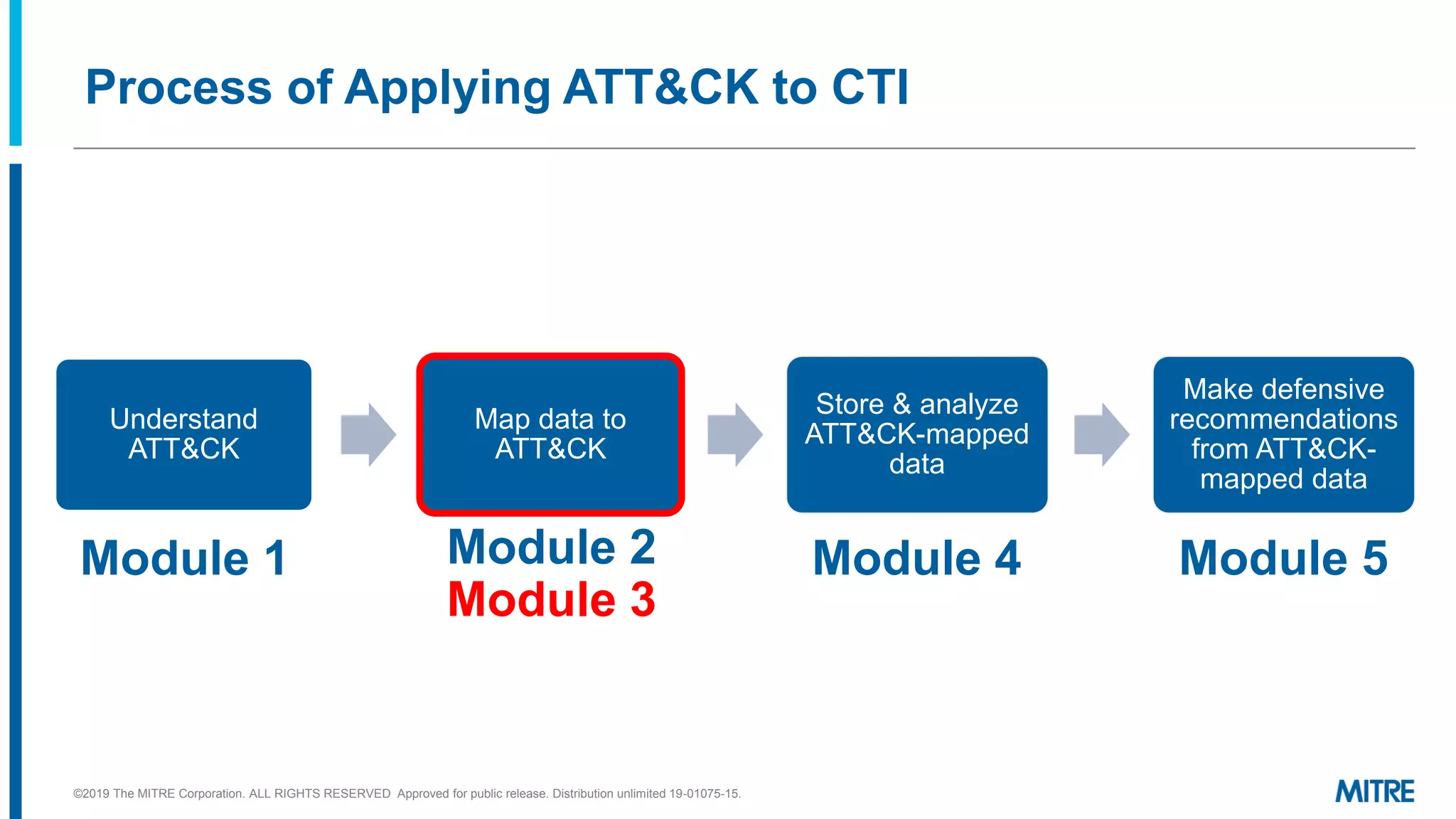
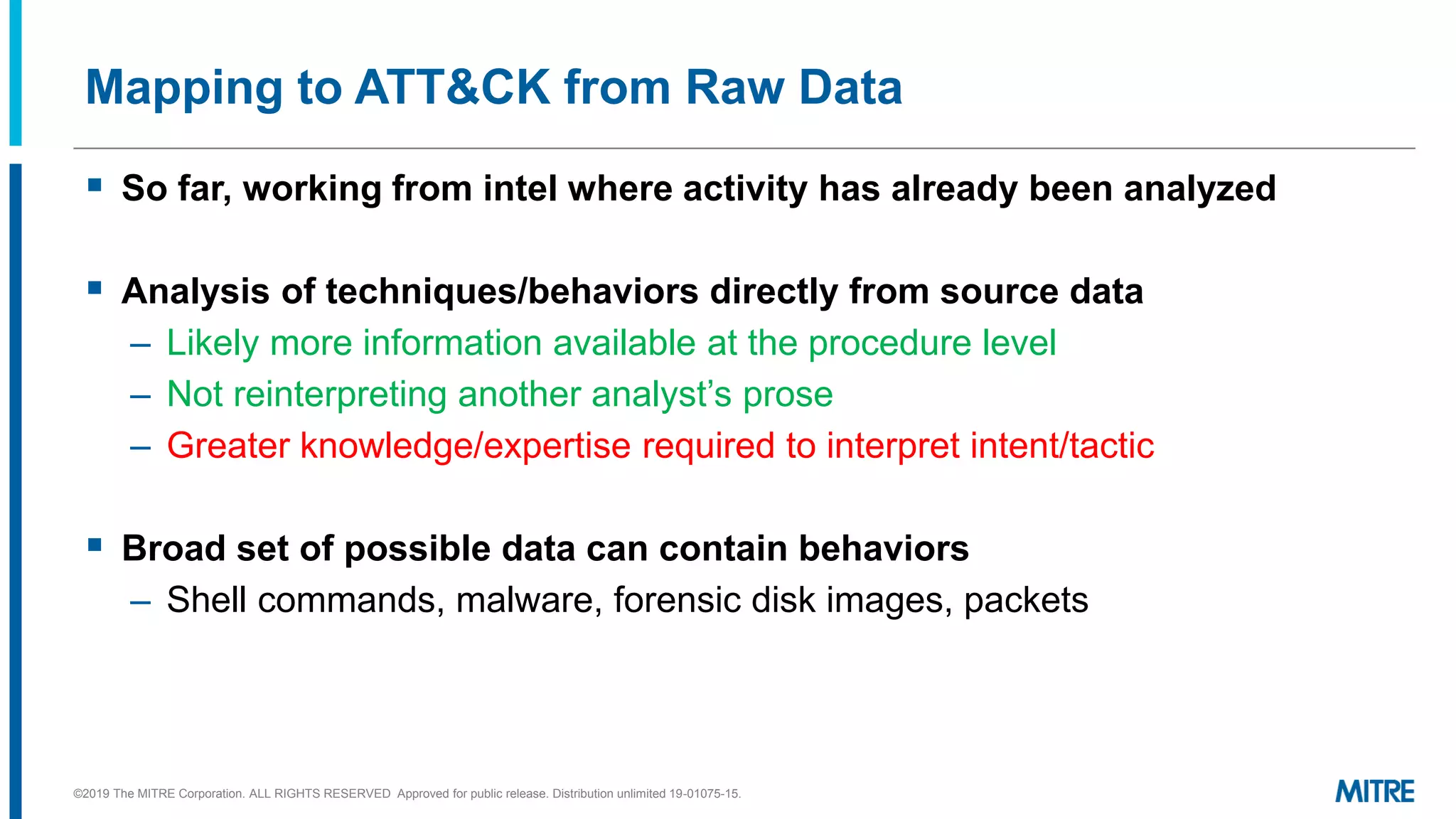
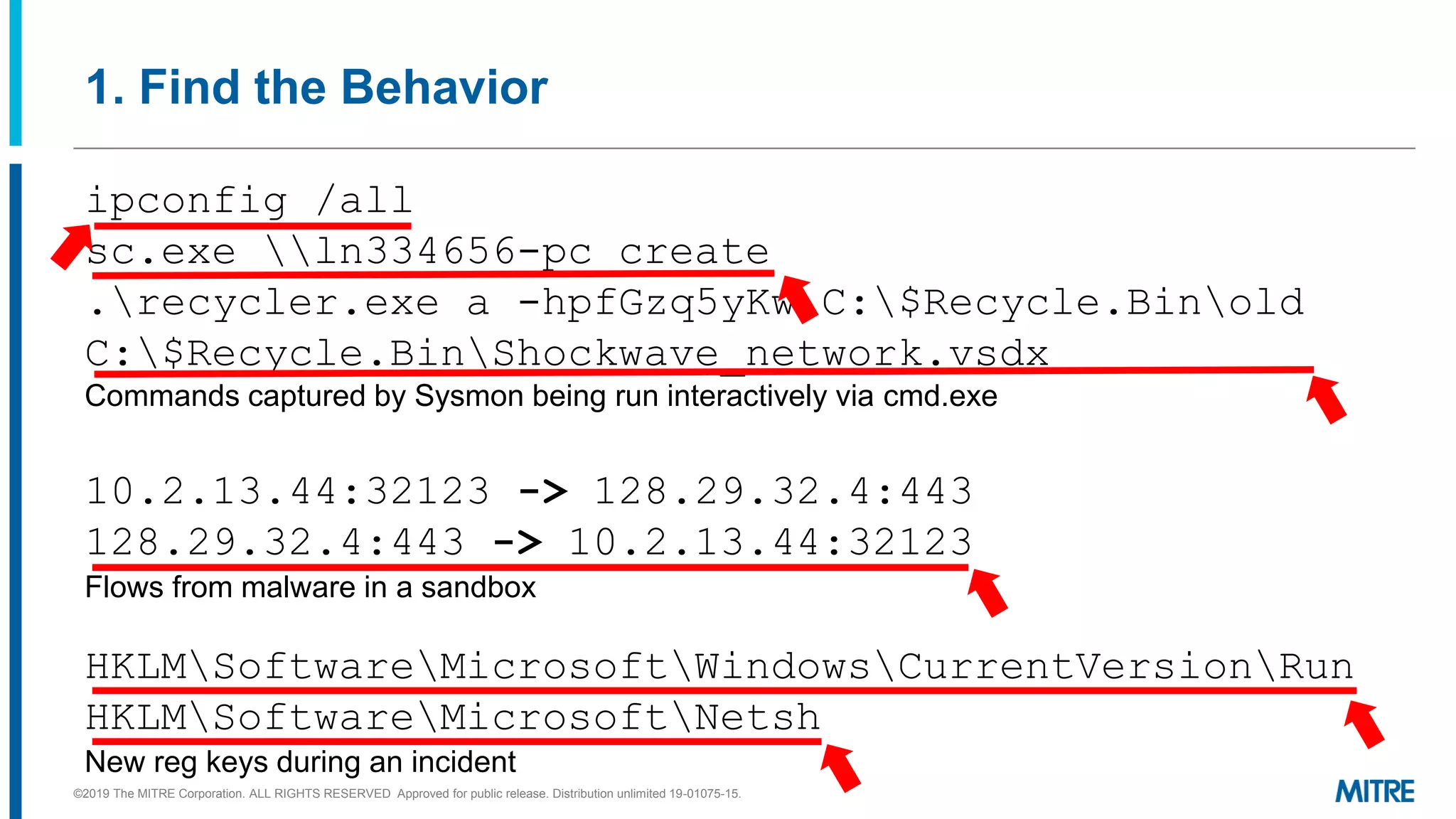
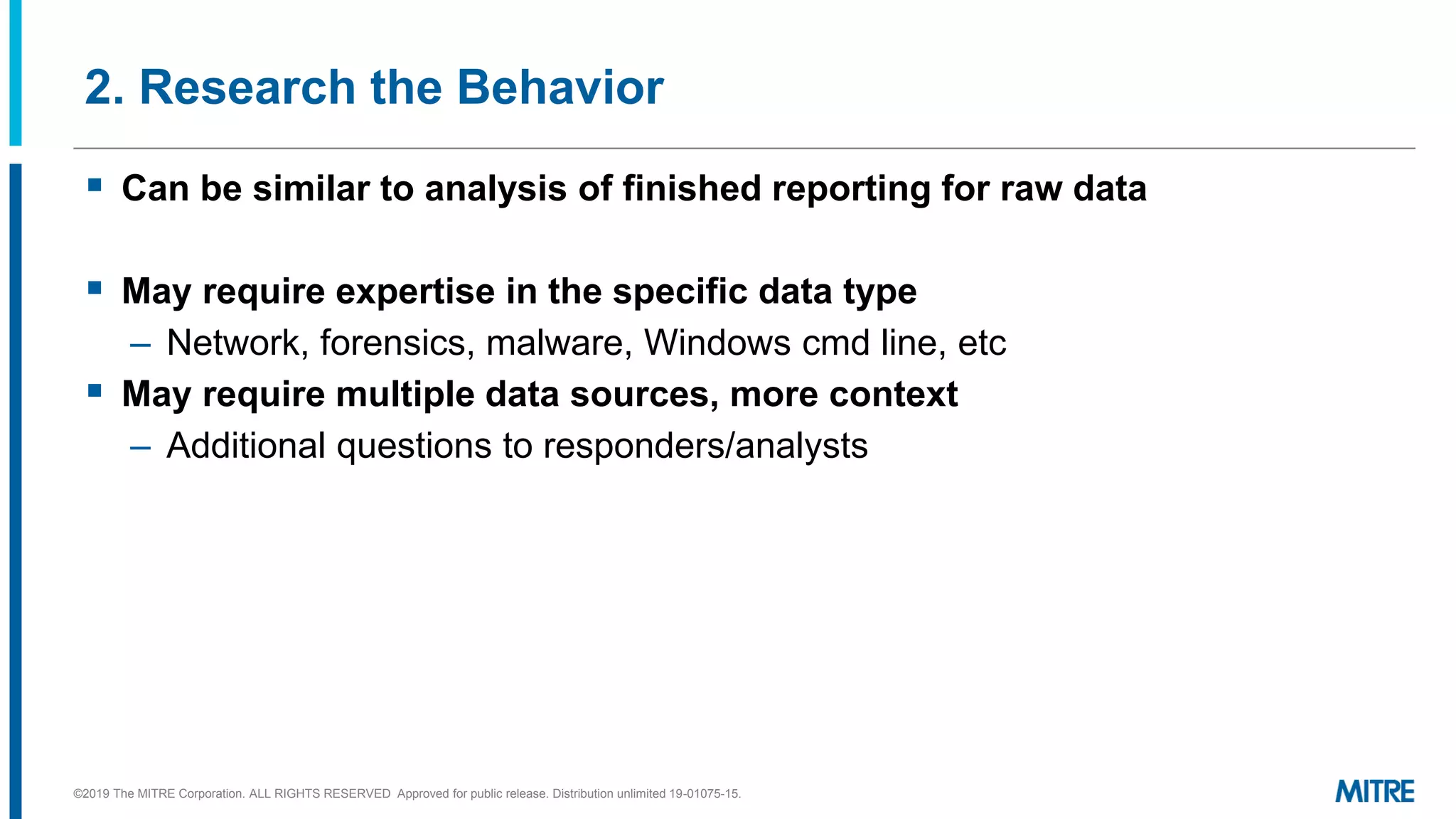
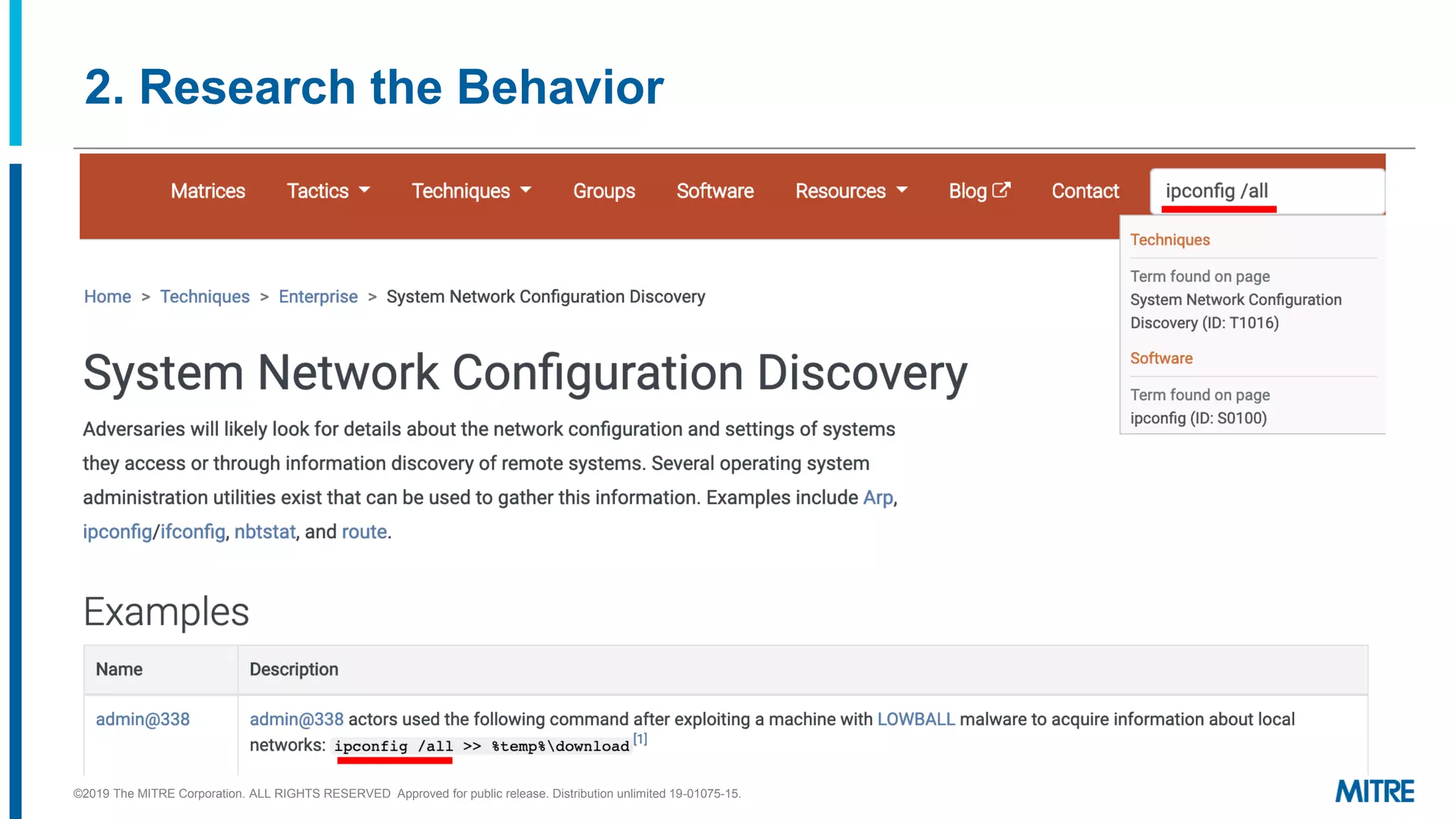
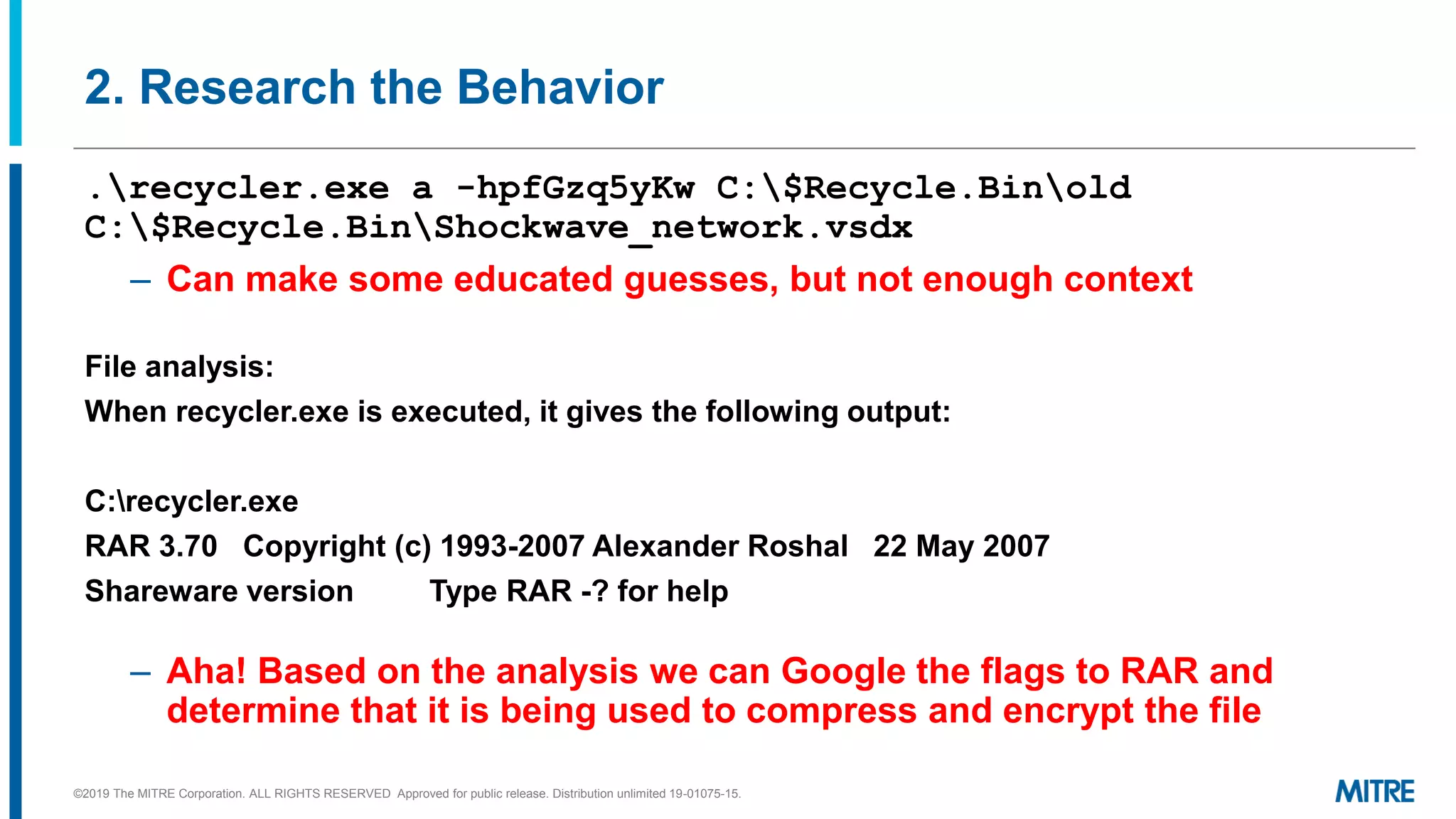
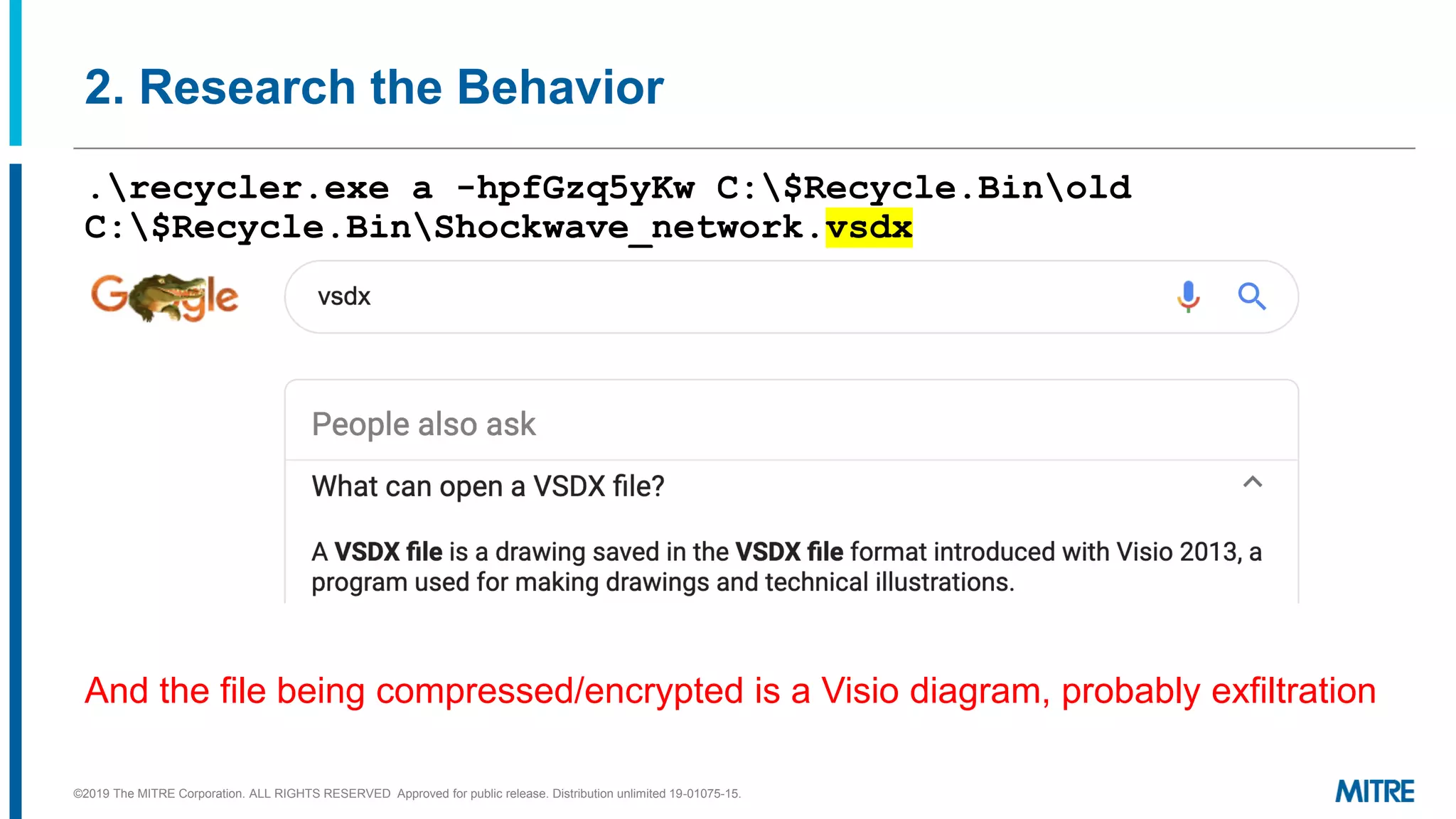
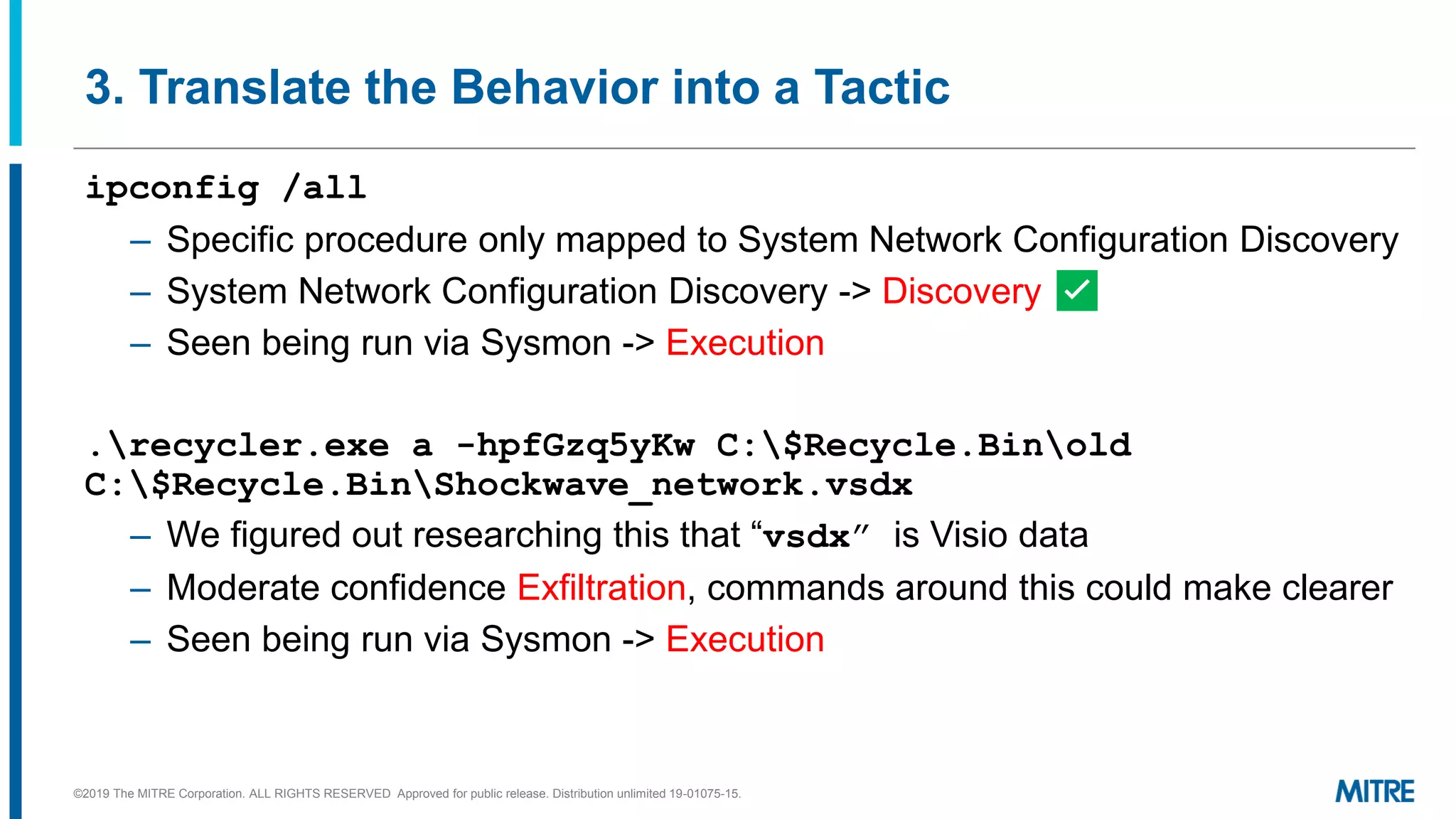
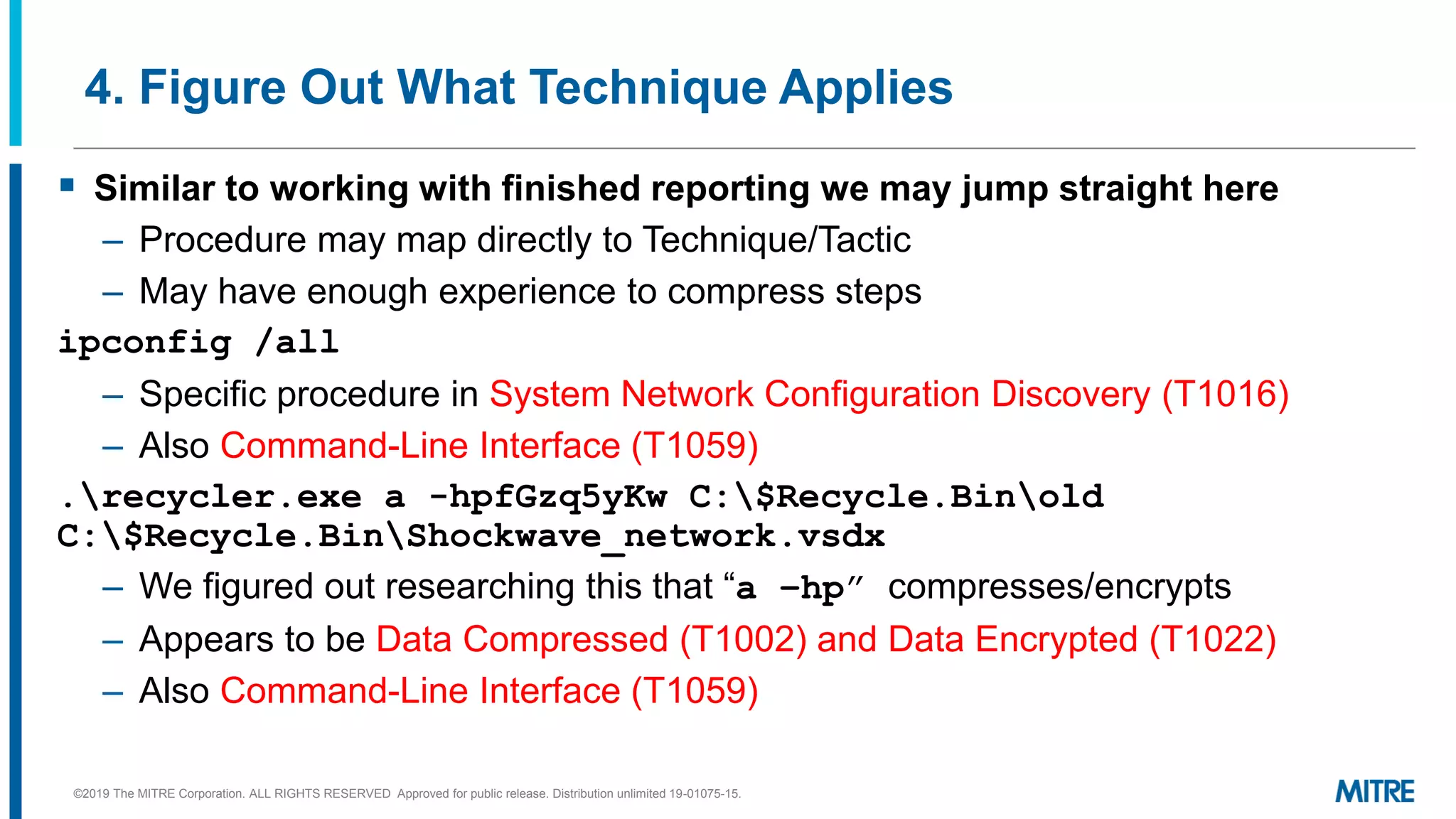
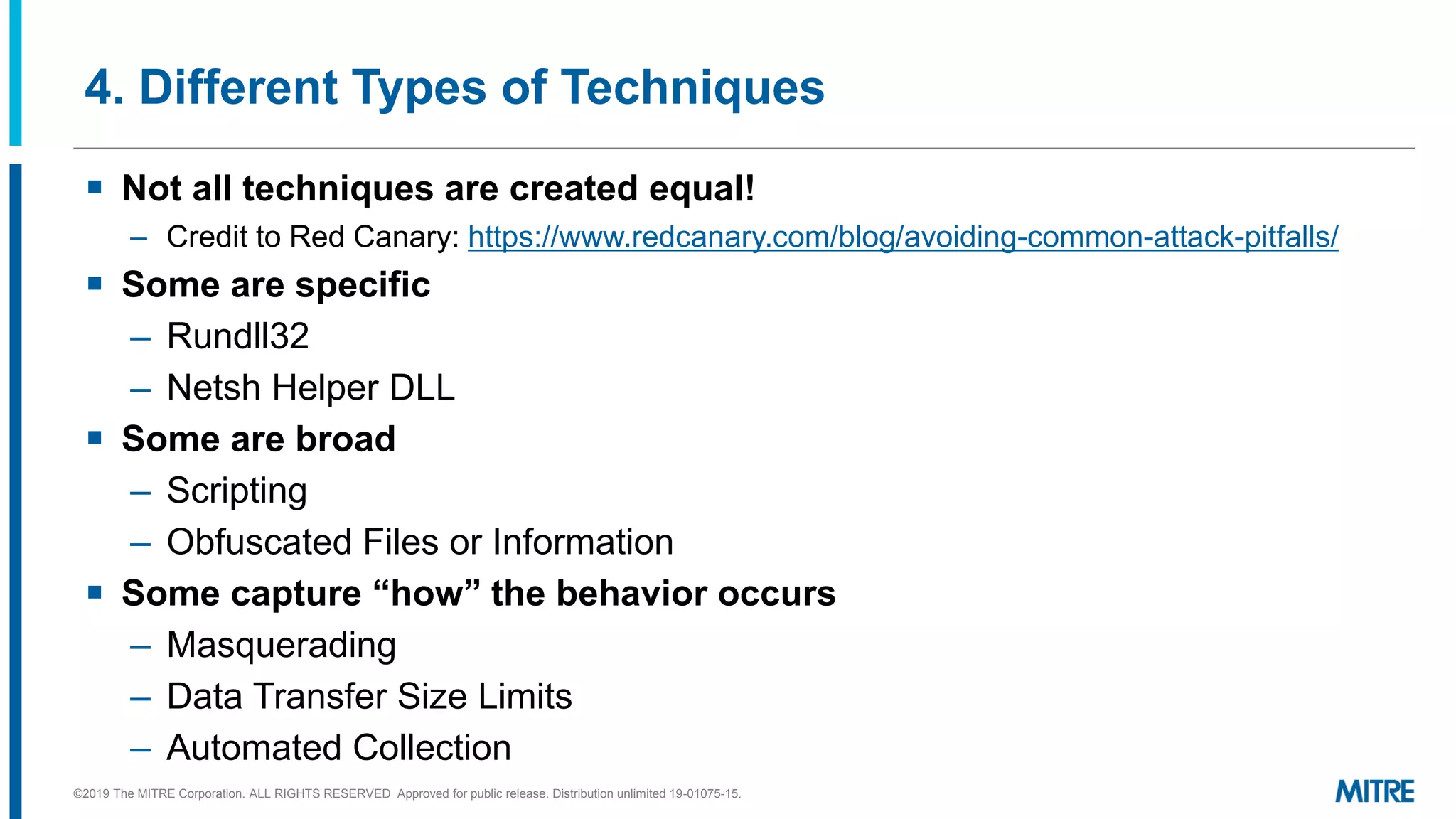
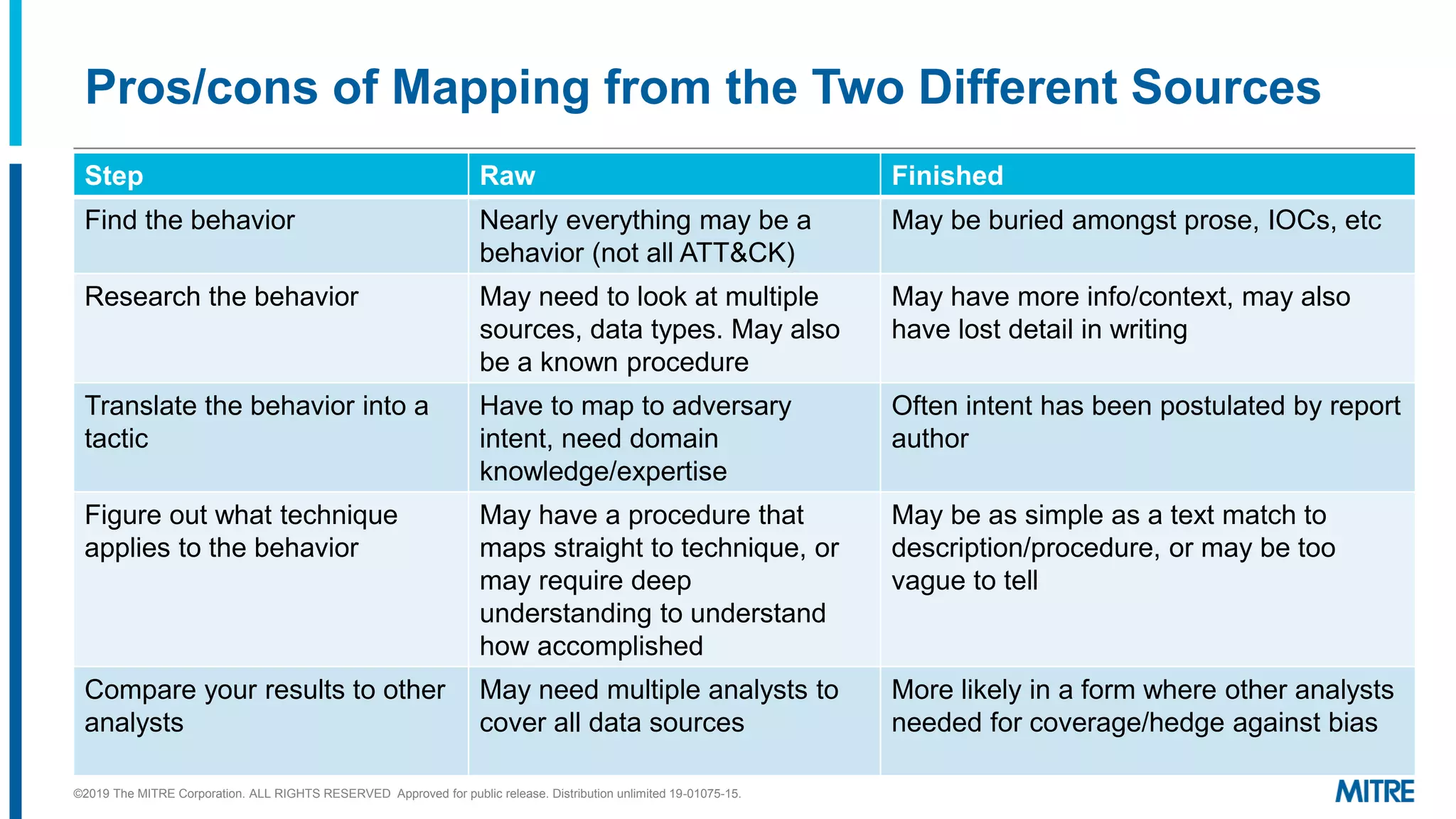
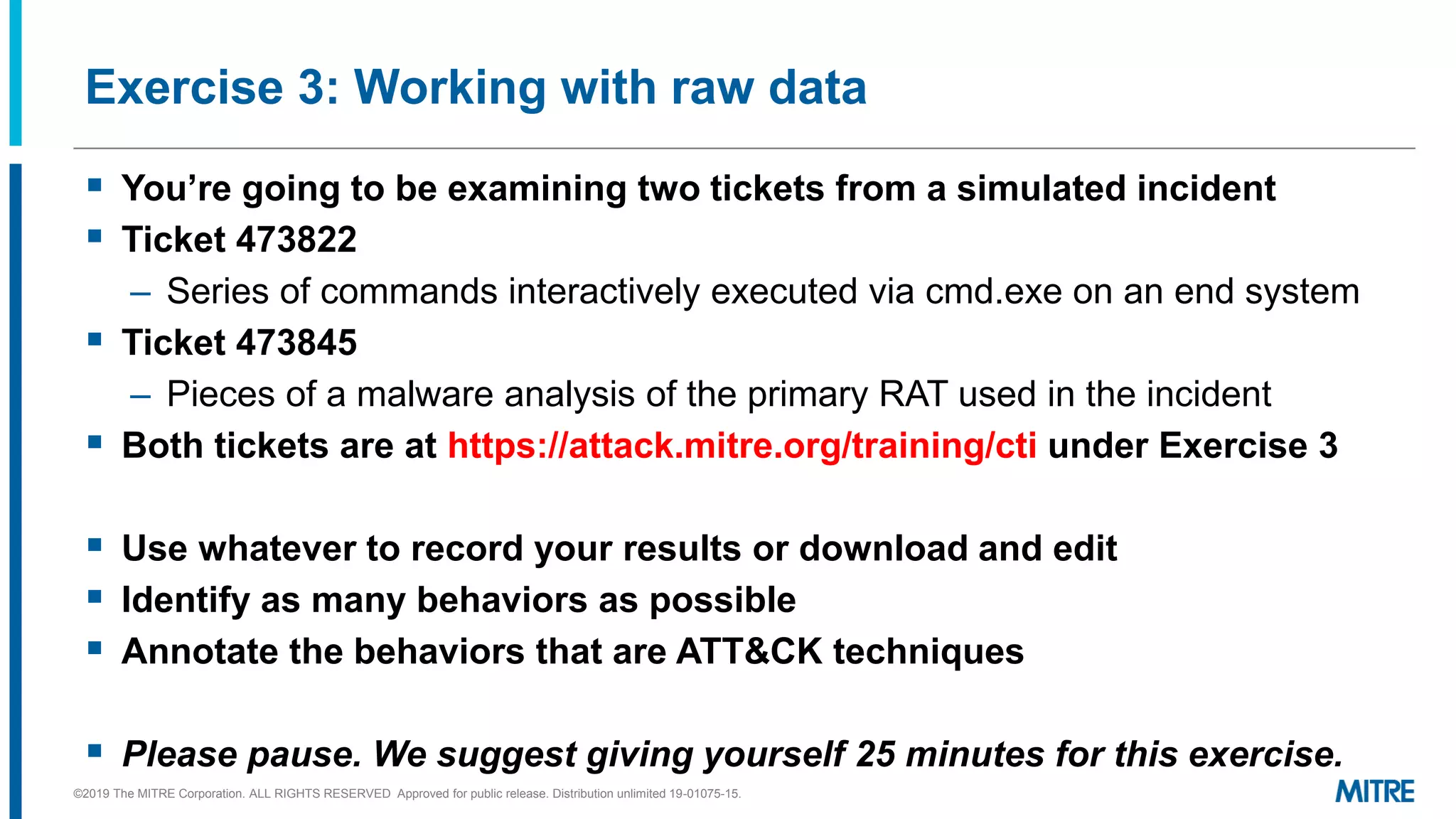
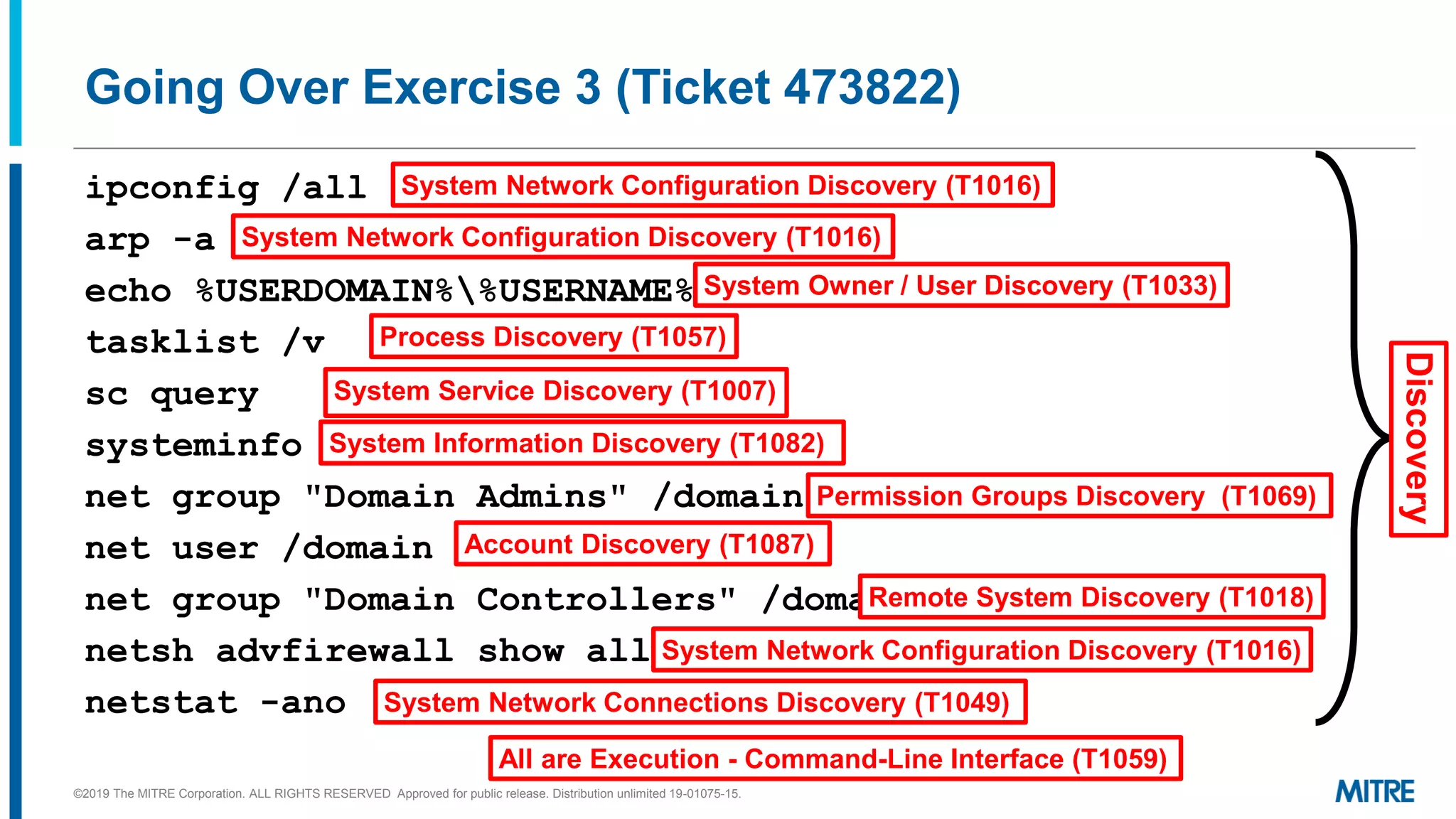
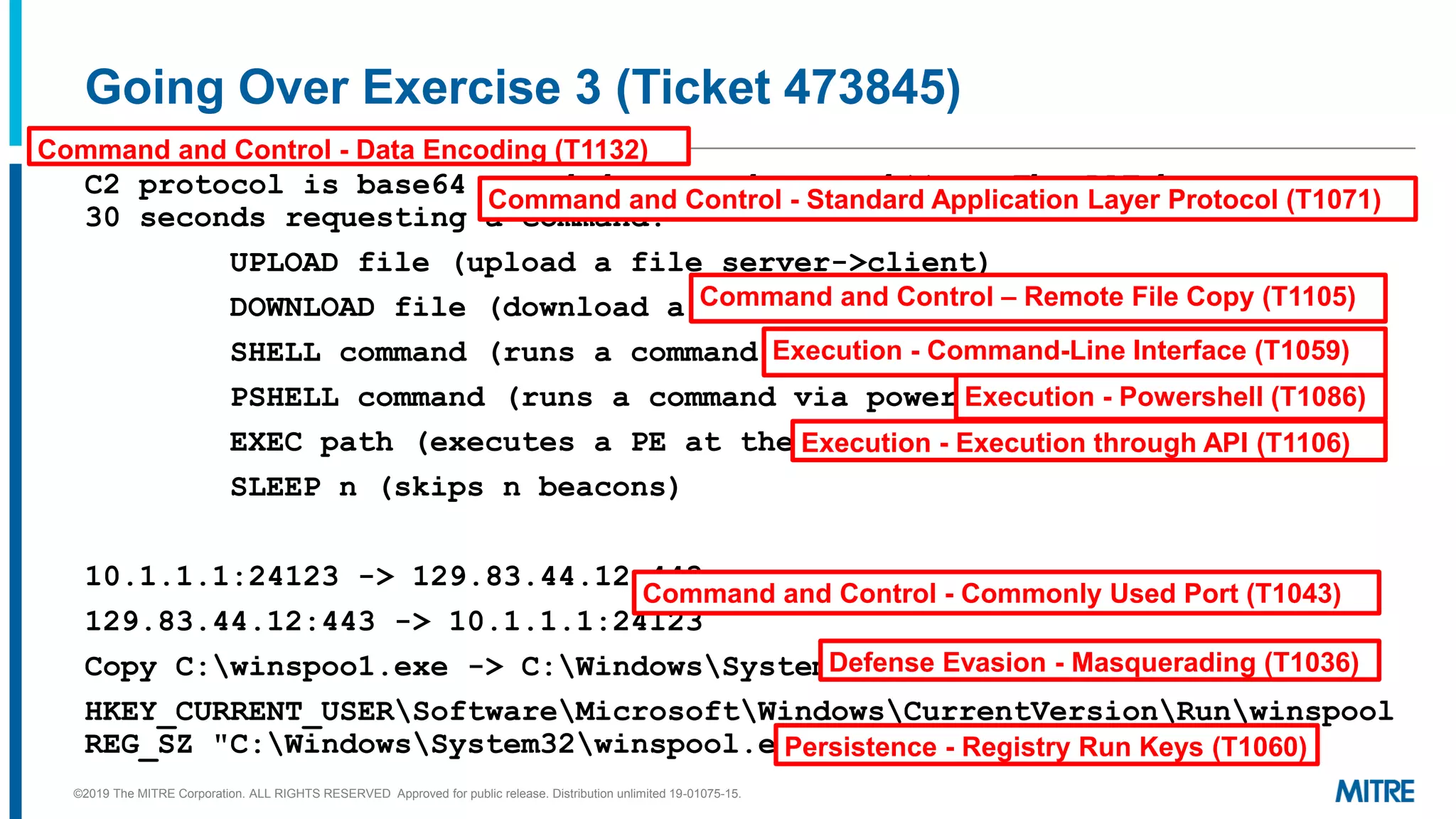
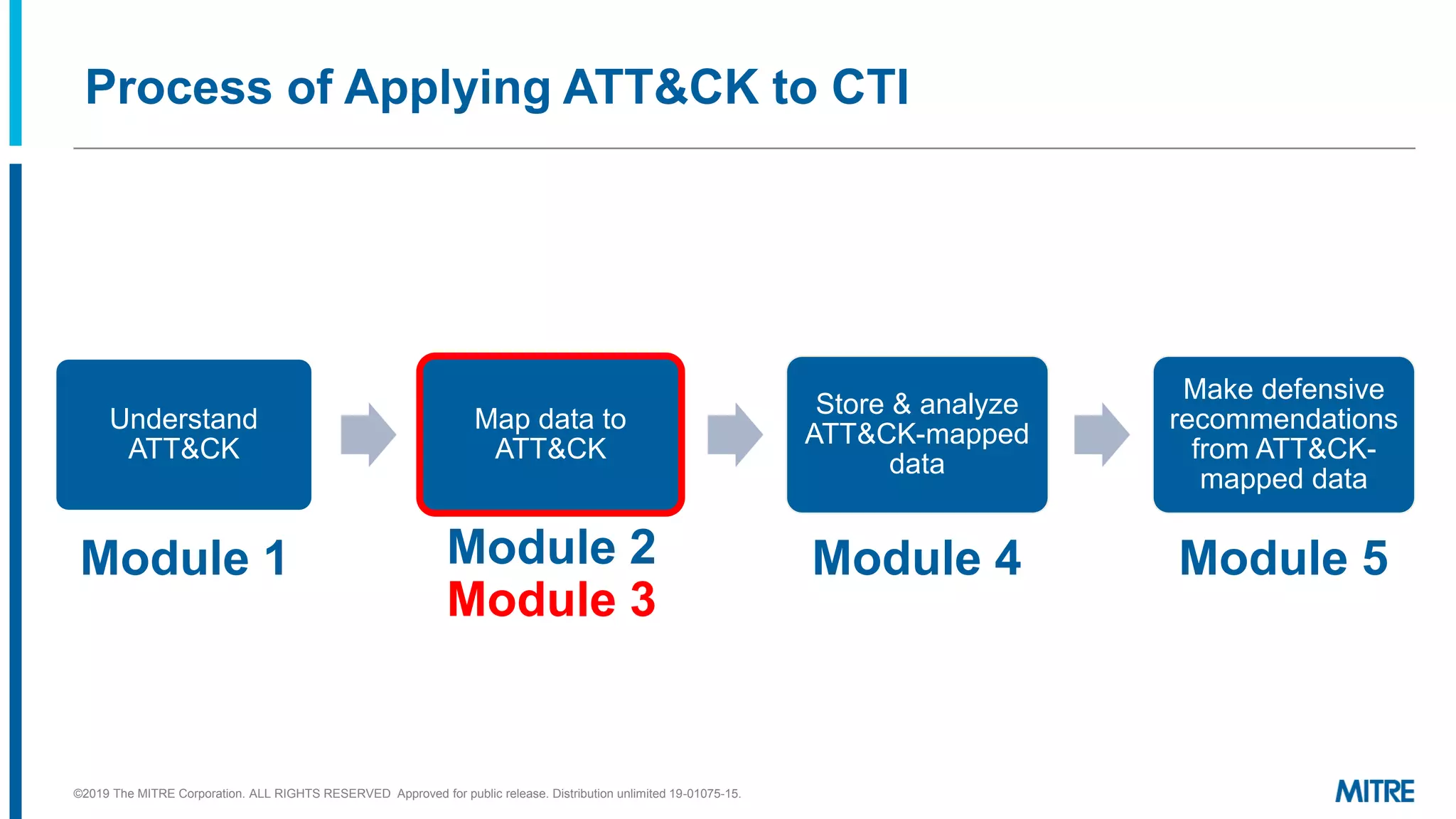
This document discusses mapping raw cyber threat data to the ATT&CK framework. It describes finding behaviors in raw data, researching the behaviors, translating them to ATT&CK tactics, and identifying the relevant ATT&CK techniques. The process includes comparing mappings to other analysts and understanding different types of techniques. An exercise demonstrates mapping behaviors from command line executions and malware analysis to ATT&CK.