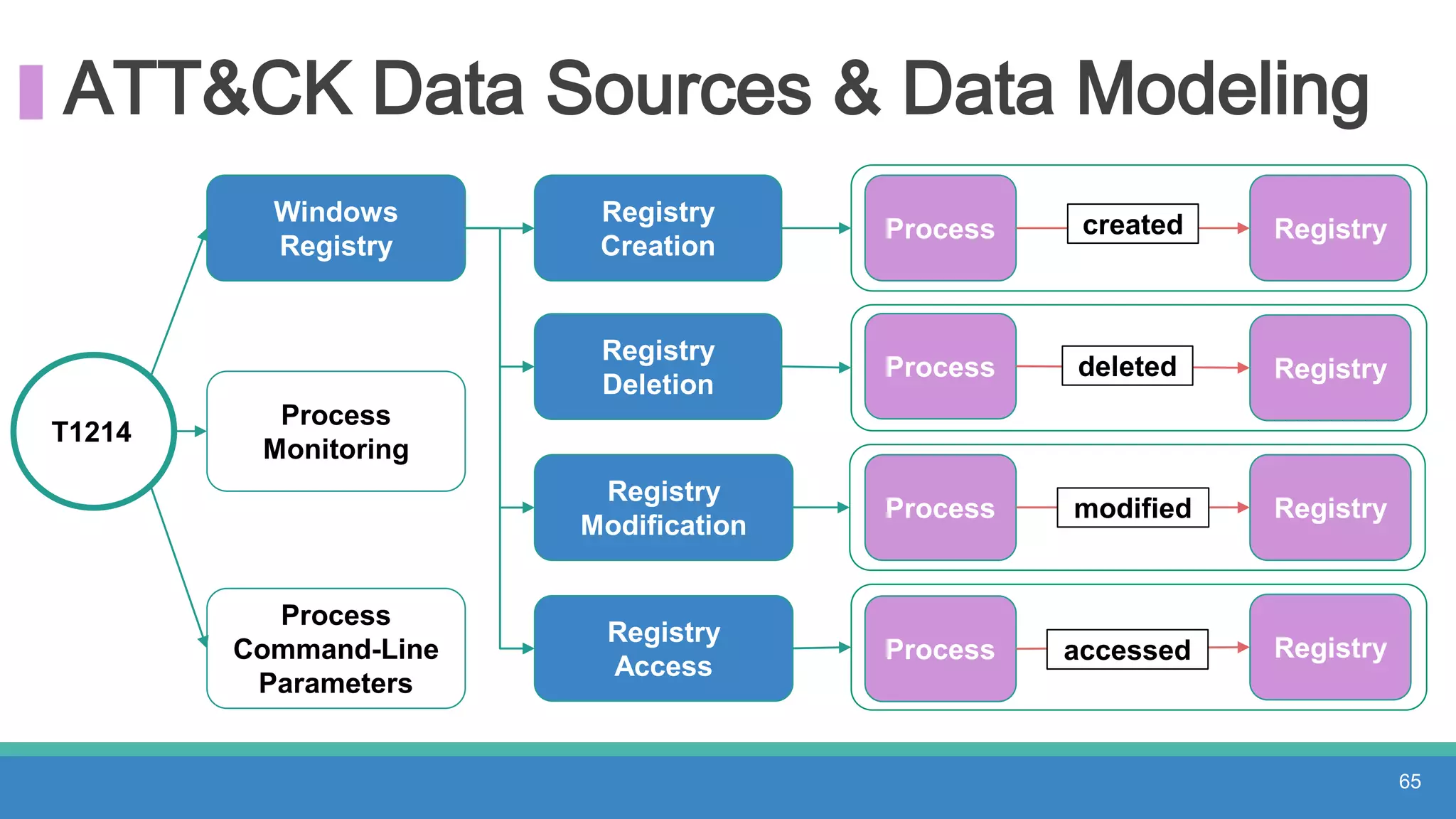
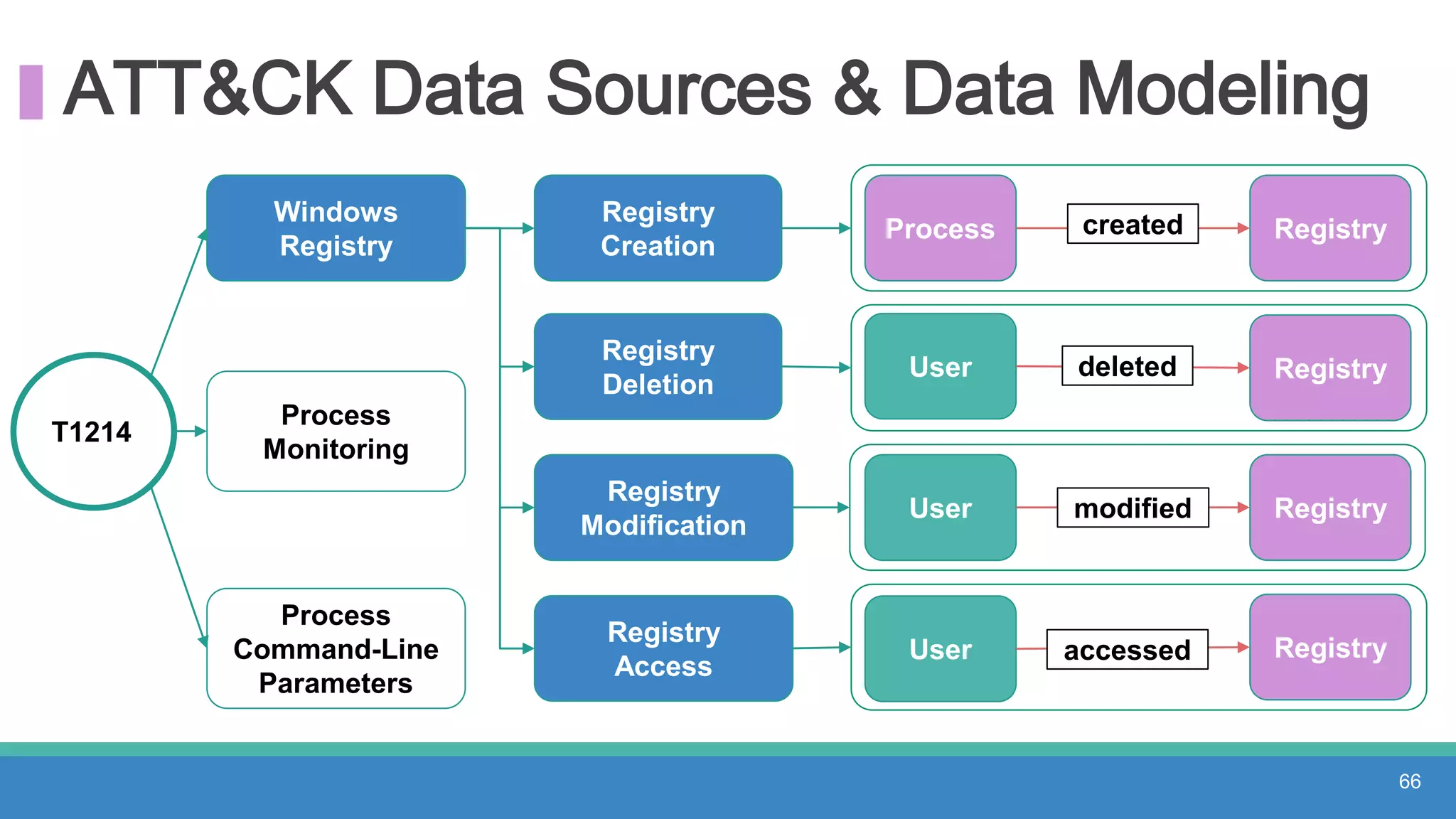
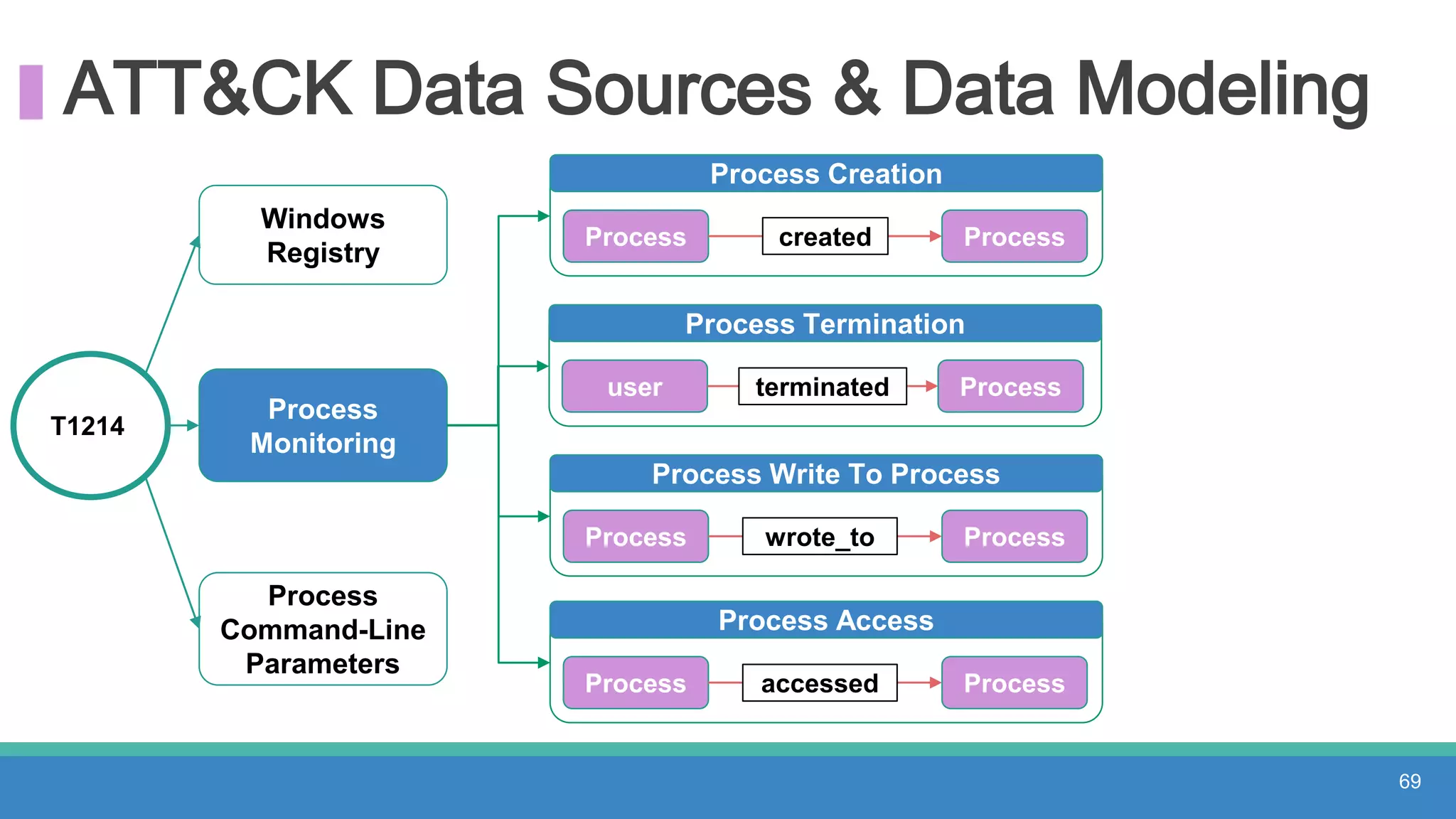
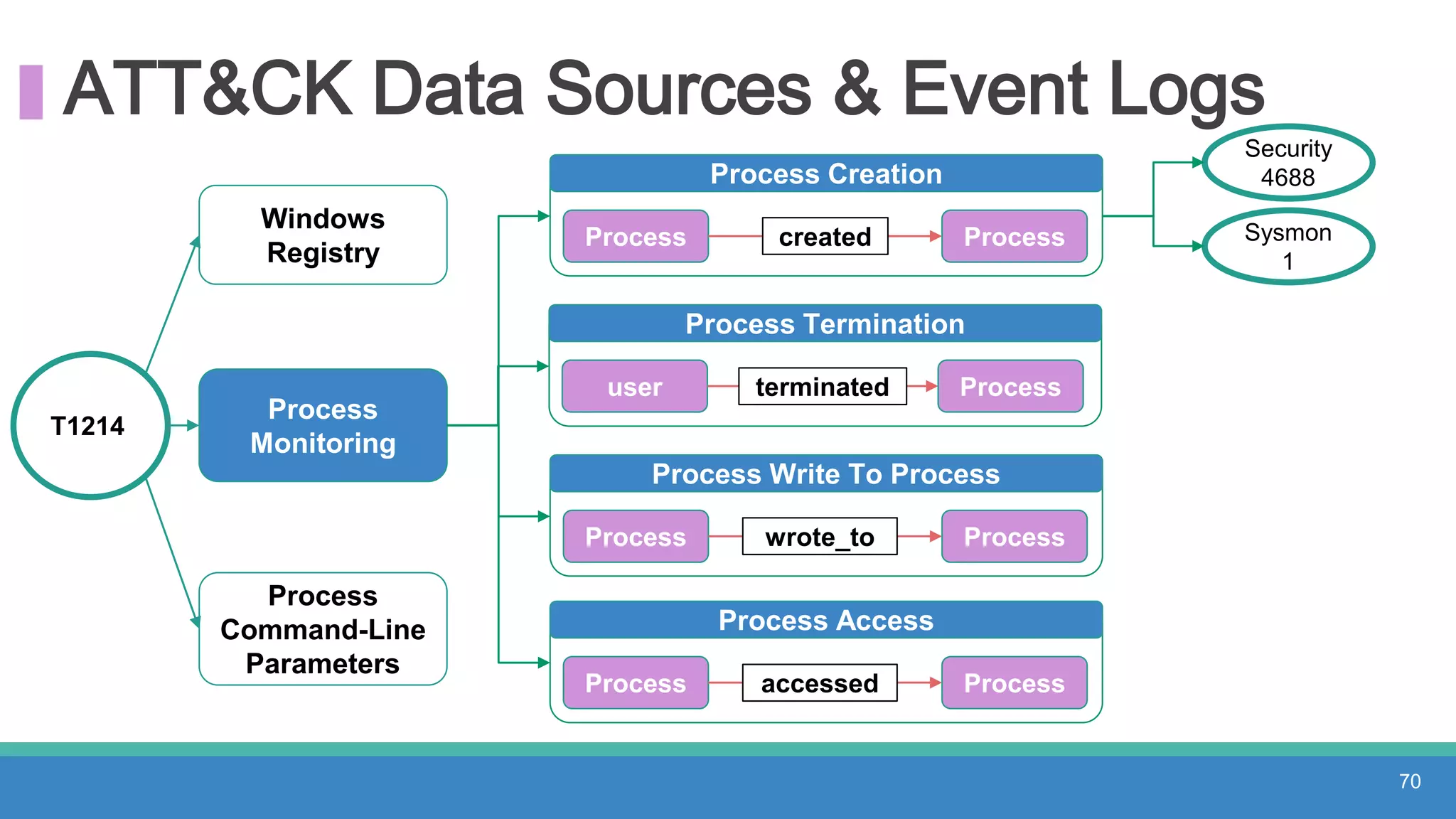
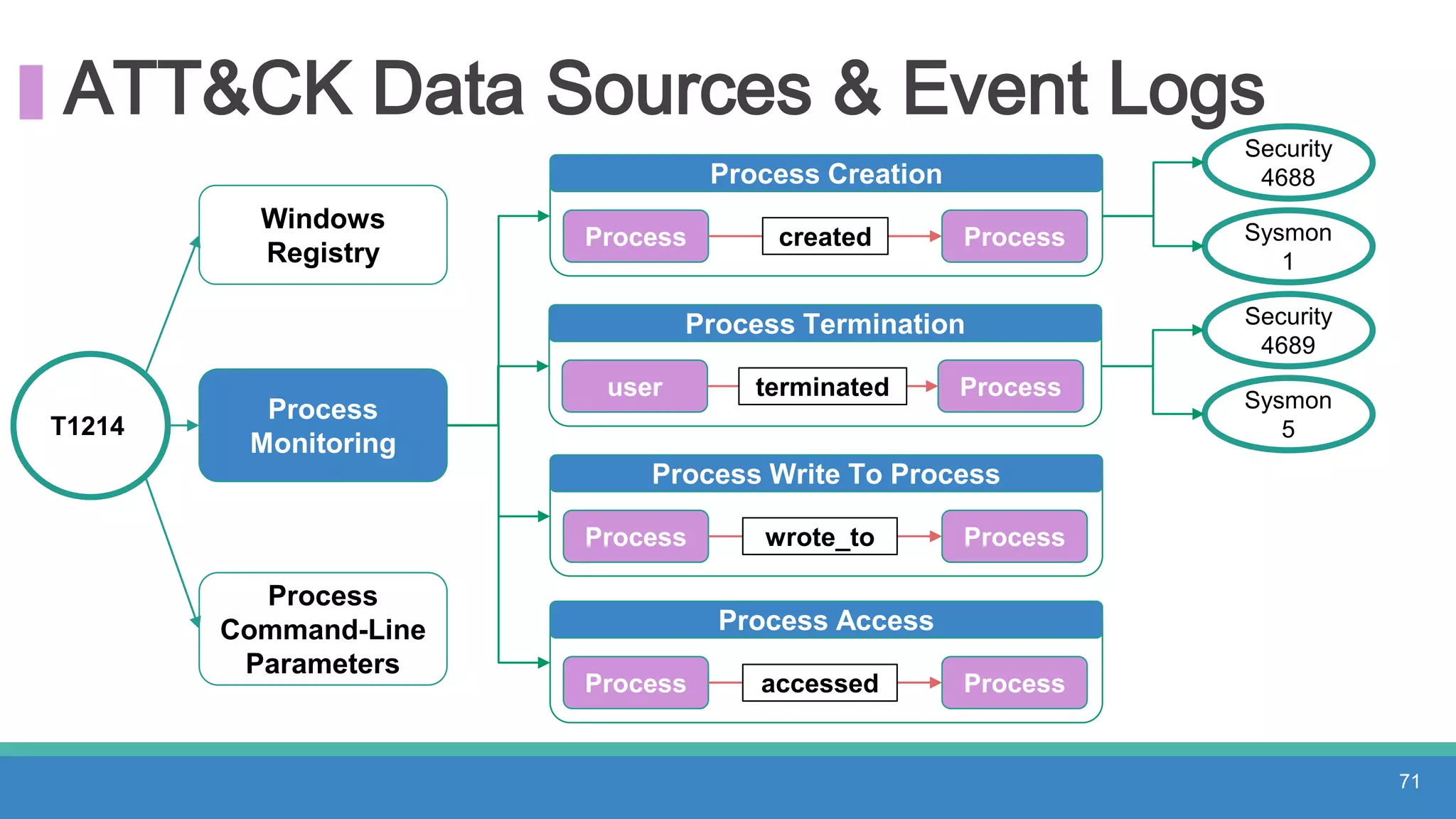
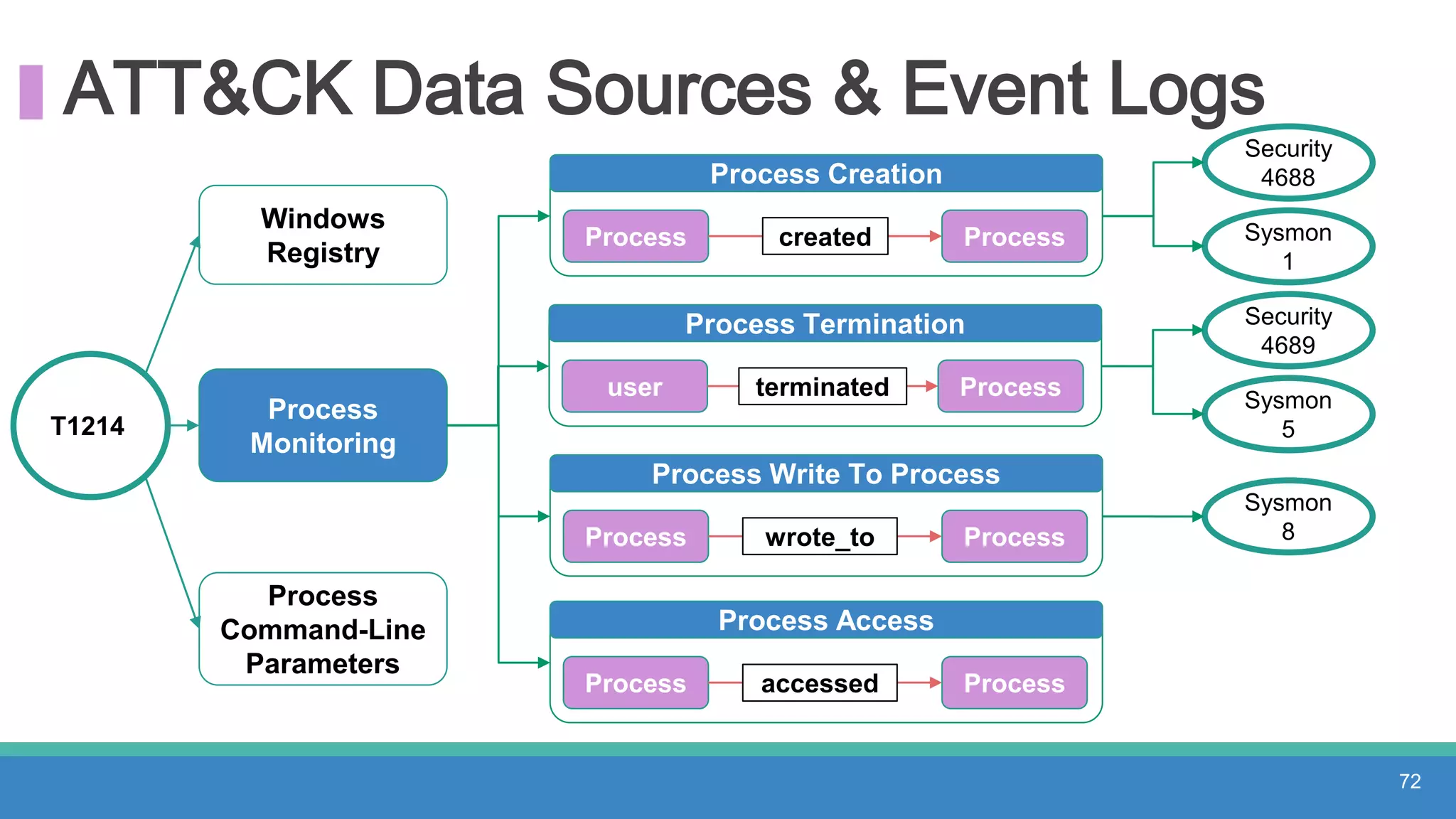
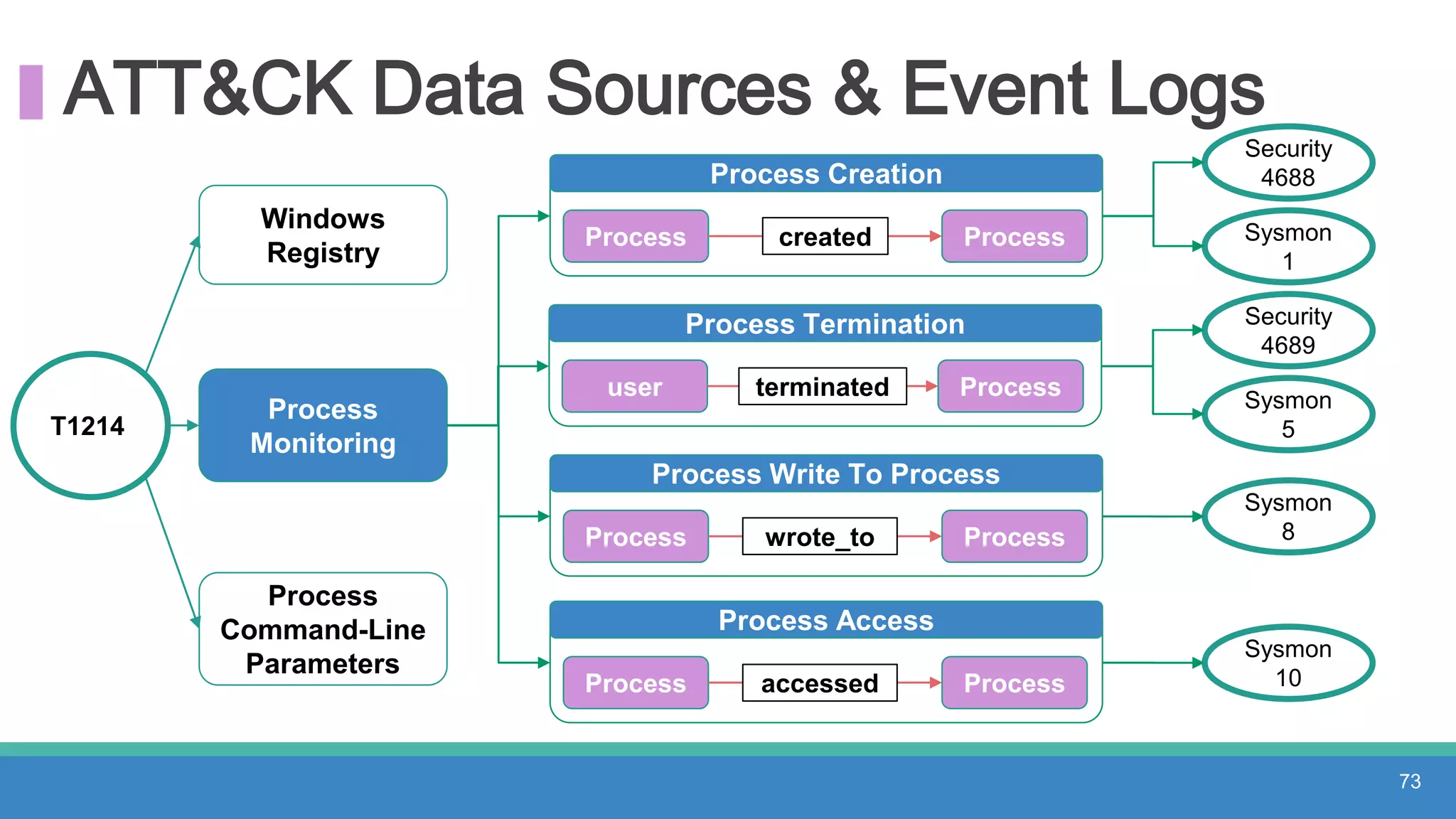
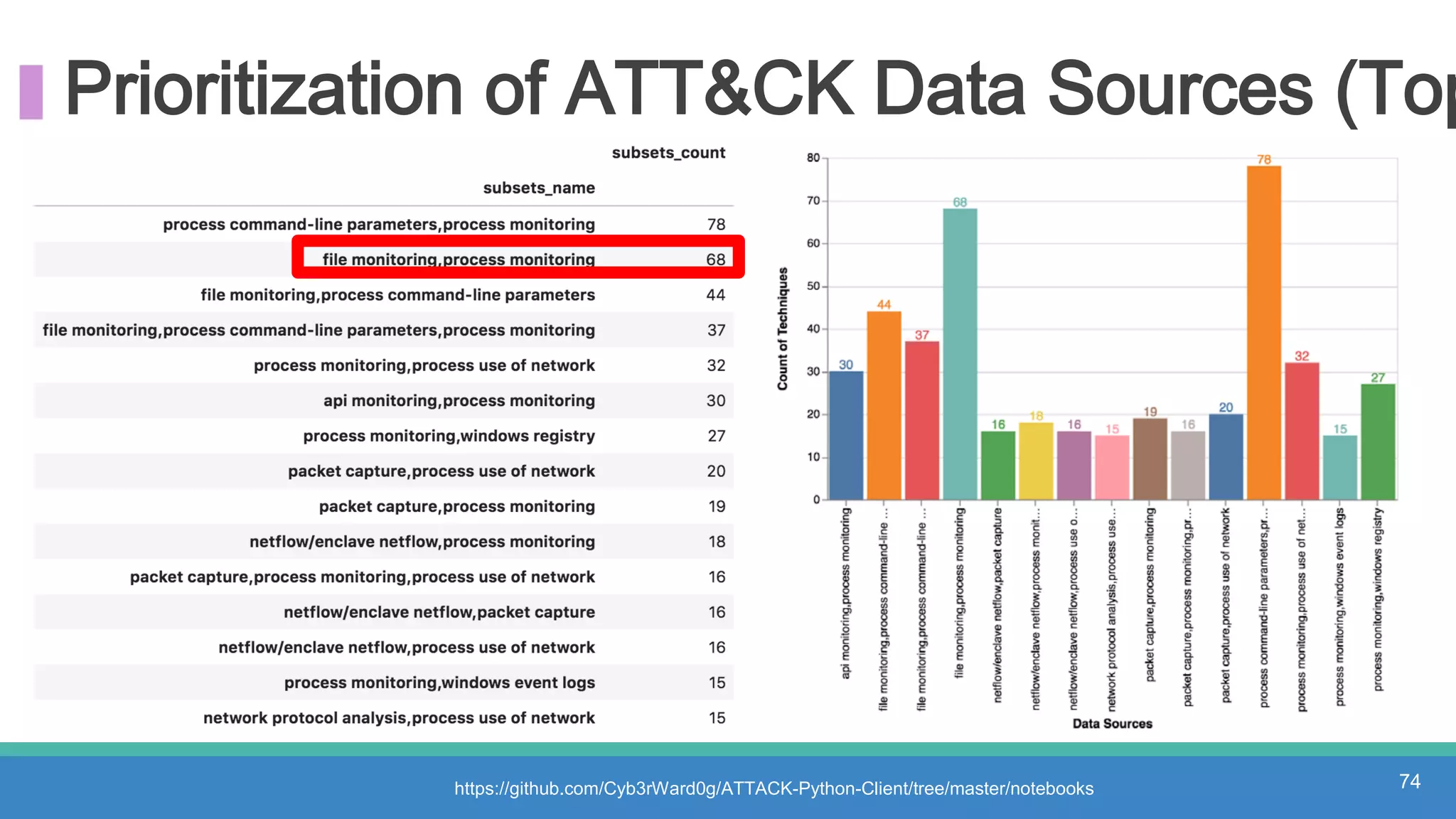
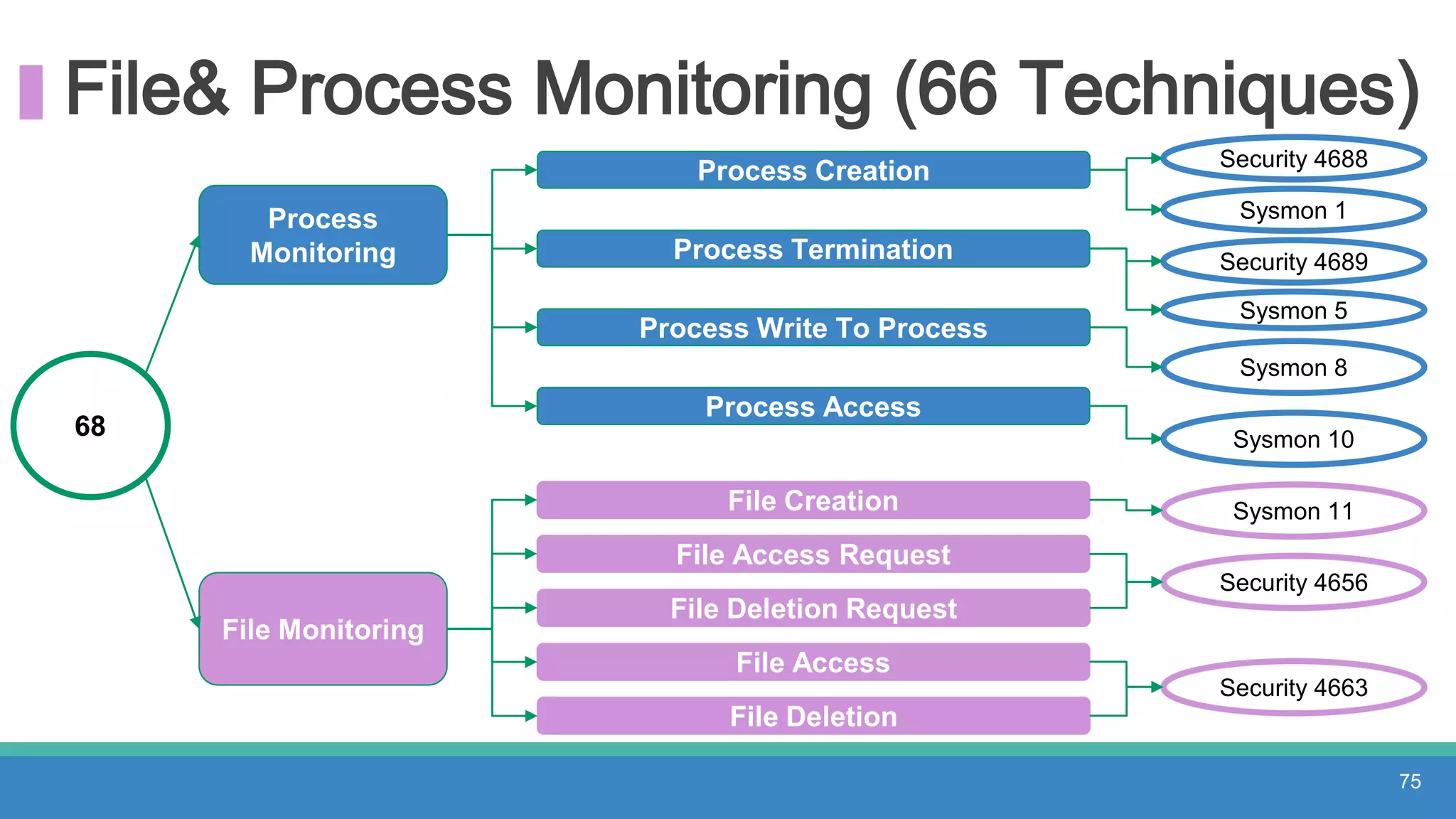
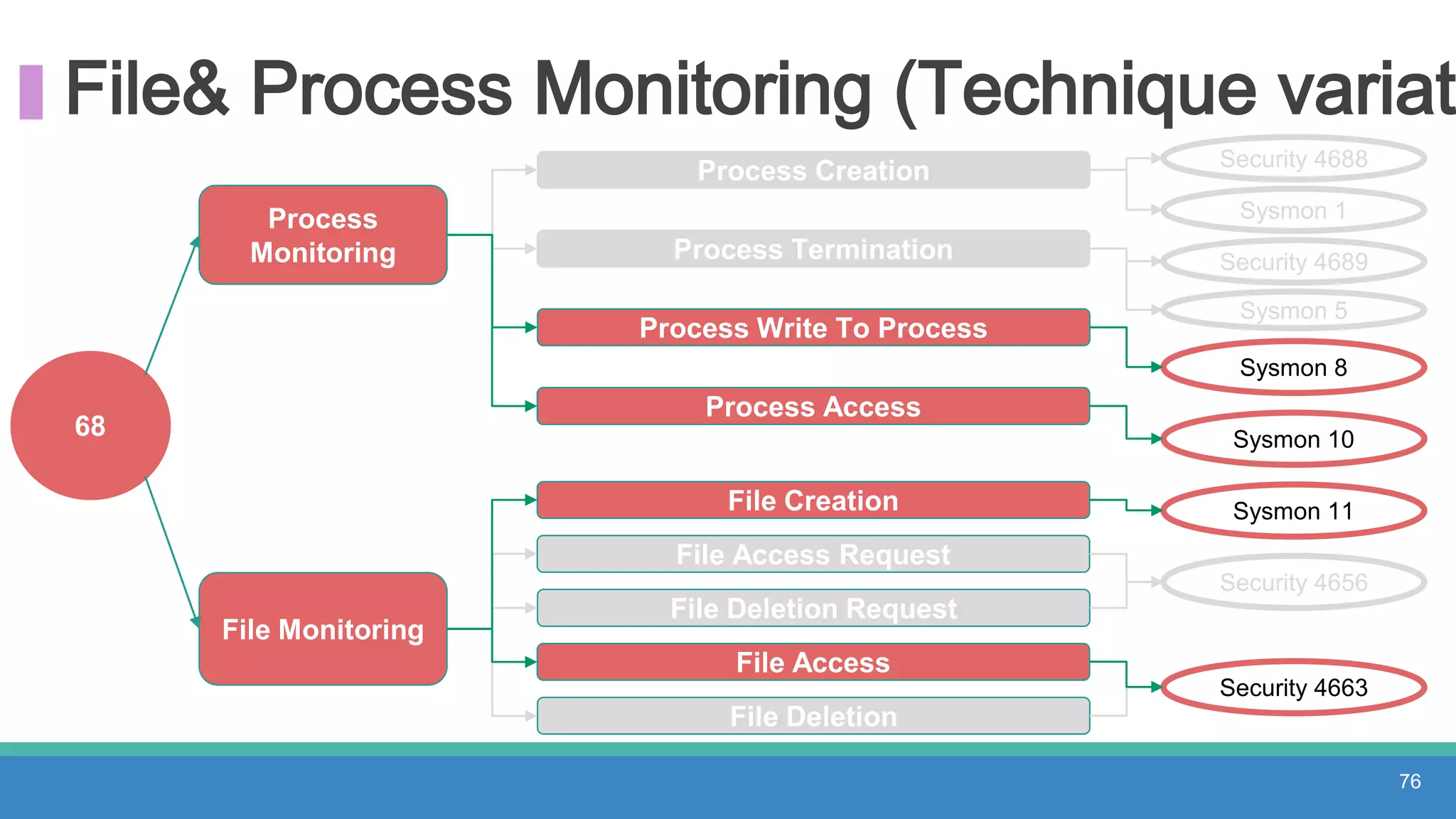
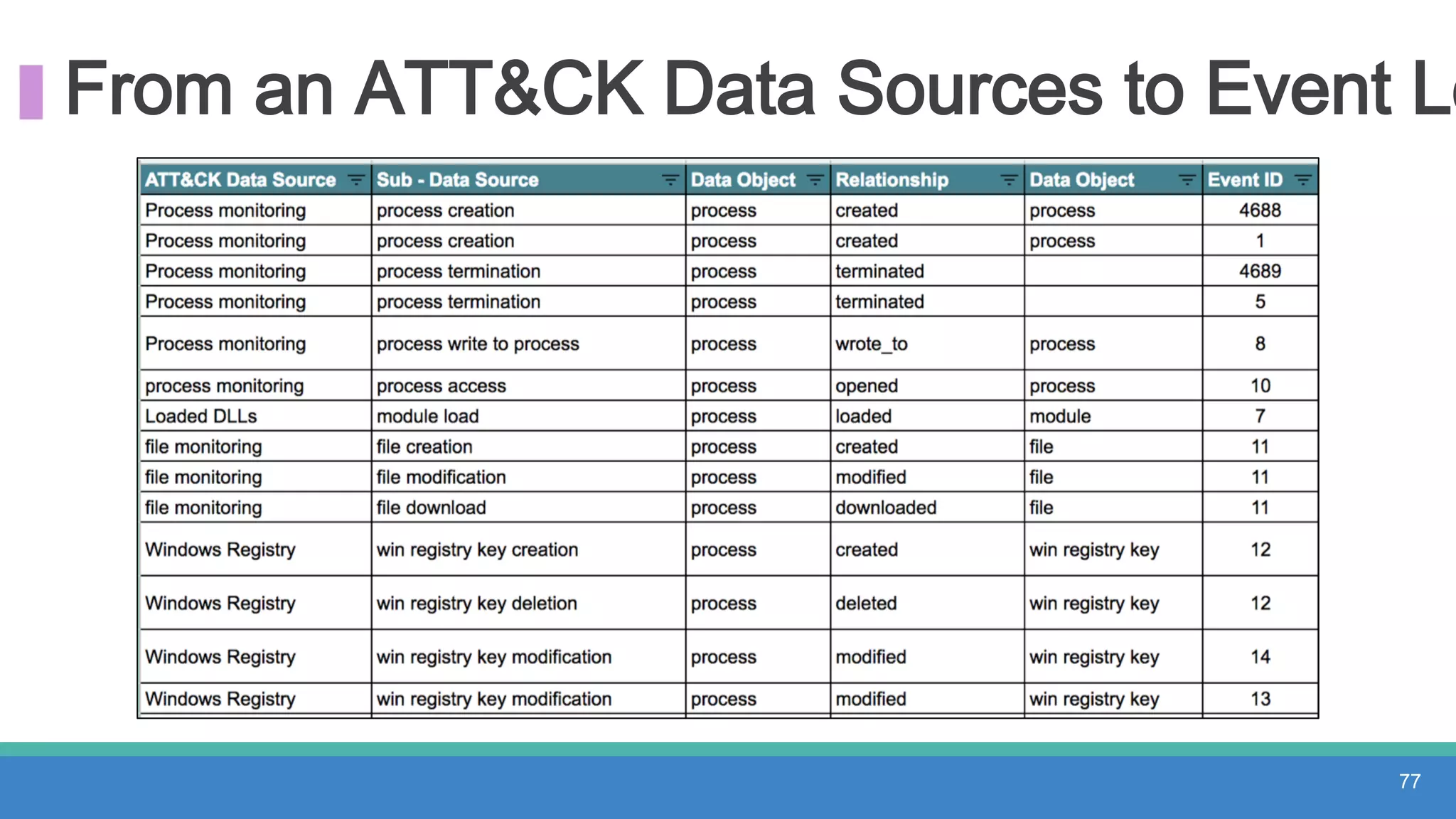
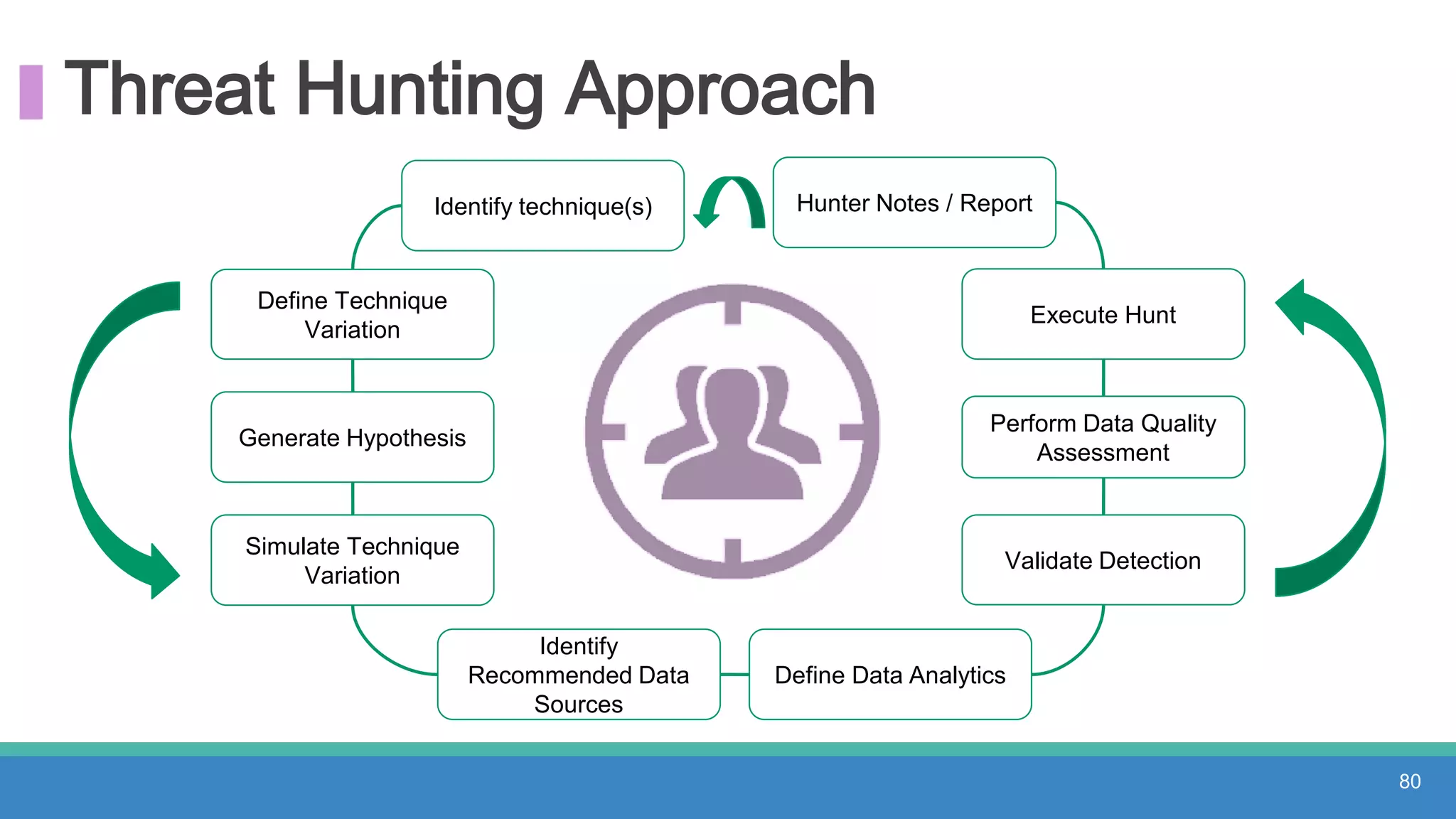
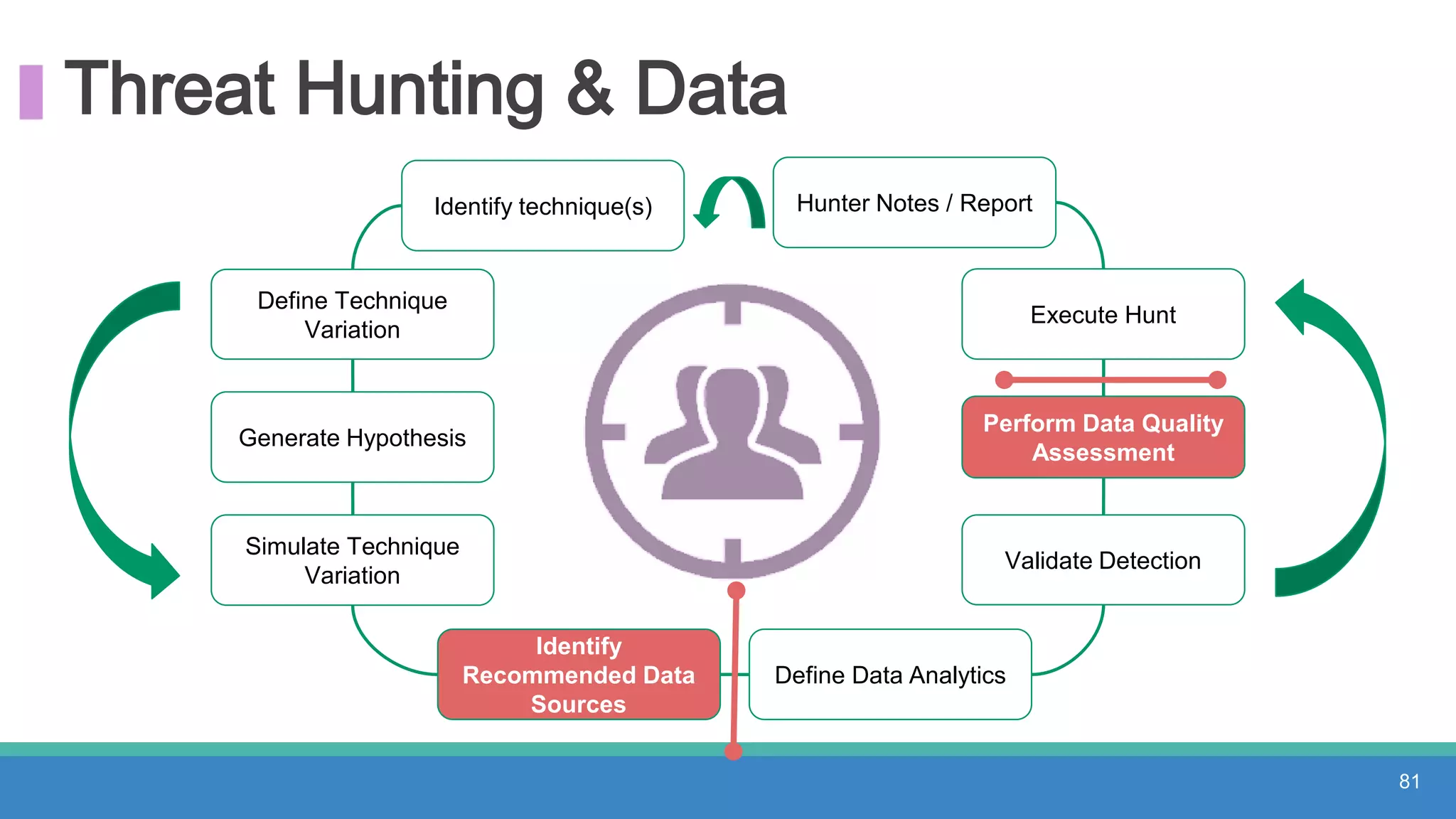
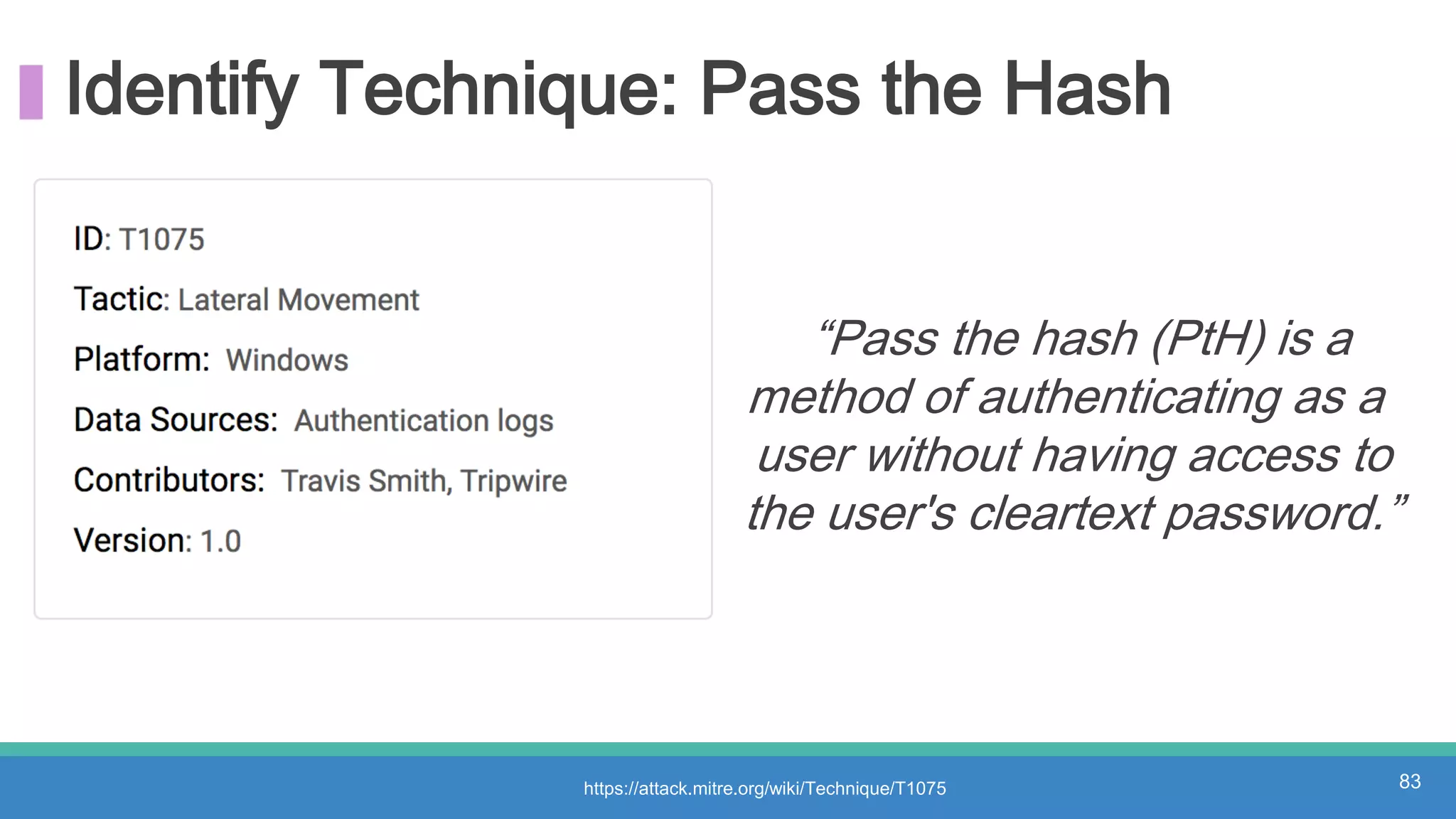
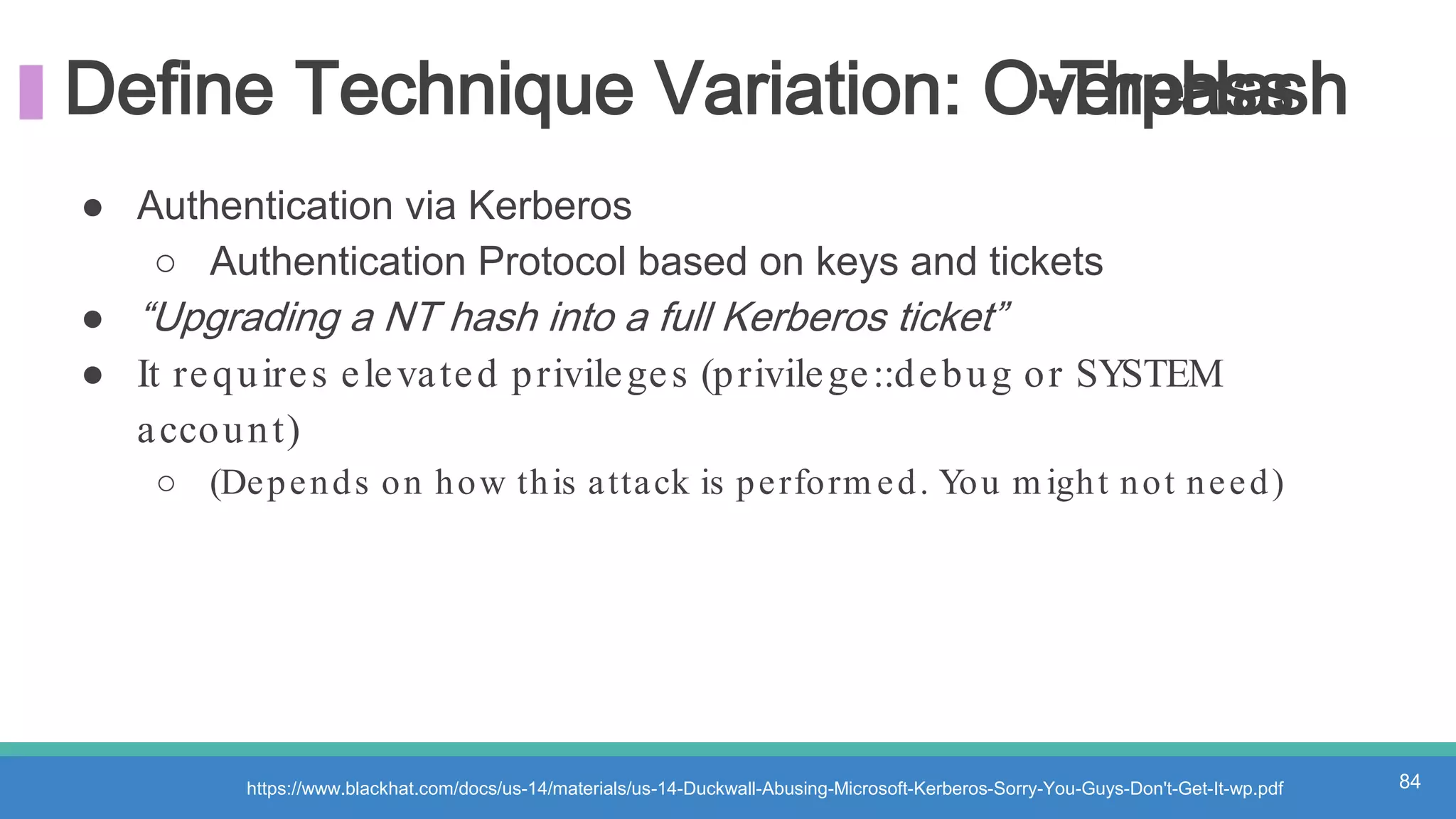
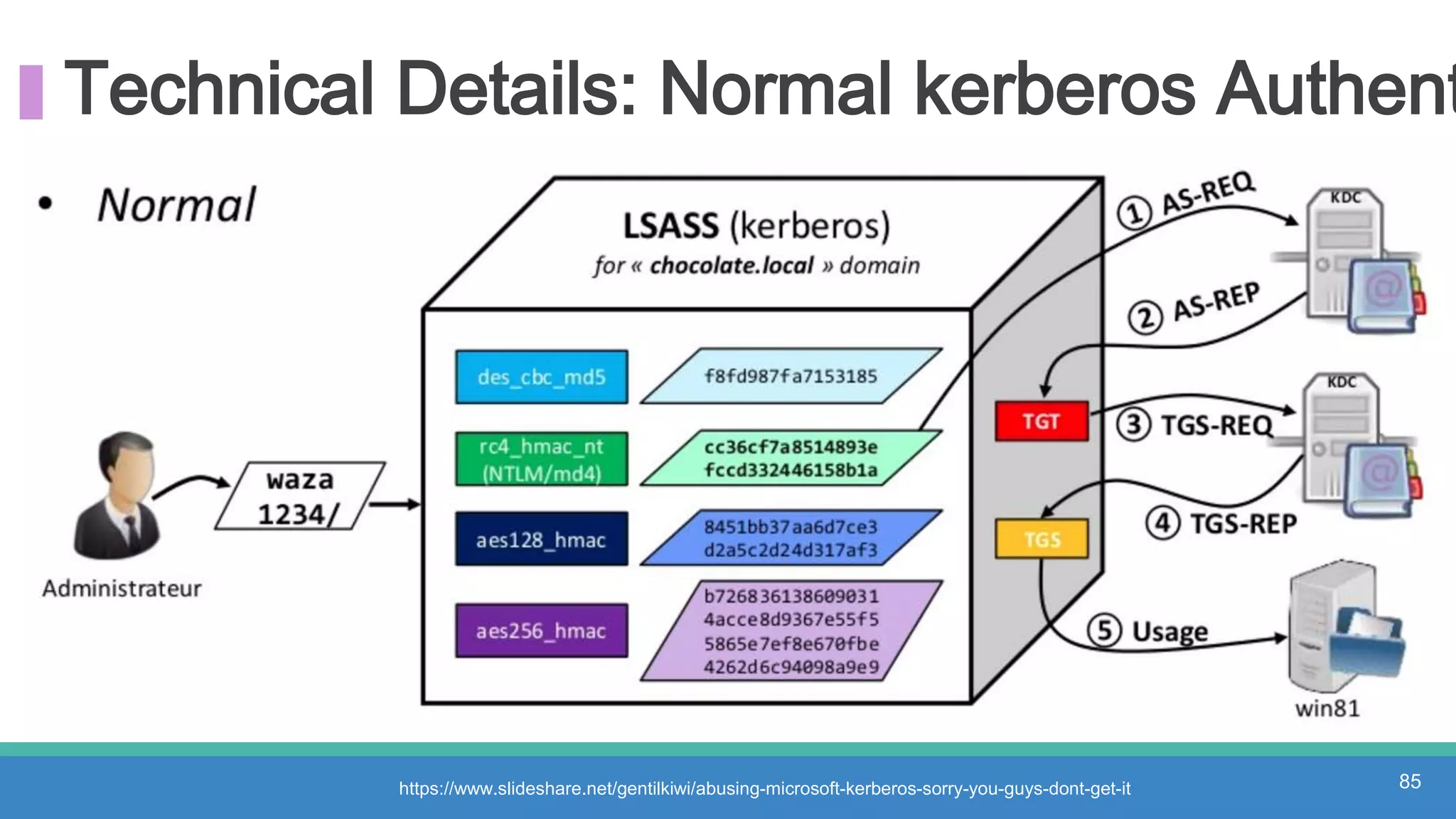
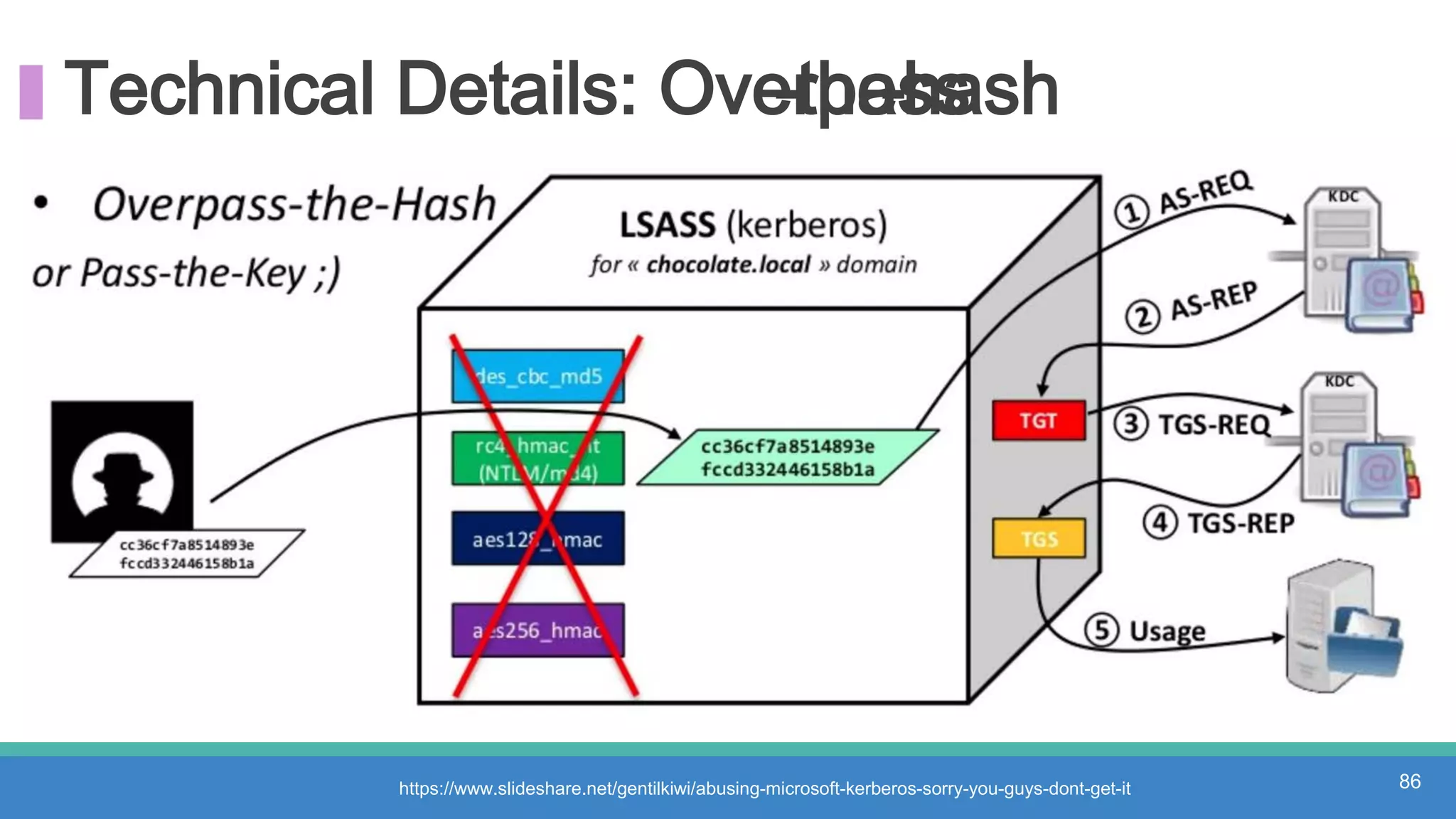
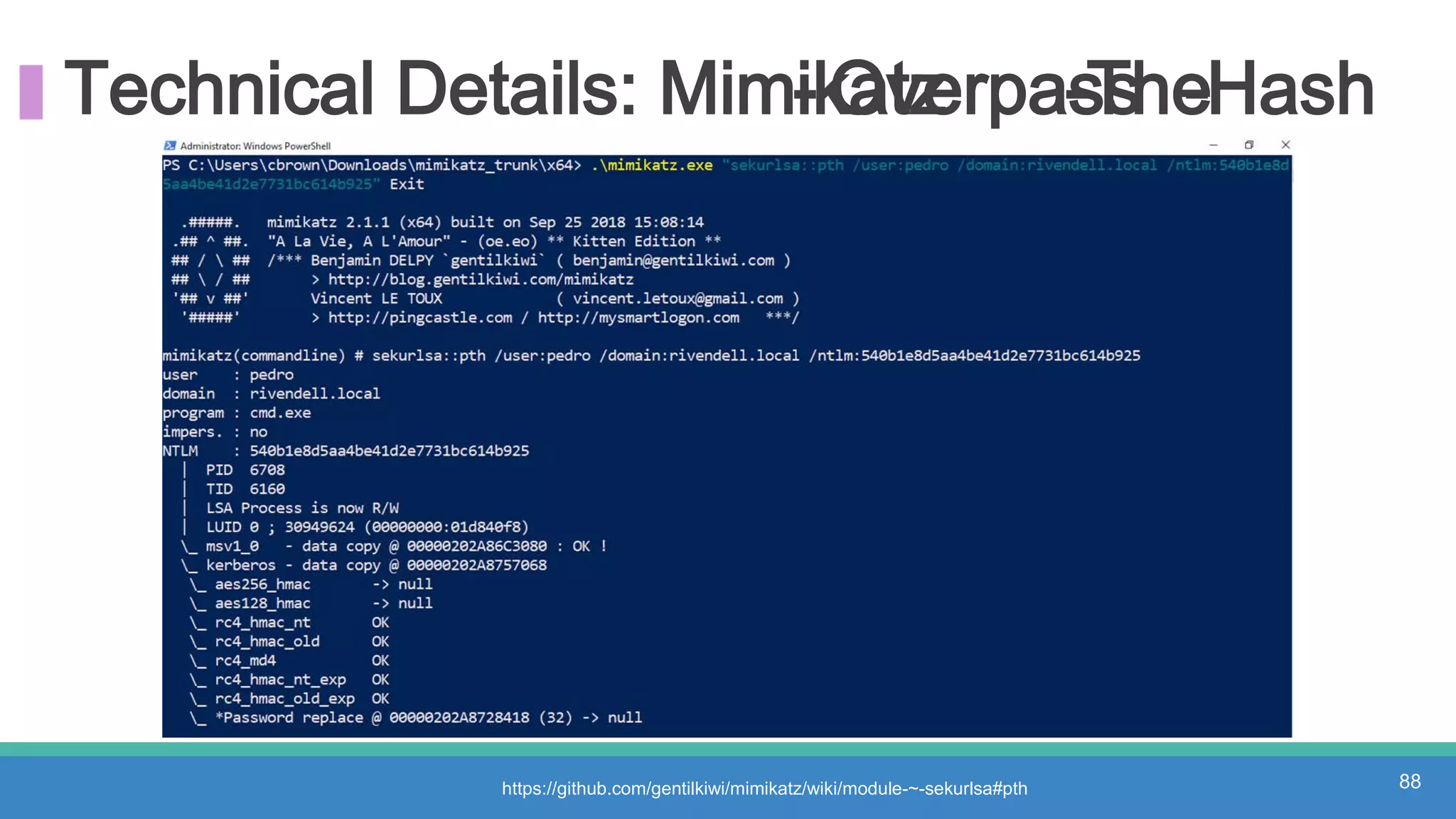
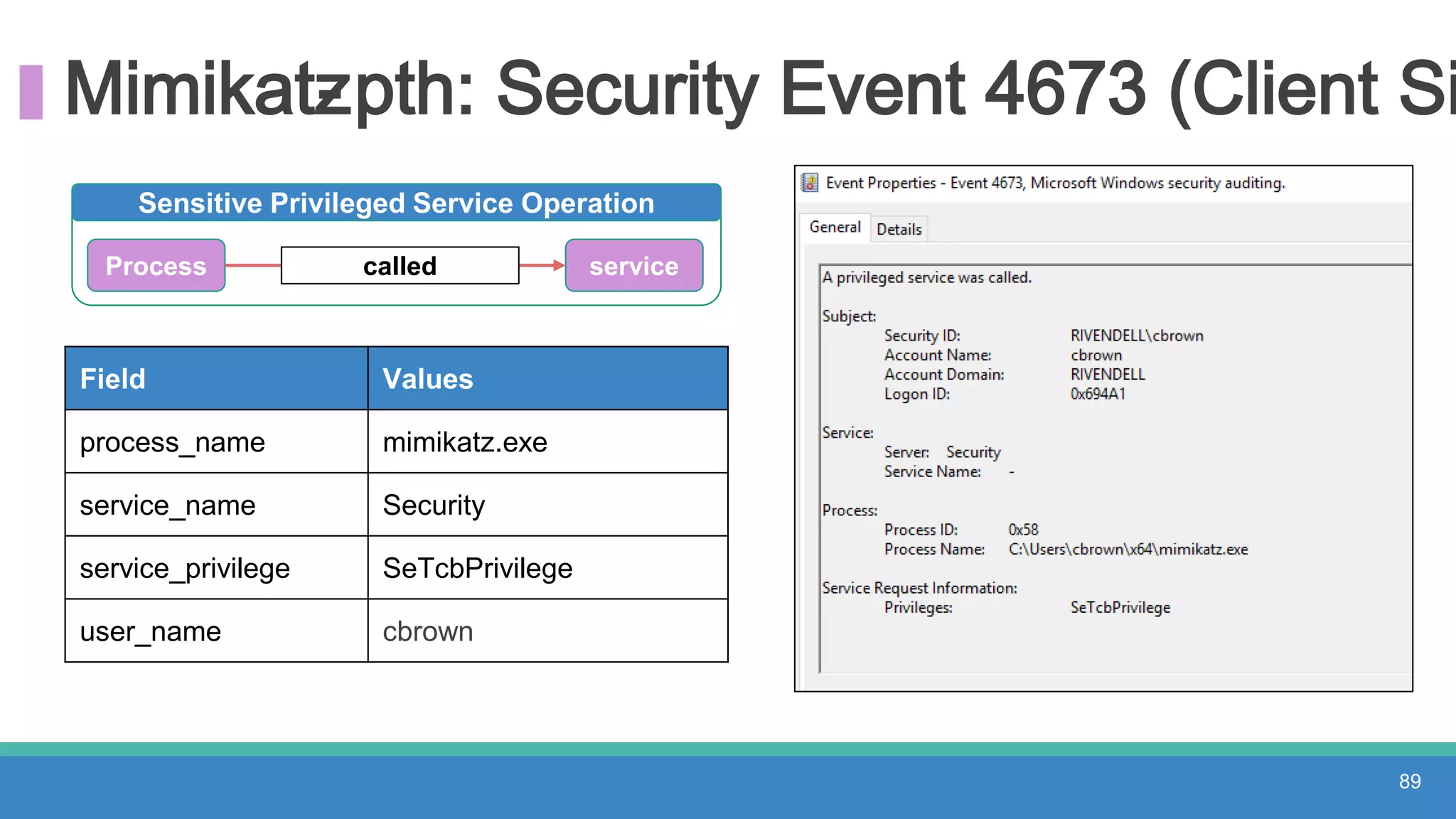
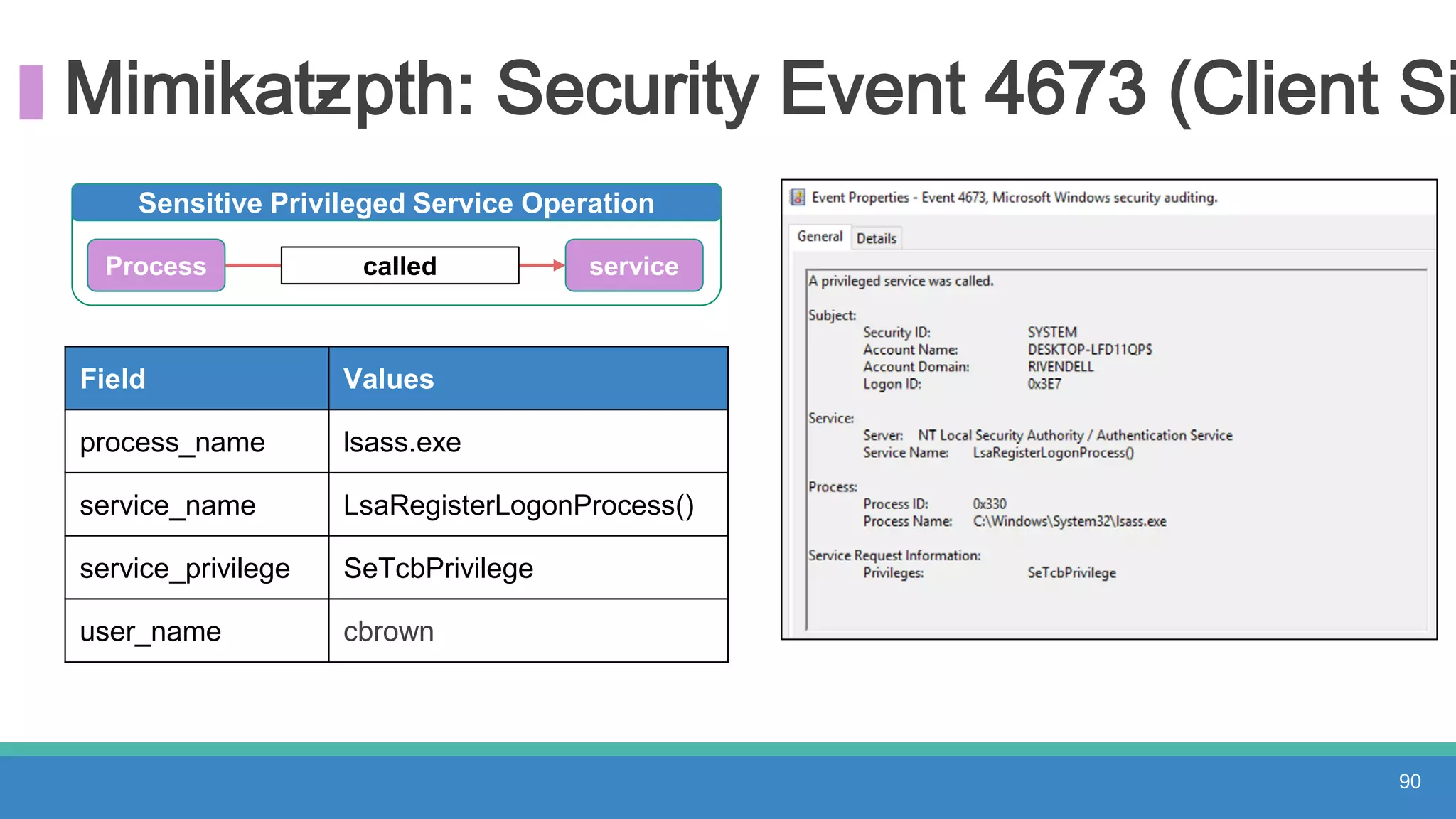
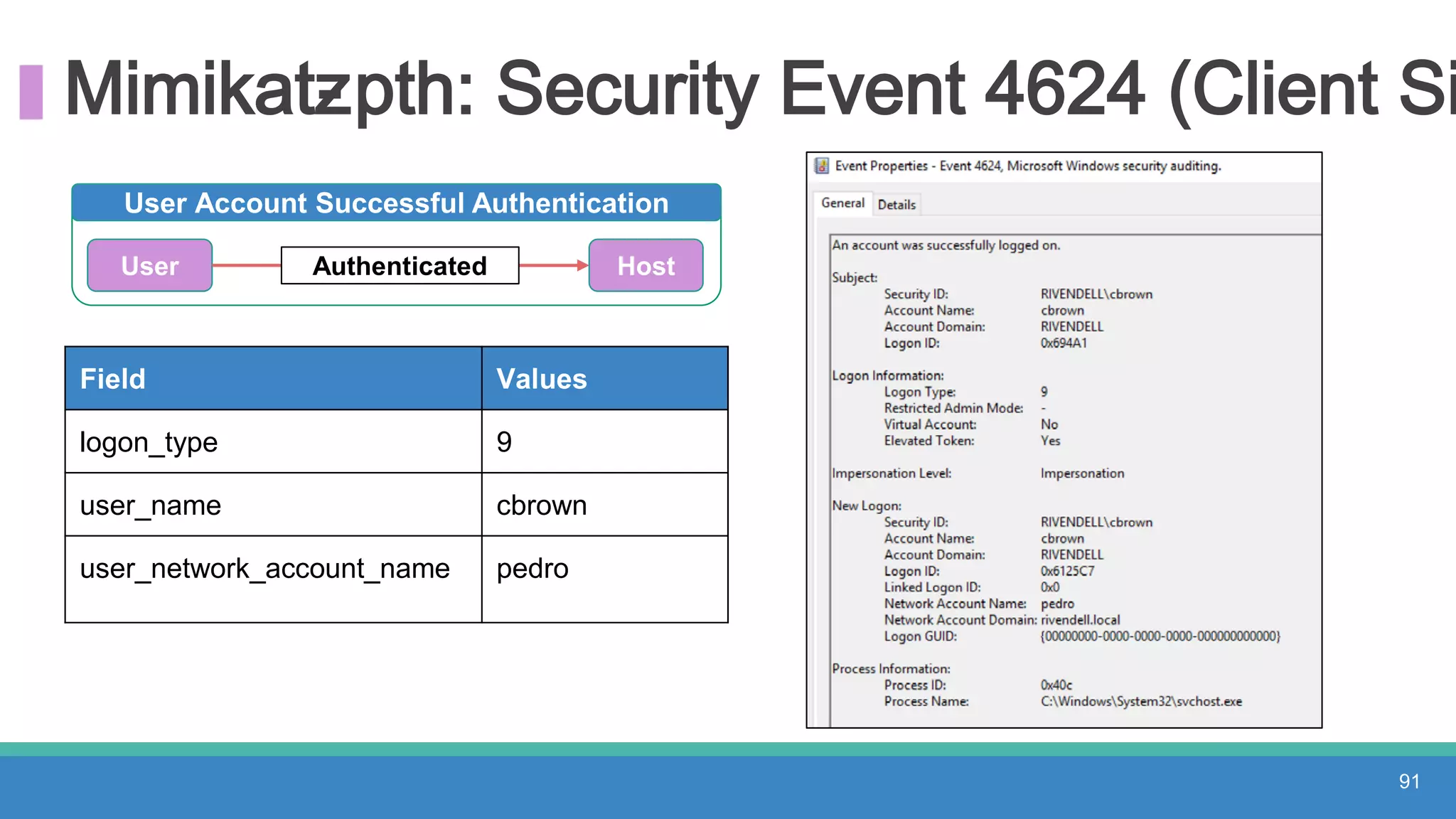
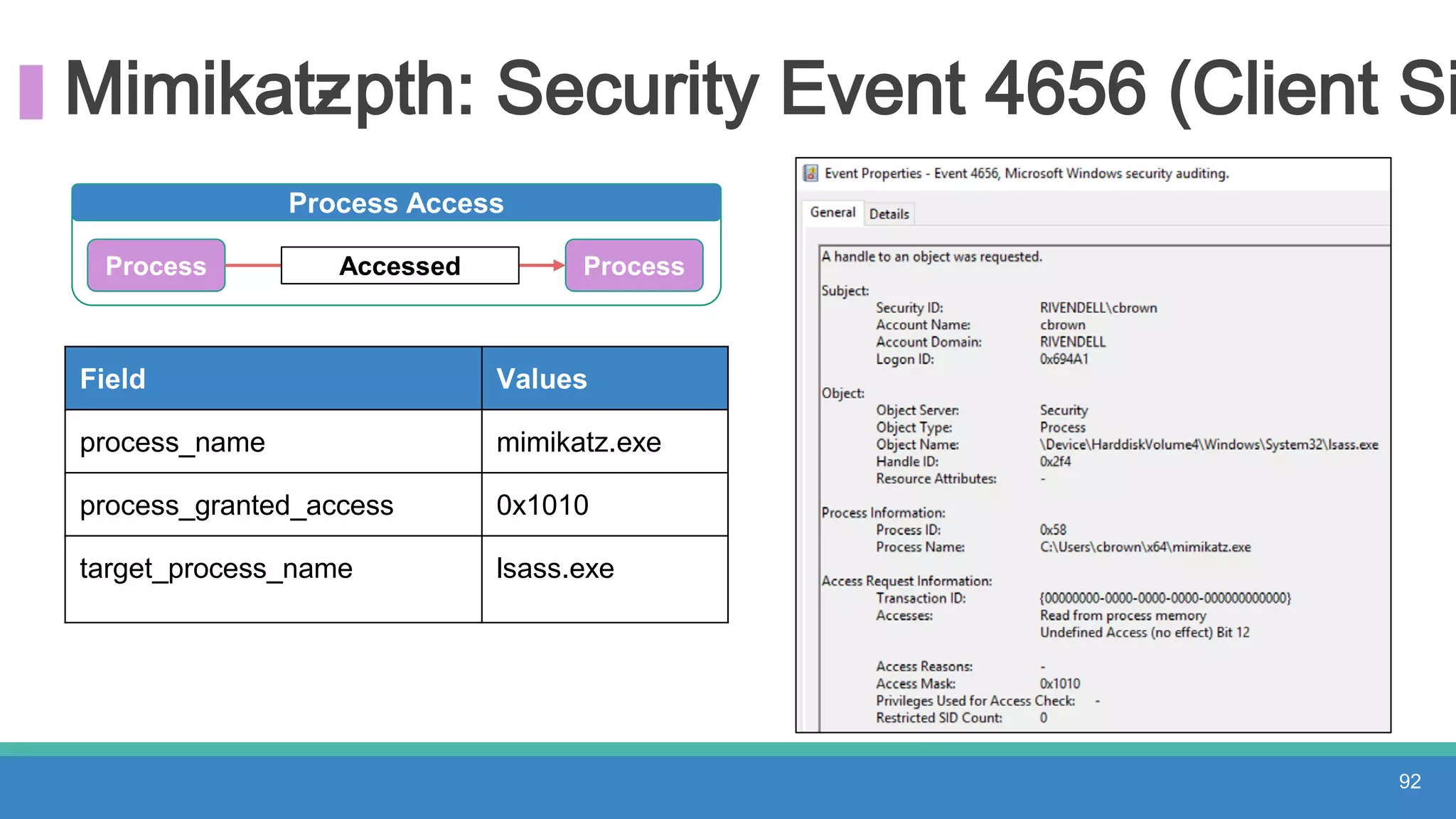
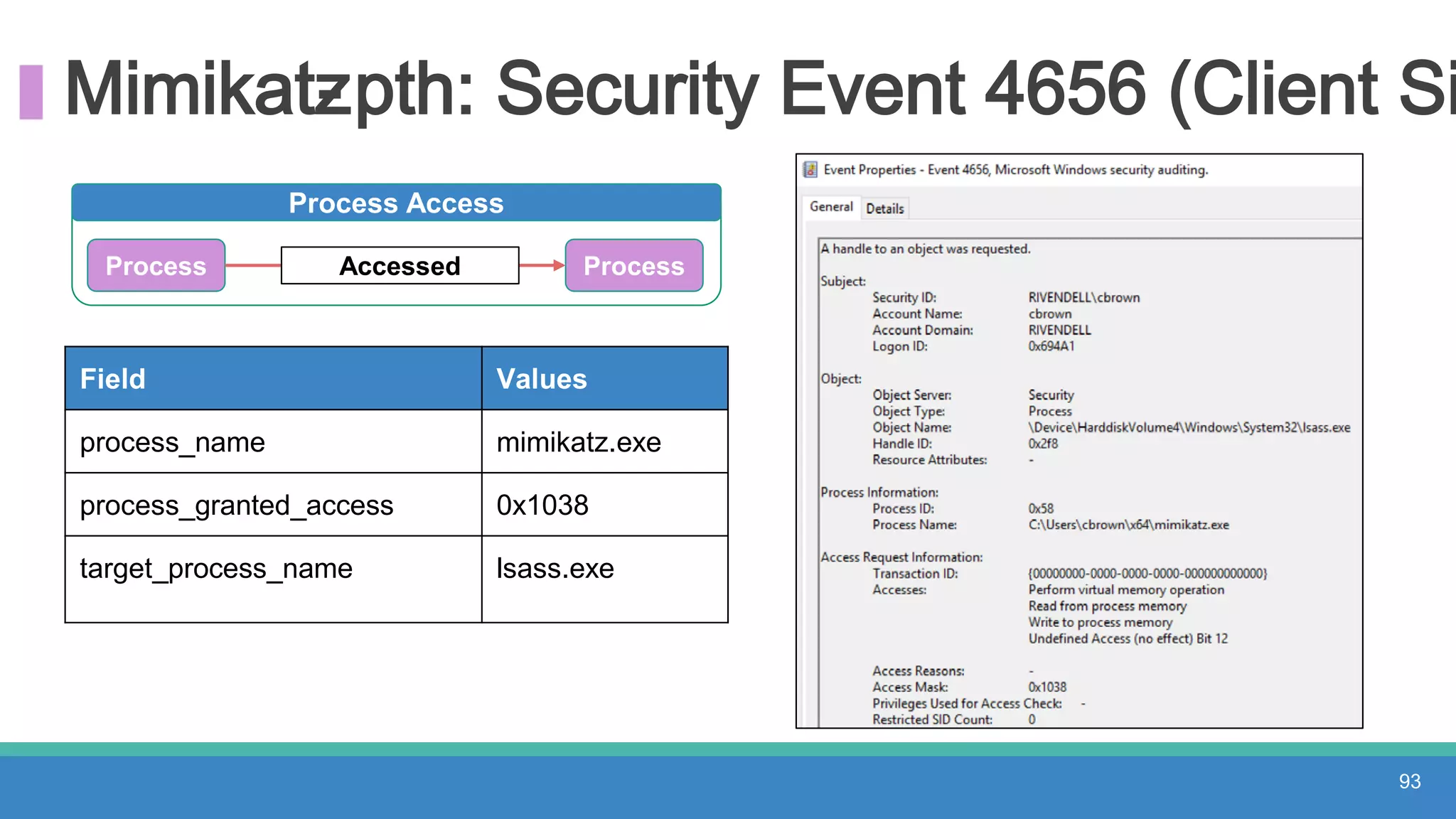
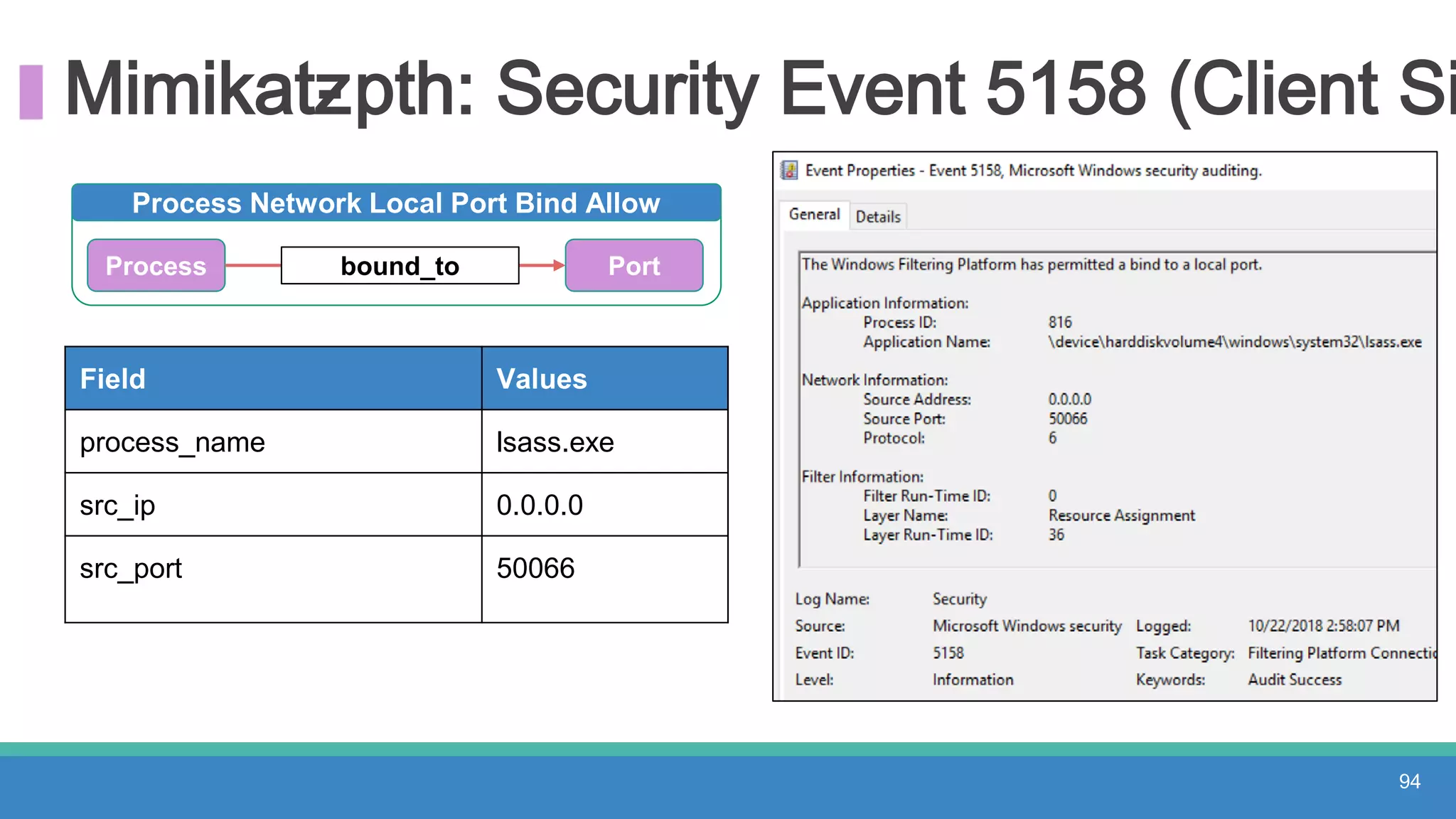
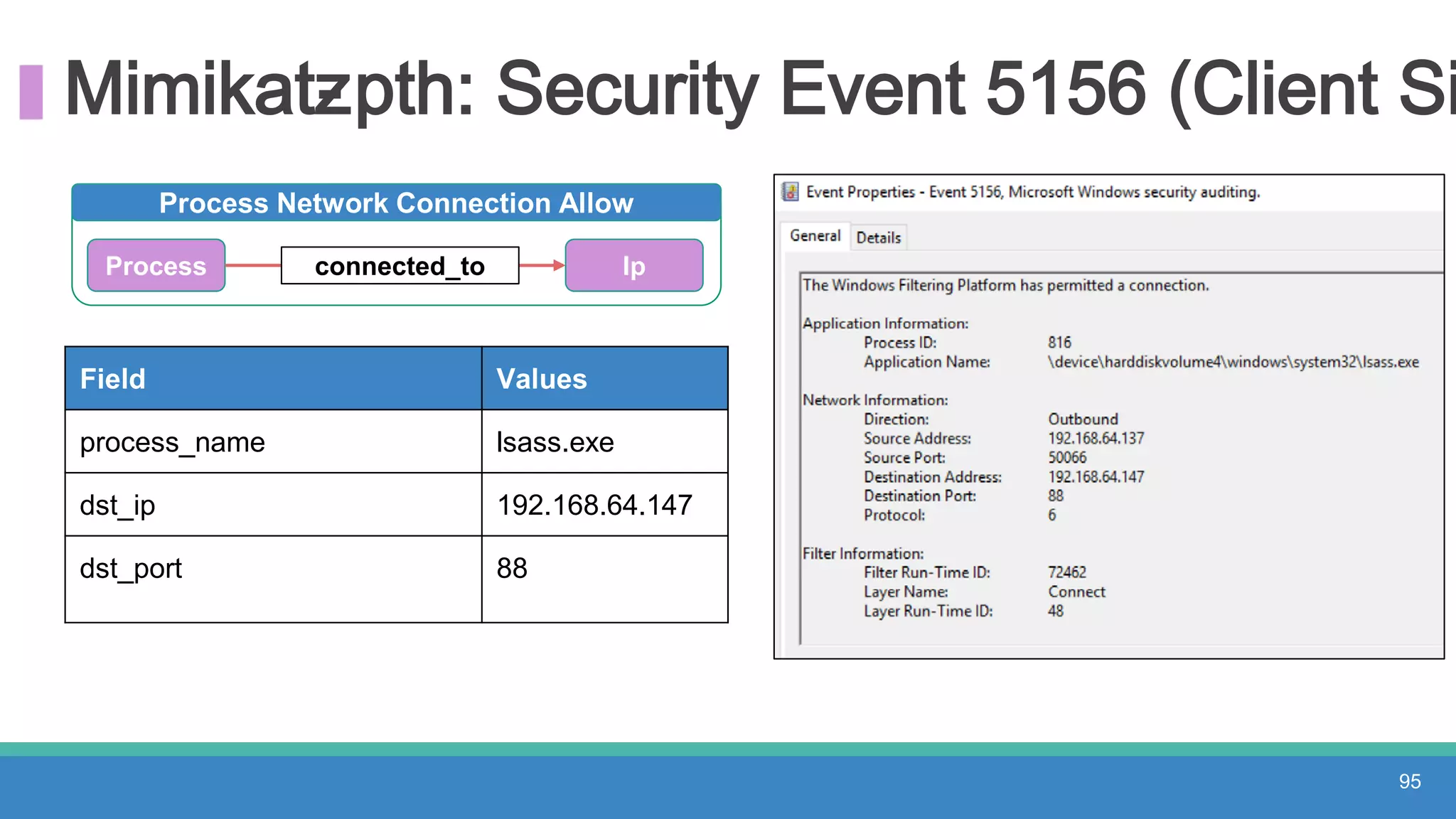
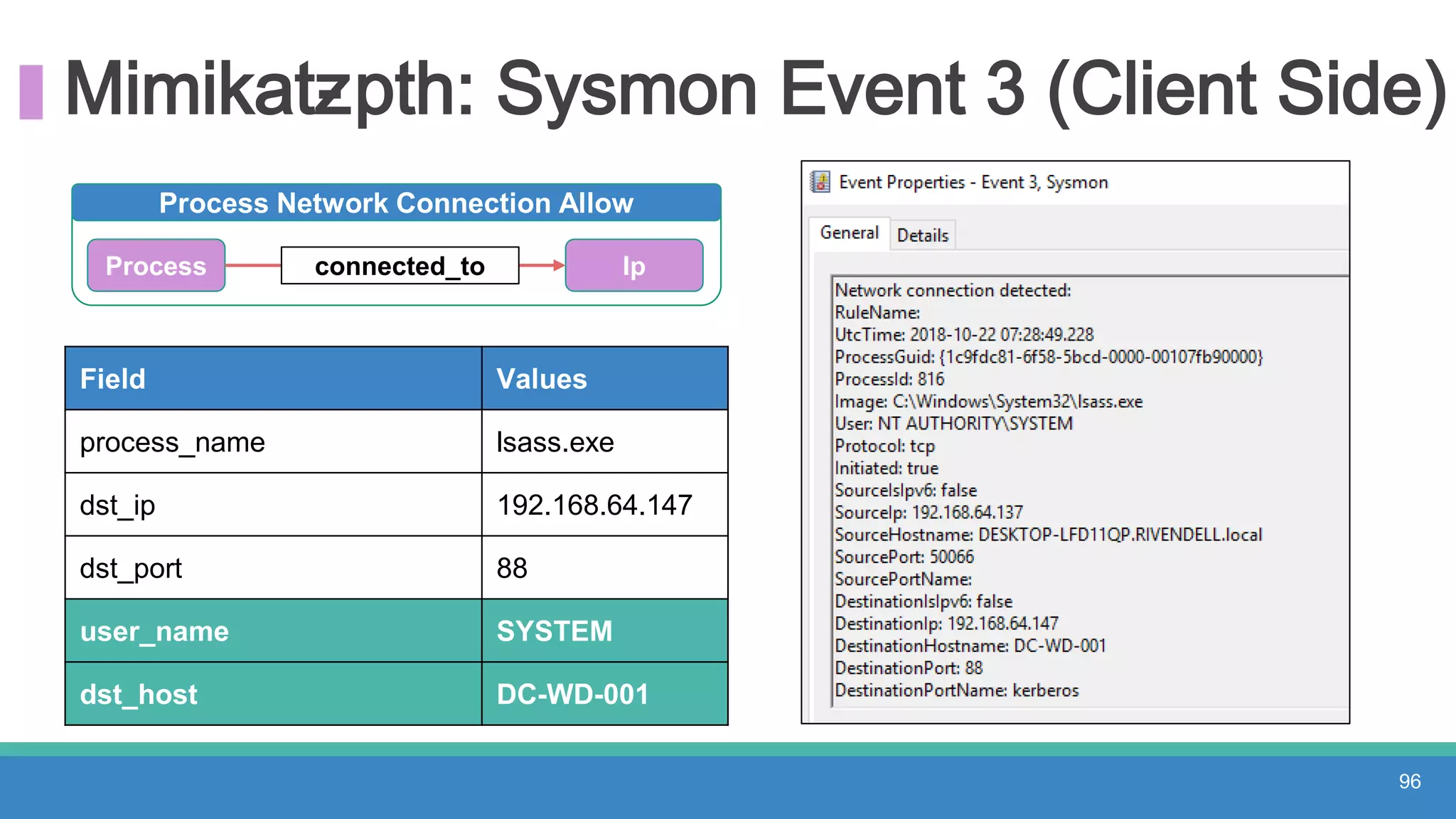
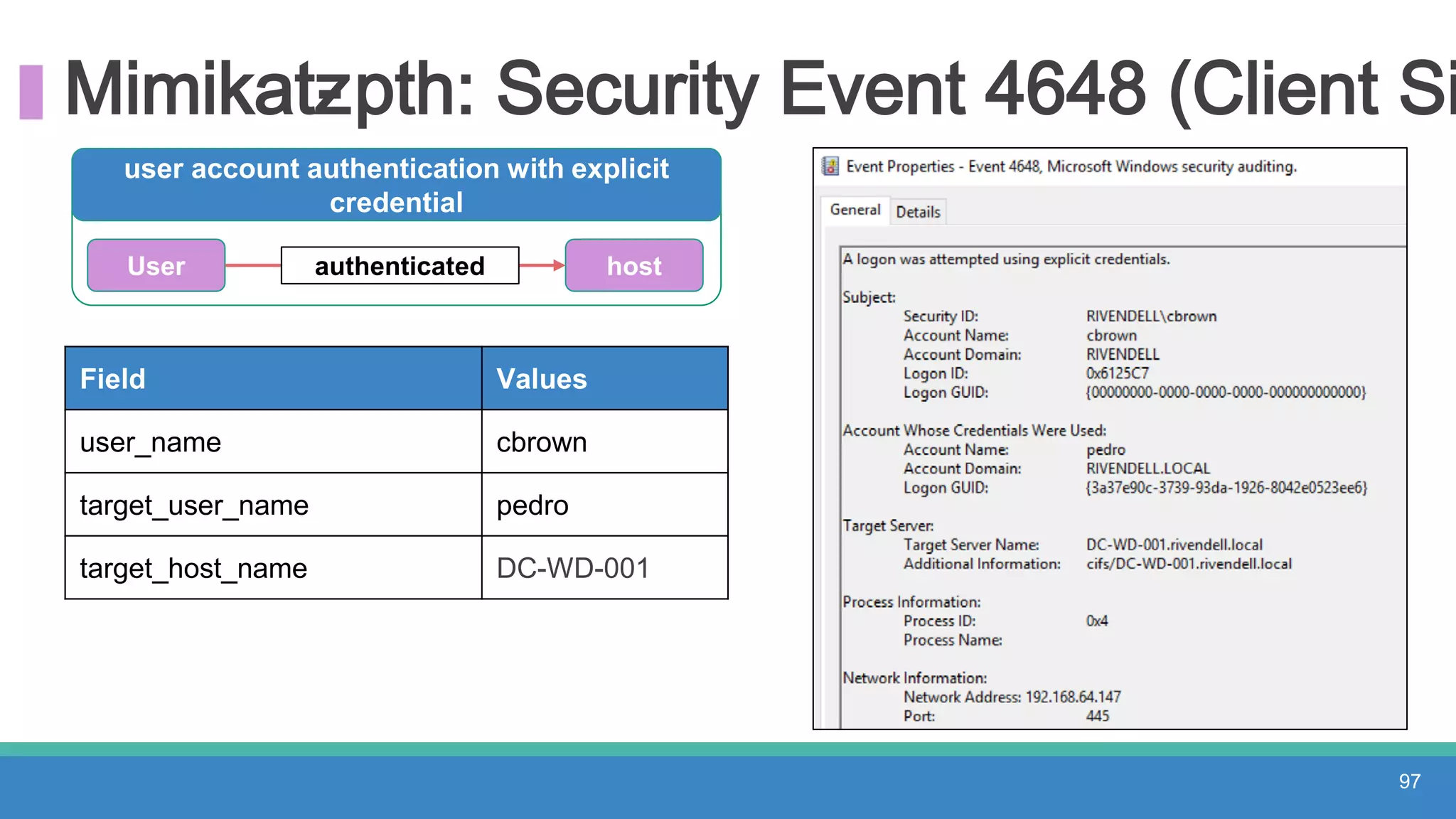
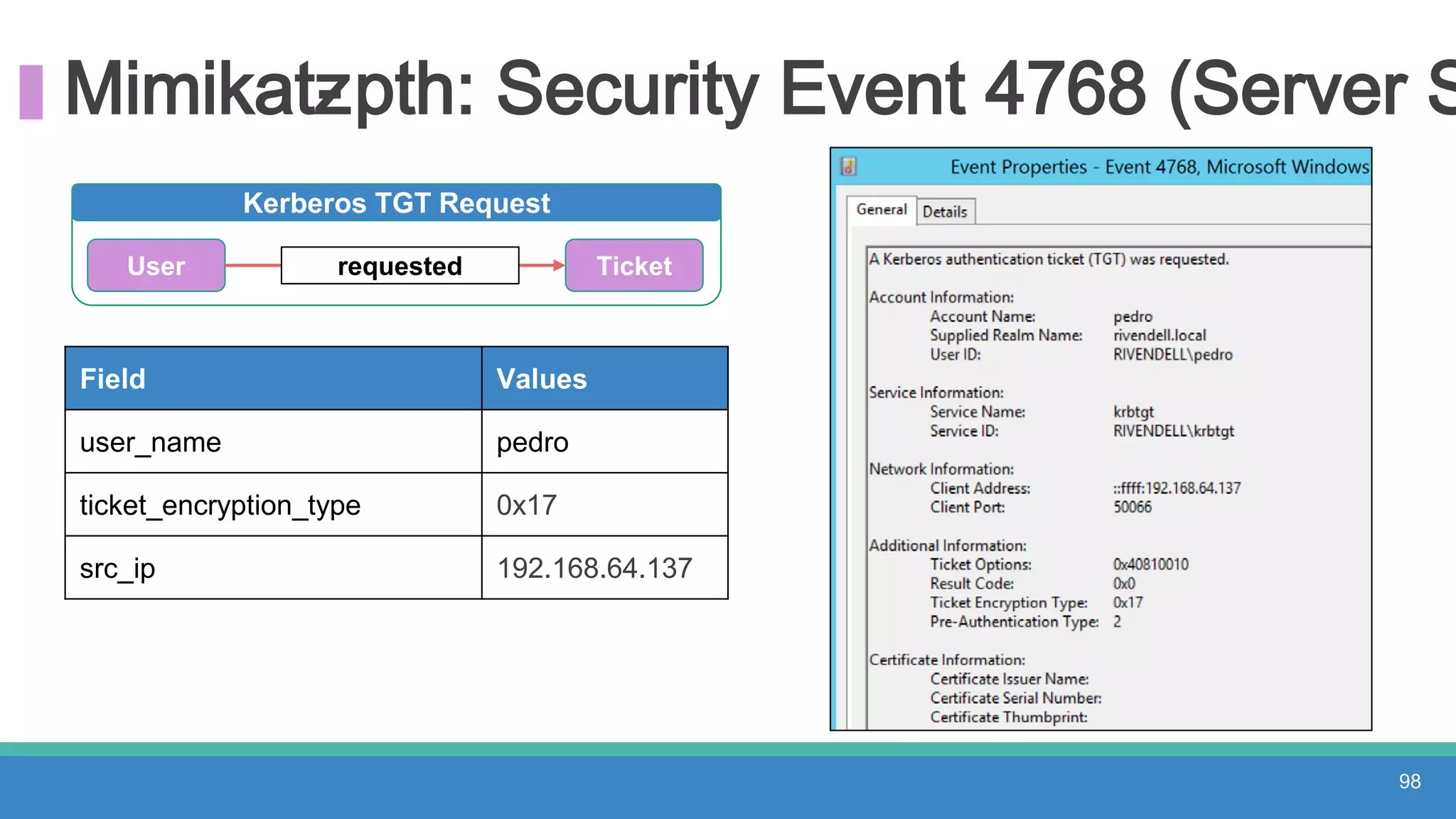
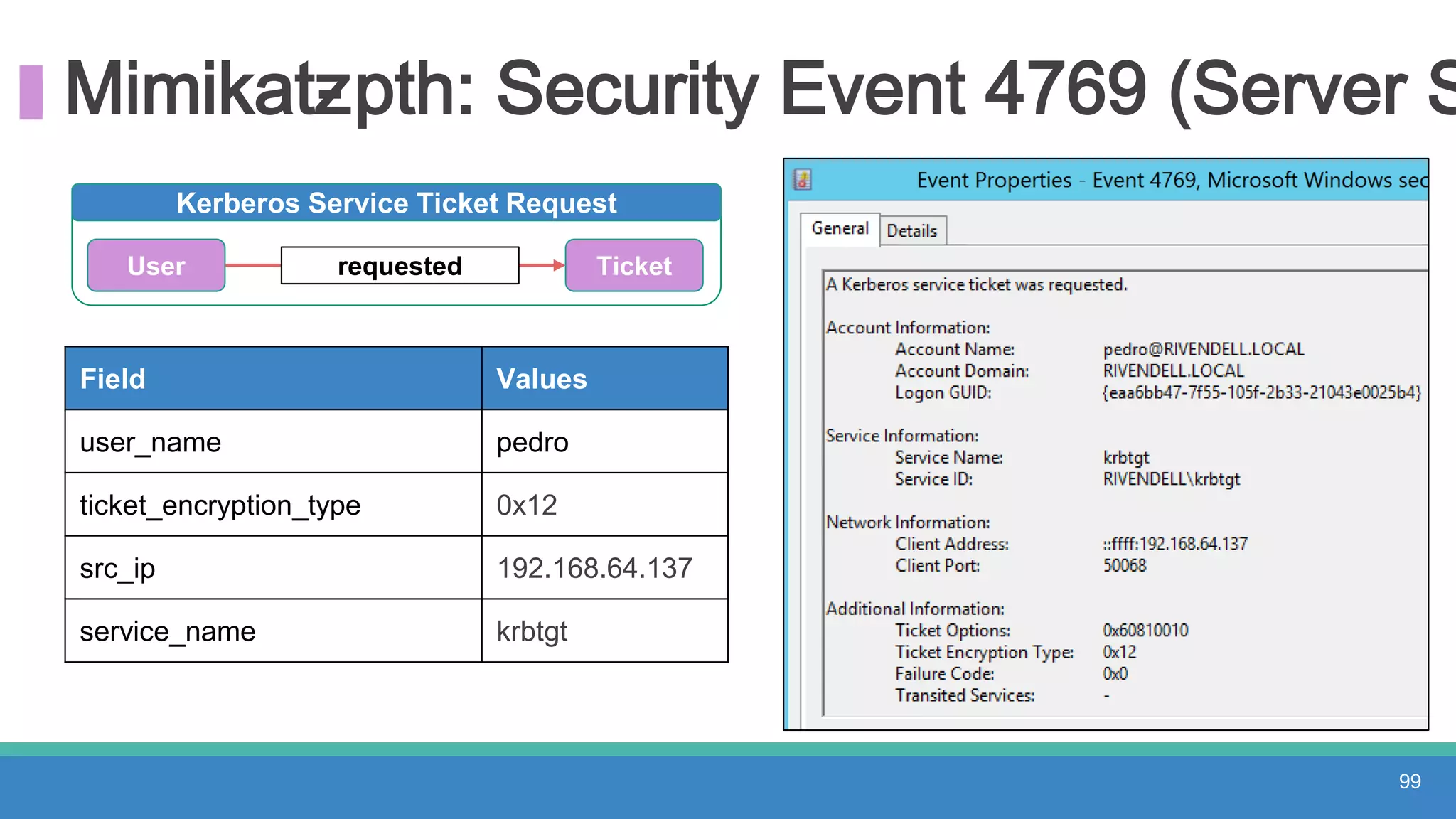
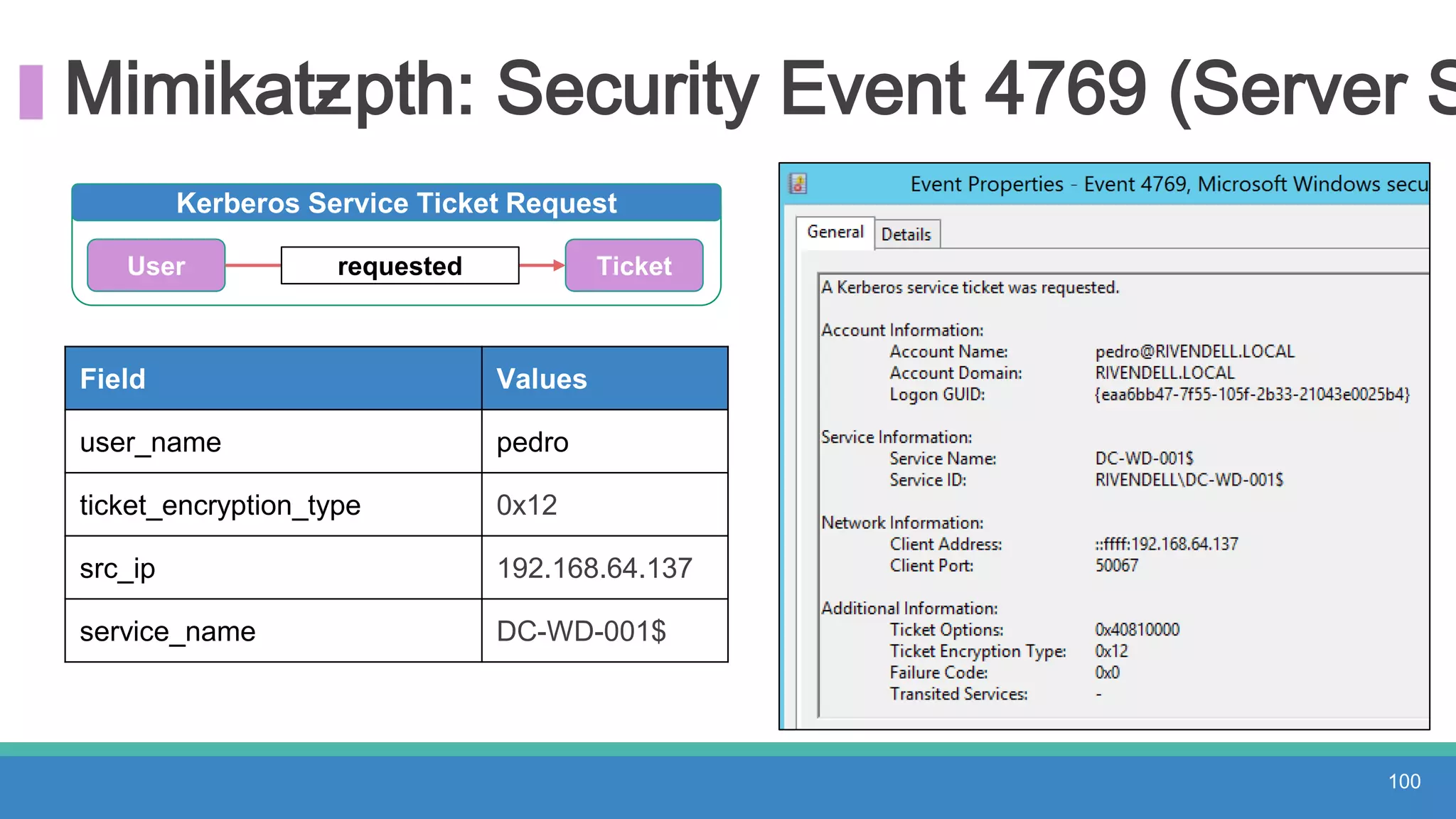
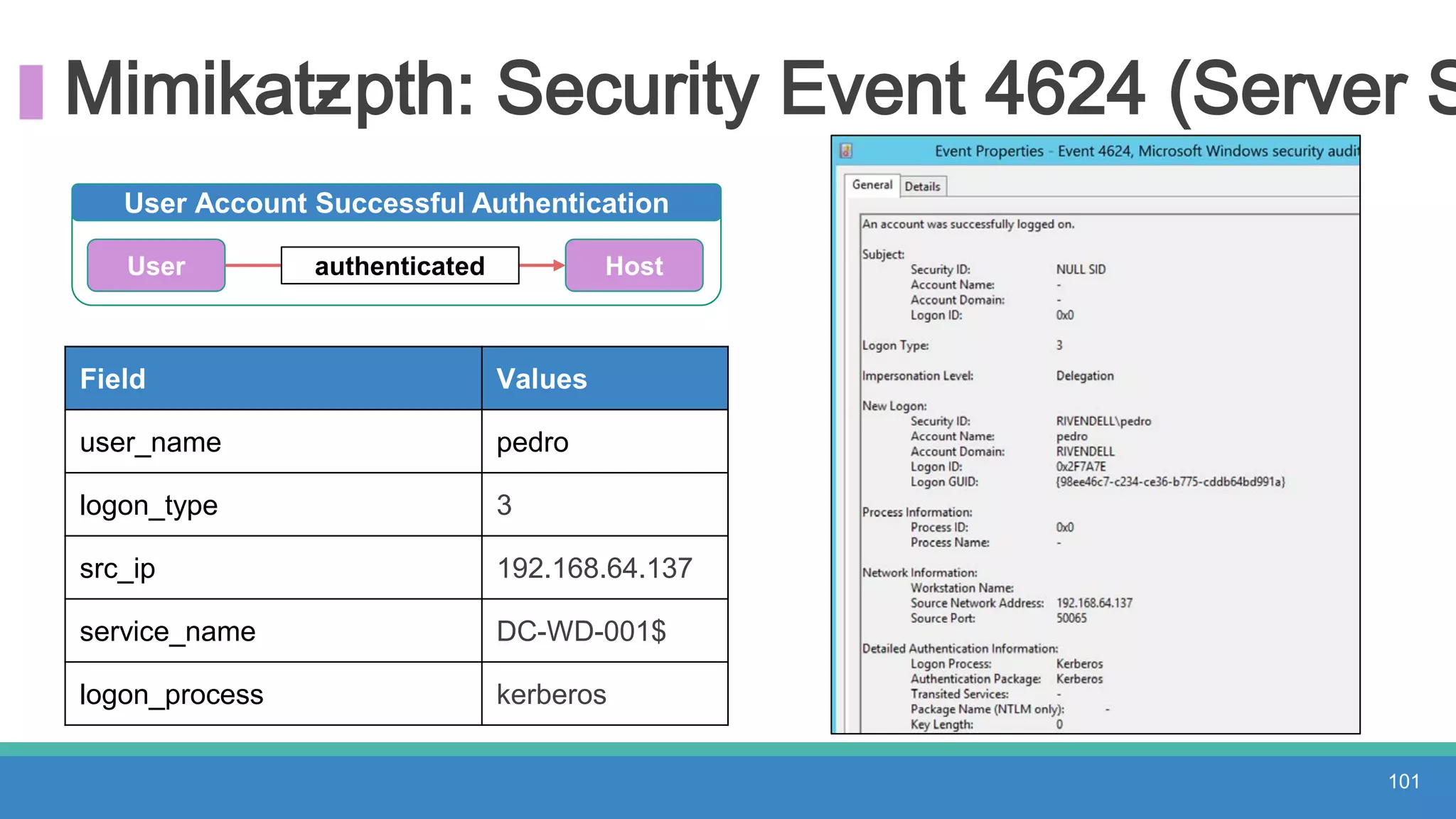
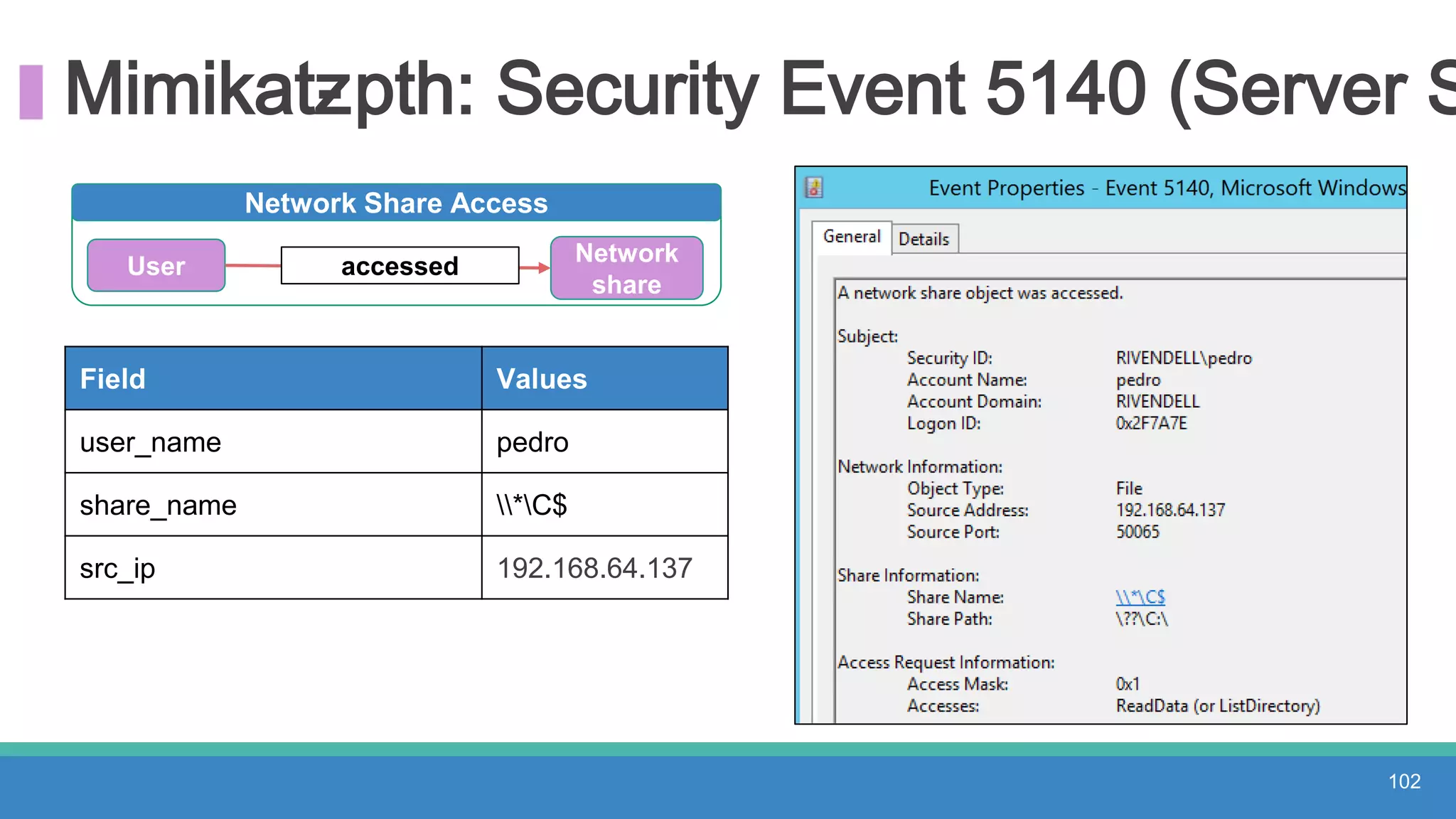
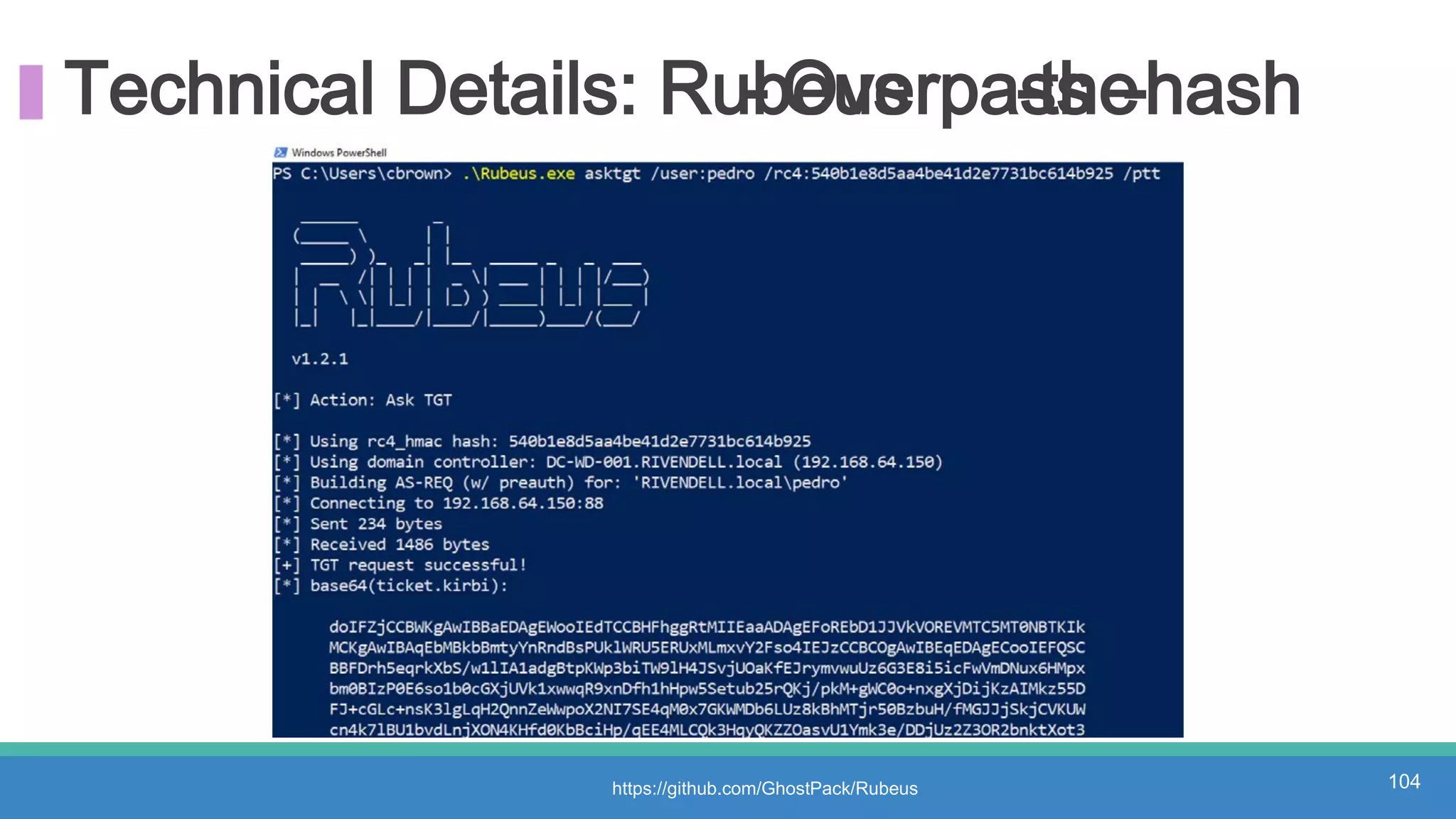
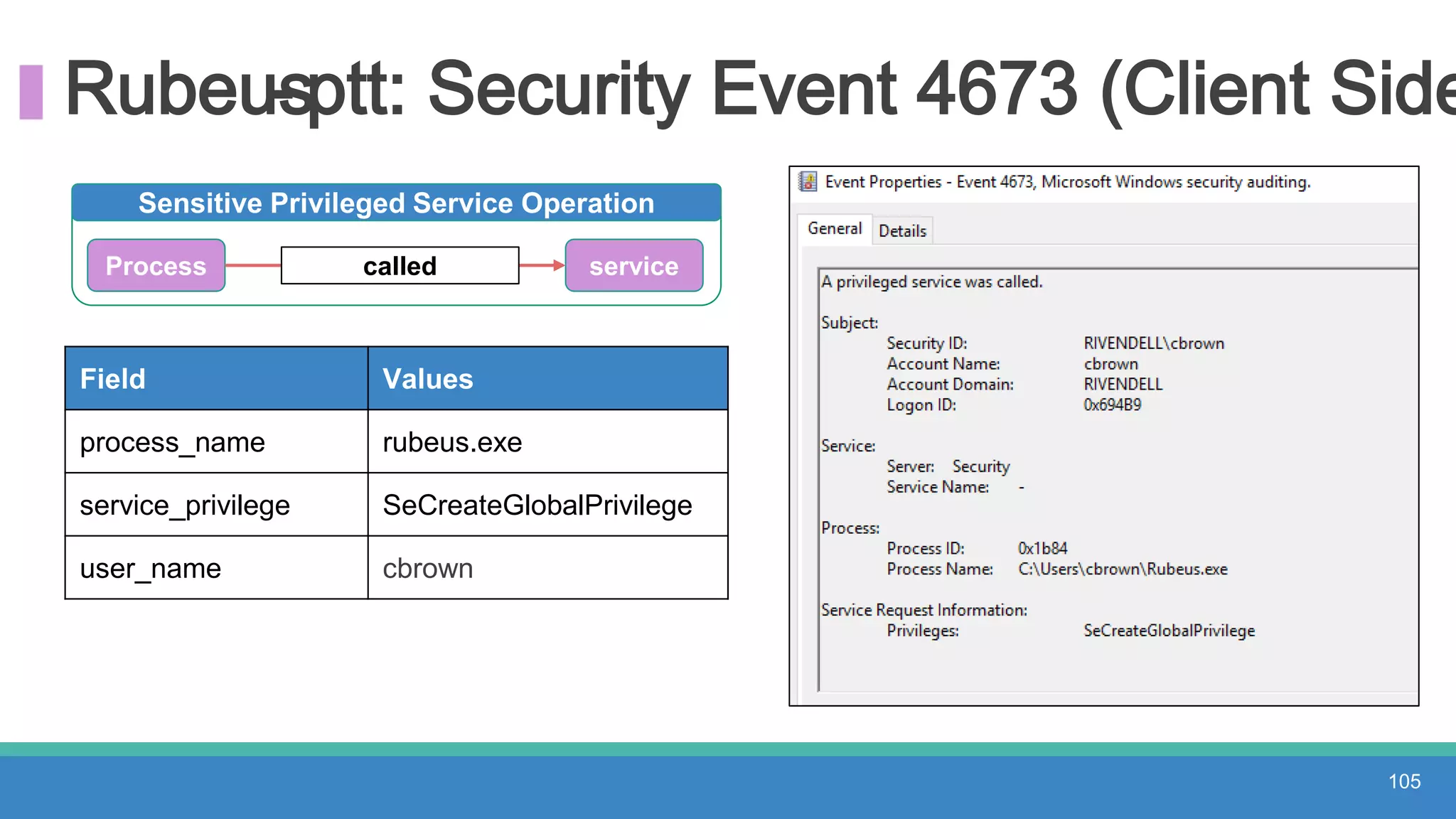
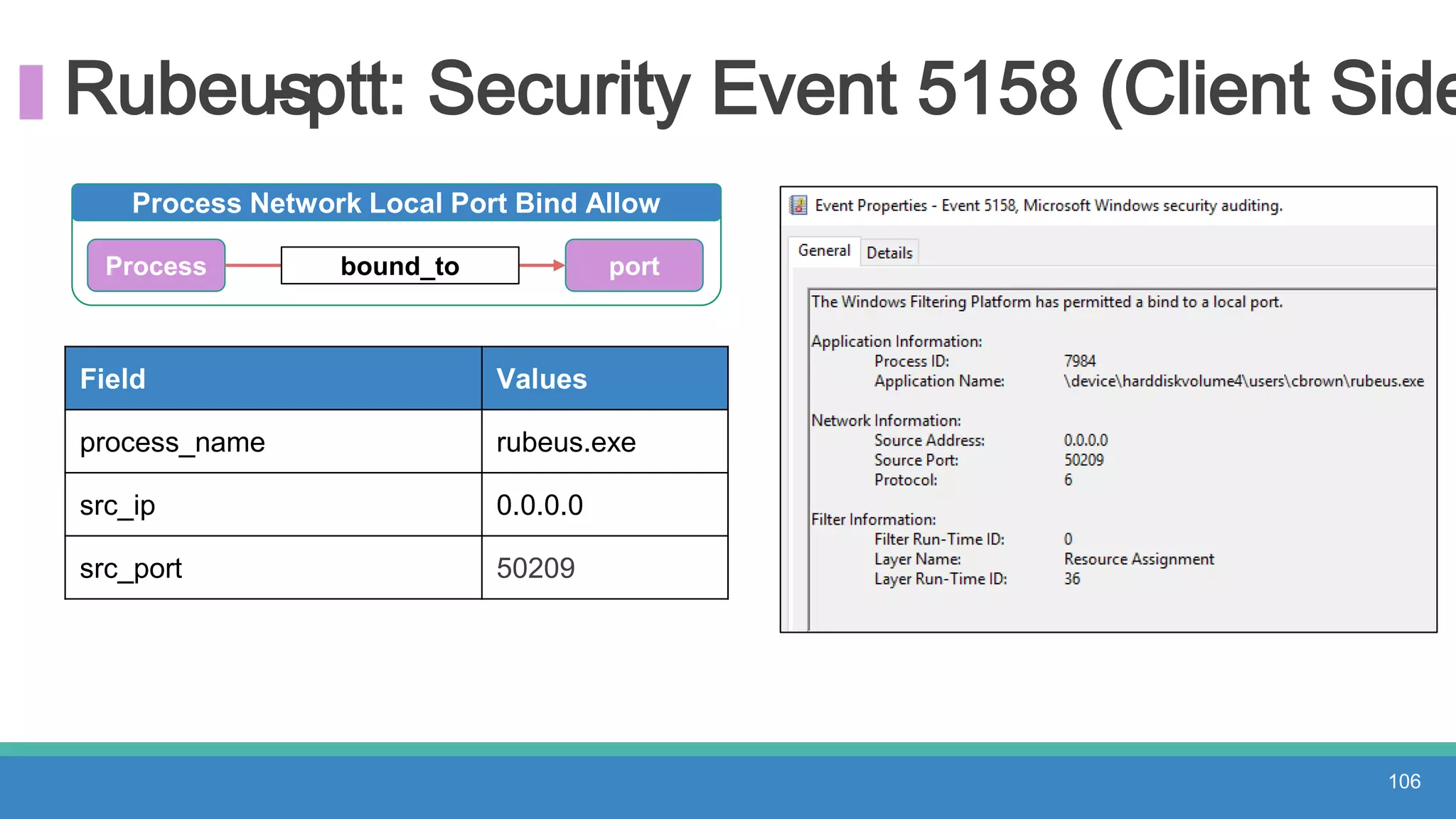
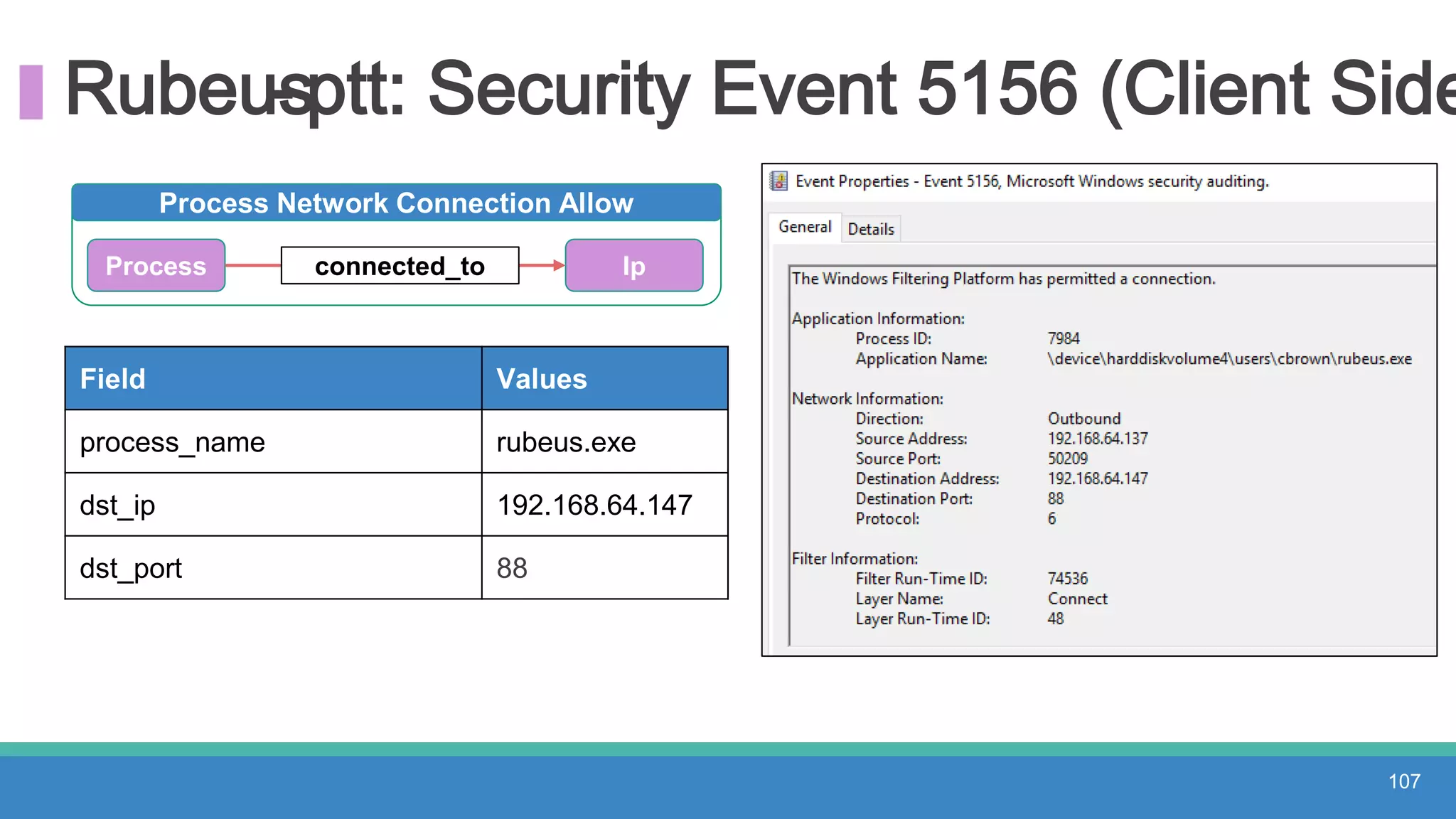
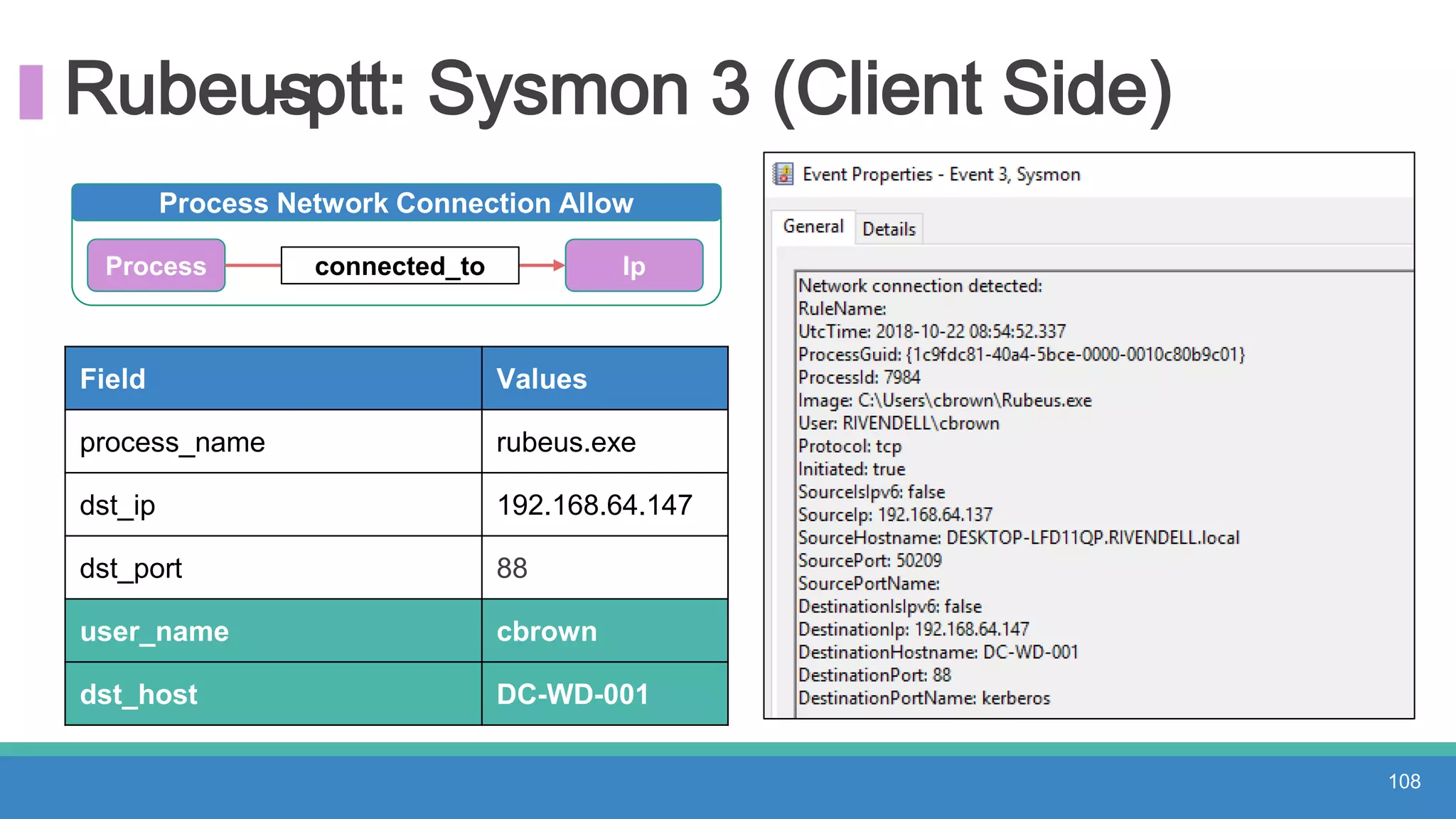
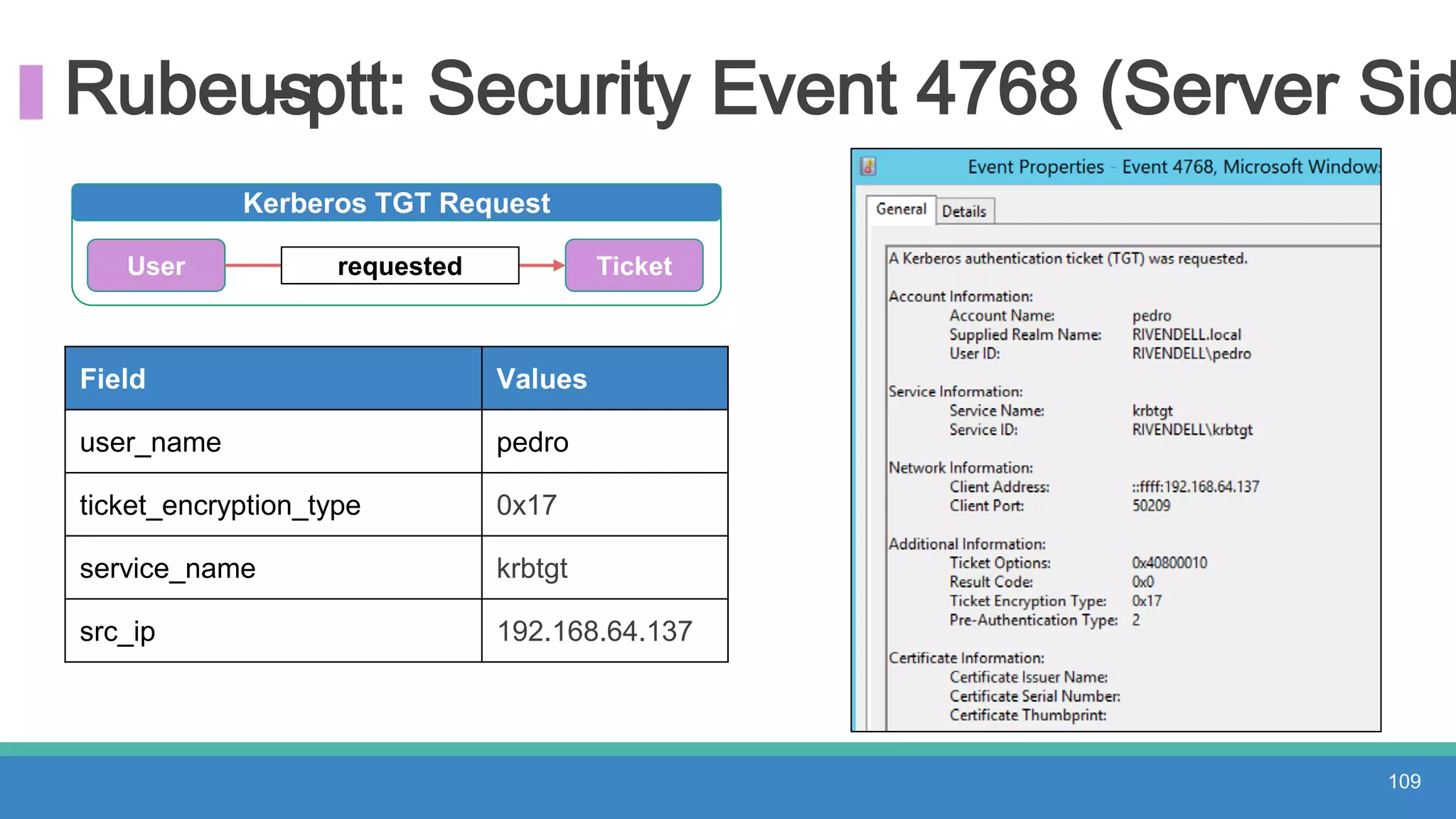
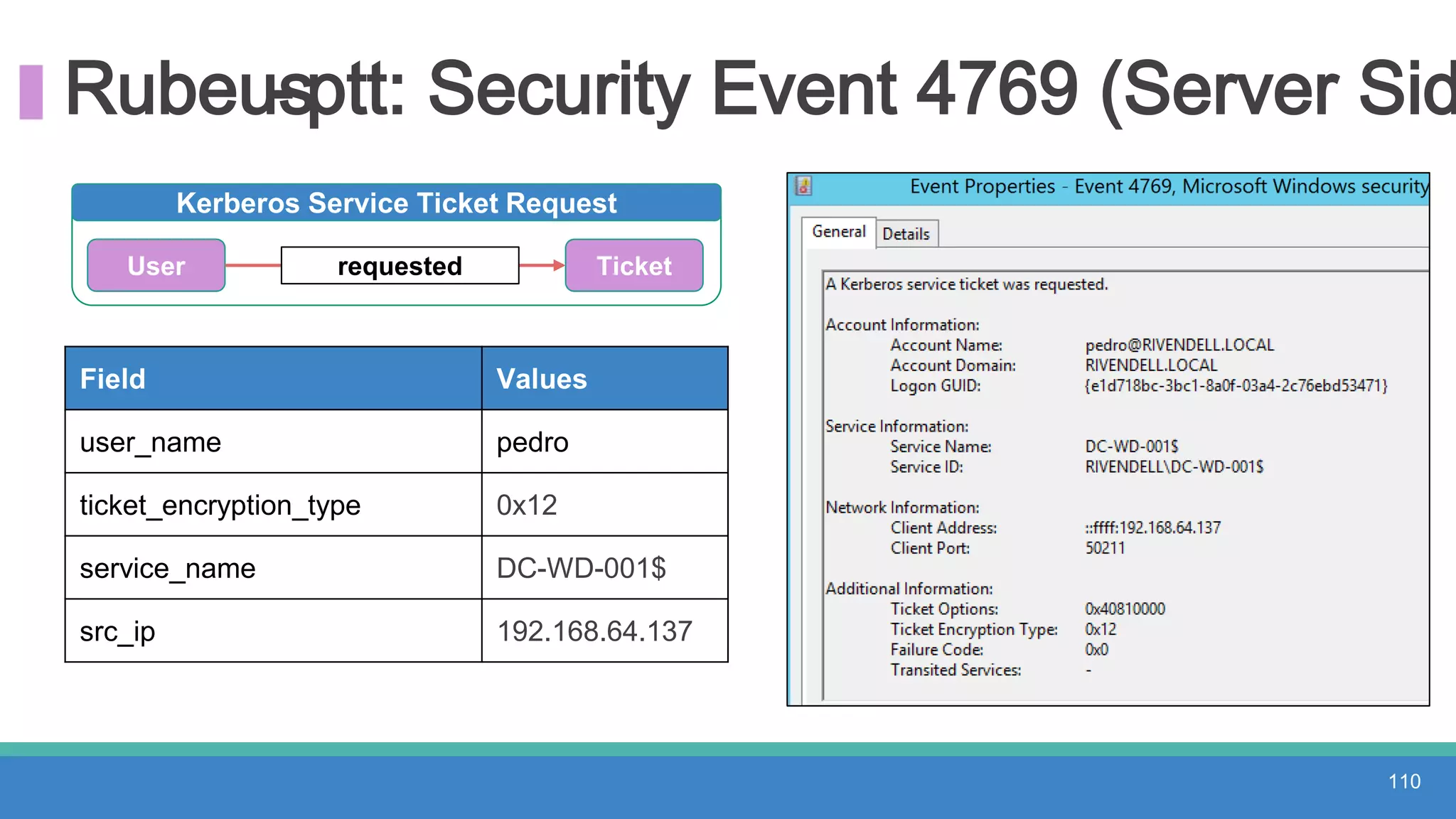
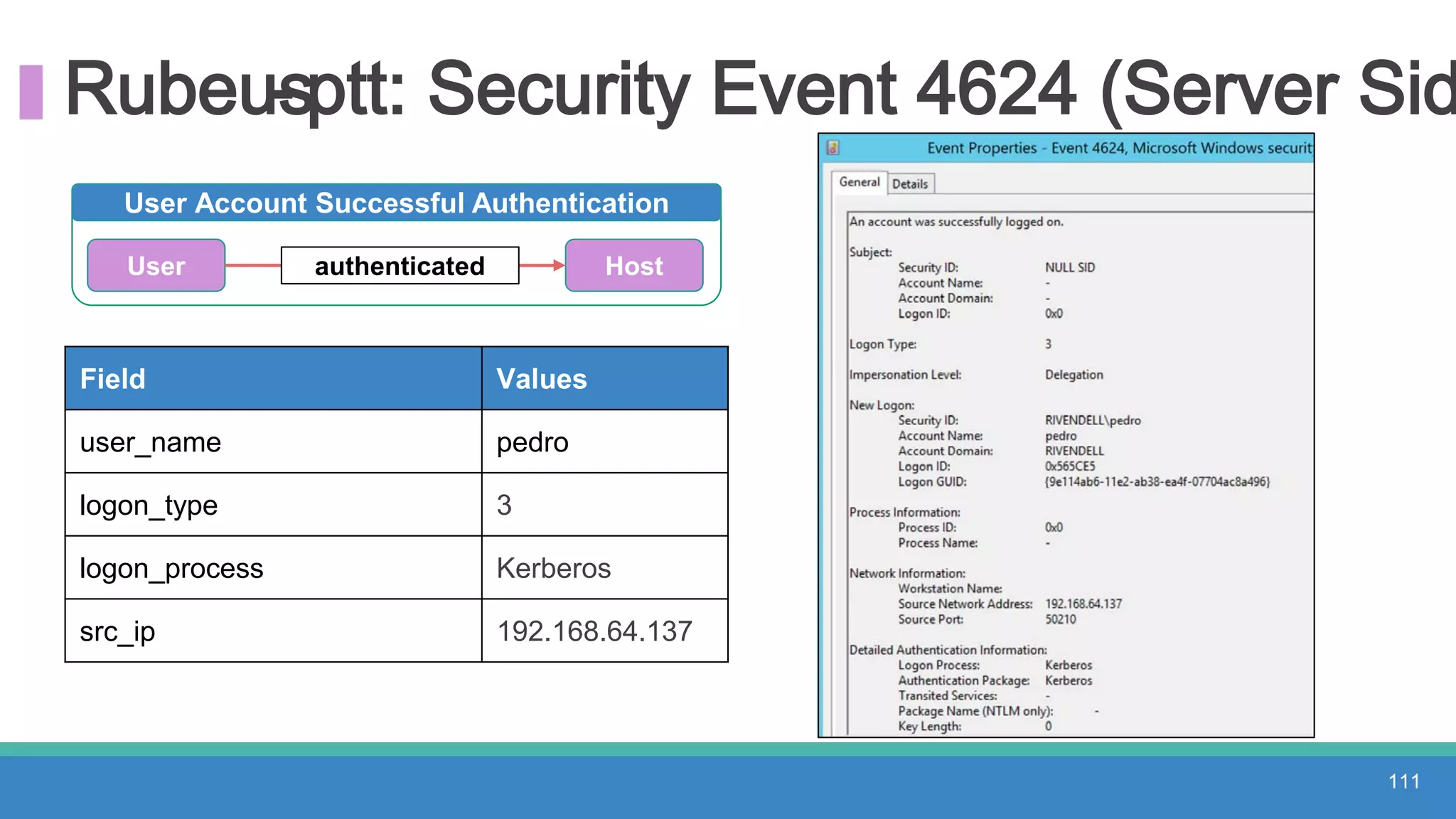
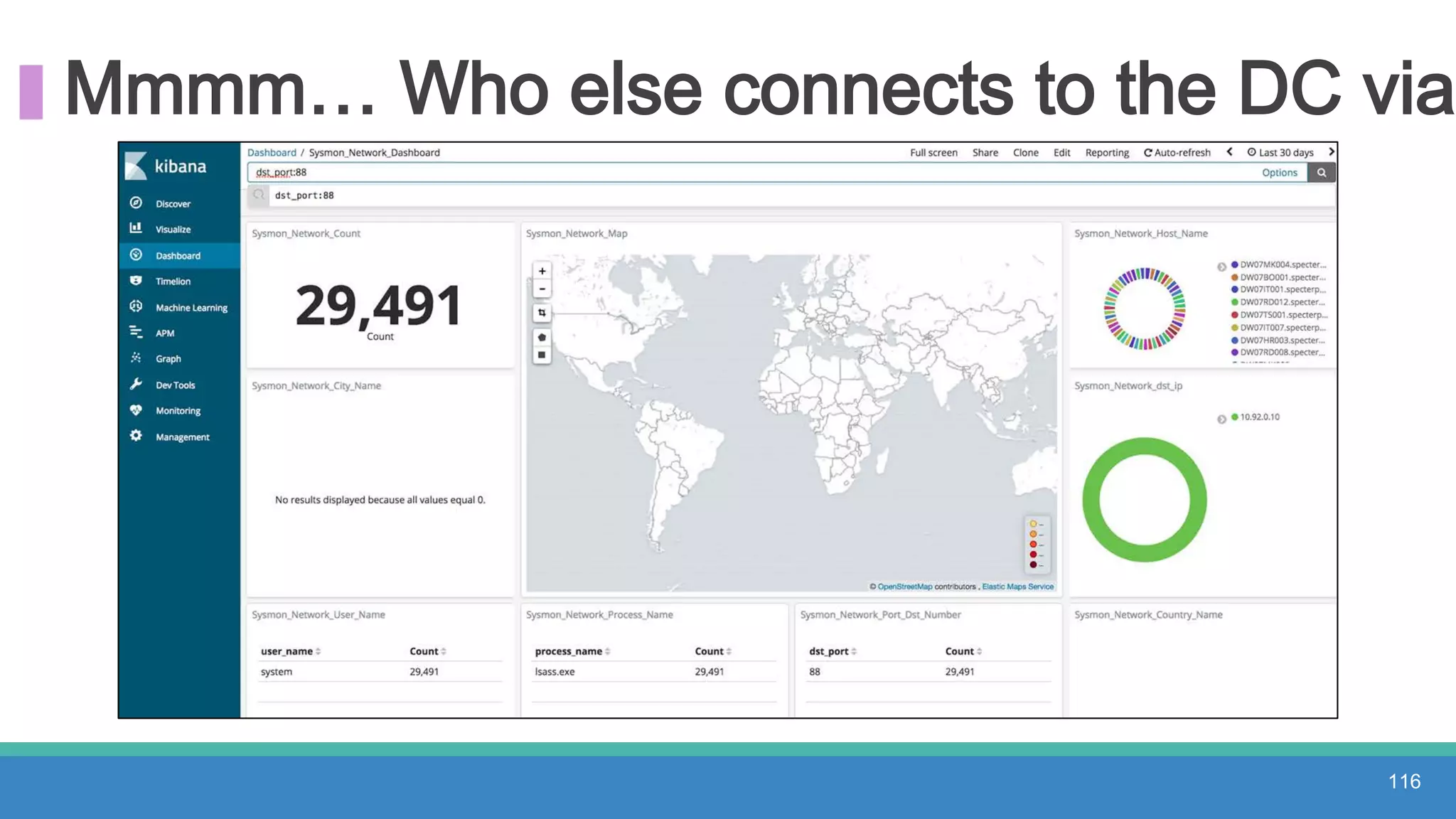
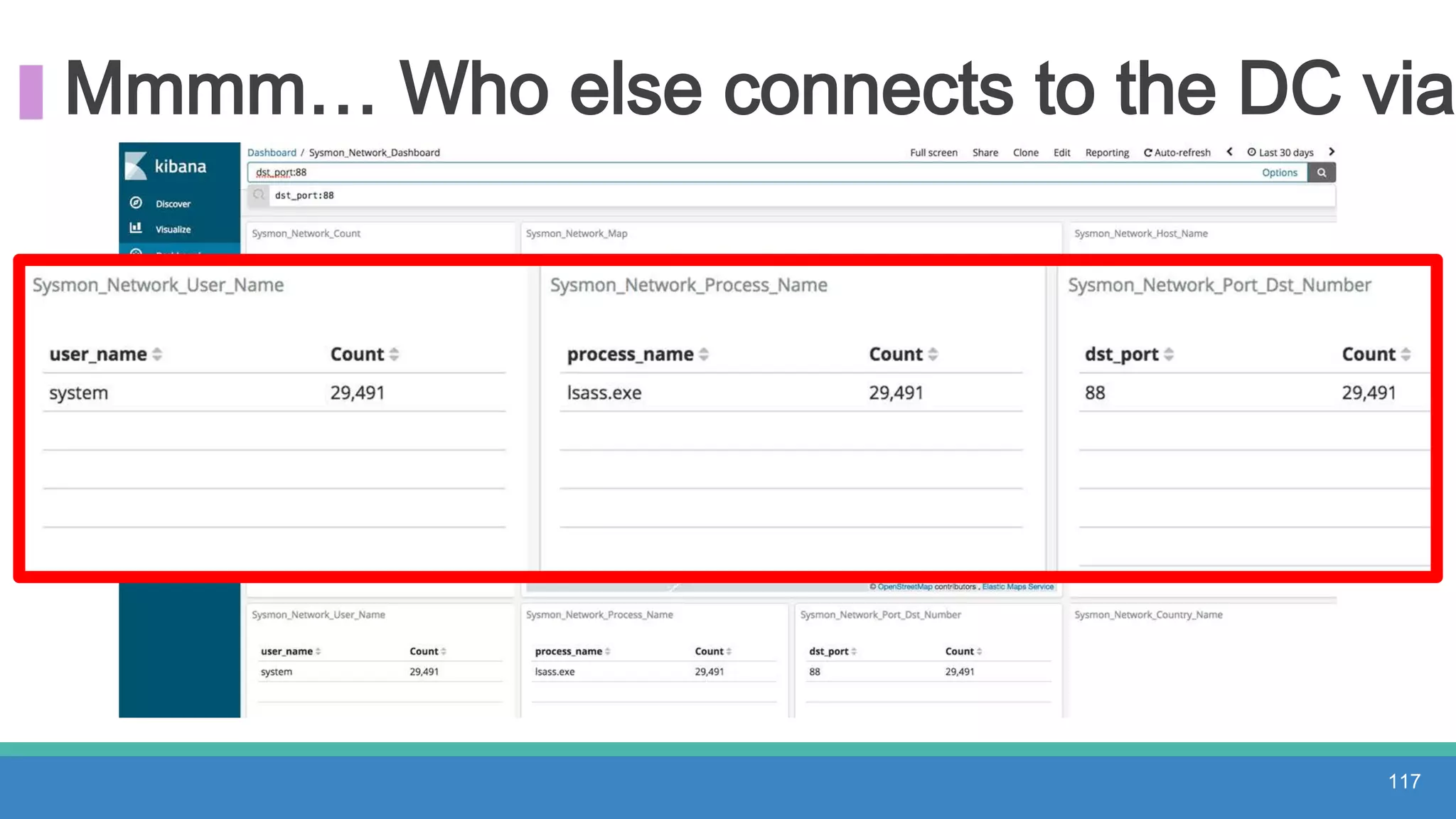
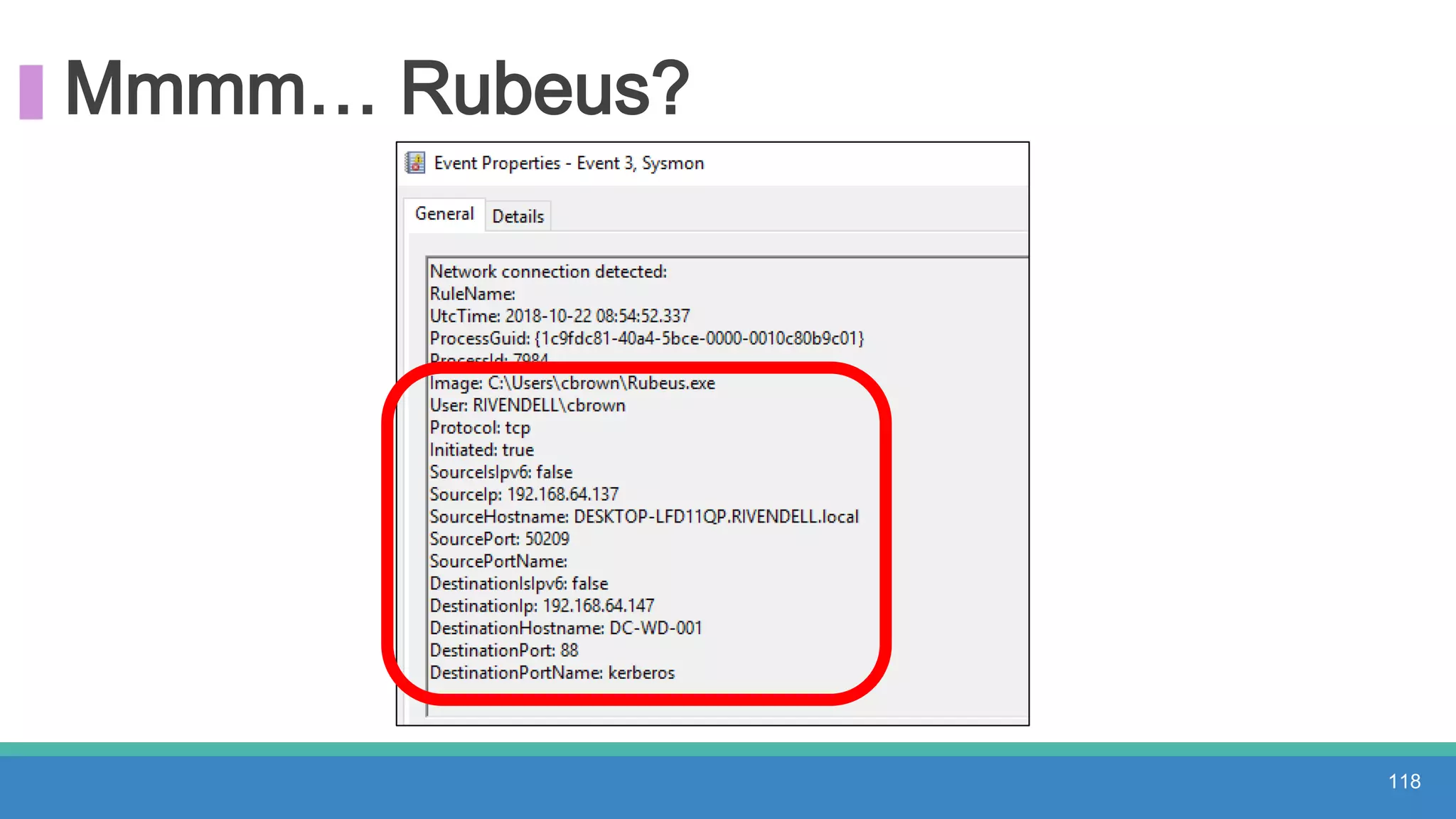
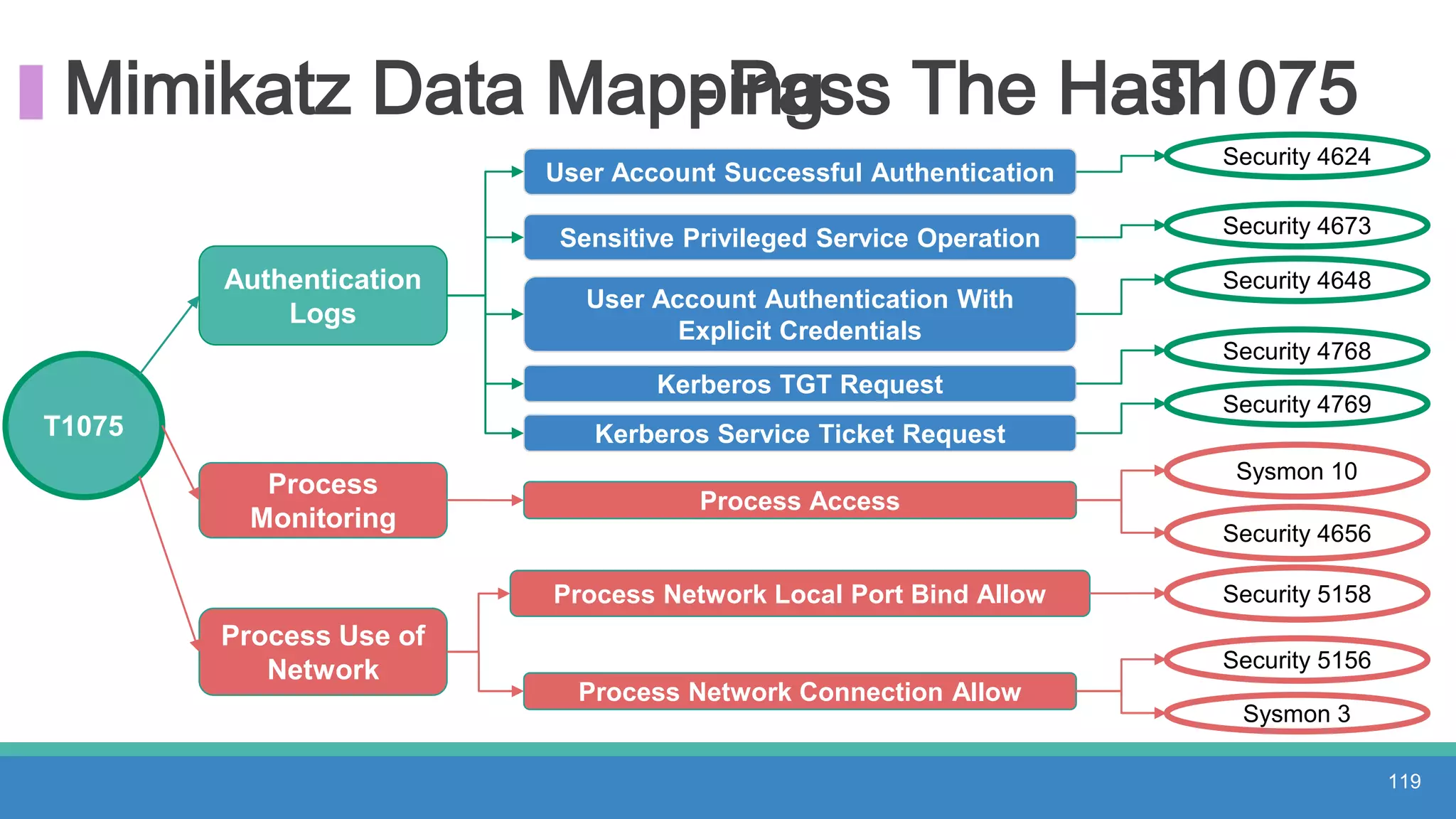
The document discusses threat hunting methodologies, emphasizing the importance of data mapping and understanding ATT&CK data sources to improve detection of adversarial techniques. It outlines steps for effective threat hunting, including defining techniques, generating hypotheses, and validating data collection methodologies. Additionally, it highlights tools like the attack-python-client for accessing ATT&CK metadata and encourages collaboration to address gaps in data source mappings.