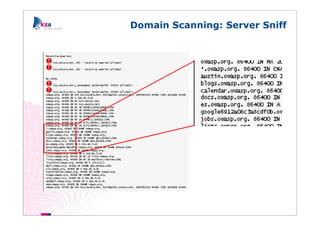
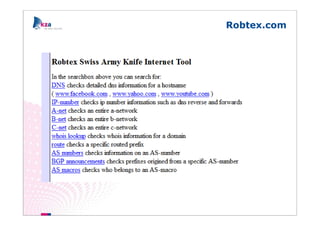
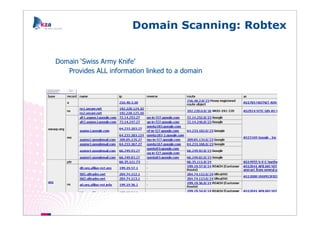
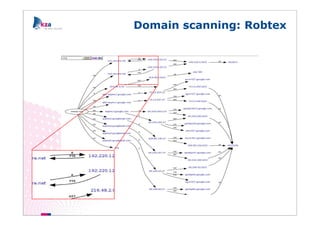
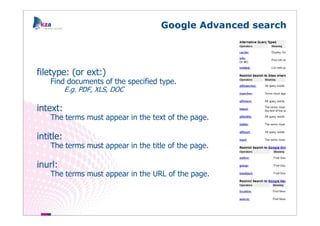
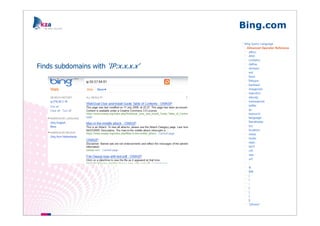
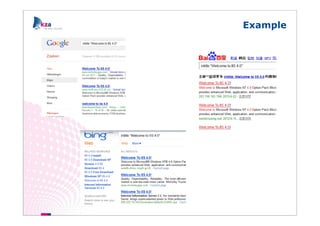
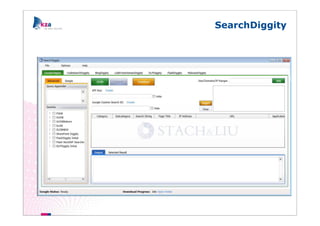
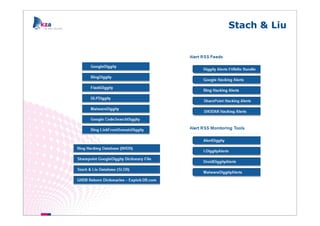
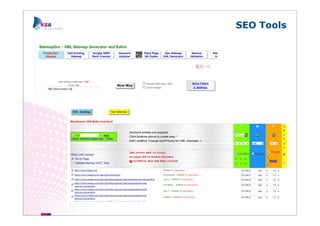
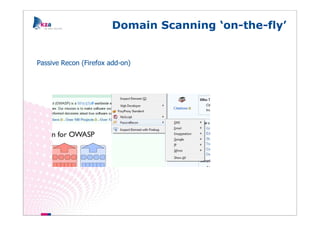
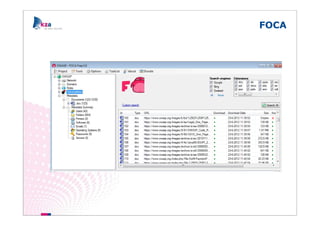
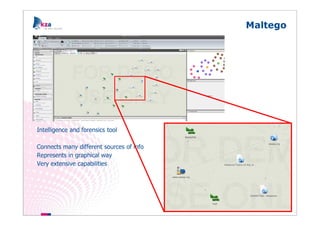
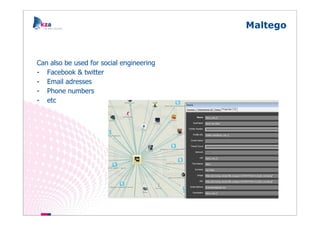
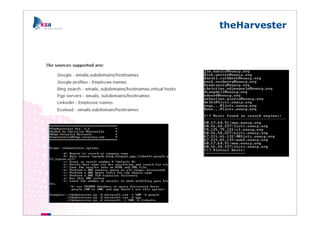
The document outlines methods of modern information gathering, emphasizing the accessibility of information about systems and users on the internet. It discusses tools and techniques such as domain scanning, search engine usage, and social engineering, highlighting potential vulnerabilities. Recommendations for enhancing security include limiting access, using hacker tools for self-assessment, and increasing awareness among employees about information exposure.