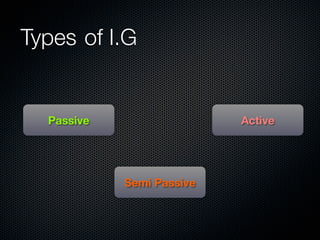
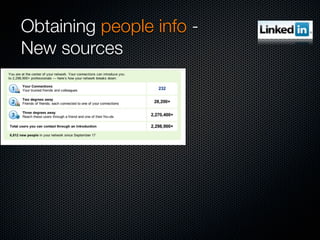
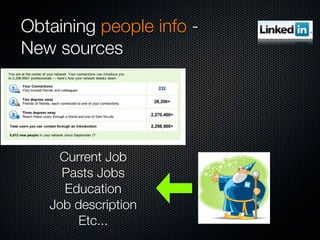
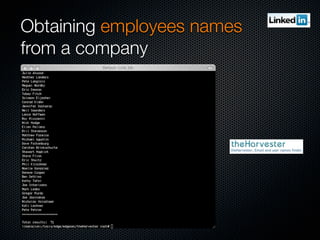
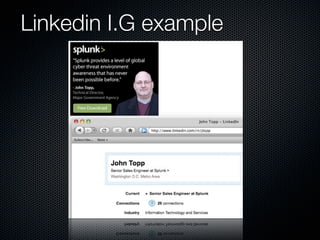
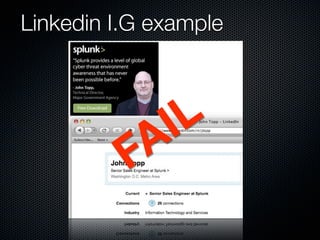
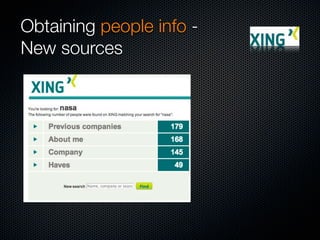
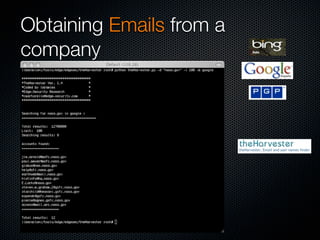
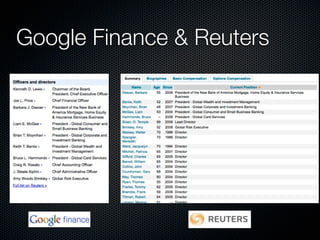
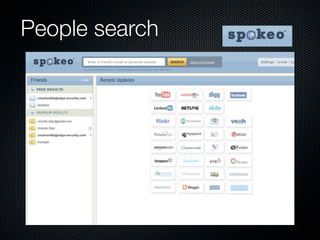
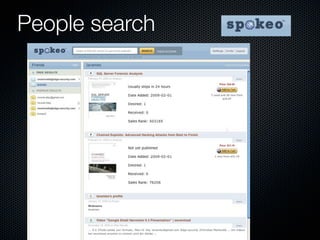
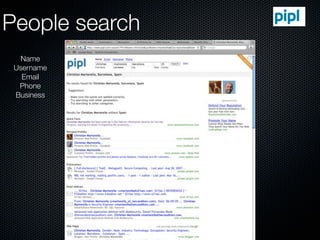
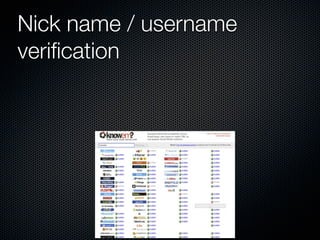
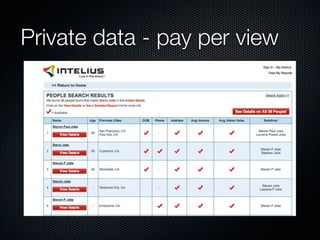
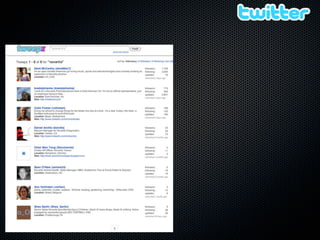
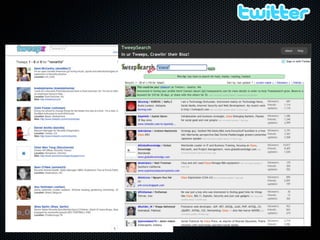
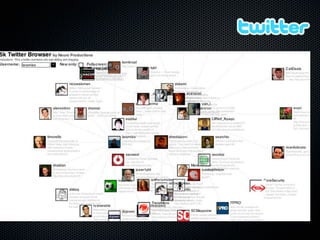
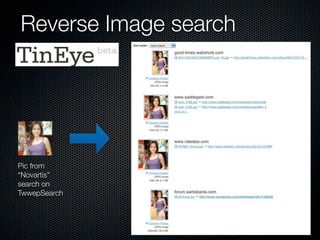
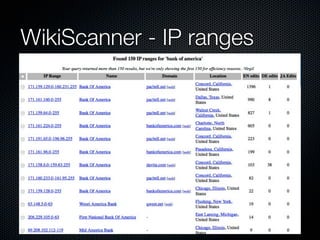
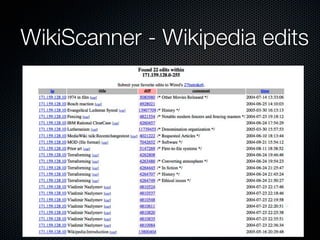
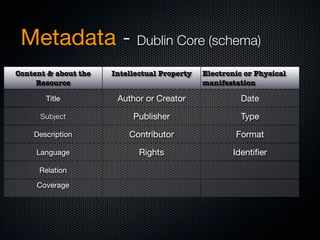
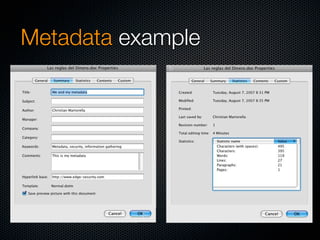
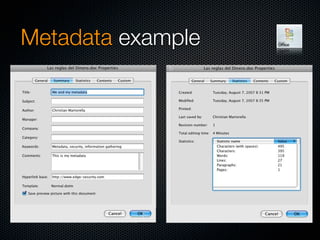
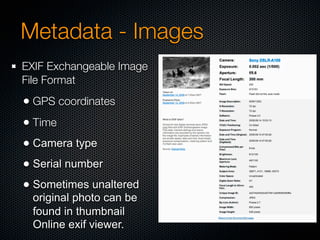
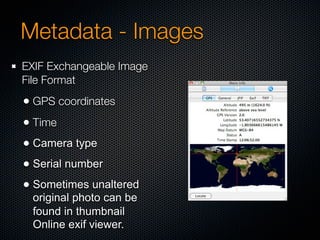
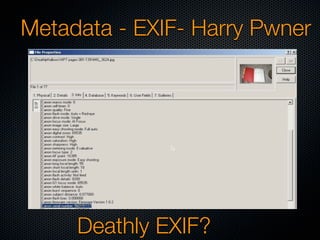
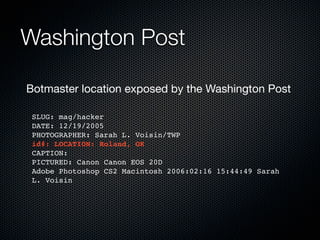
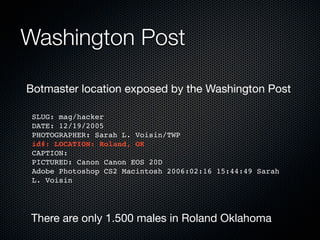
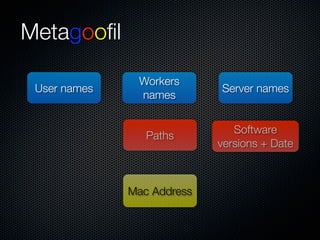
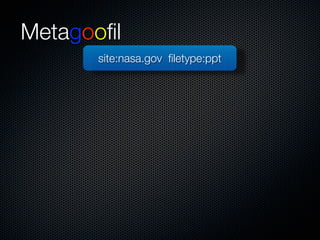
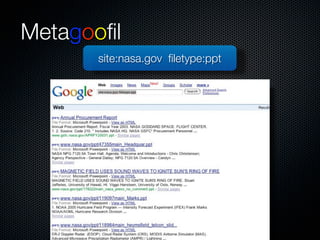
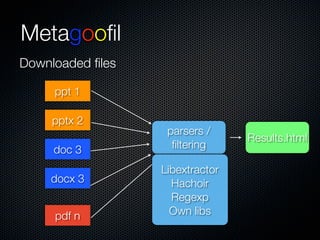
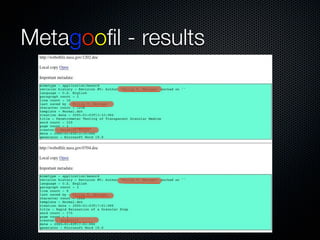
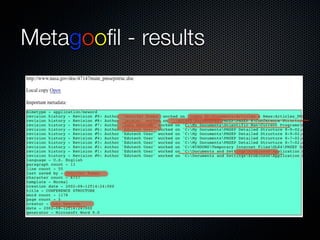
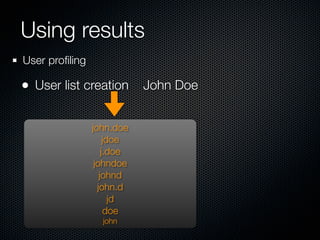
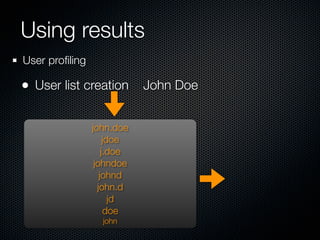
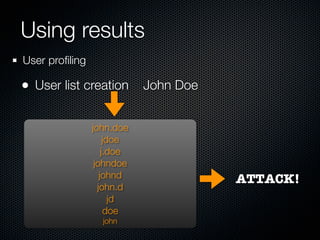
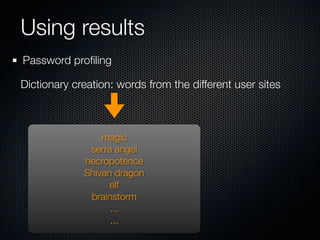
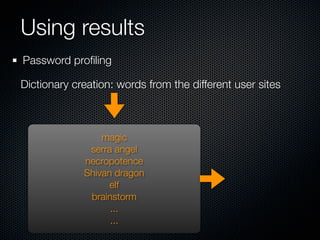
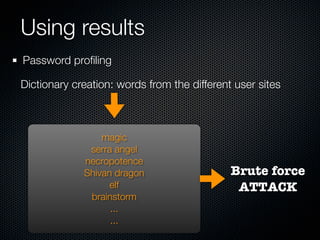
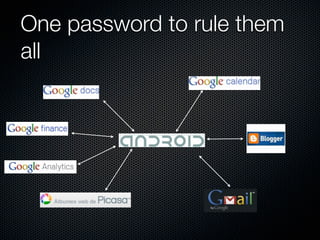
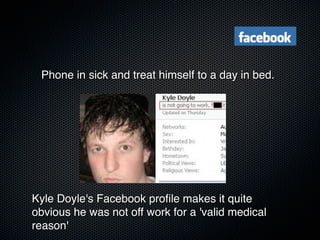
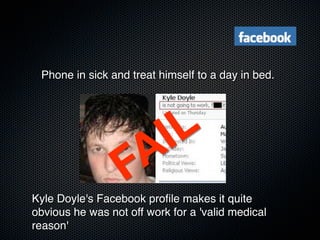
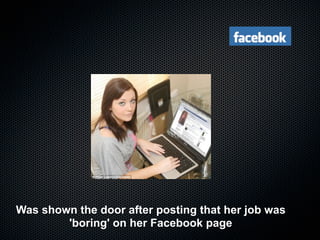
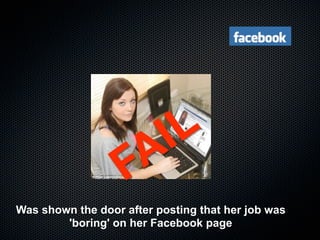
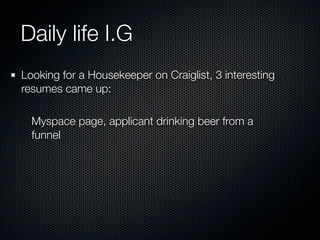
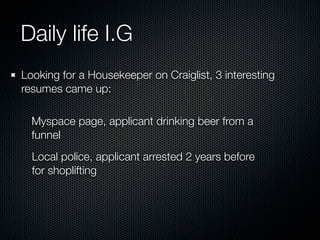
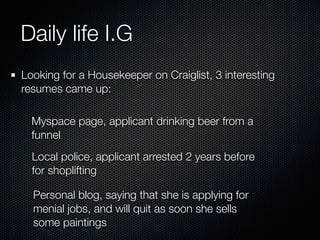
Christian Martorella's presentation at the 2009 conference in Barcelona focused on tactical information gathering for security purposes, emphasizing the need for attackers to collect detailed information about their targets before launching attacks. He discussed various methodologies, tools, and passive and active sources for obtaining this information, particularly emphasizing the significance of online data from social networks and metadata extraction. The talk concluded with a warning about the implications of oversharing online and the importance of maintaining privacy in a digital age.