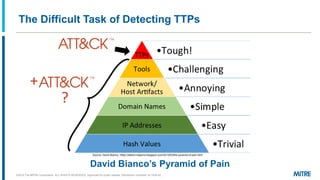
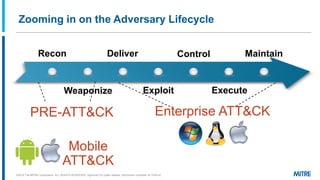
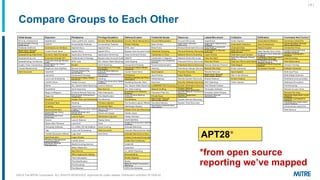
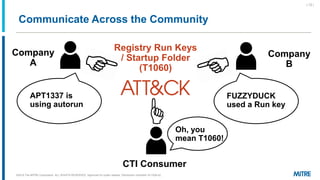
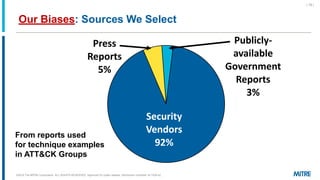
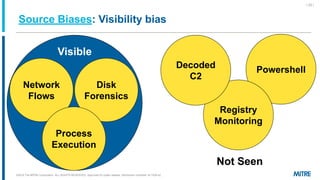
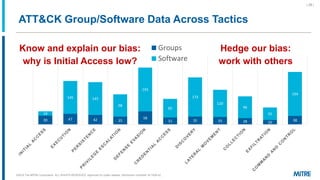
MITRE ATT&CK is a knowledge base of adversary behavior derived from real-world observations, designed to facilitate a common language and community-driven defense strategies. The document discusses various tactics and techniques used by adversaries throughout the attack lifecycle, as well as the importance of understanding biases in threat intelligence reporting. It emphasizes comparing behaviors, improving communication, and enhancing defenses using ATT&CK-mapped threat intelligence.