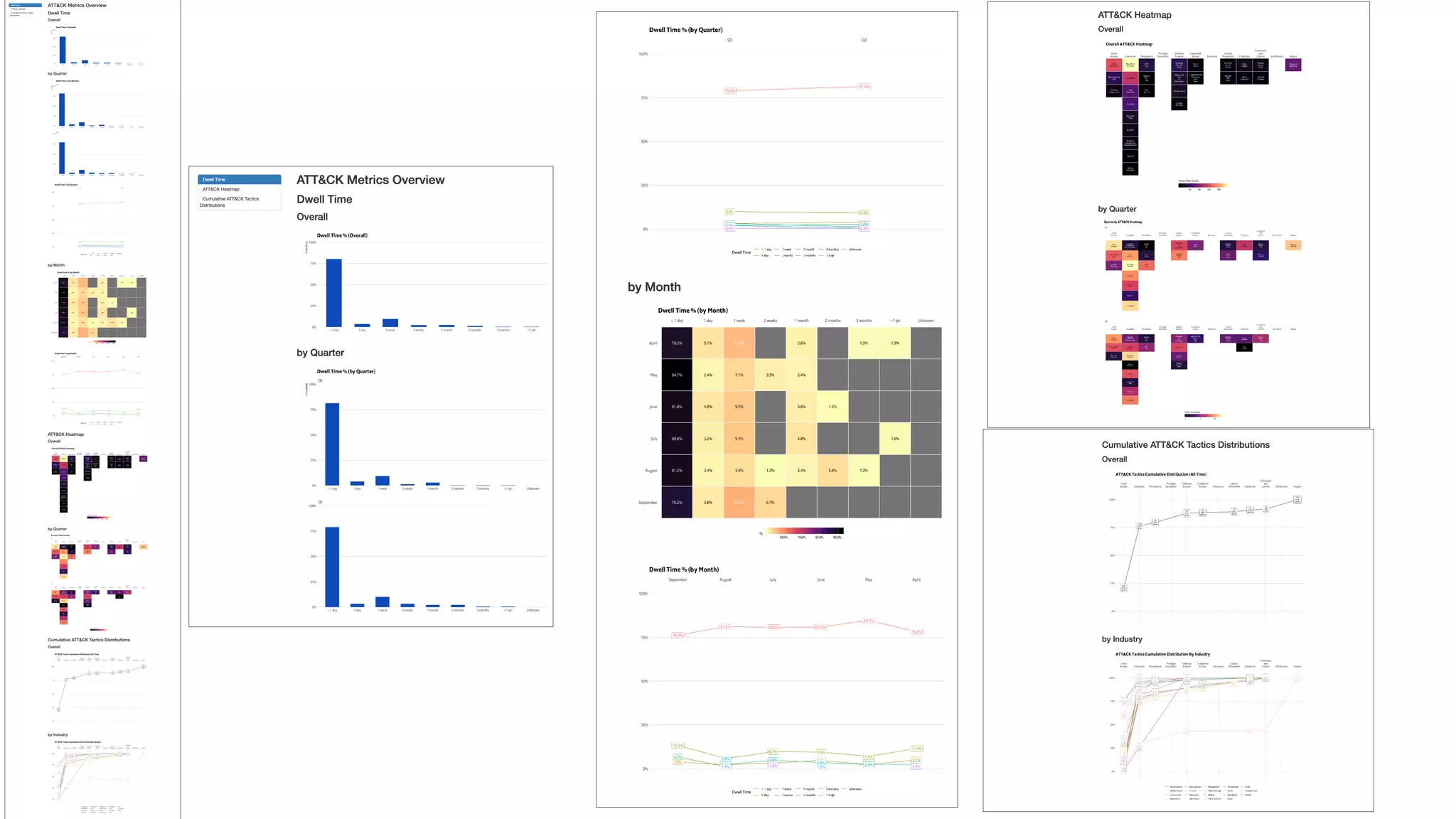
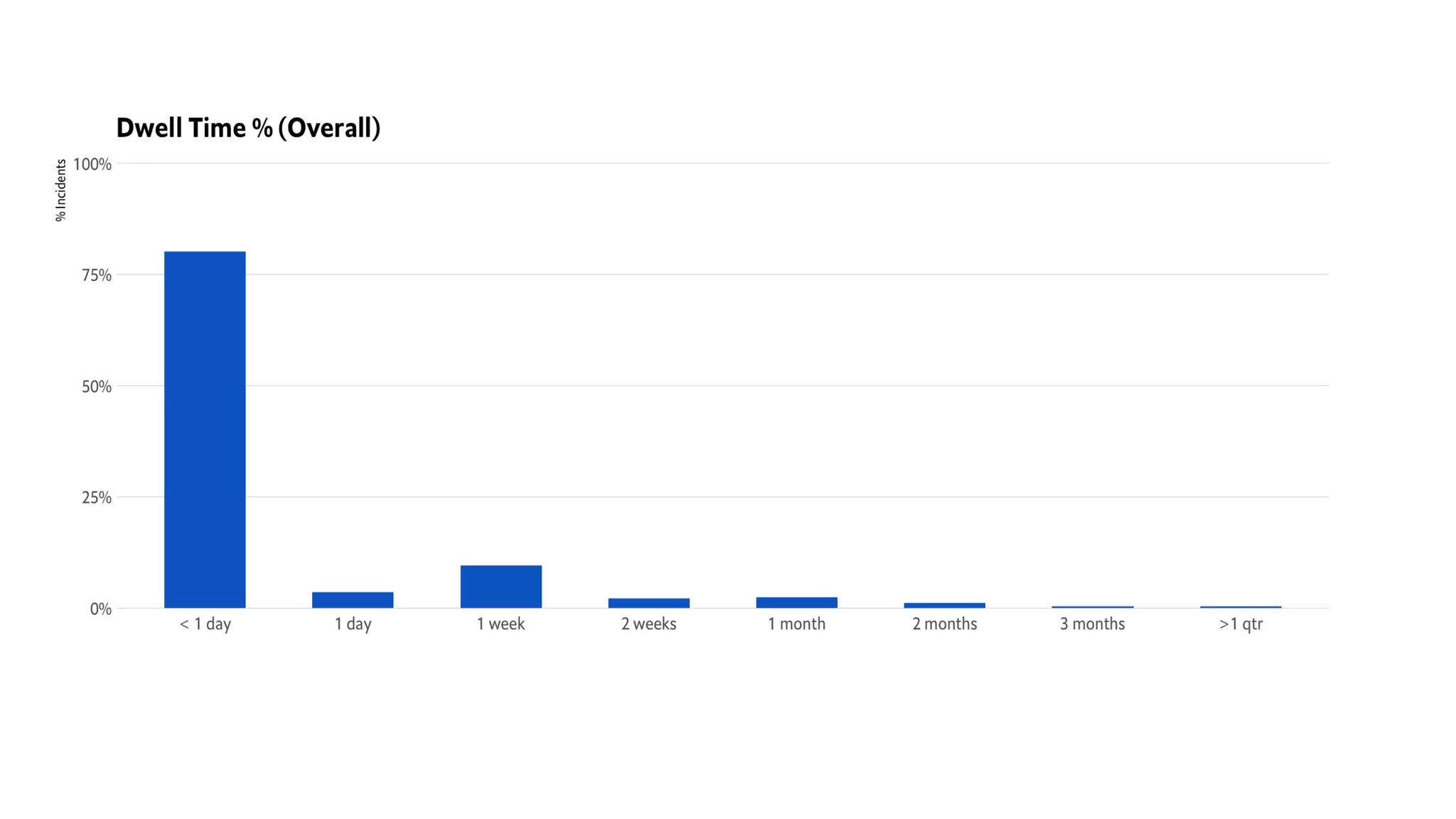
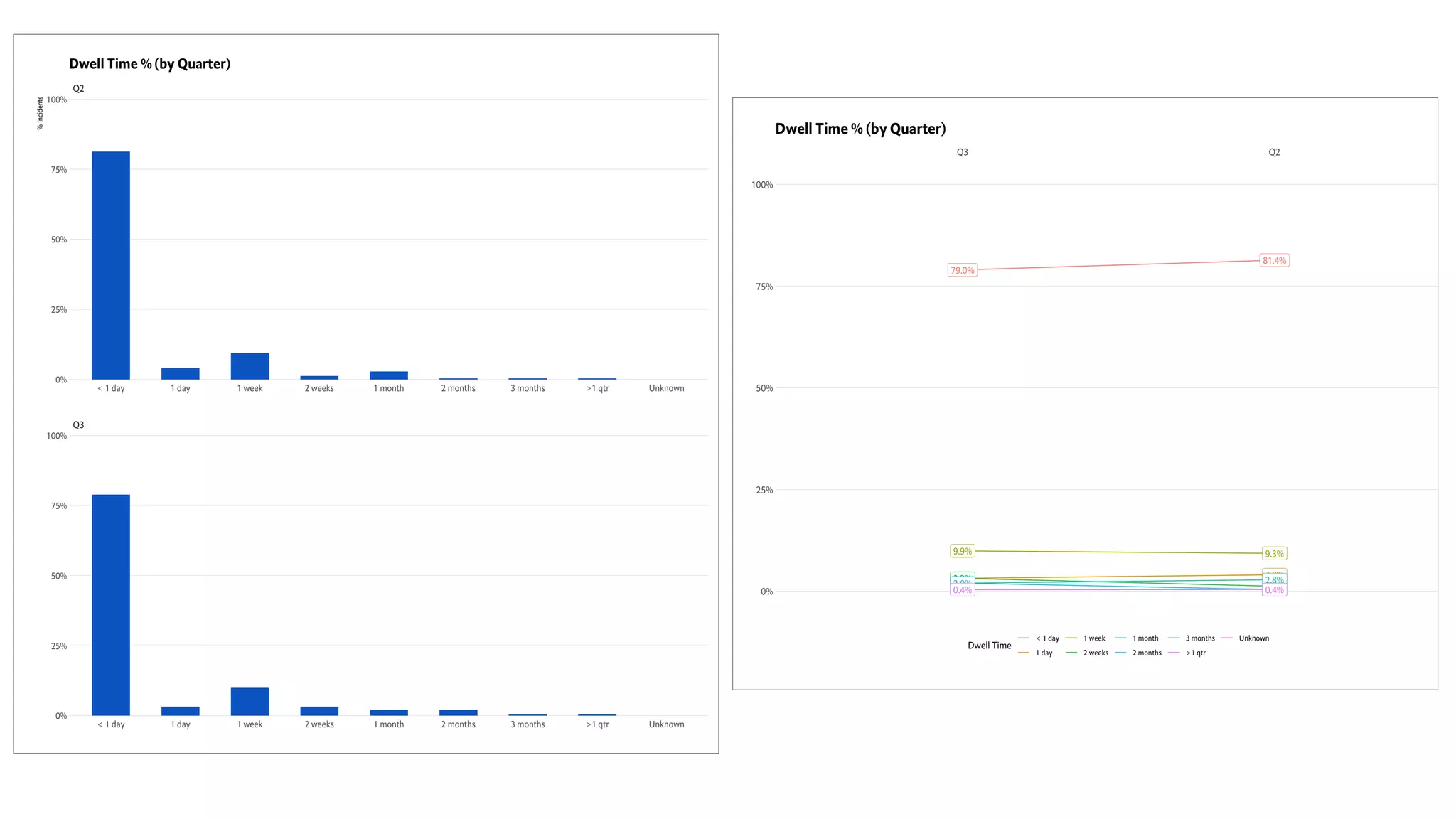
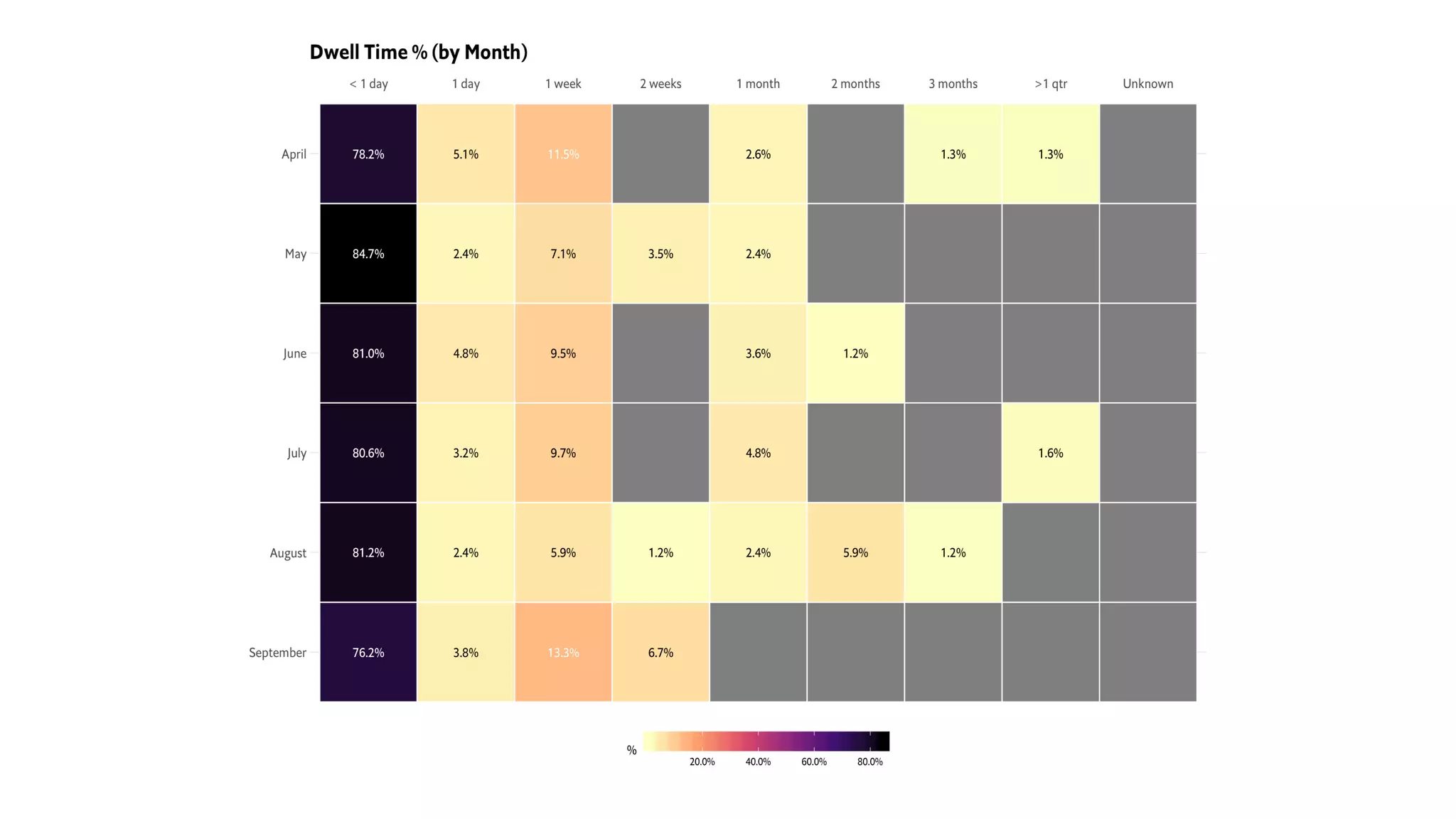
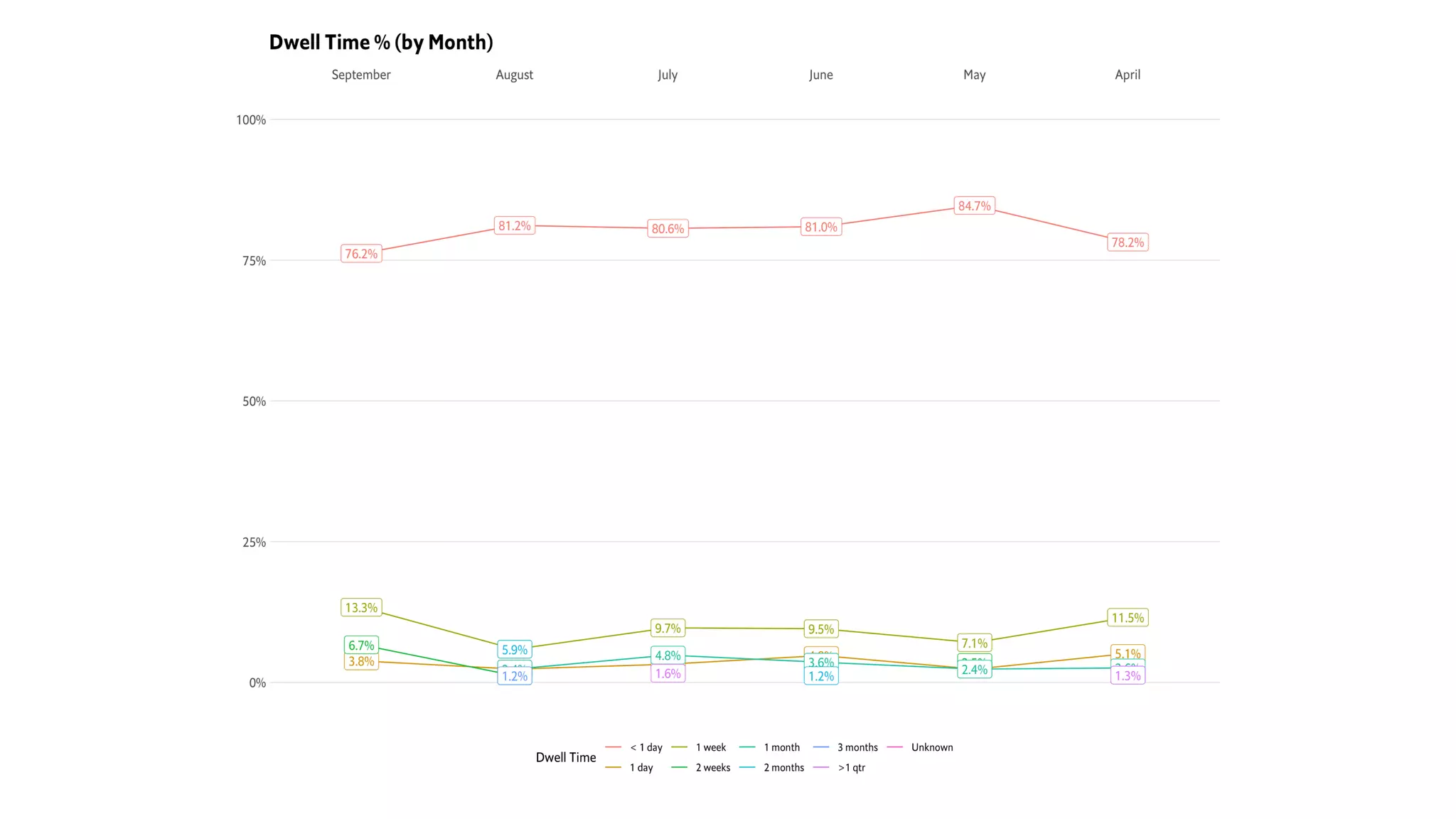
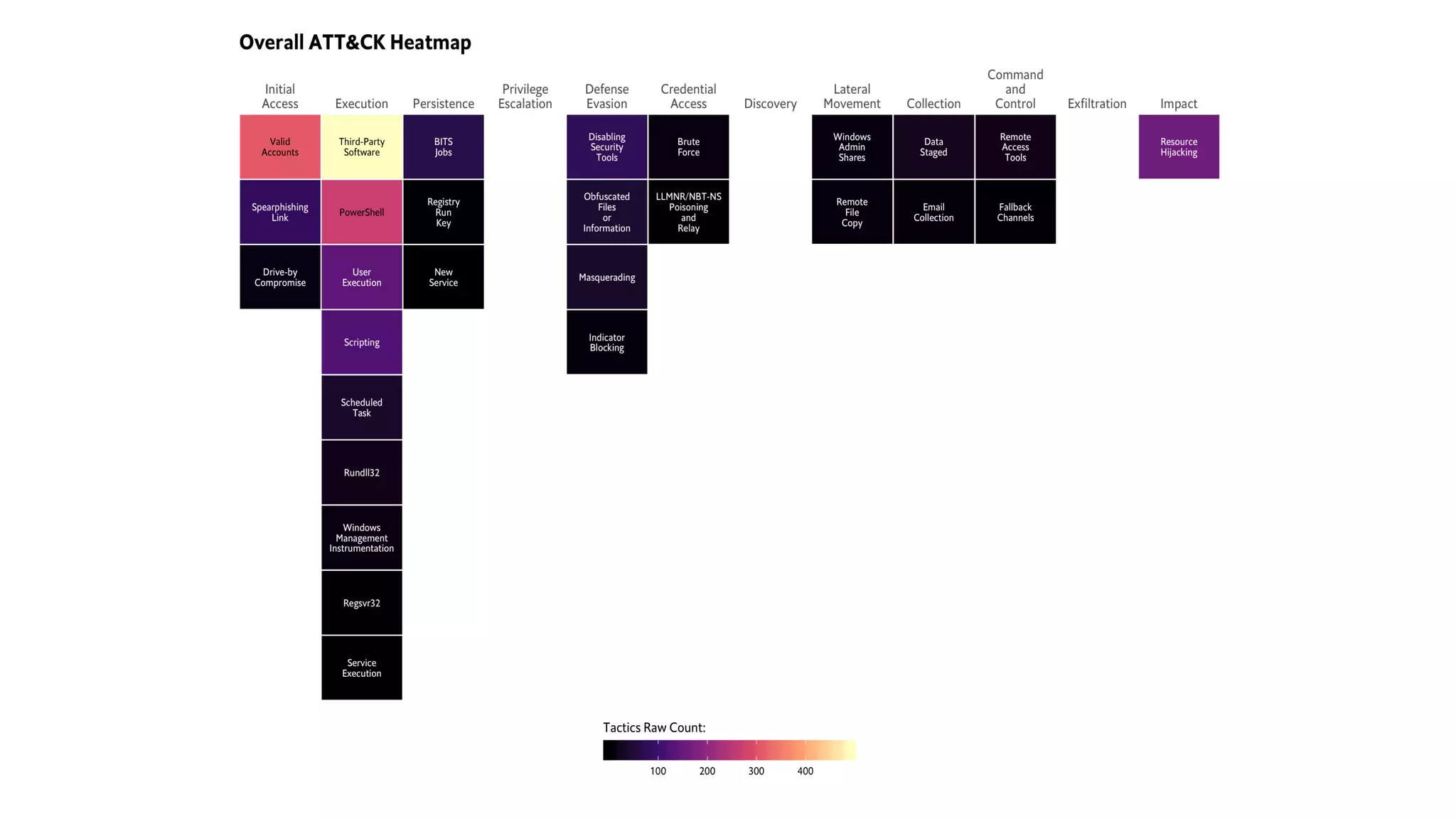
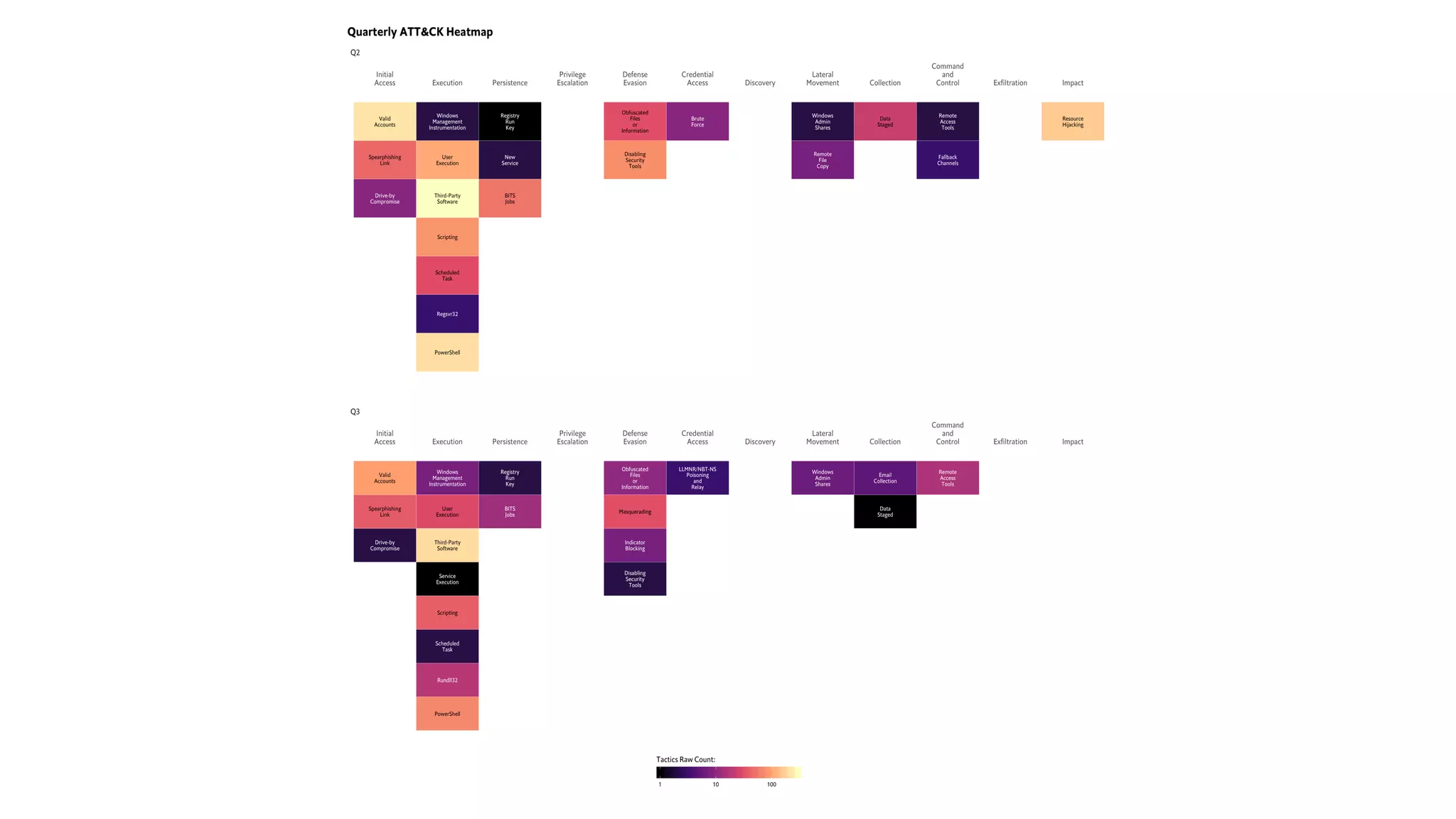
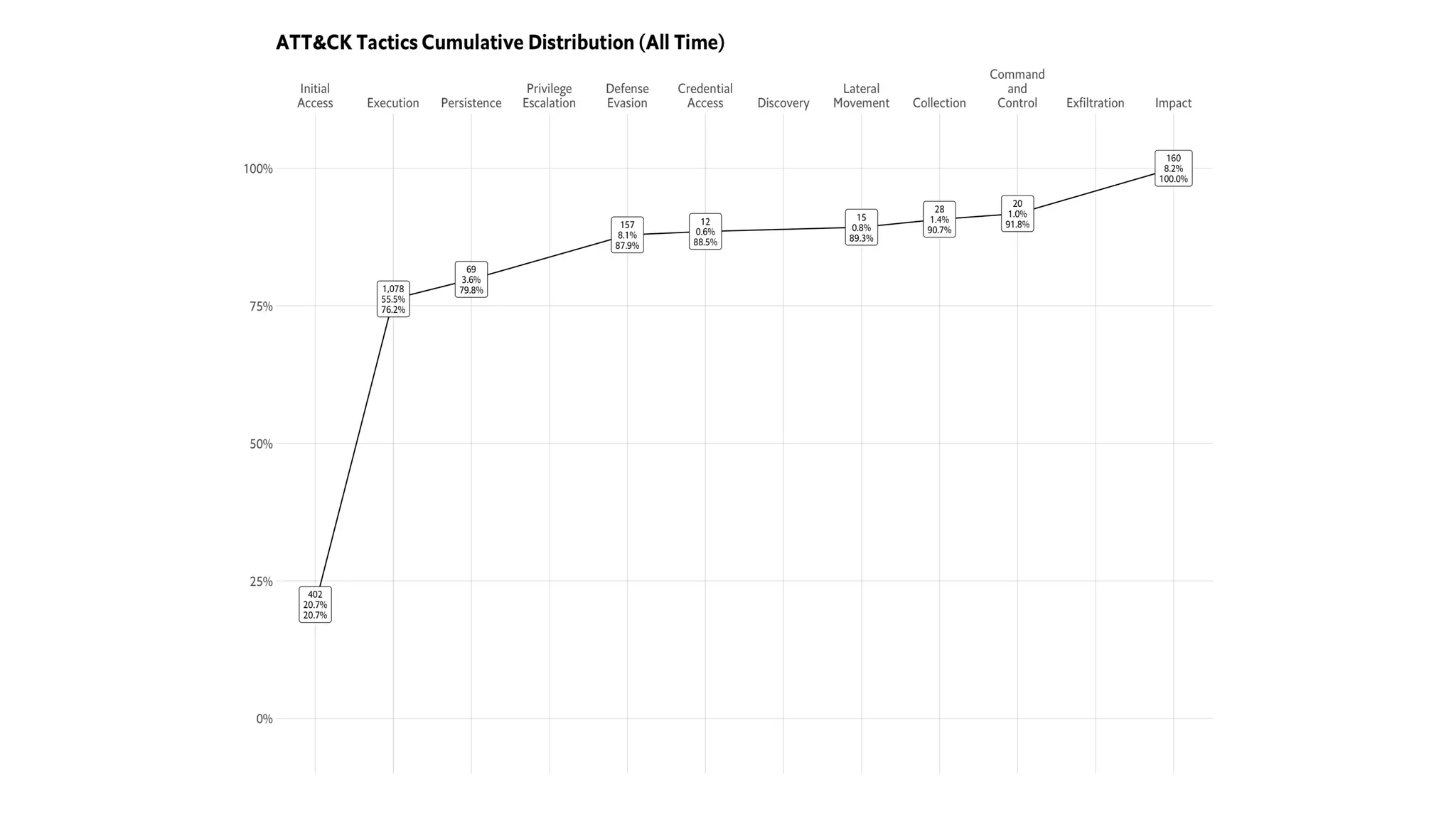
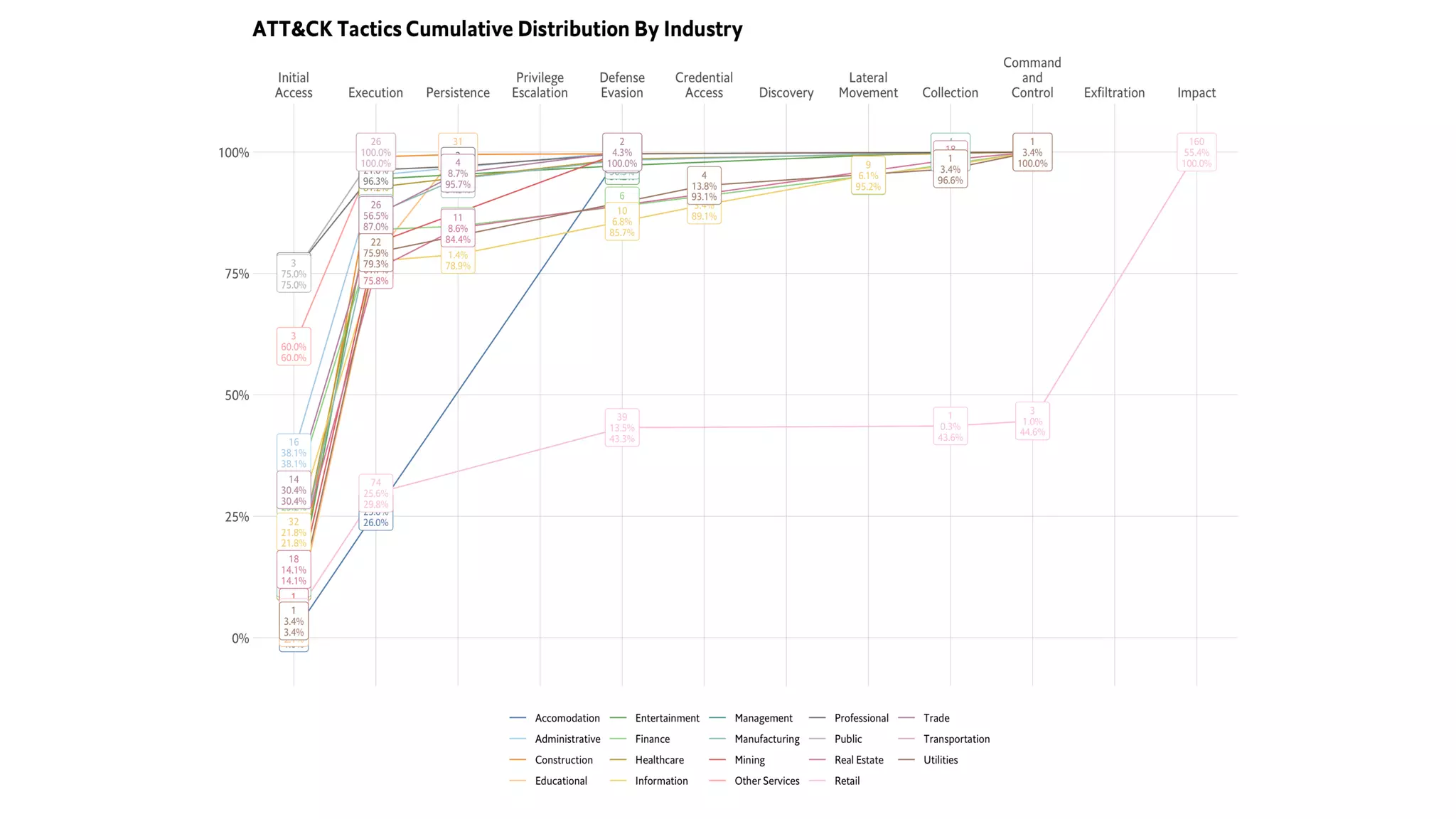
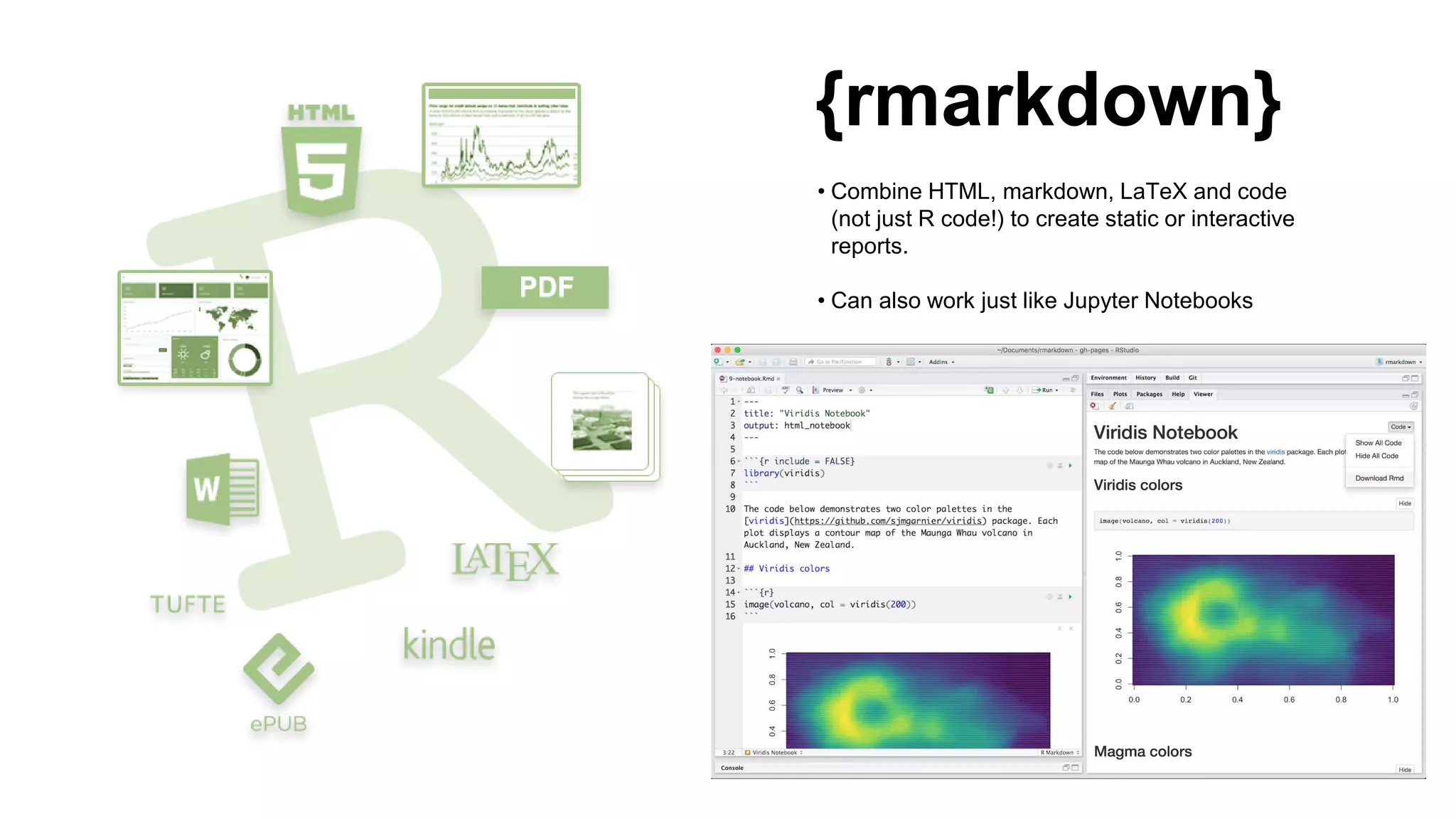
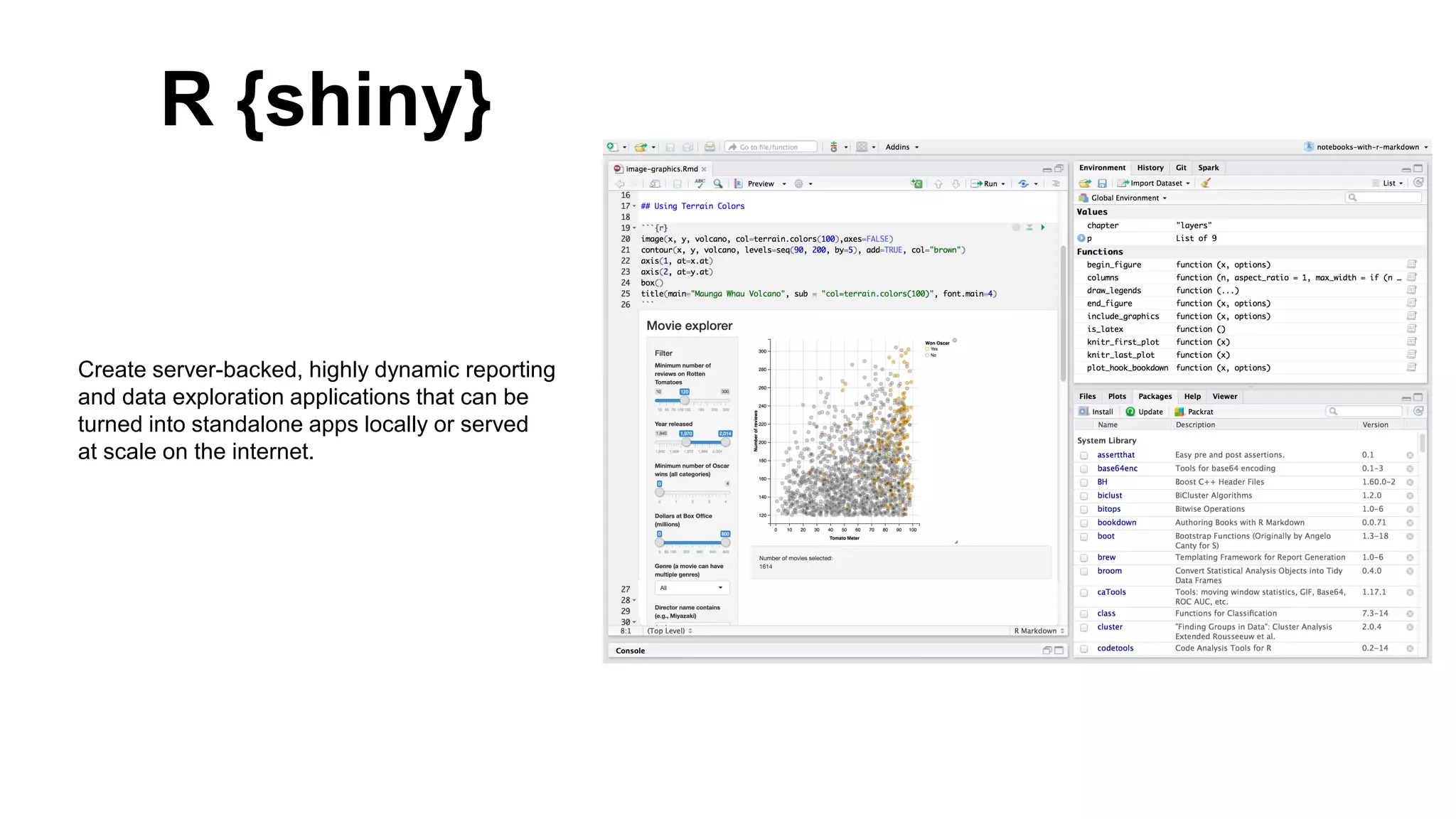
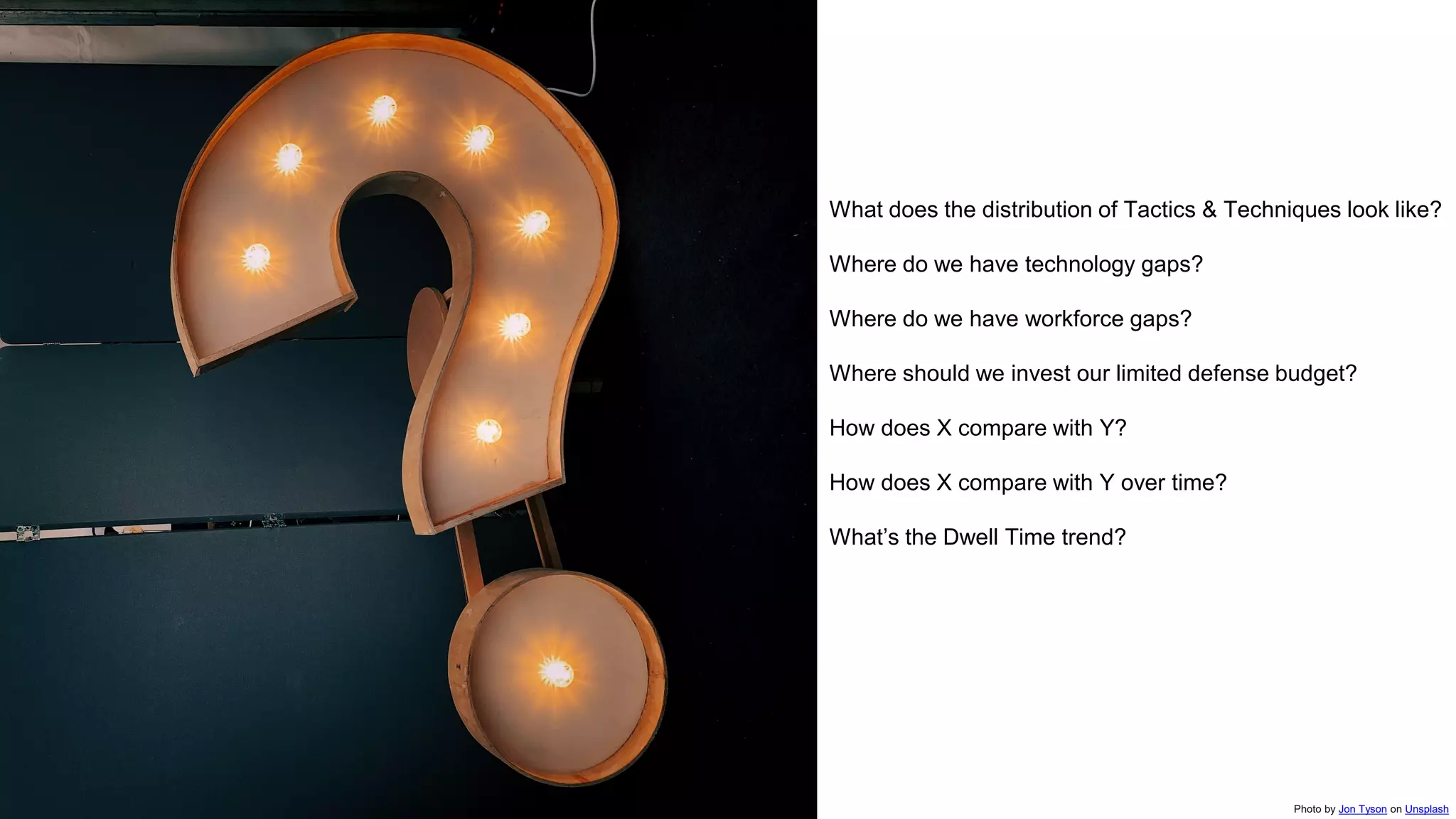
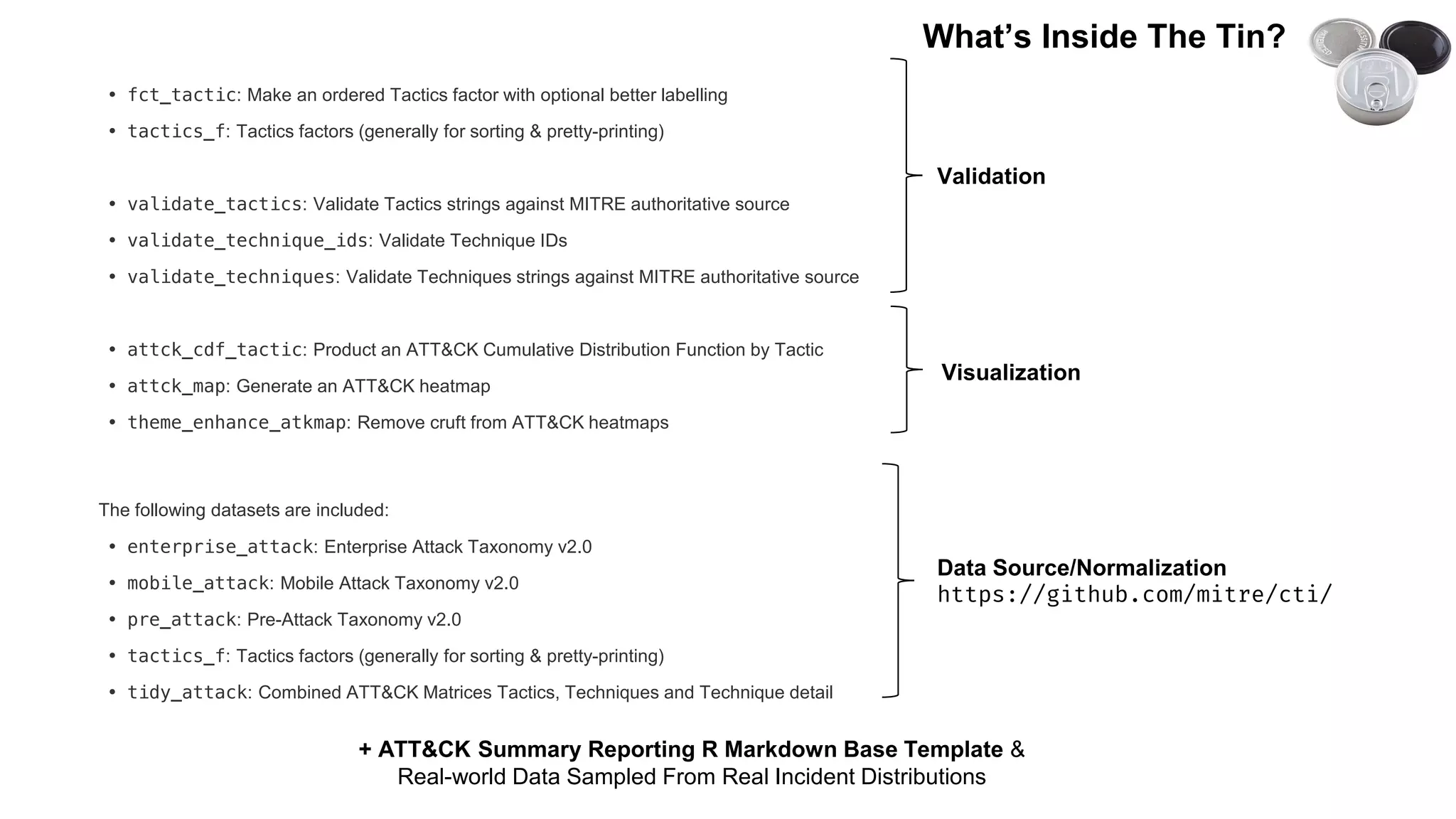
This document introduces attckr, an open-source toolkit for analyzing and visualizing ATT&CK incident data. It provides concise summaries of ATT&CK tactics and techniques from real-world incidents. Attckr includes functions for validating, normalizing, and visualizing ATT&CK data. It produces heatmaps and distributions of ATT&CK tactics to help analyze technology and workforce gaps. The toolkit is designed for use in R and can create interactive reports and dashboards from ATT&CK data without coding.






![[
{
"first_event_ts": "2019-05-21 13:54:03",
"first_alert_ts": "2019-05-21 13:54:03",
"containment_ts": "2019-05-21 14:02:38",
"org": "ac33b693",
"mitre_attack": [
{
"tactic": "Execution",
"technique": "Third-Party Software",
"id": "T1072"
},
{
"tactic": "Execution",
"technique": "Third-Party Software",
"id": "T1072"
},
{
"tactic": "Persistence",
"technique": "BITS Jobs",
"id": "T1197"
},
{
"tactic": "Execution",
"technique": "Third-Party Software",
"id": "T1072"
},
{
"tactic": "Persistence",
"technique": "BITS Jobs",
"id": "T1197"
},
{
"tactic": "Execution",
"technique": "Third-Party Software",
"id": "T1072"
}
],
"industry": "Manufacturing"
}
]](https://image.slidesharecdn.com/mitreattckcon2019attckr-toolkitforanalysisandvisualizationrudisrapid7-191114200701/75/MITRE-ATT-CKcon-2-0-attckr-A-Toolkit-for-Analysis-and-Visualization-of-ATT-CK-Incident-Data-for-Service-Providers-and-Organizations-Bob-Rudis-Rapid7-14-2048.jpg)