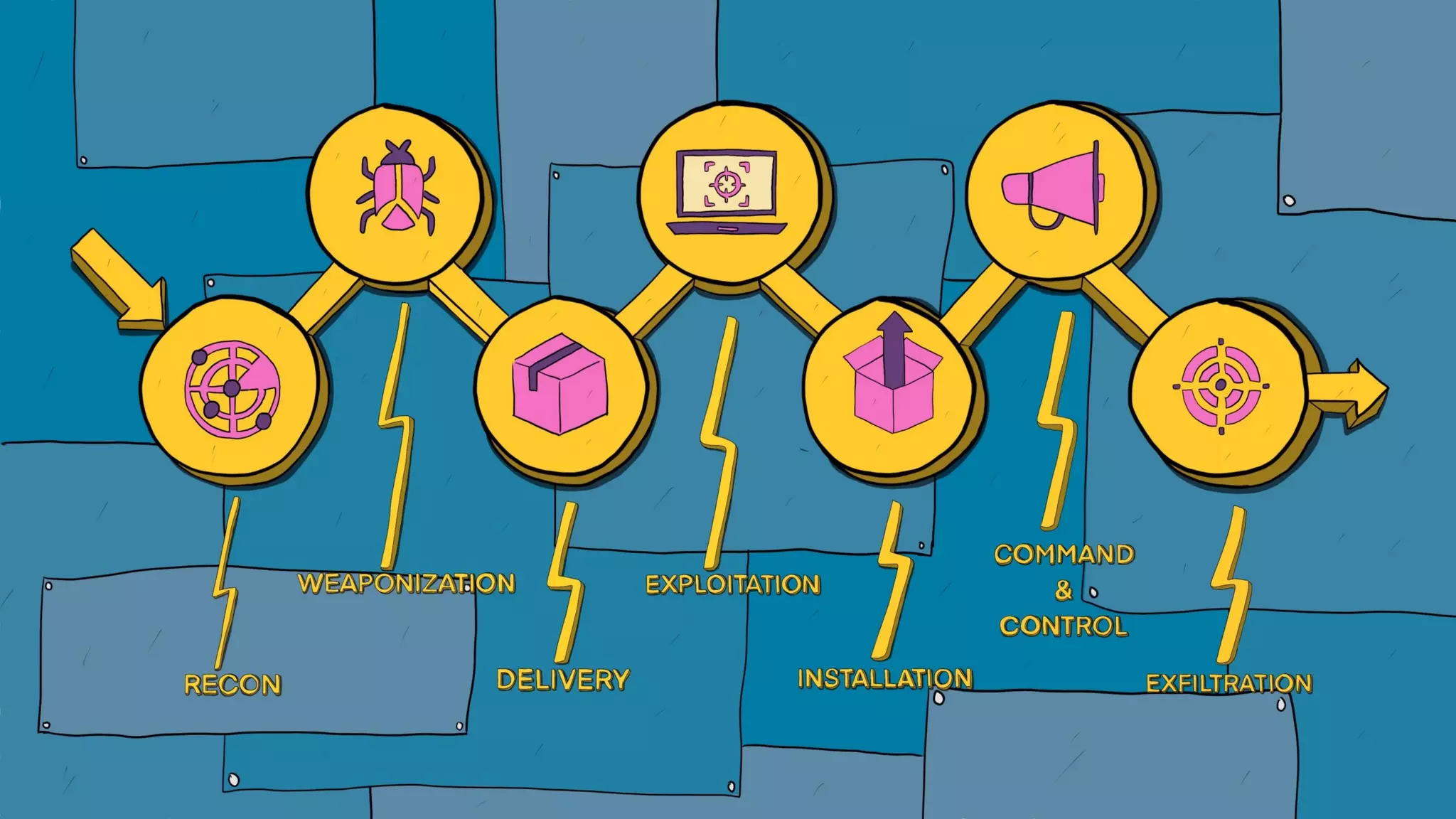
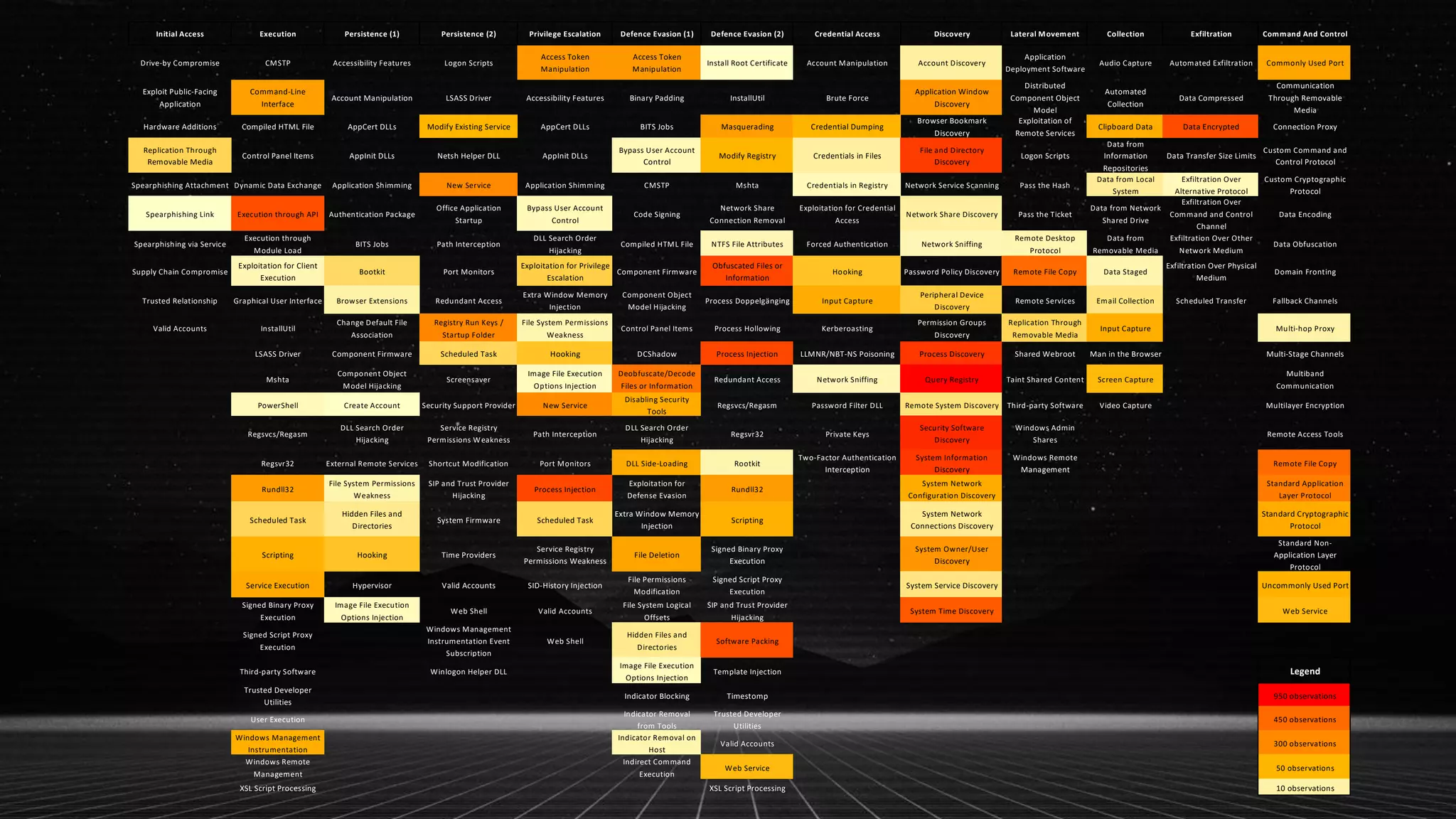
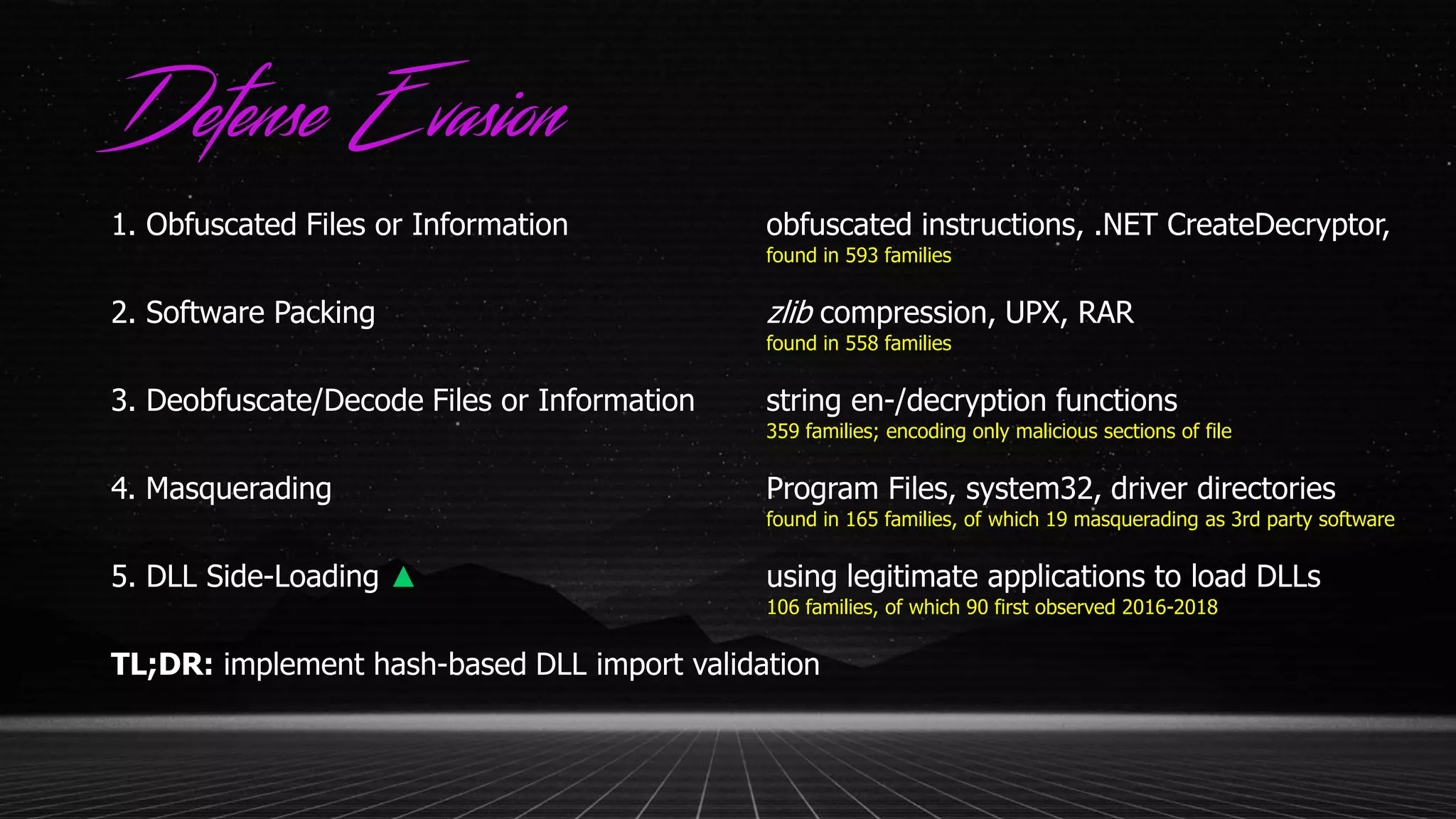
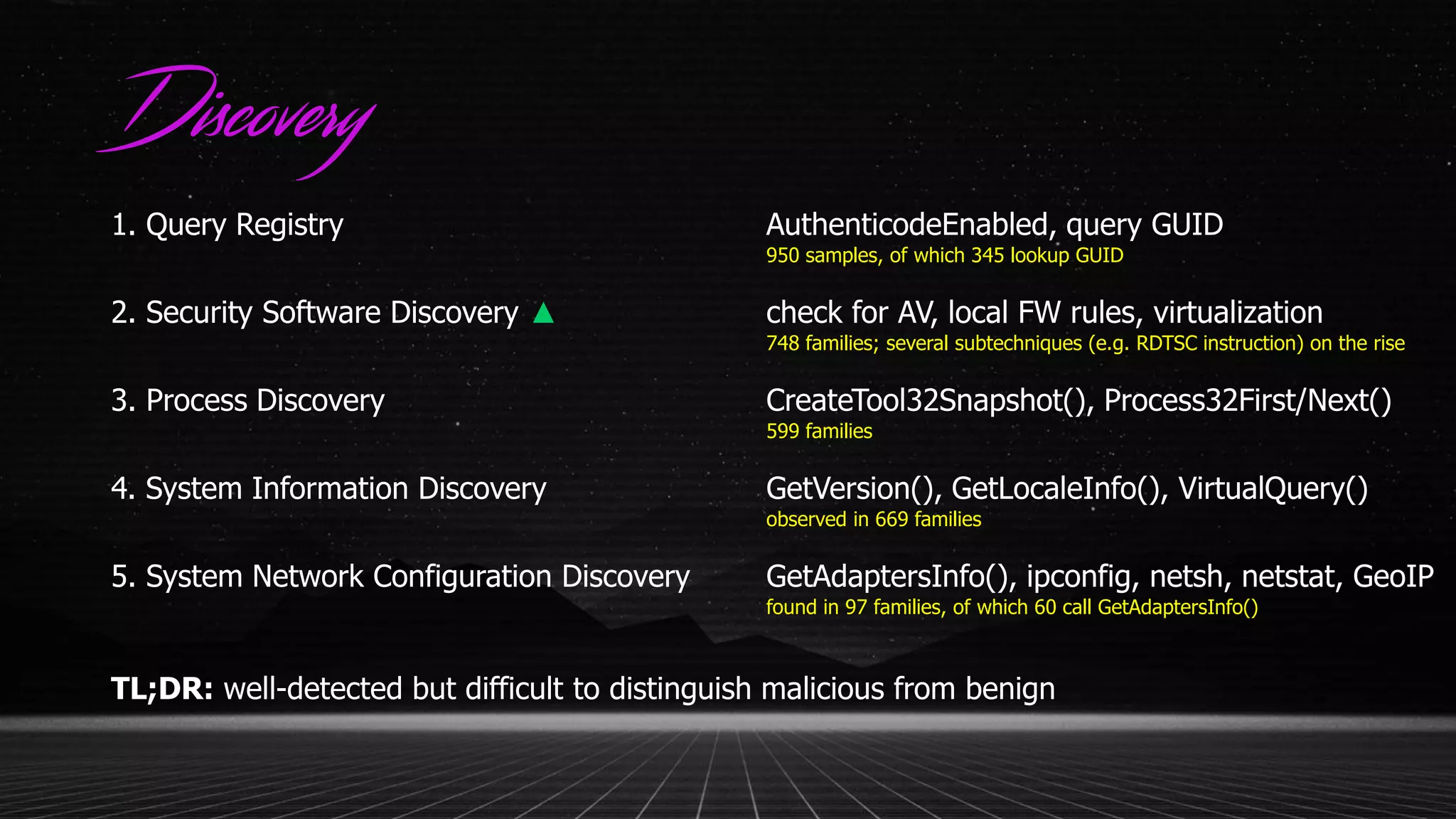
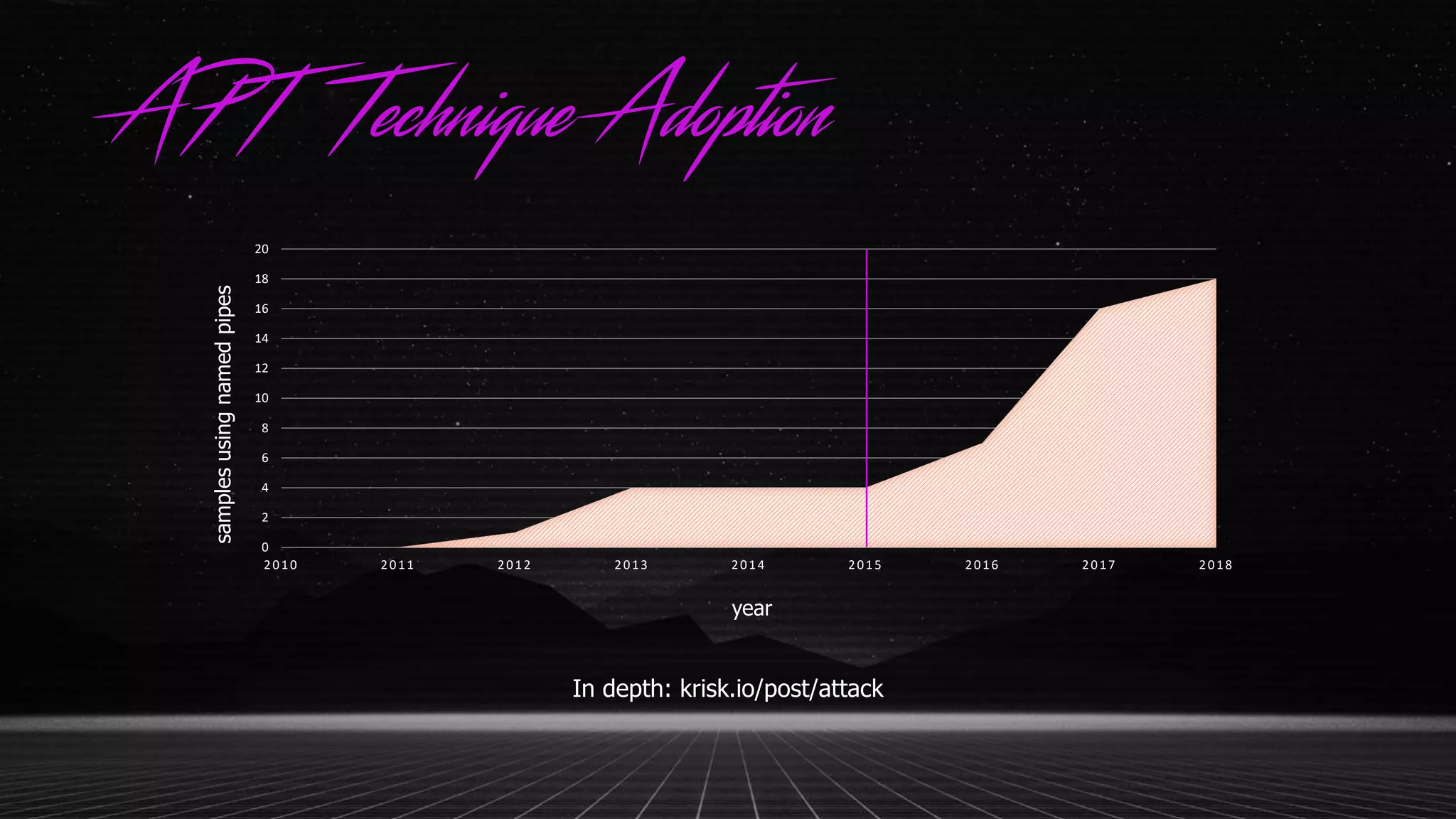
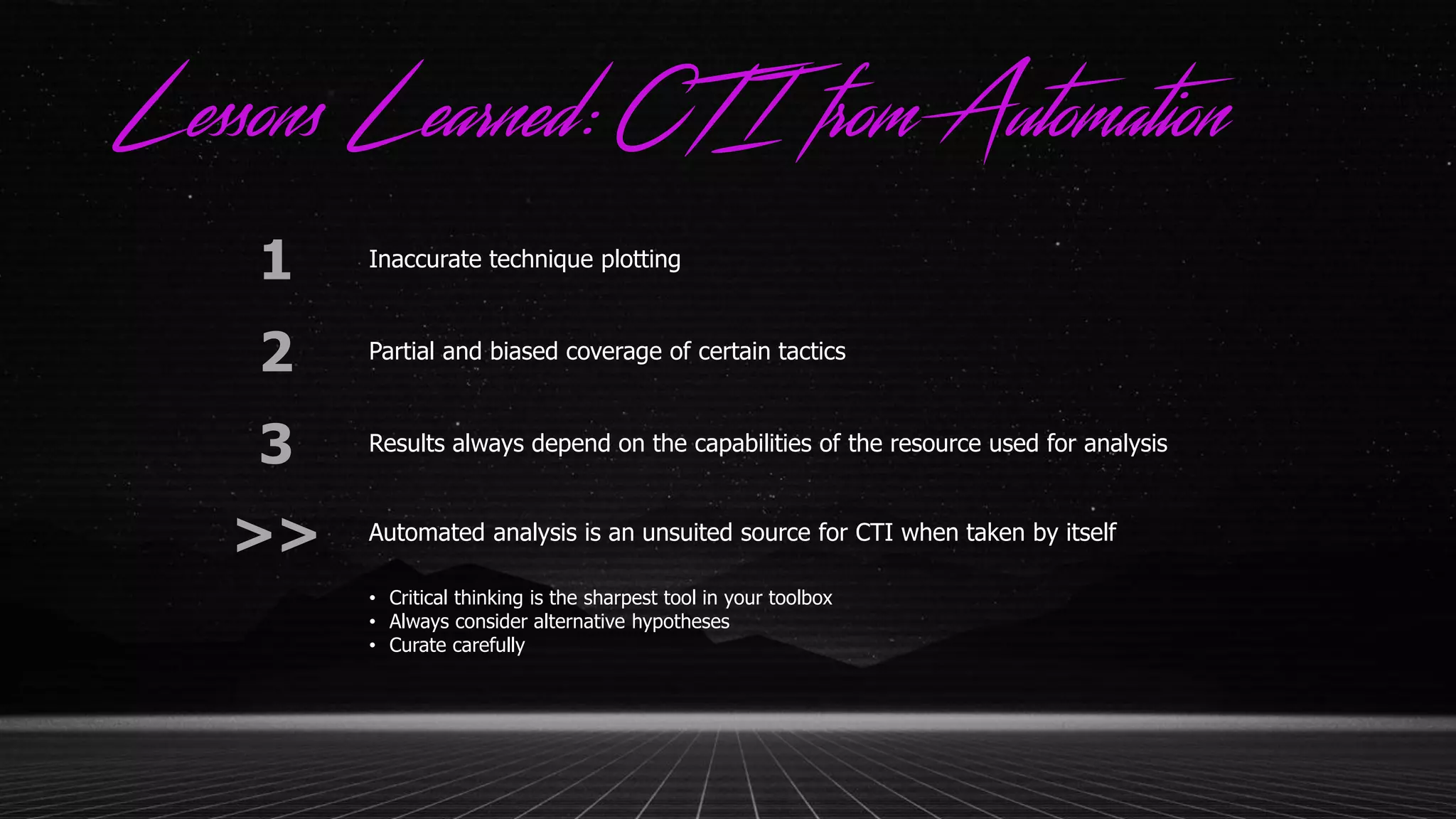
This document discusses applying the ATT&CK framework to analyze malware samples through automated analysis. It summarizes the findings of analyzing 951 malware samples against ATT&CK techniques. The most common techniques were related to execution, defense evasion, and discovery. Fileless execution techniques like PowerShell and WMI are increasing. The document cautions that automated analysis has limitations and critical thinking is needed to properly interpret results and consider alternative hypotheses.