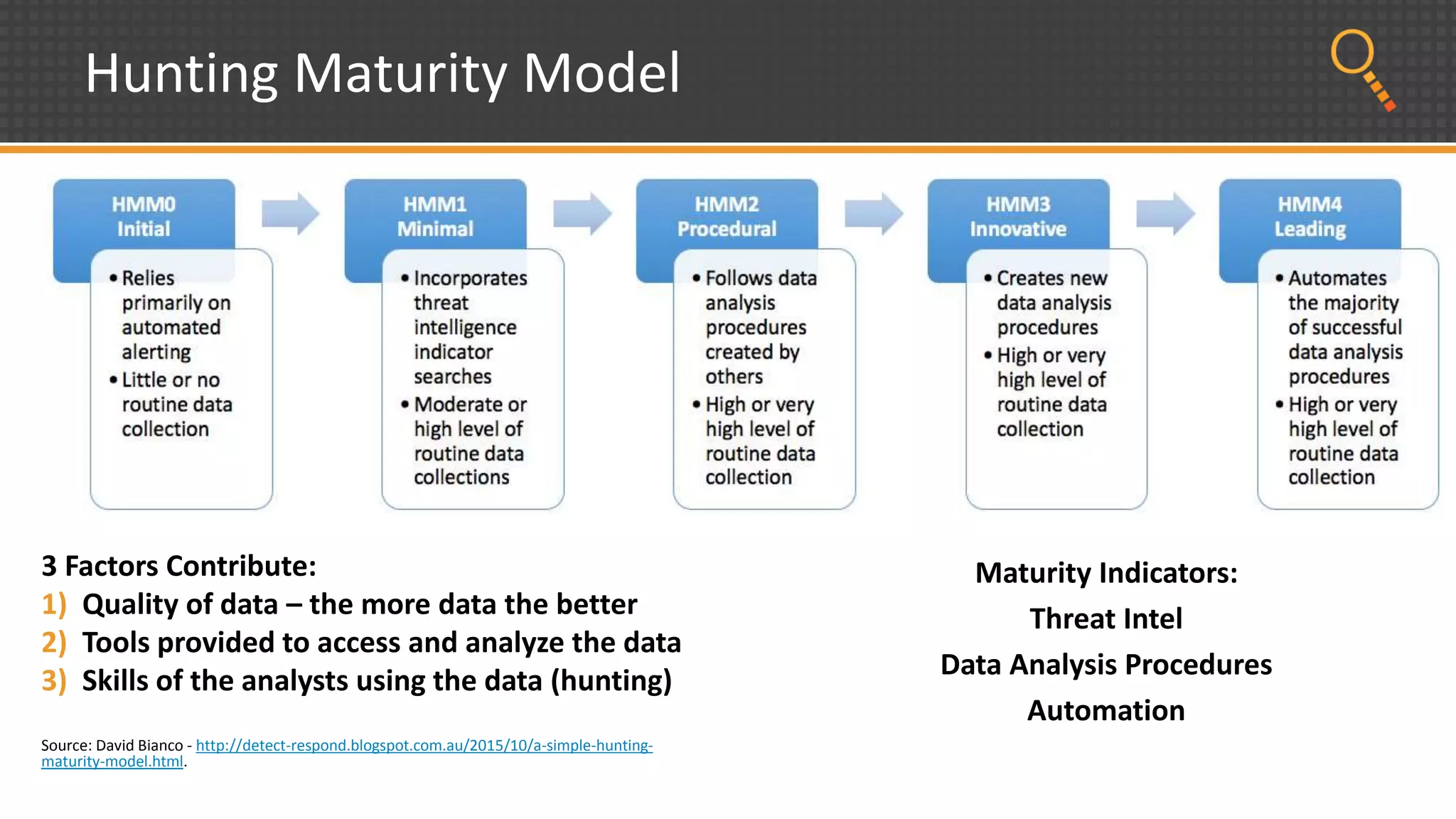
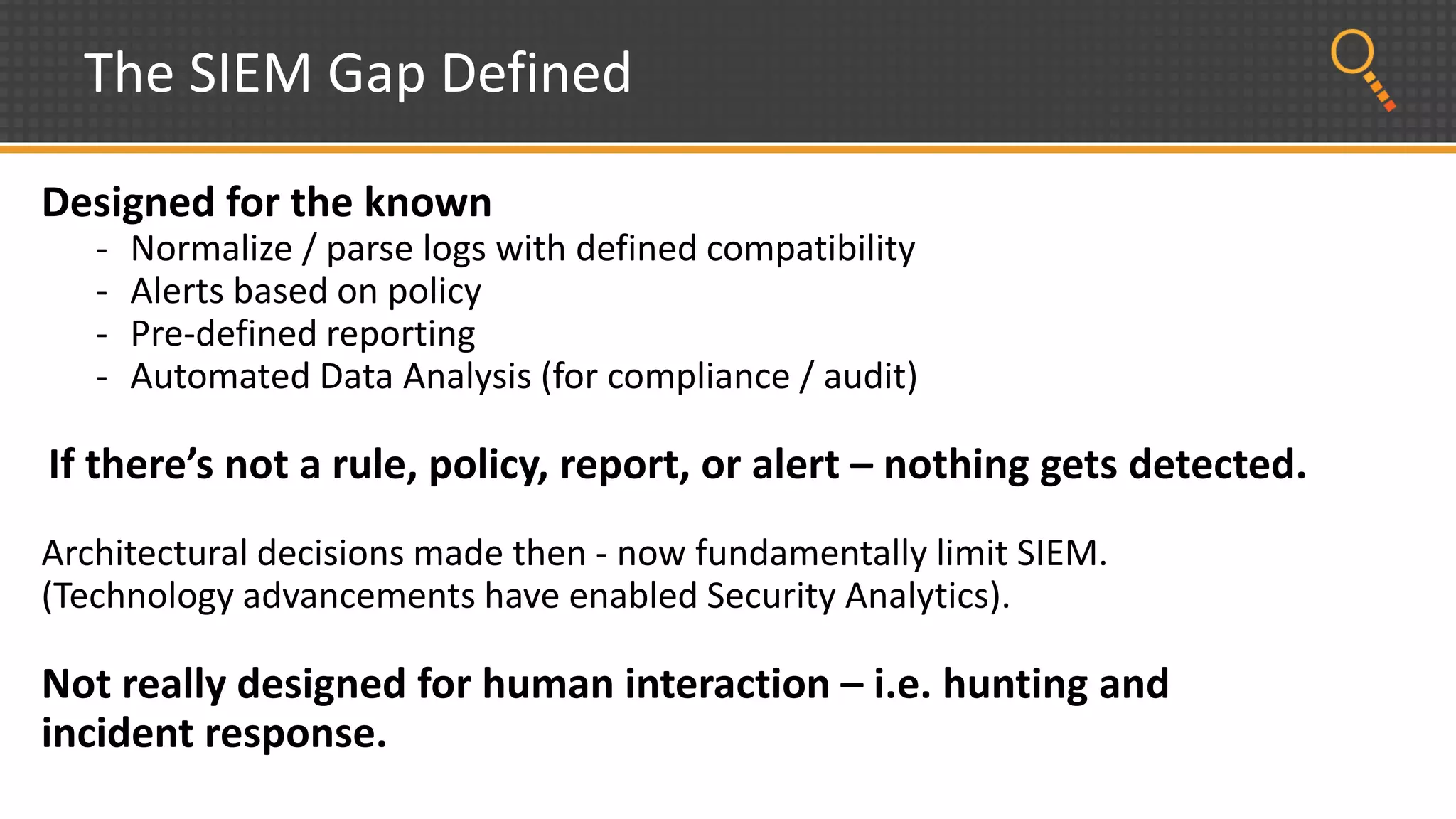
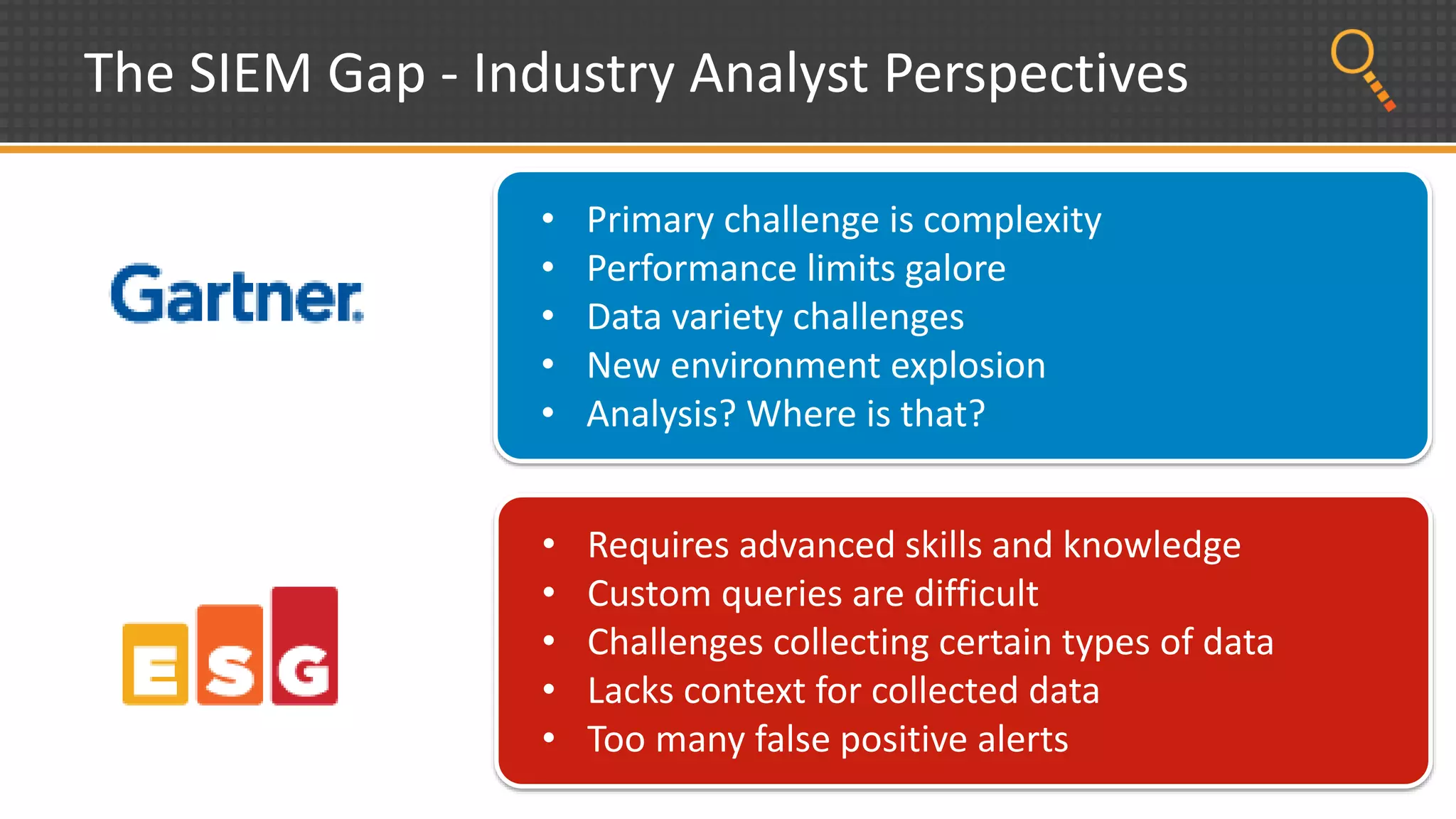
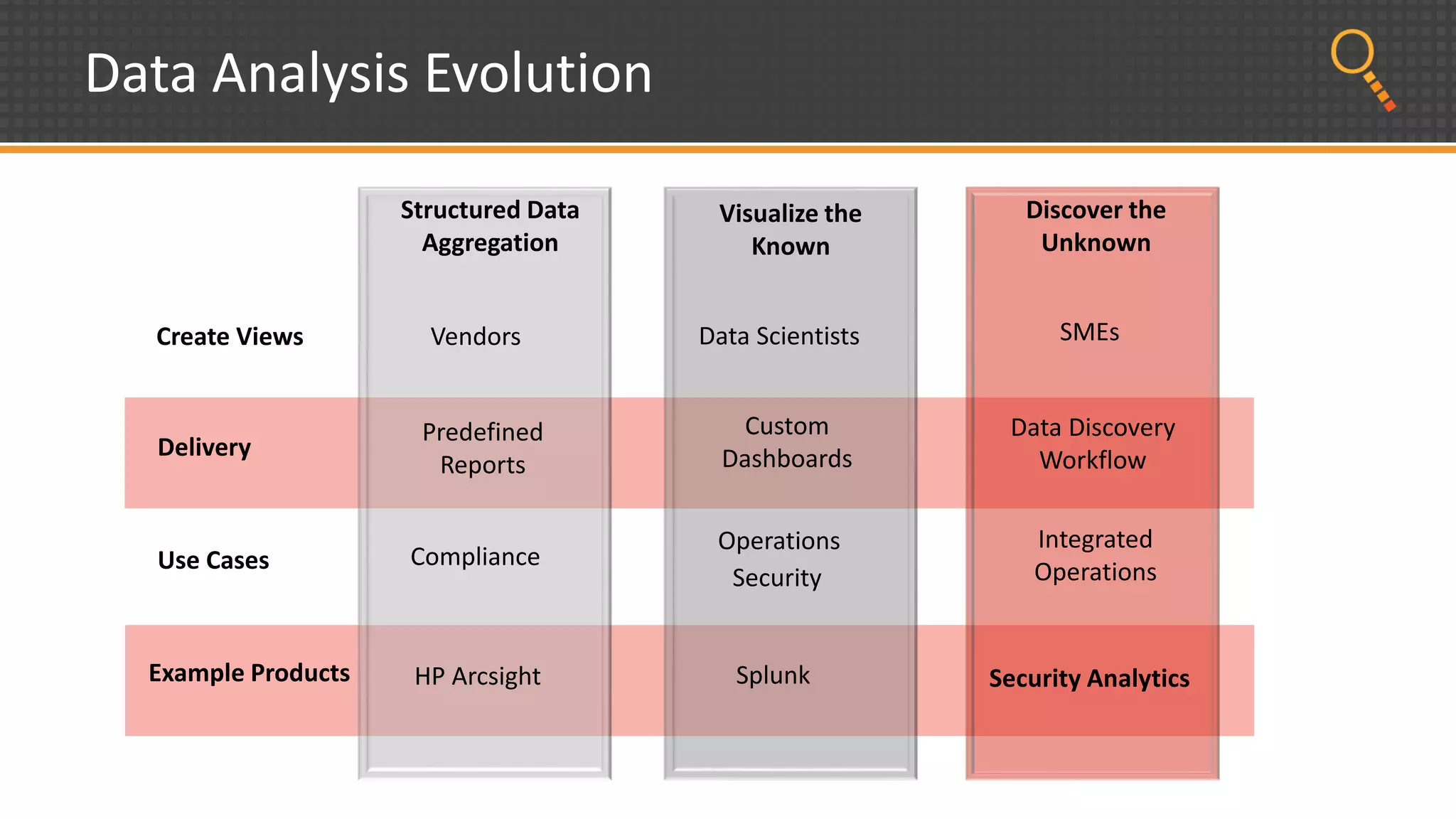
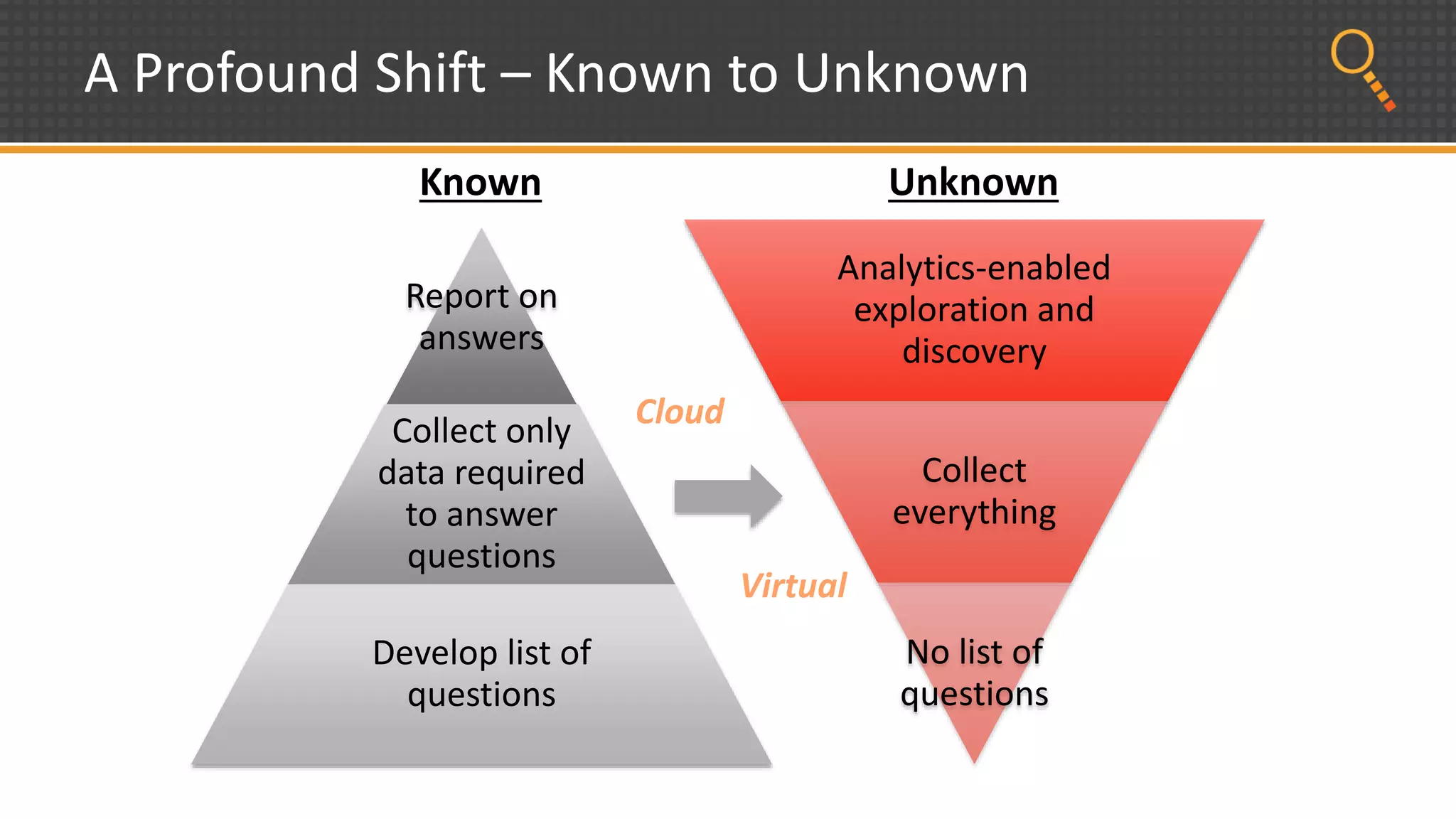
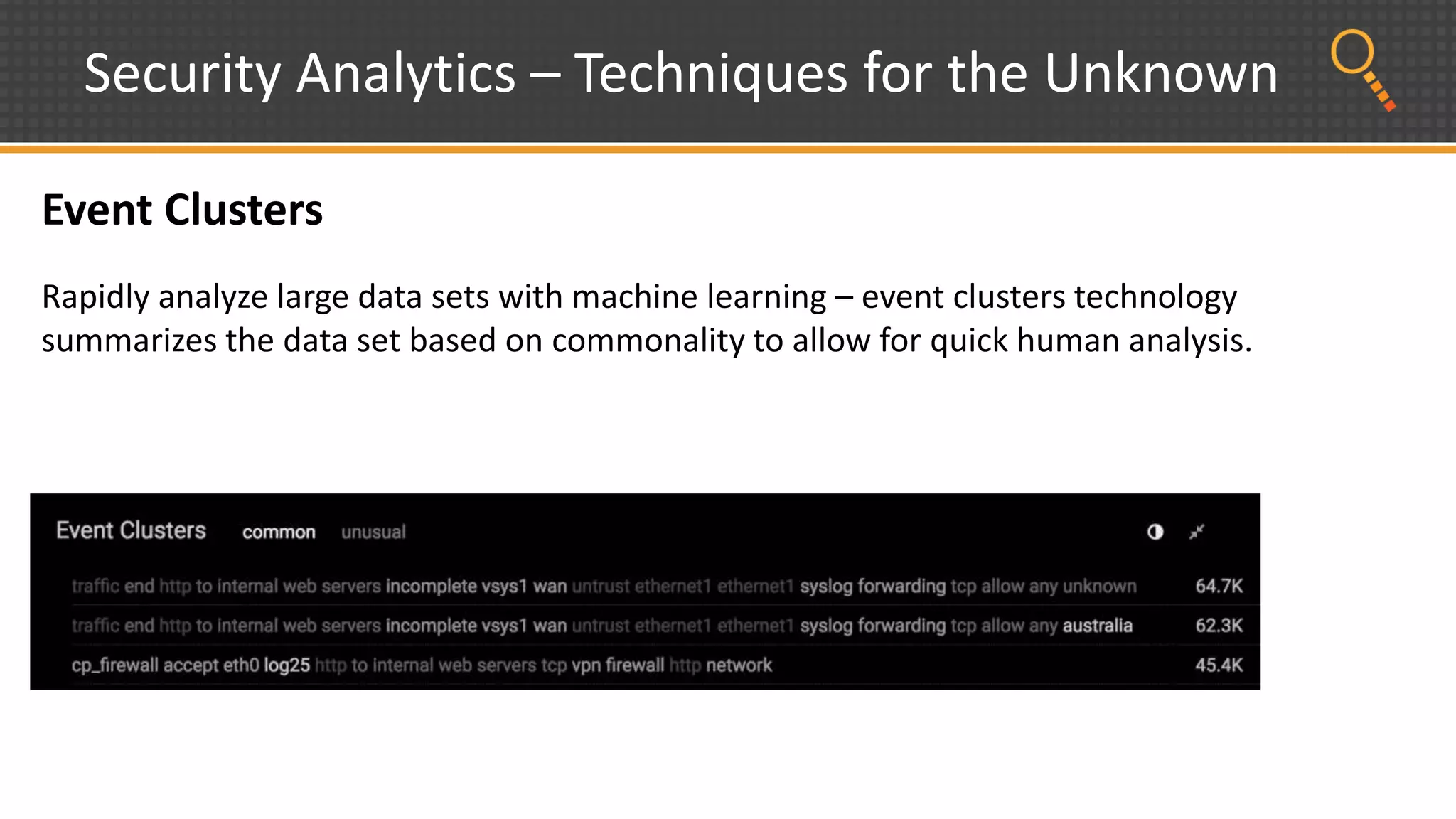
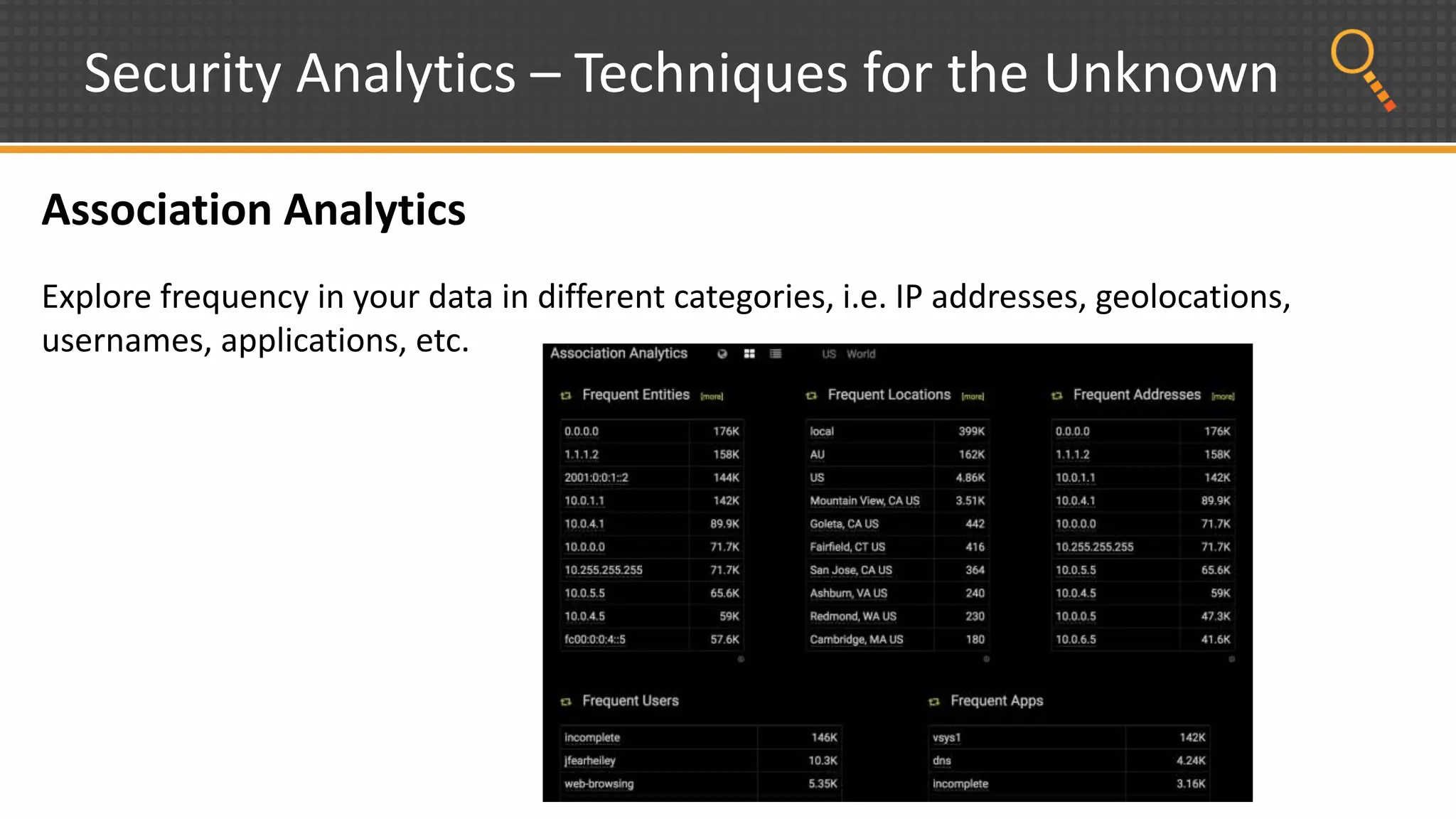
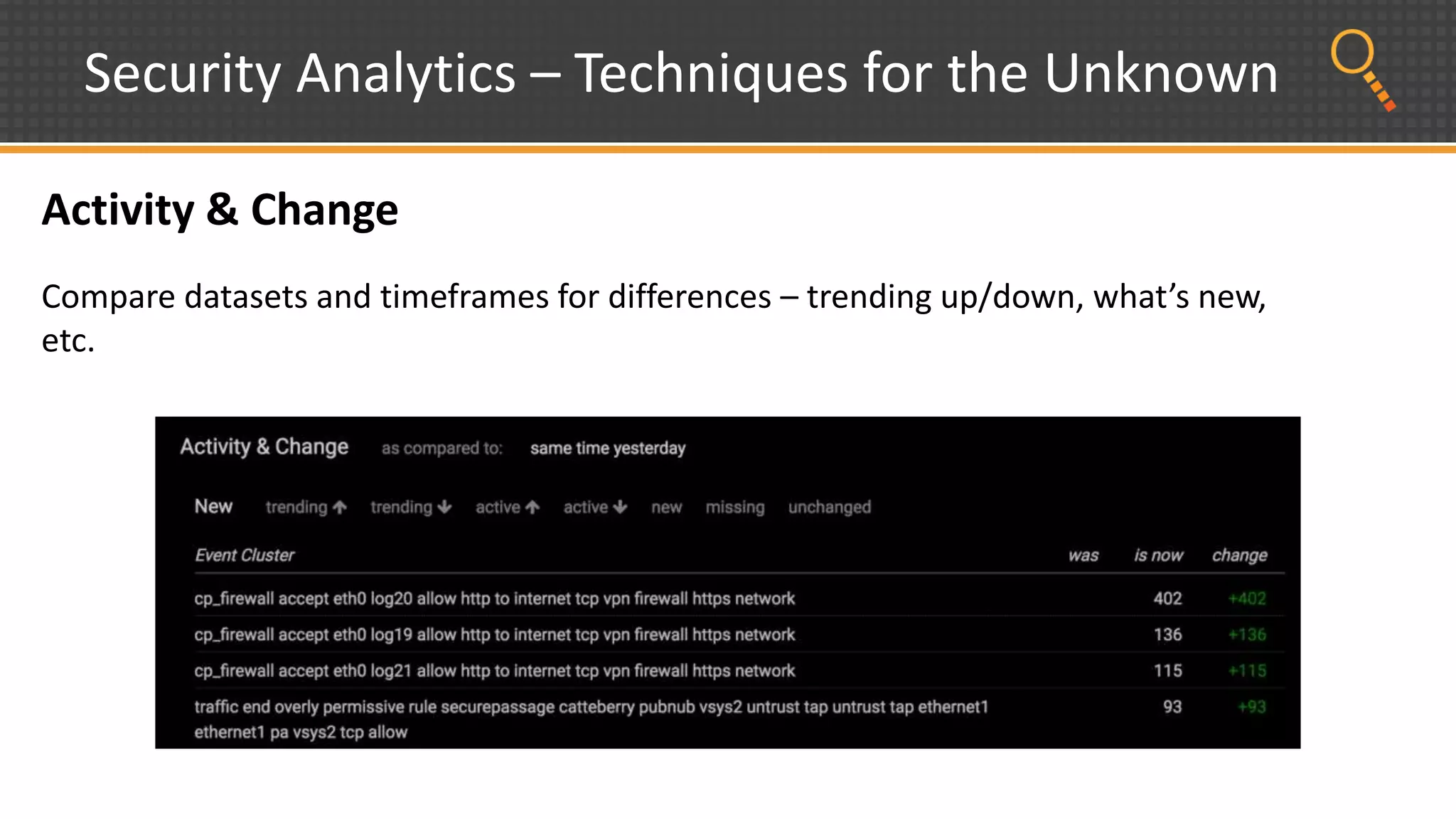
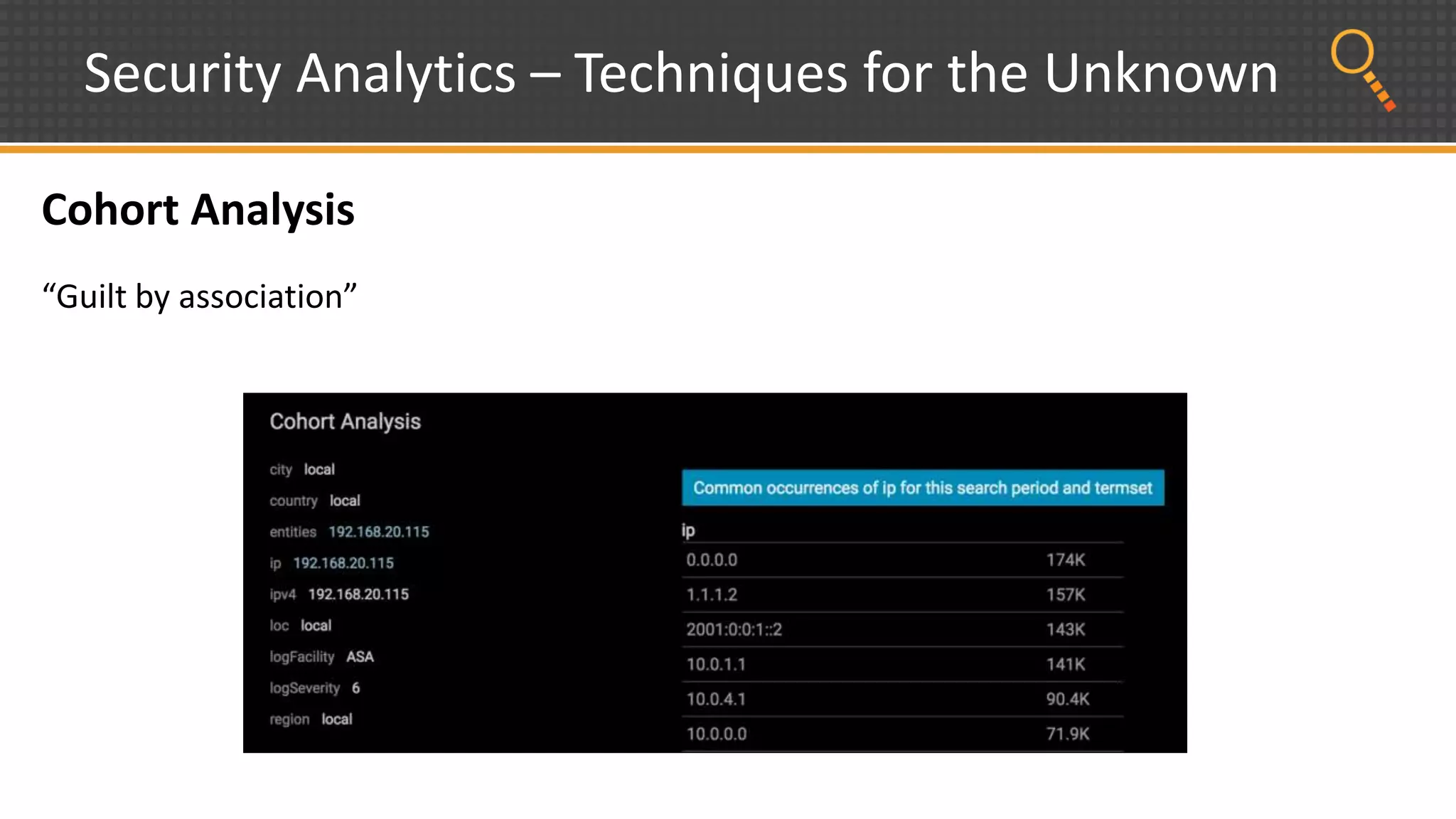
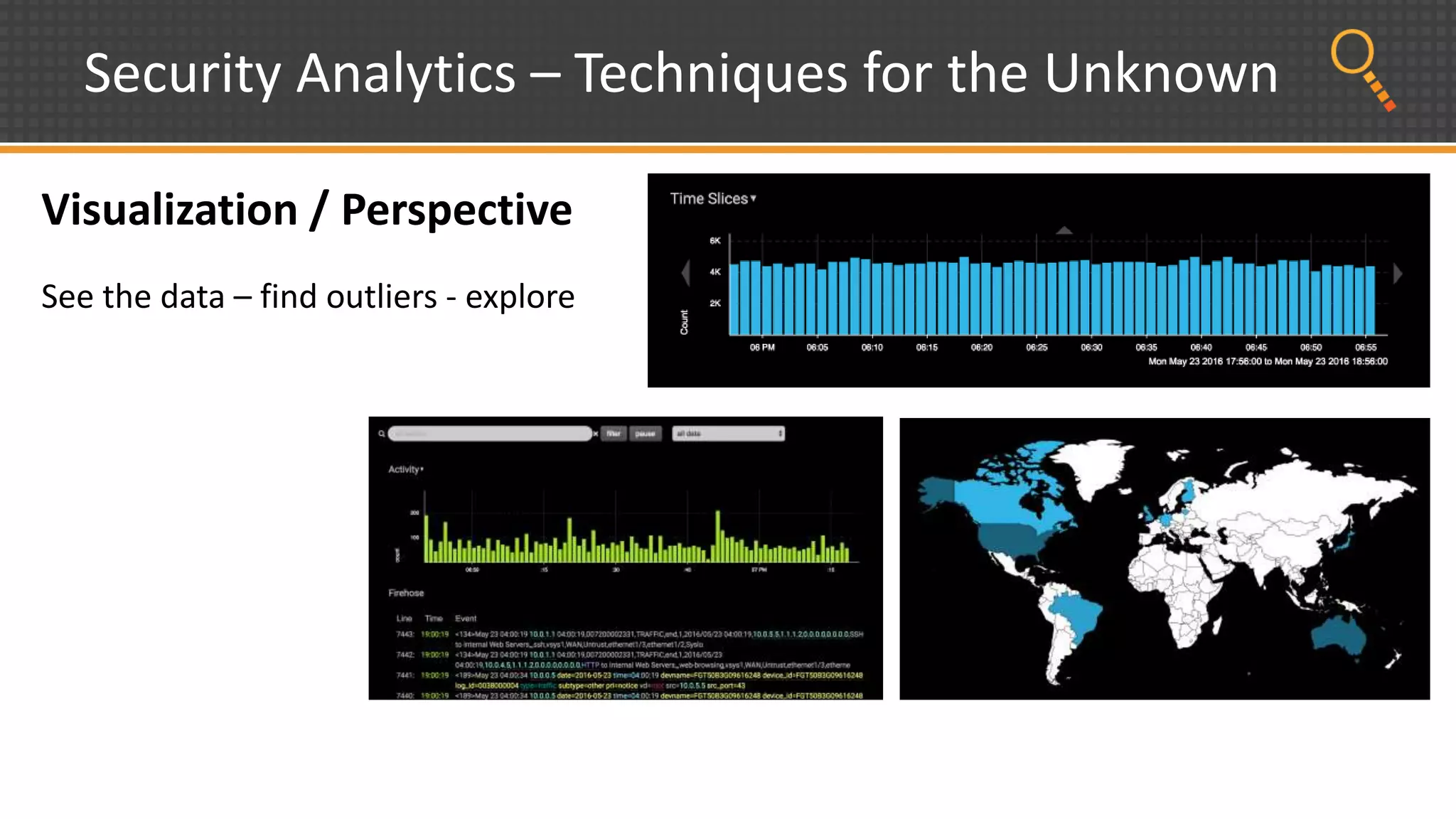
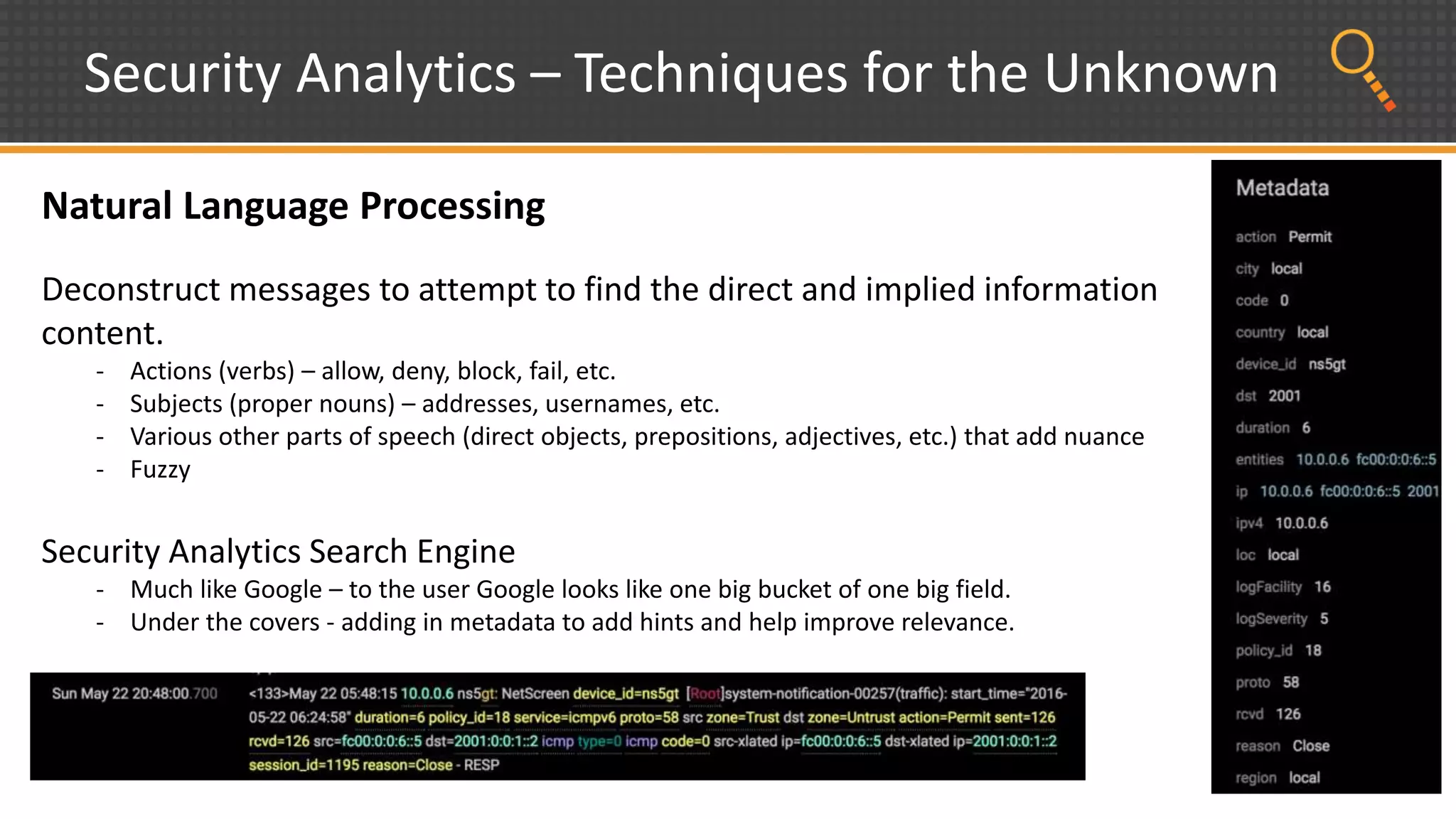
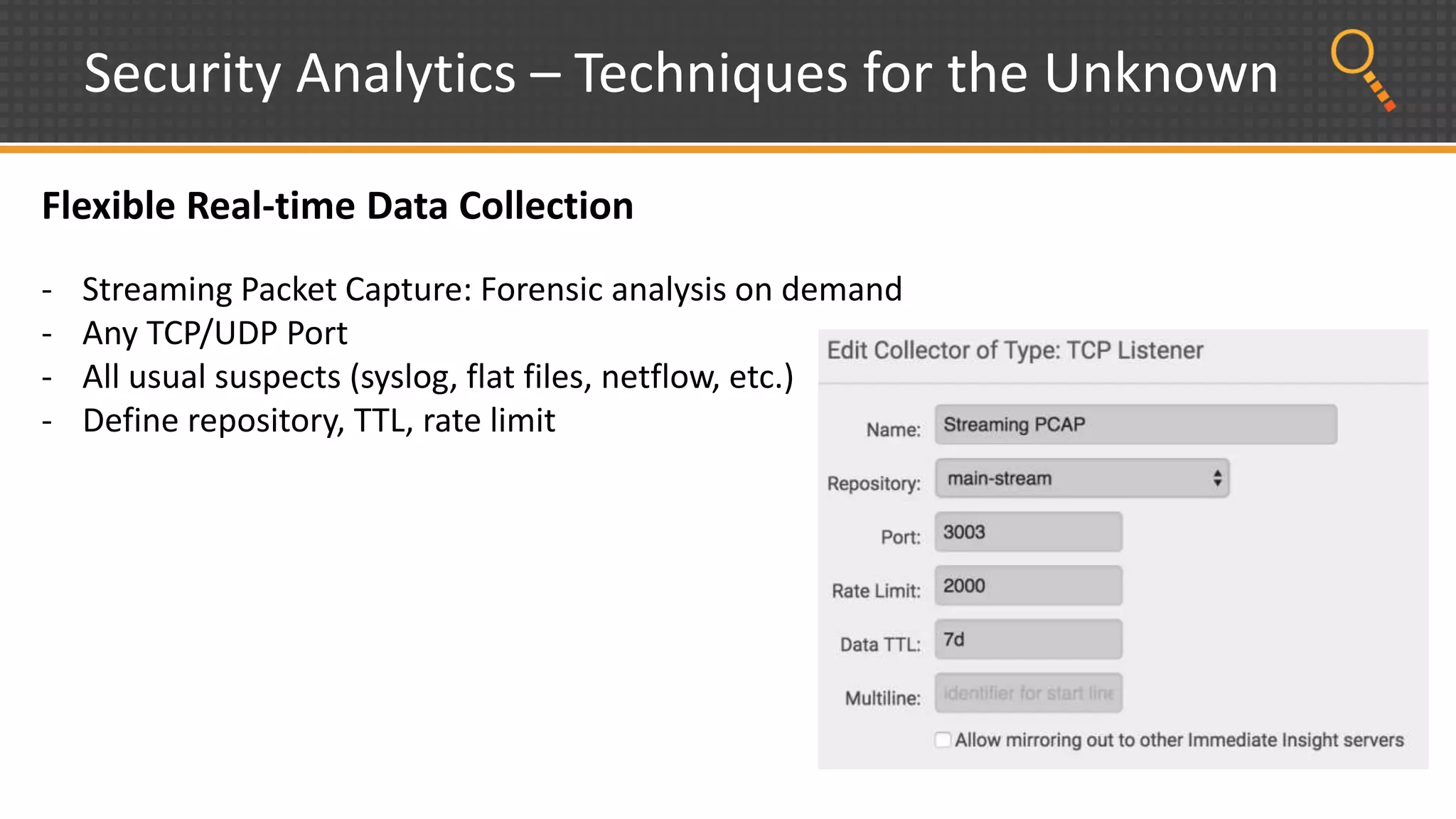
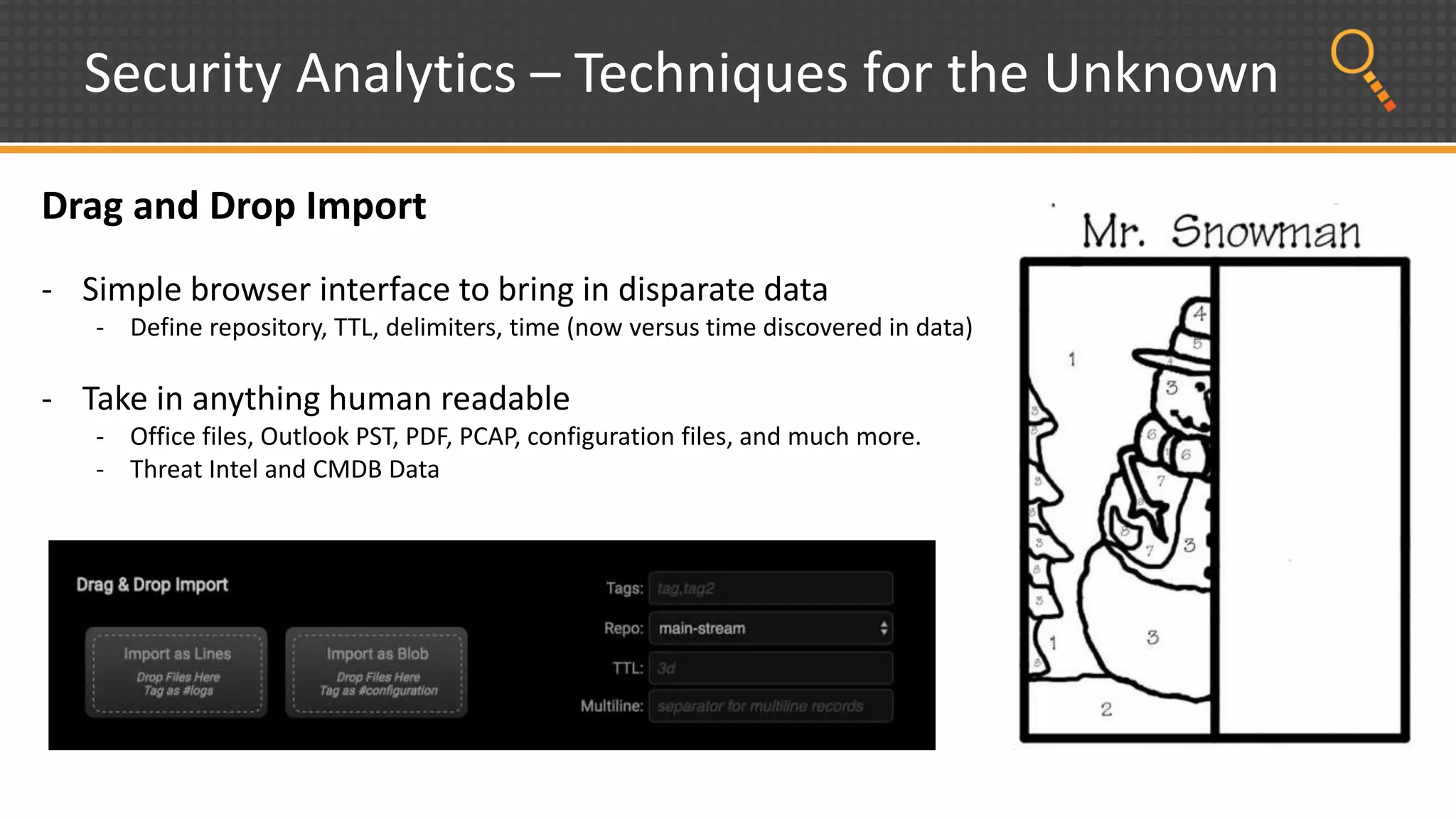
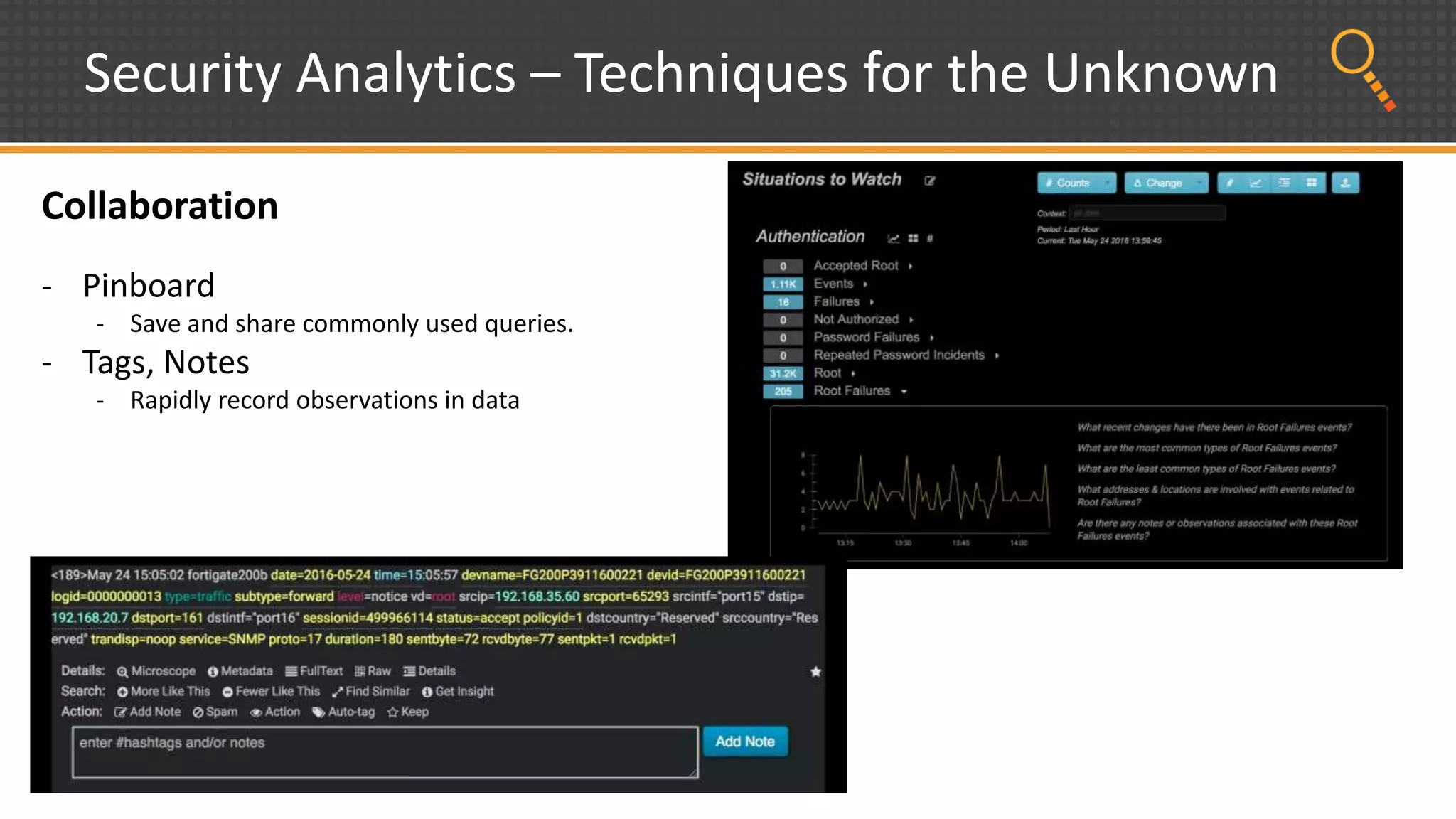
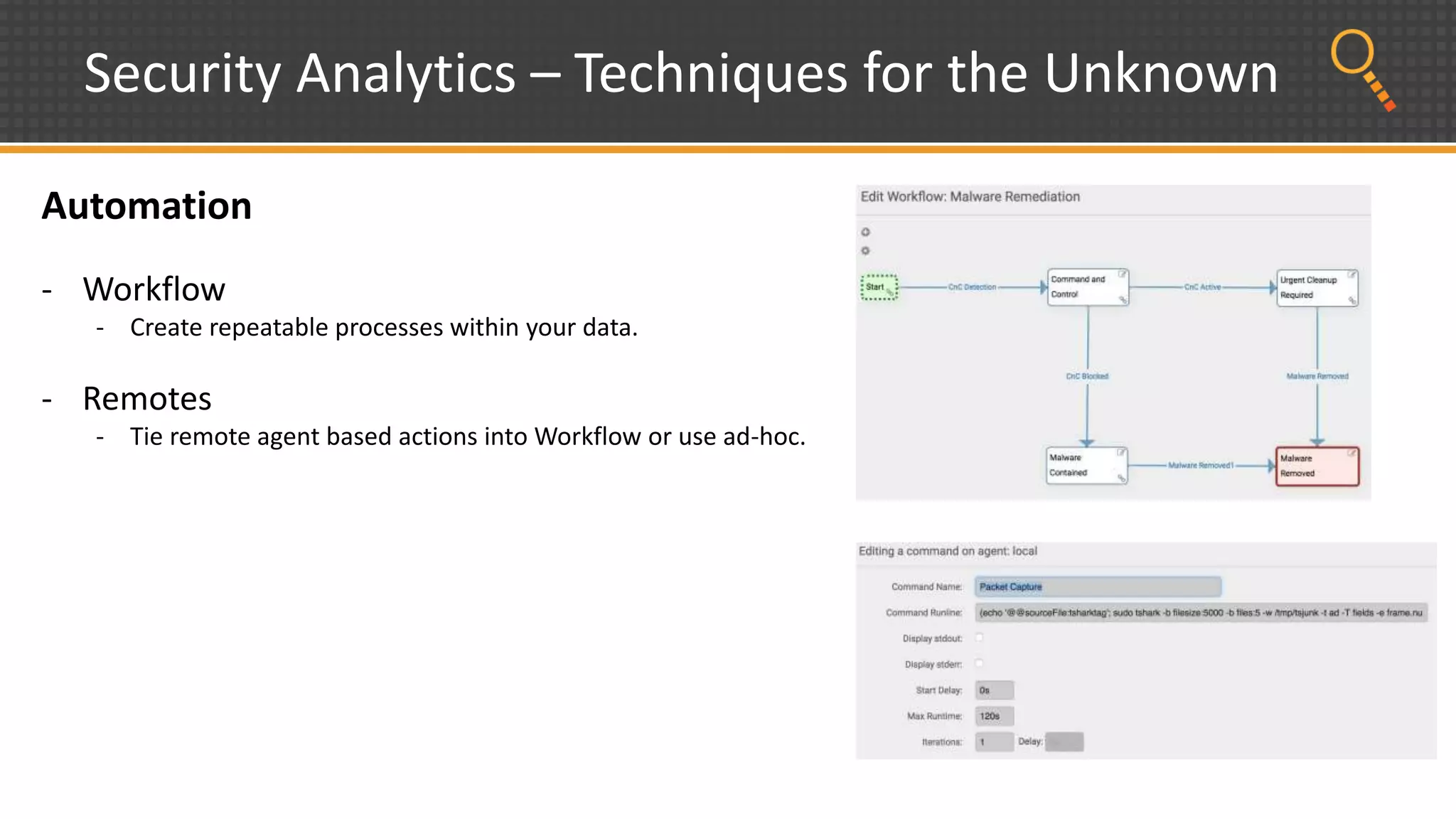
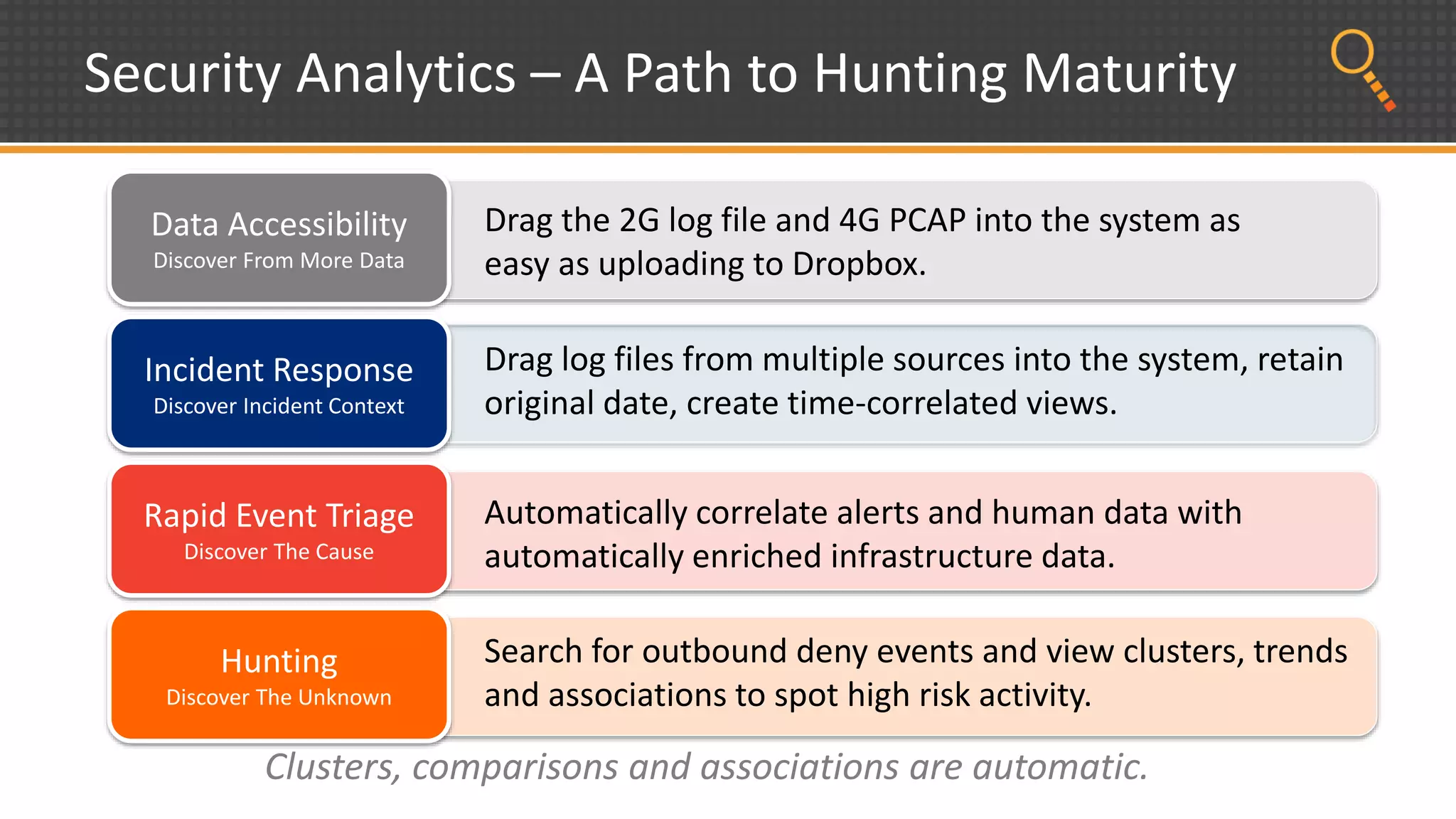
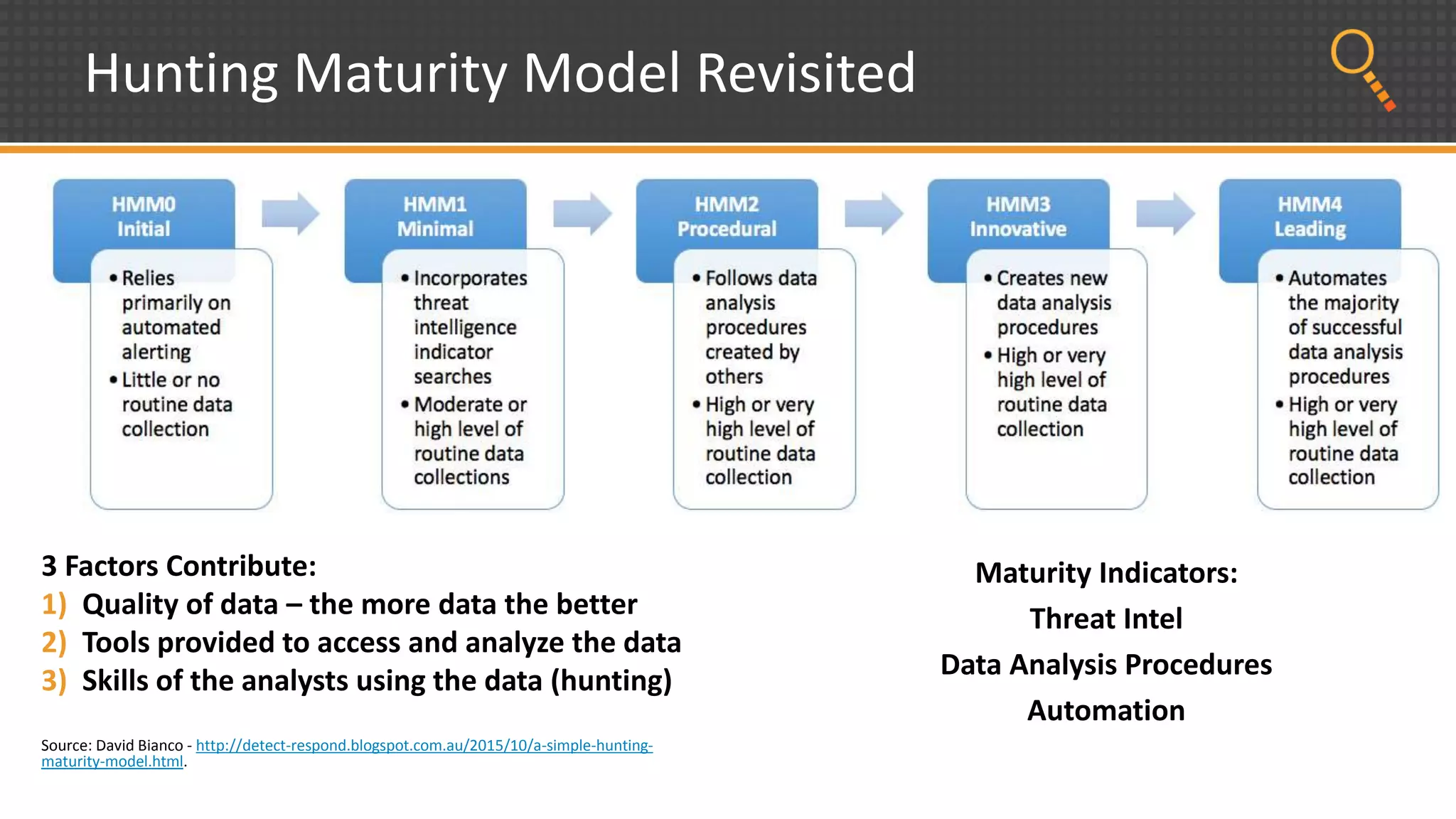
This document discusses security analytics and hunting maturity. It defines hunting as a proactive approach to identifying incidents by actively looking for patterns, intelligence or hunches, rather than waiting for notifications. It describes the "SIEM gap" where SIEM tools are designed for known threats and lack the tools and flexibility for human analysis and hunting of unknown threats. It outlines techniques used in security analytics like event clustering, association analysis, and visualization to help analyze large datasets and discover unknown threats. The document argues security analytics provides the data access, analysis techniques and workflows to help close the SIEM gap and improve an organization's hunting maturity over time.