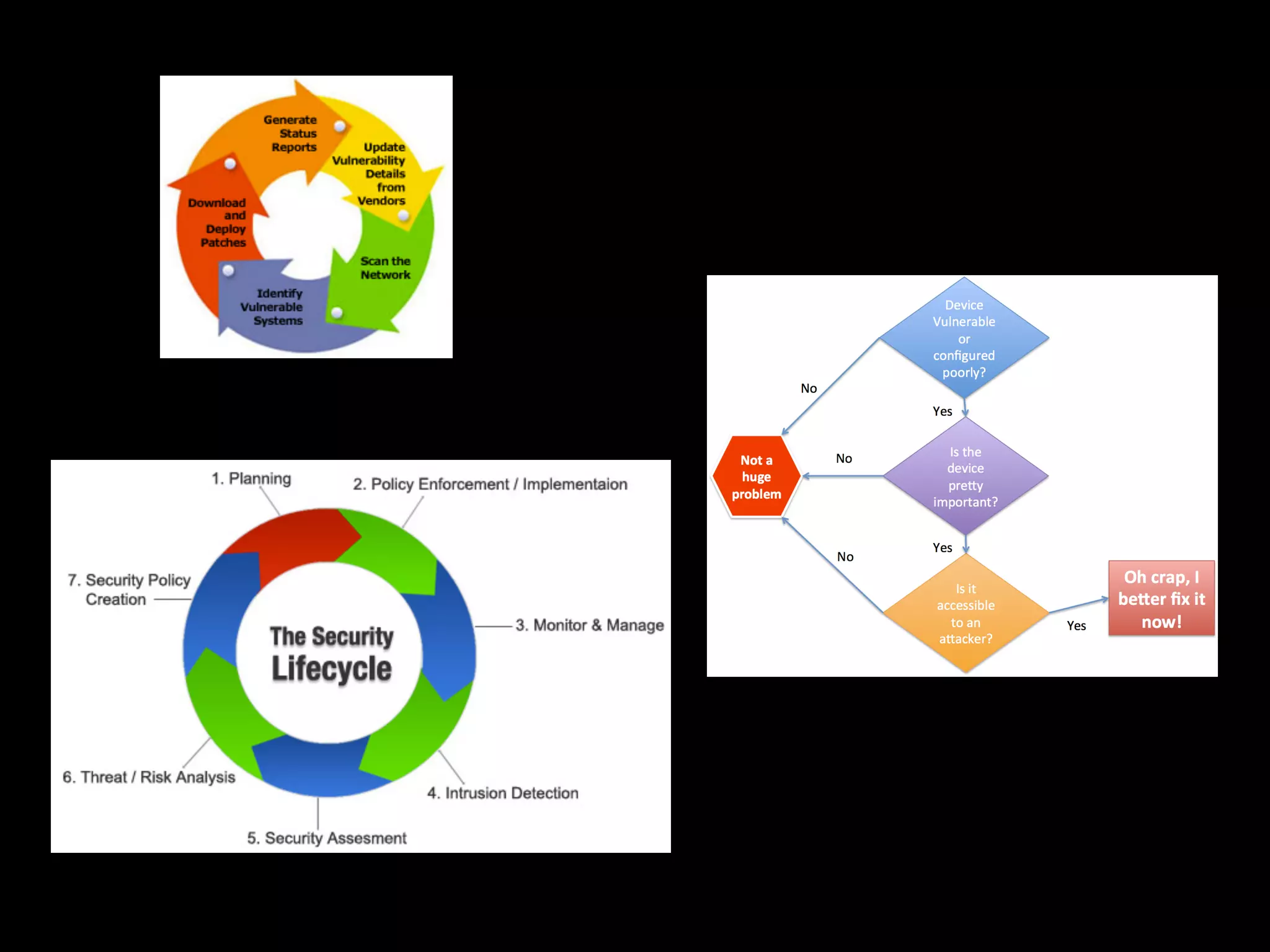
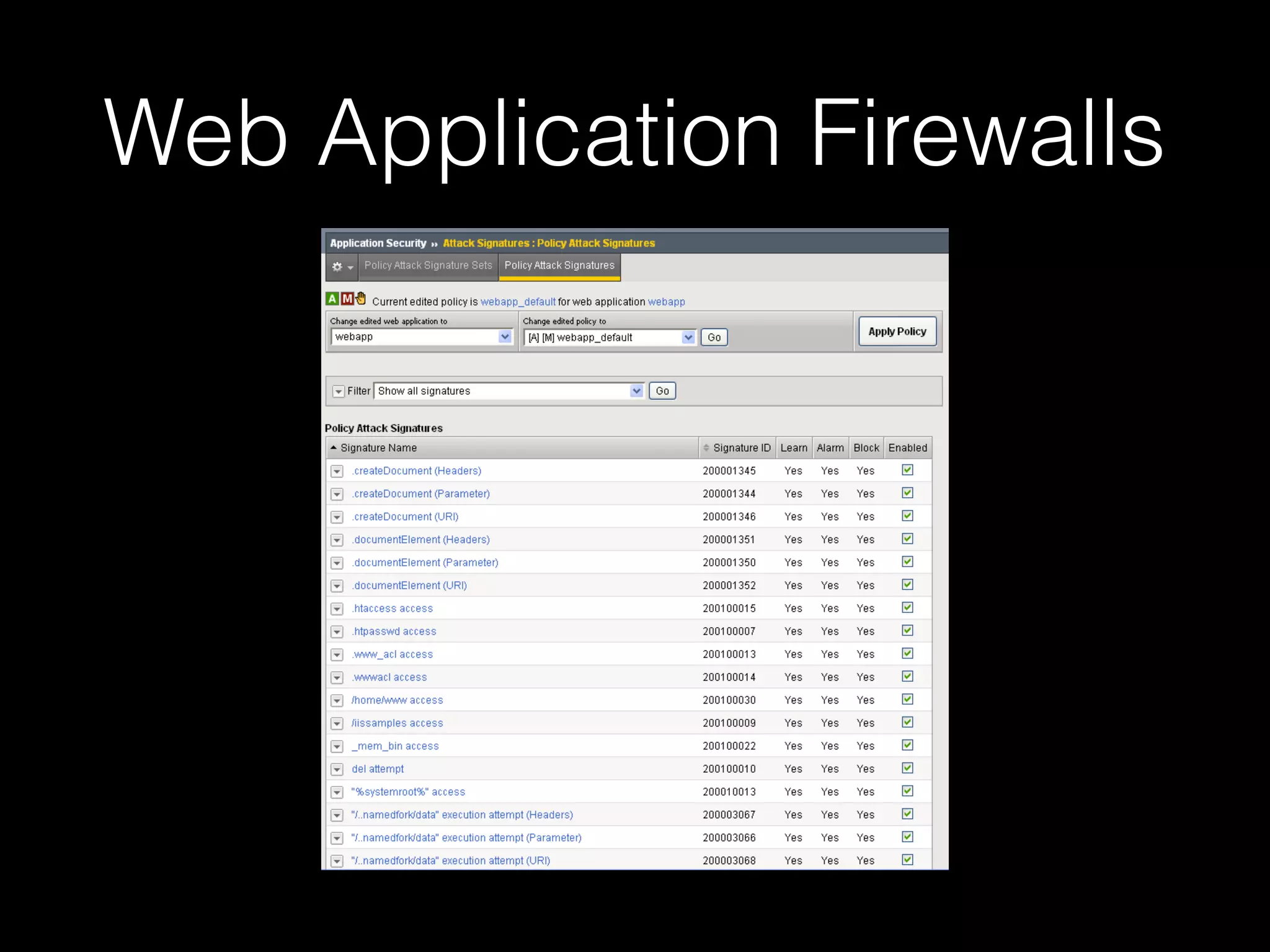
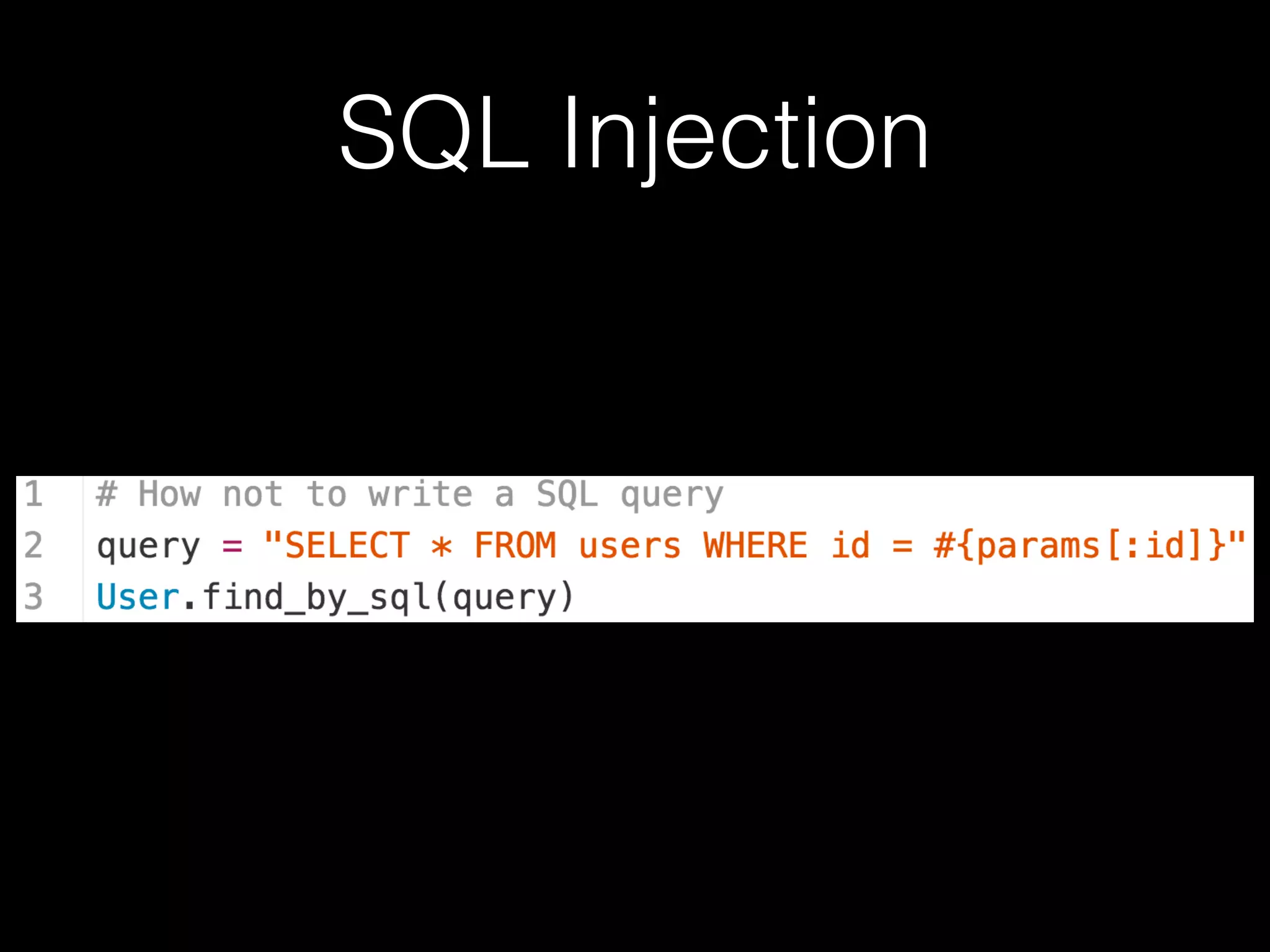
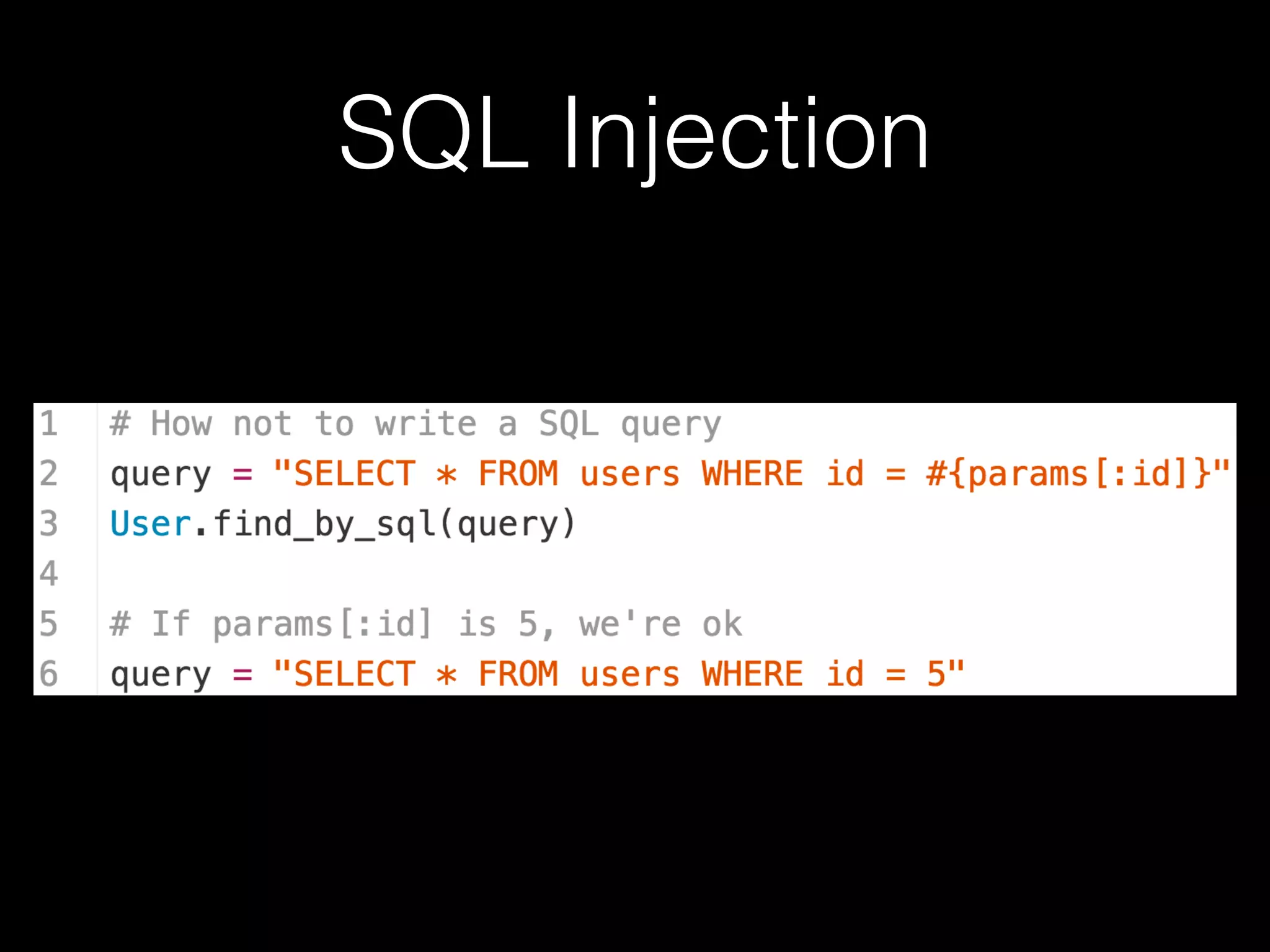
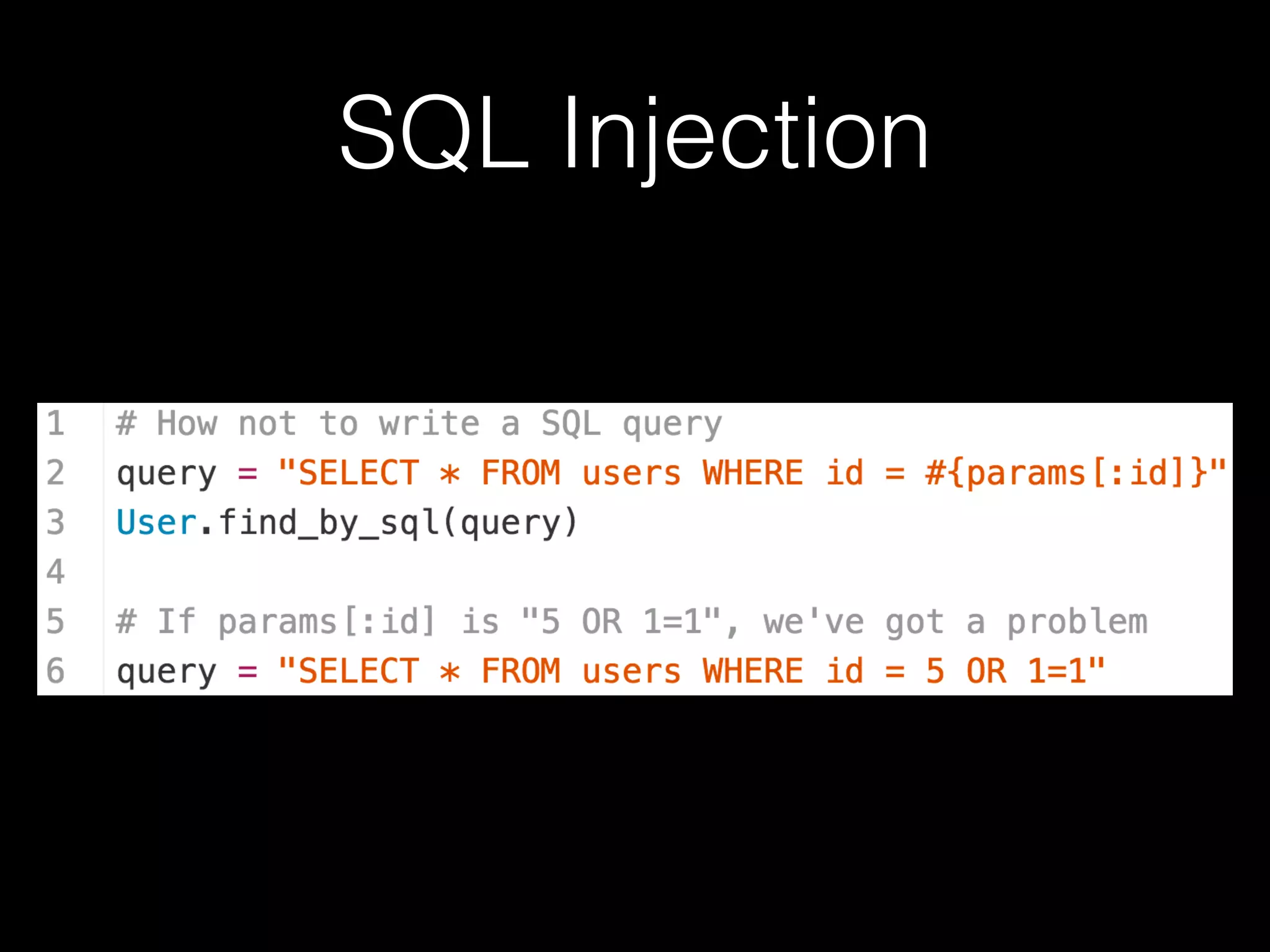
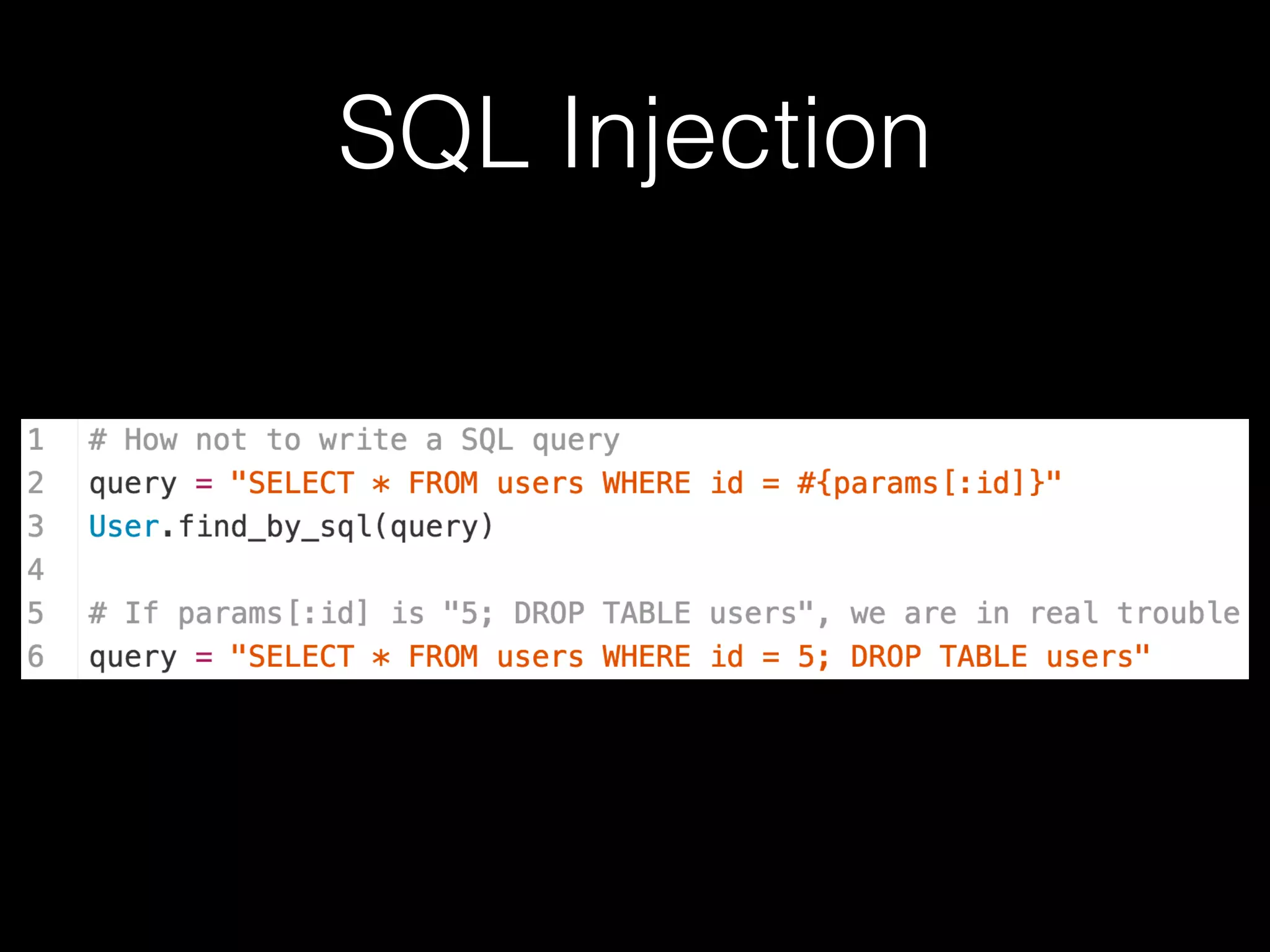
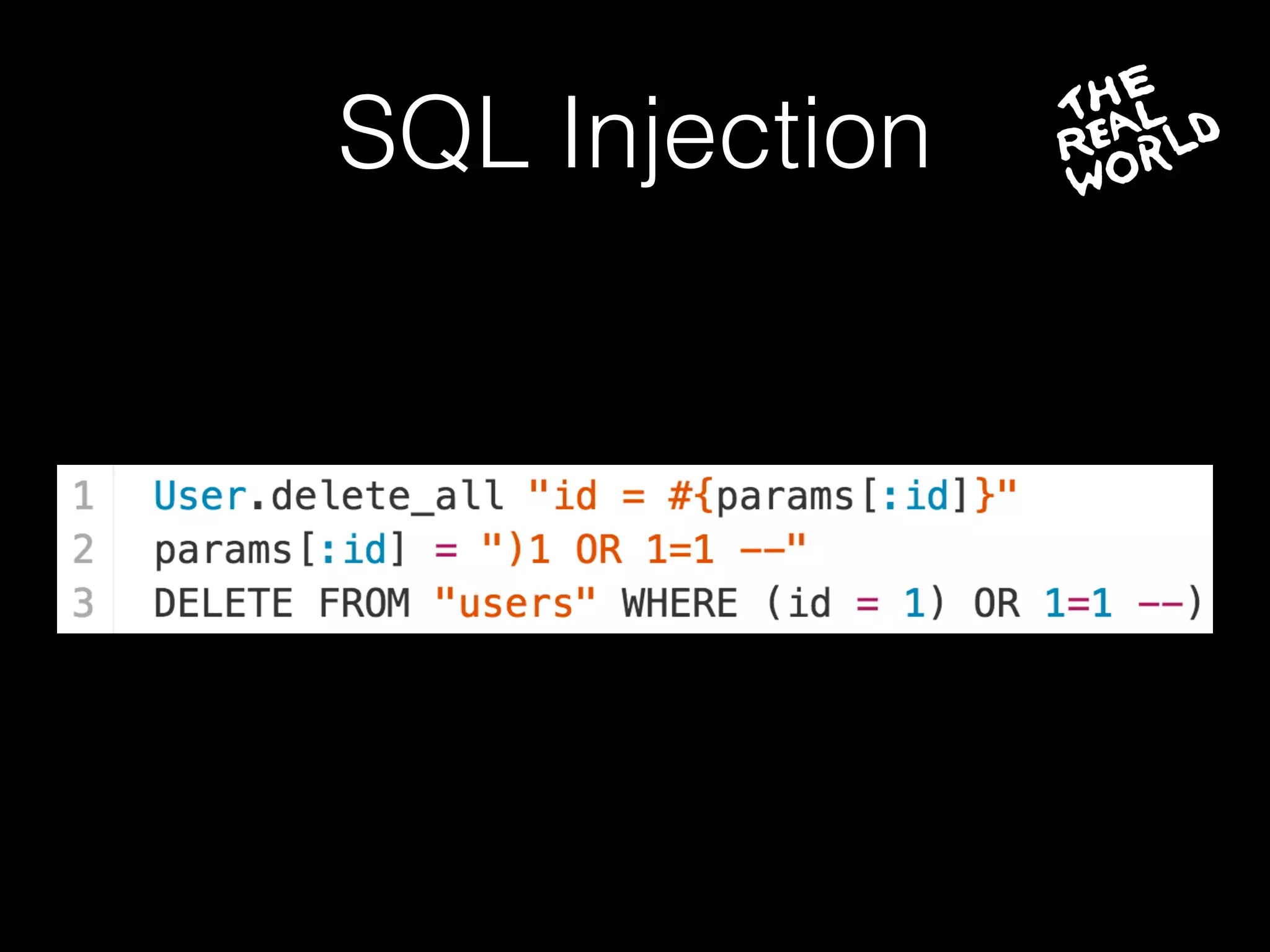
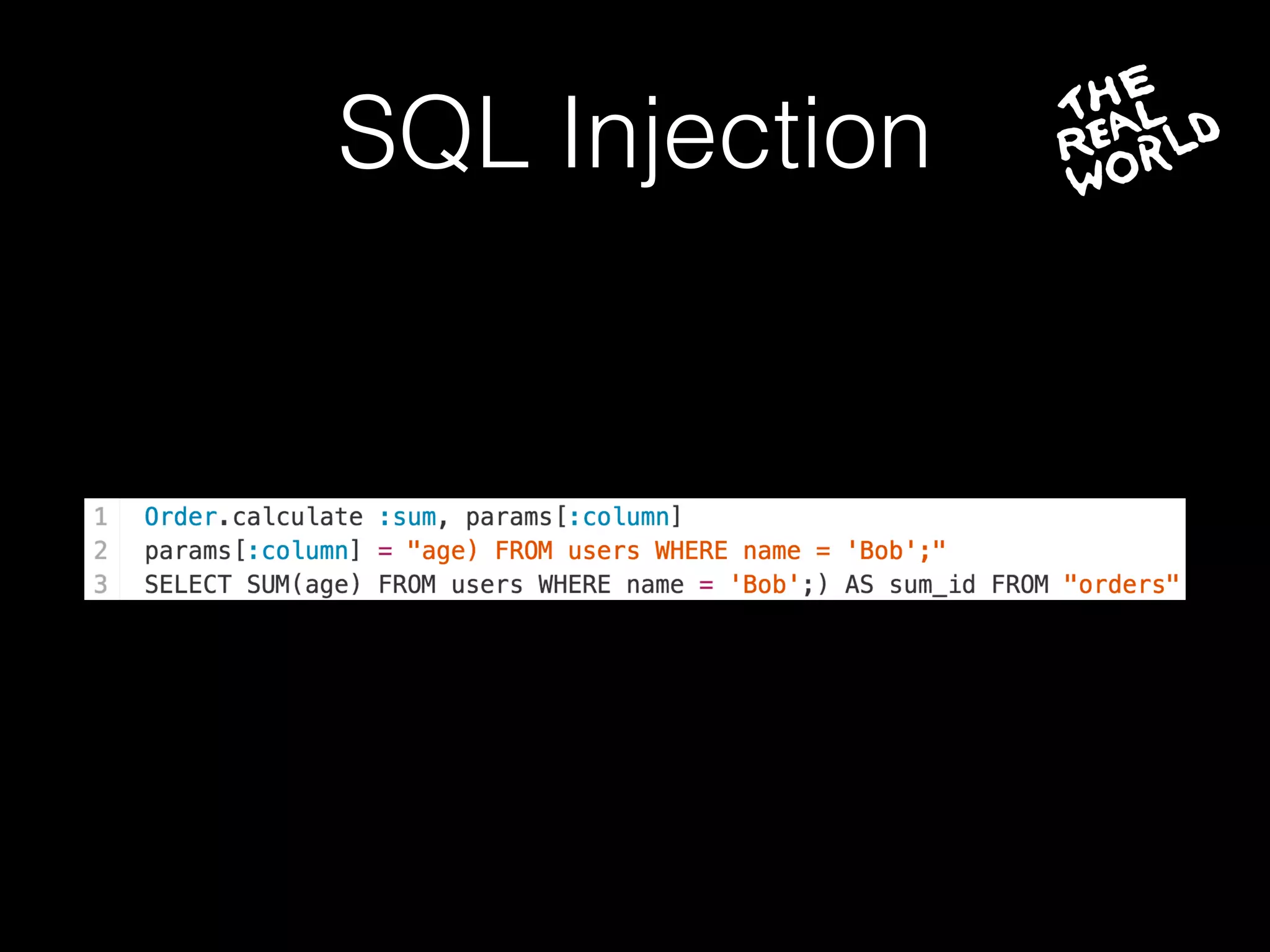
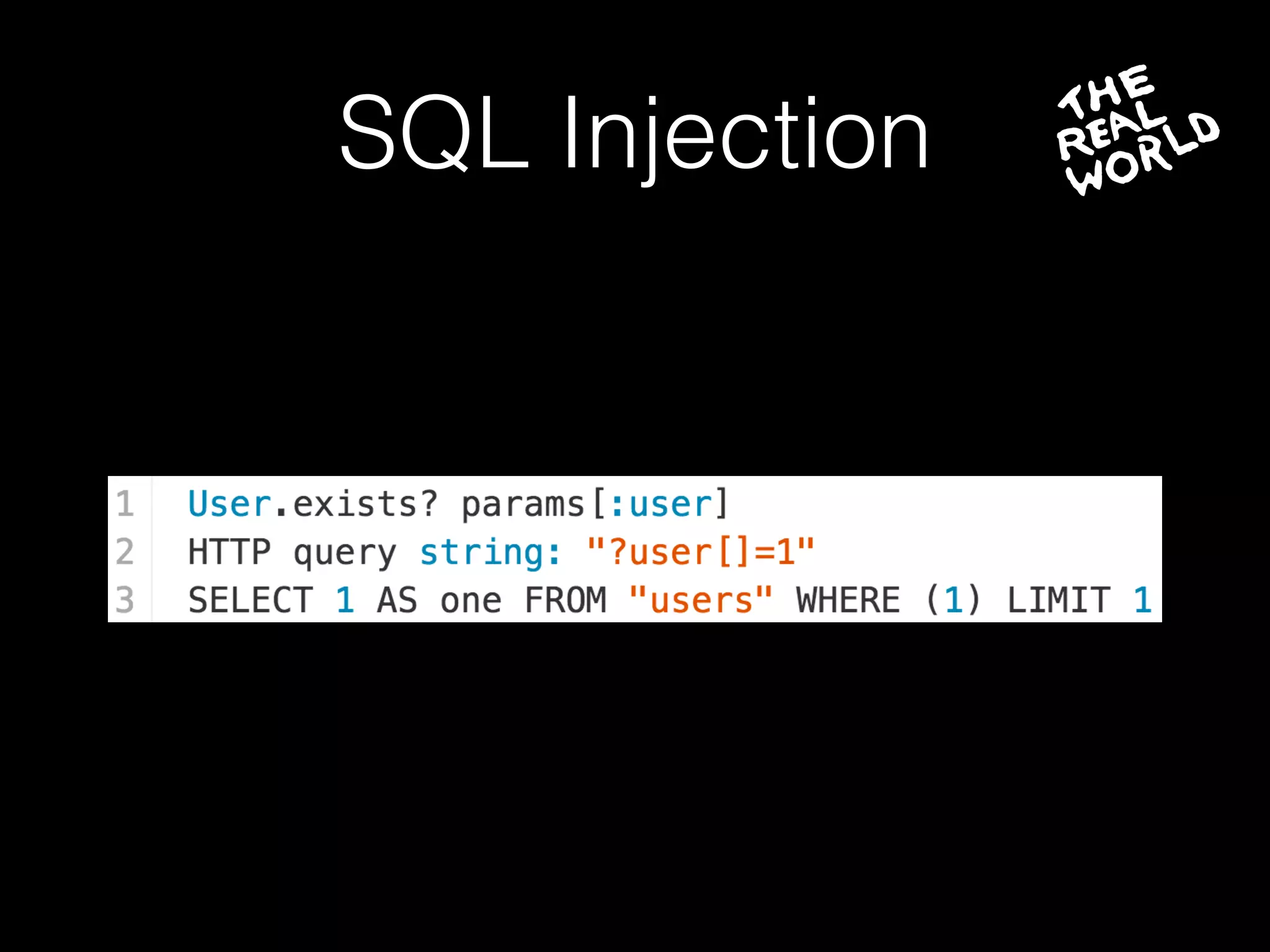
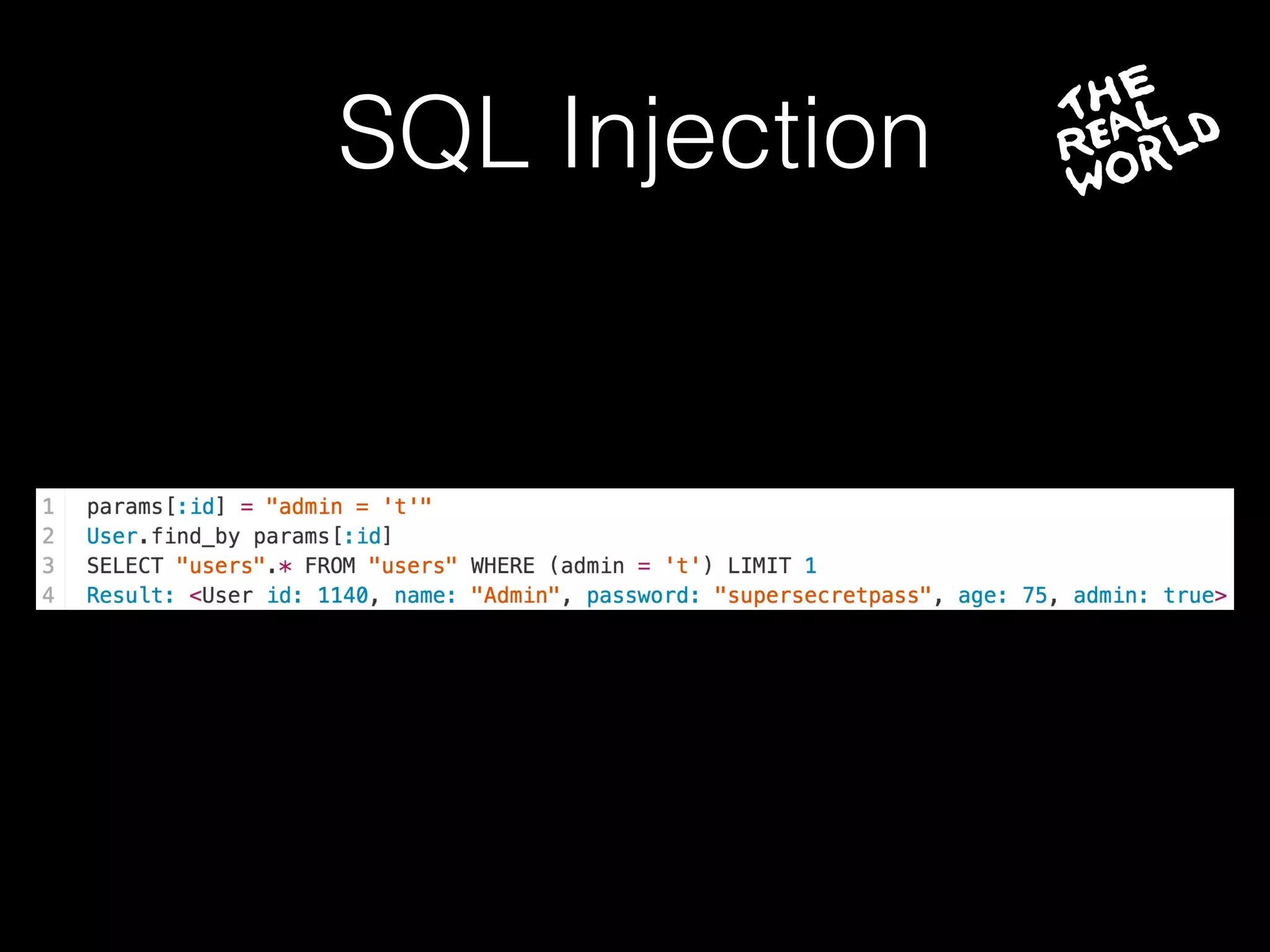
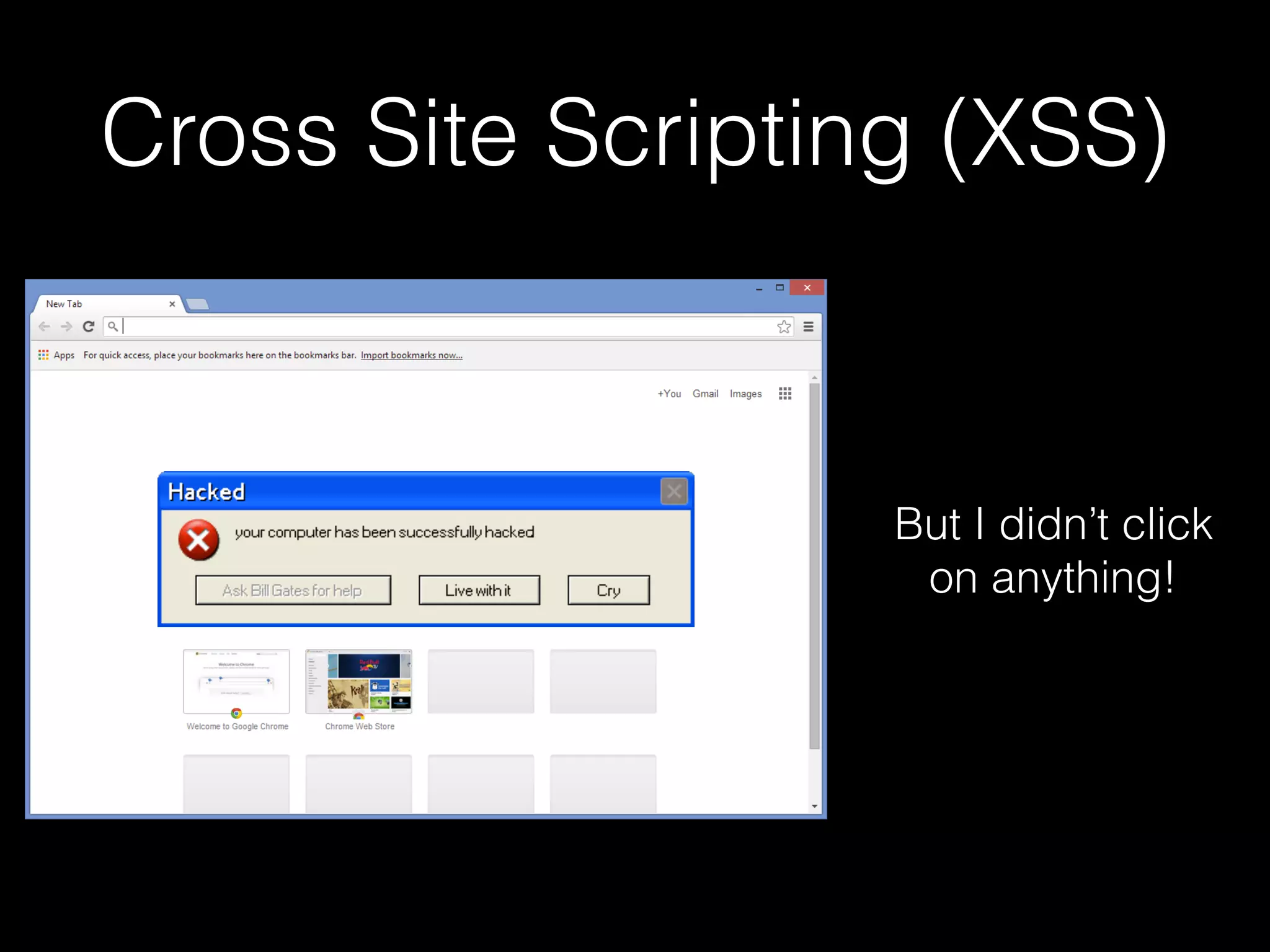
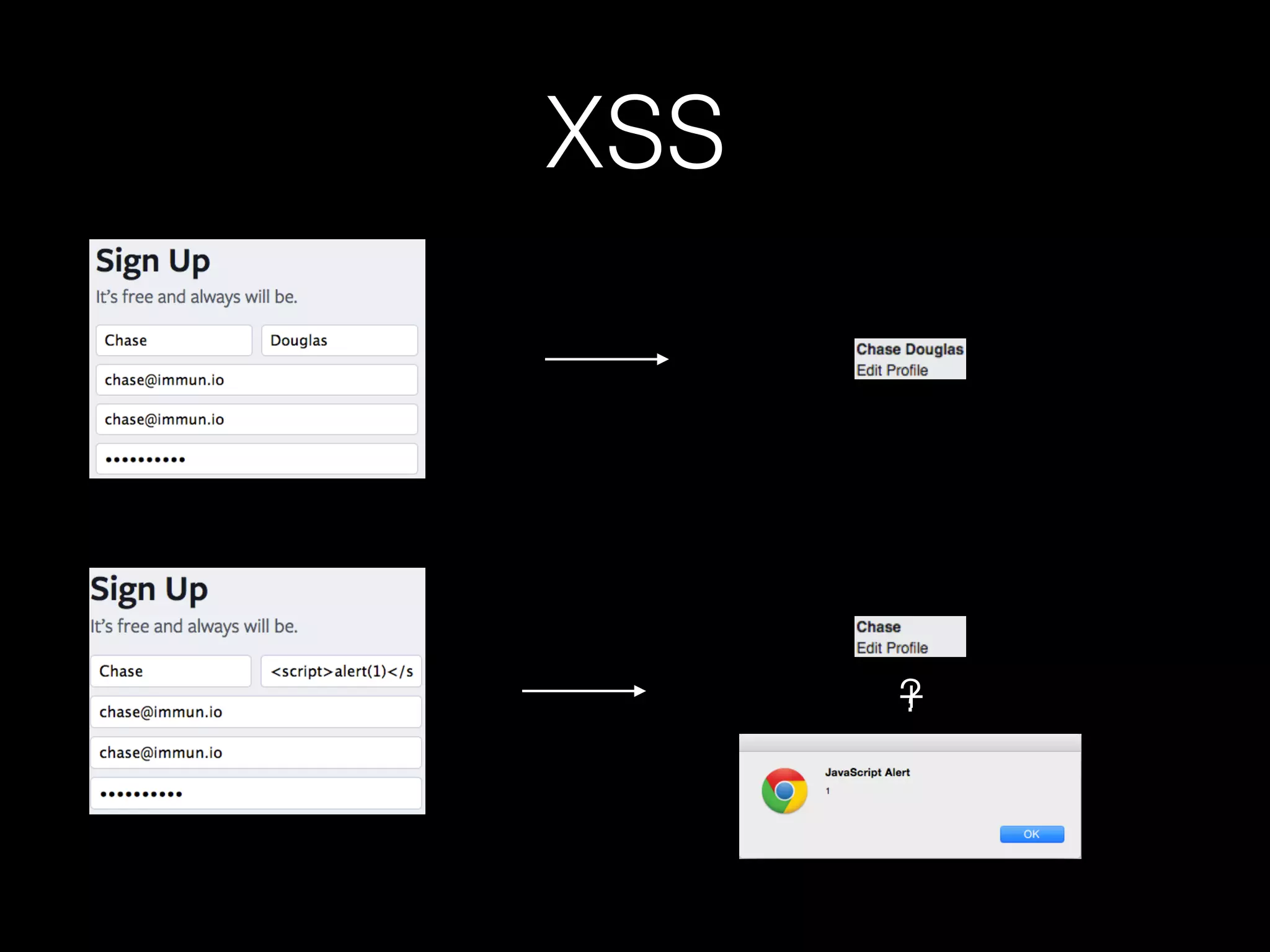
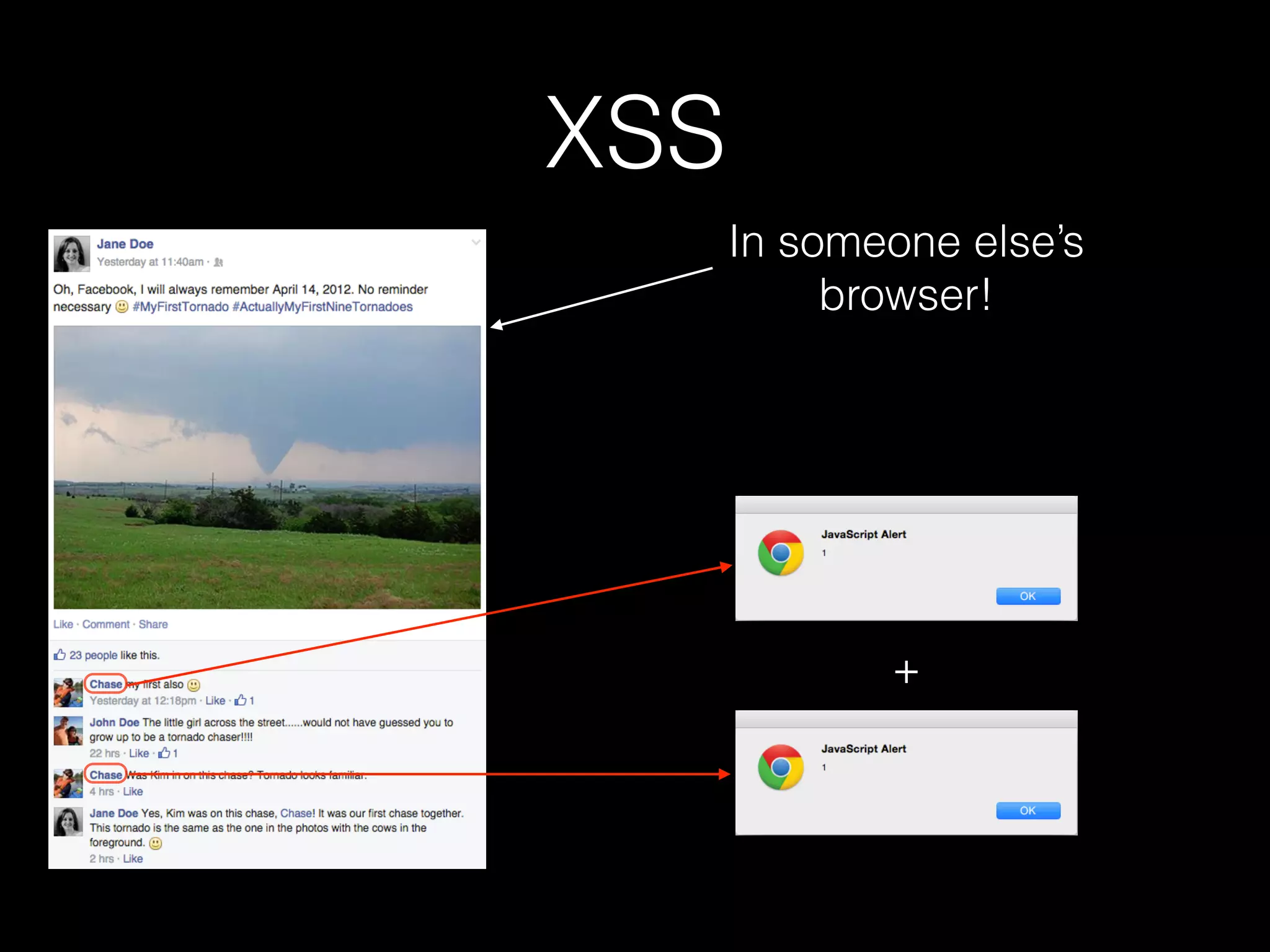
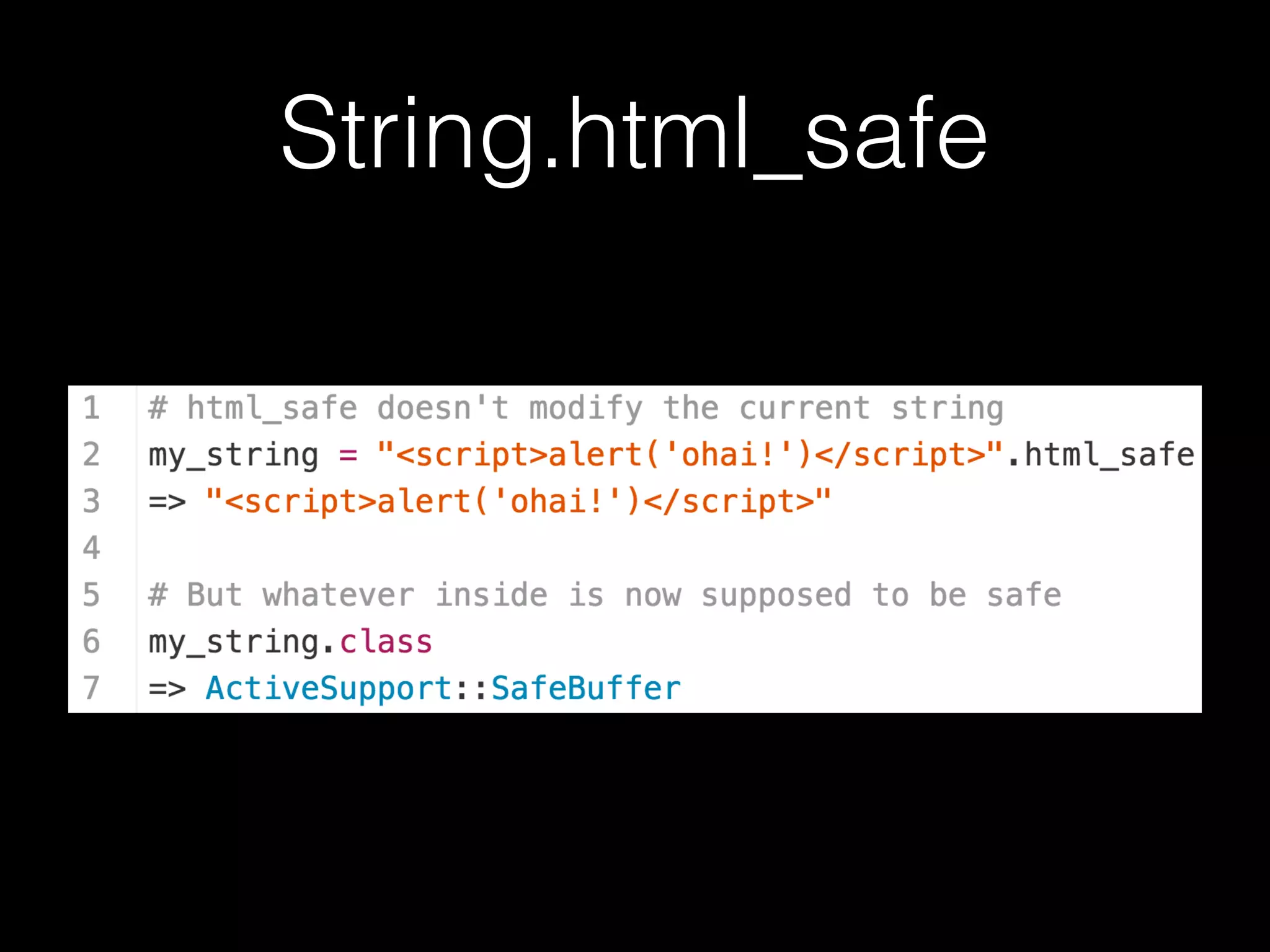
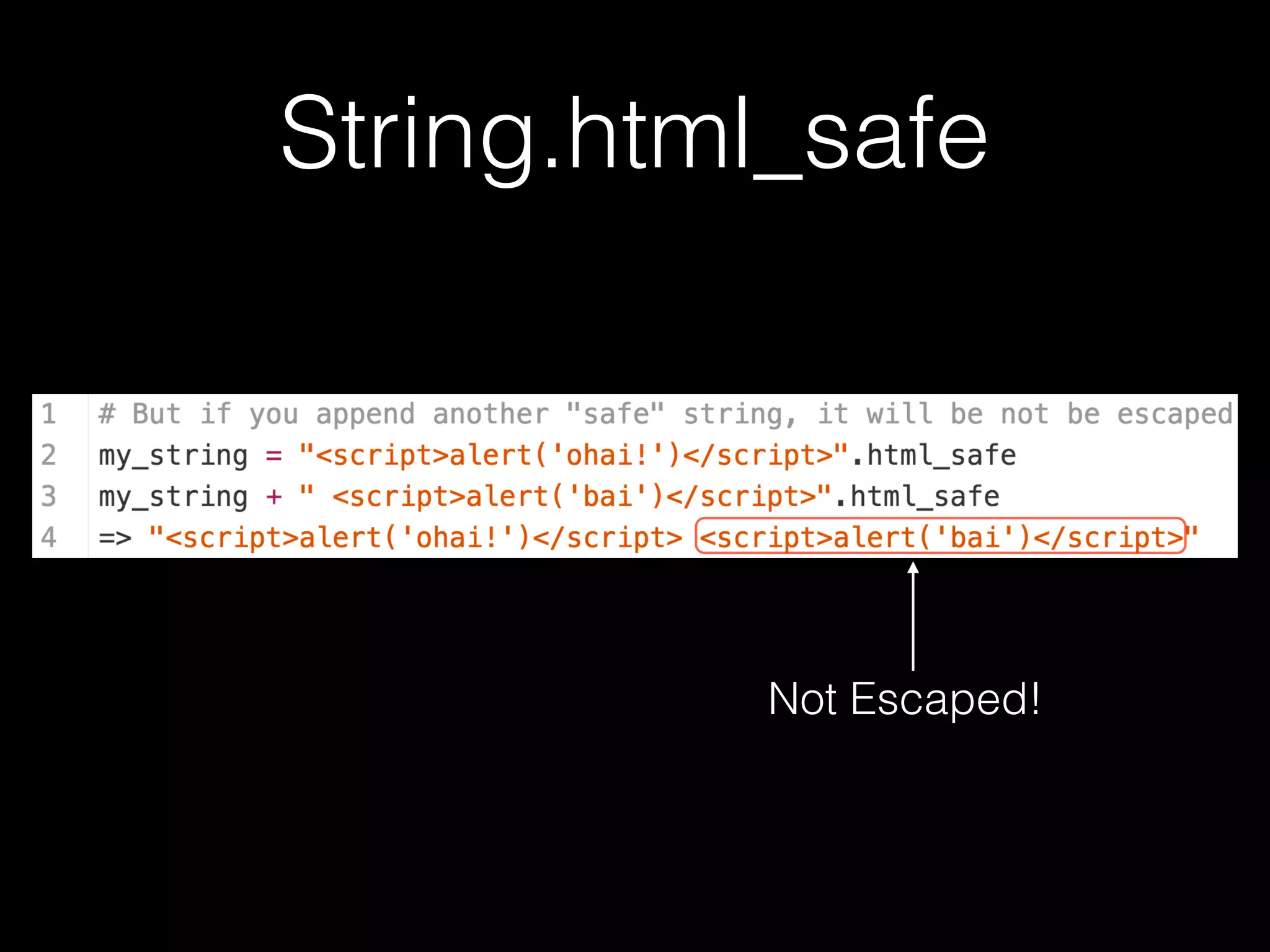
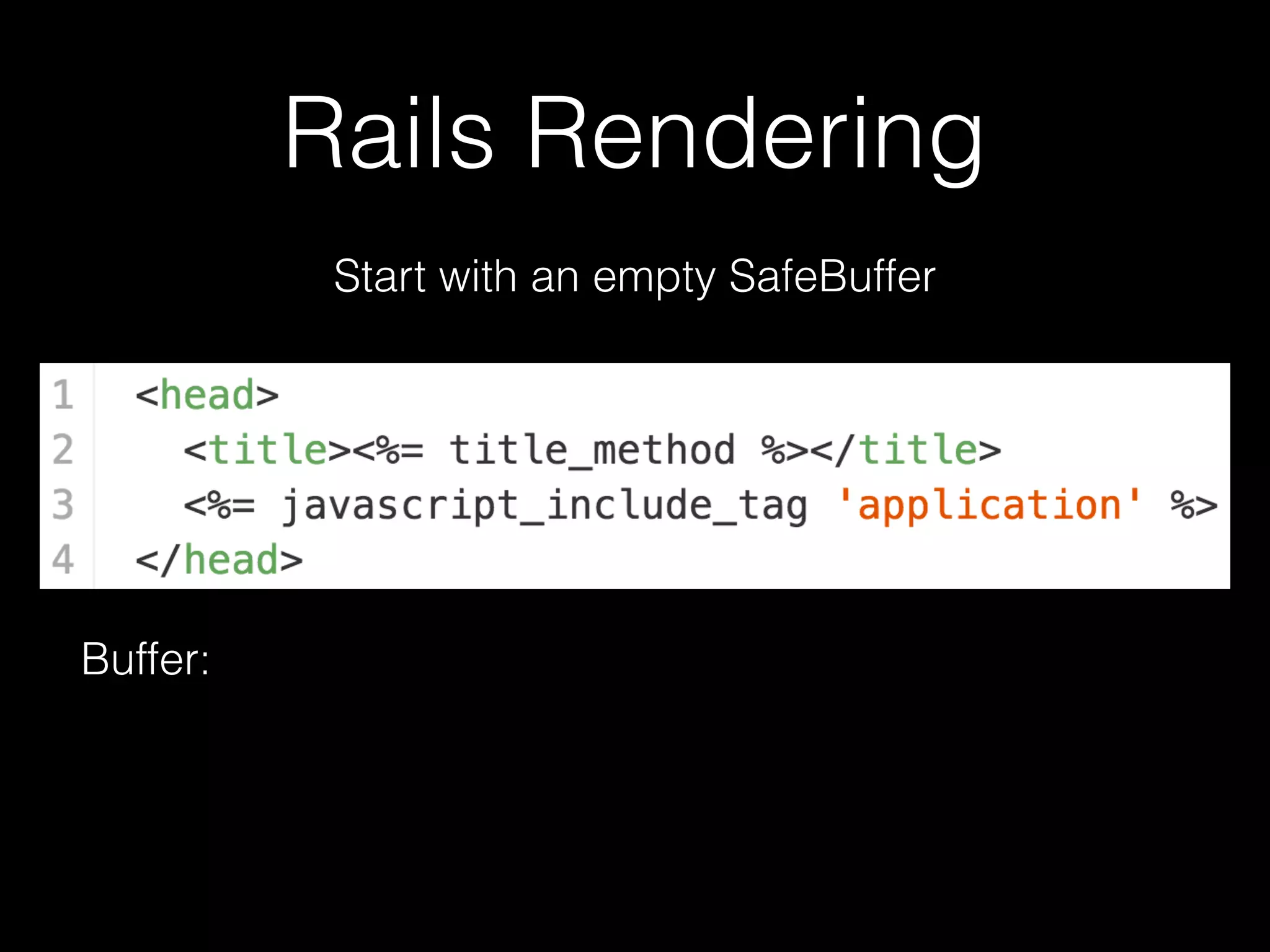
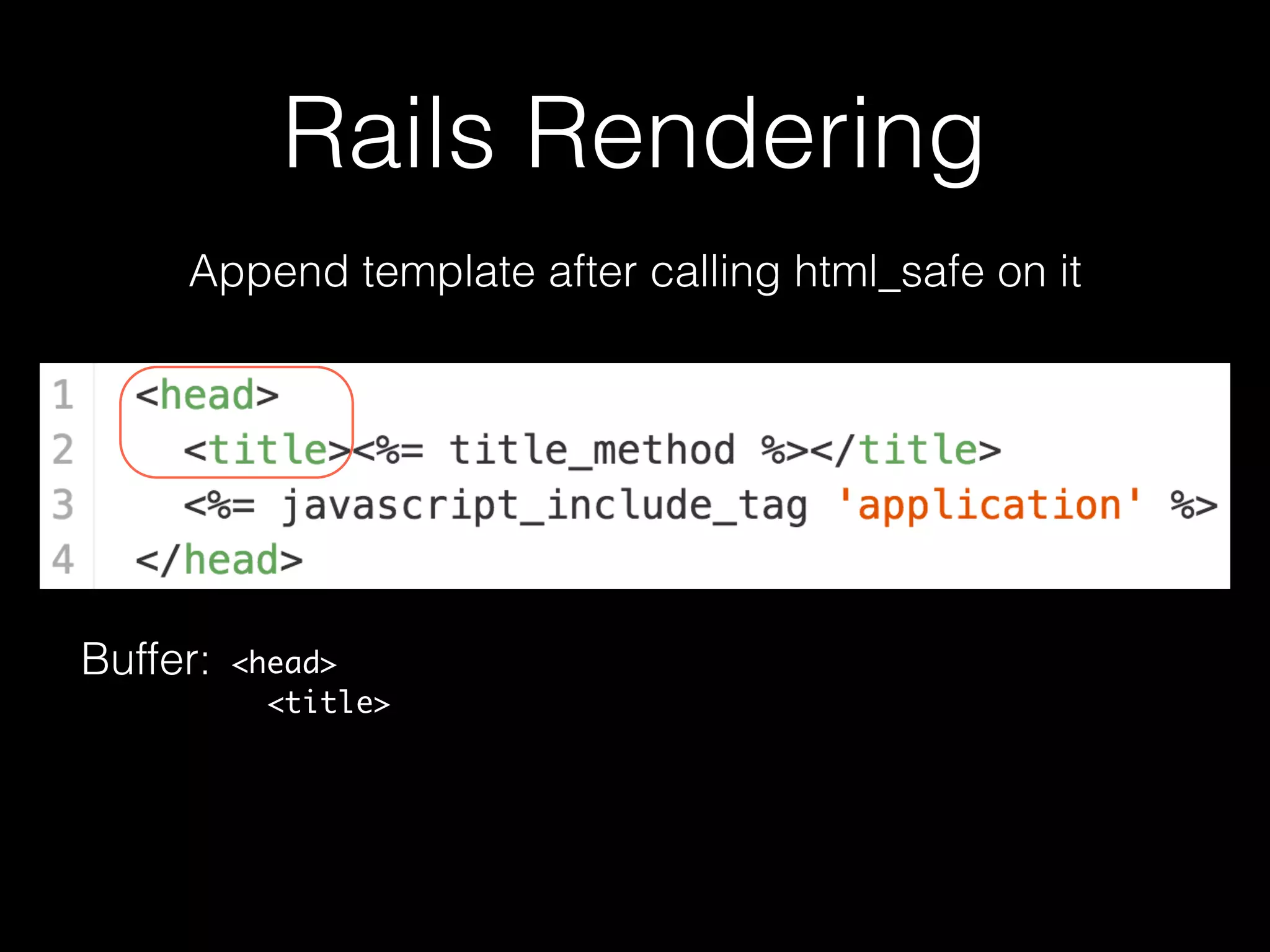
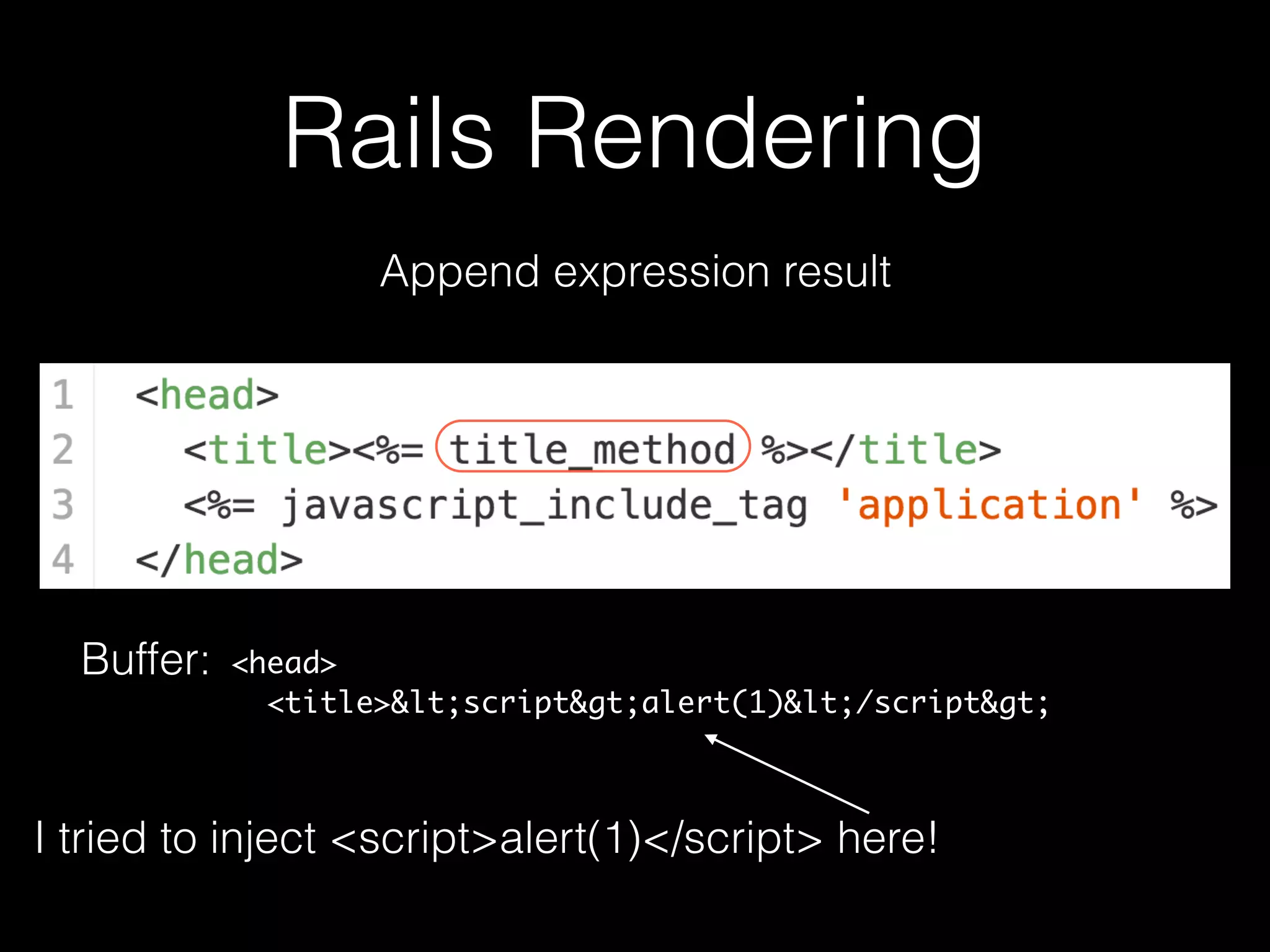
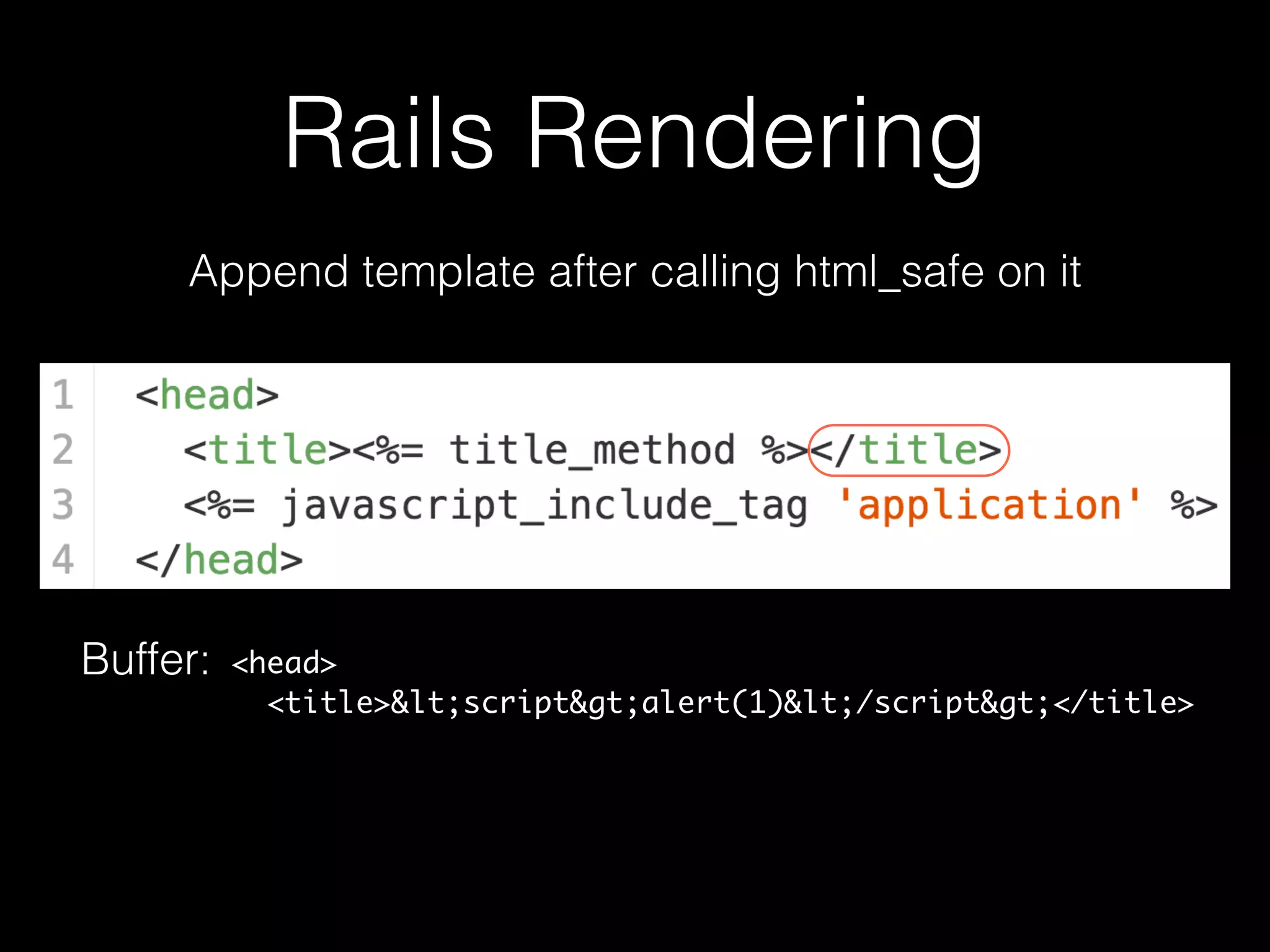
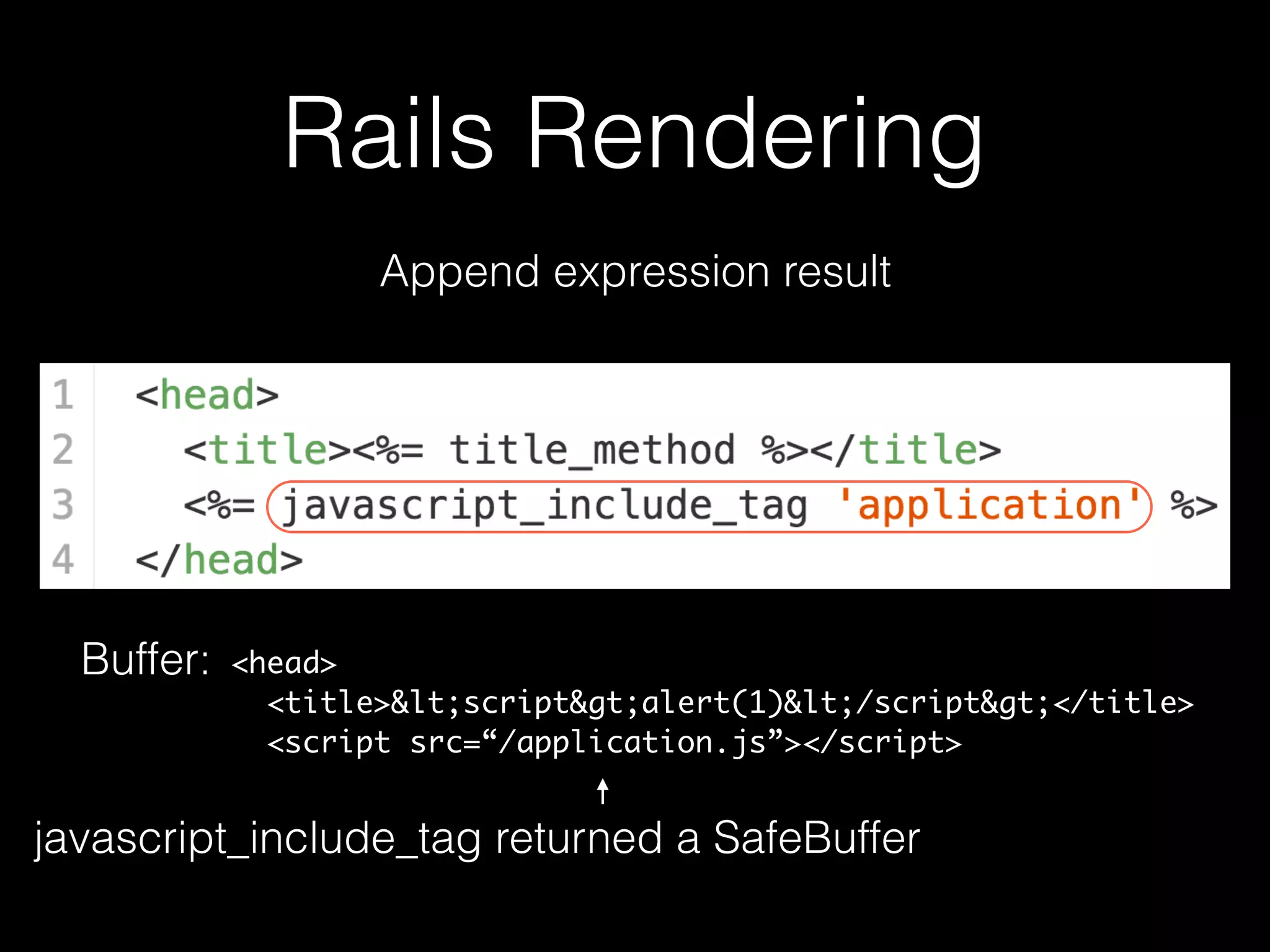
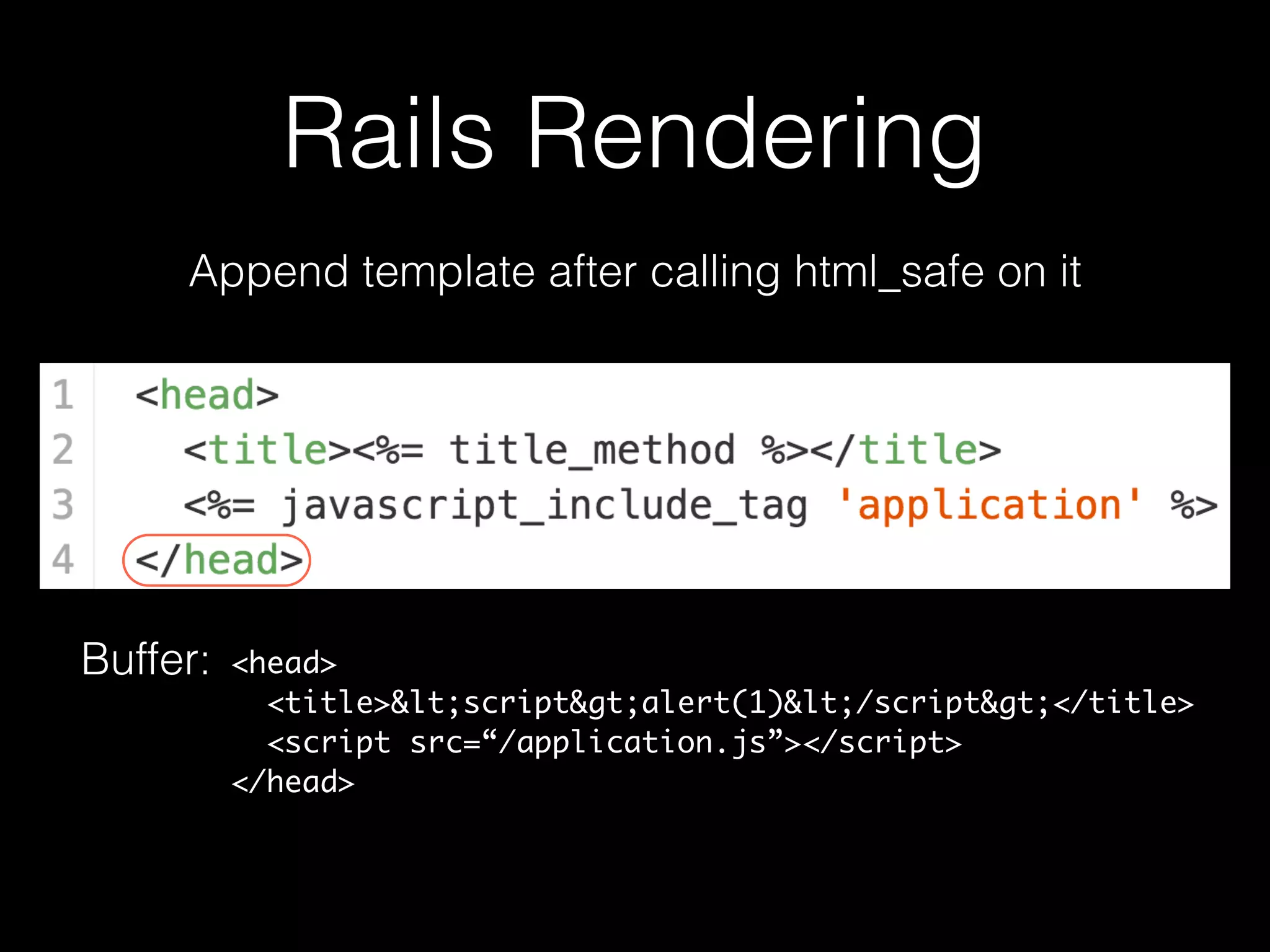
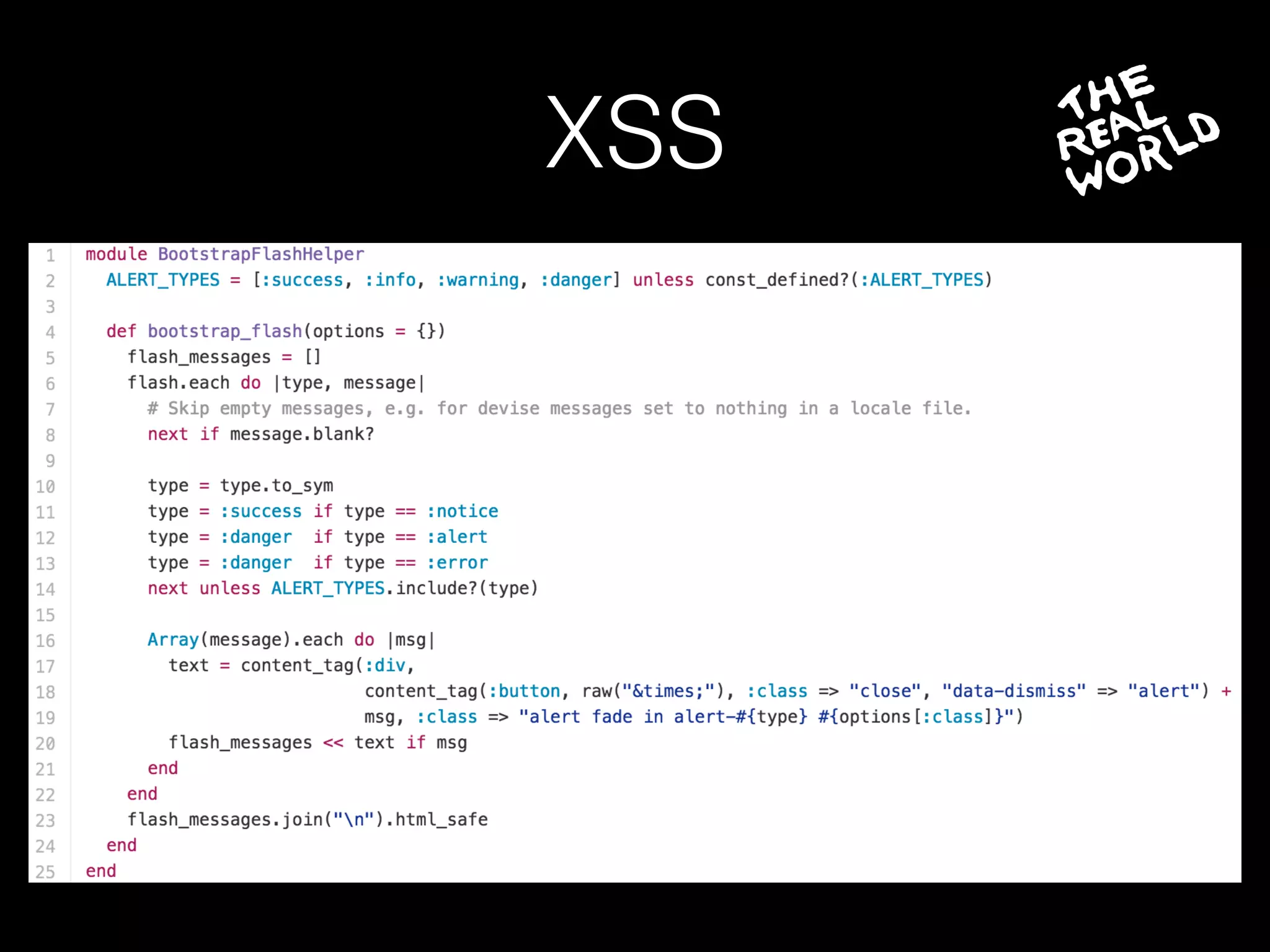
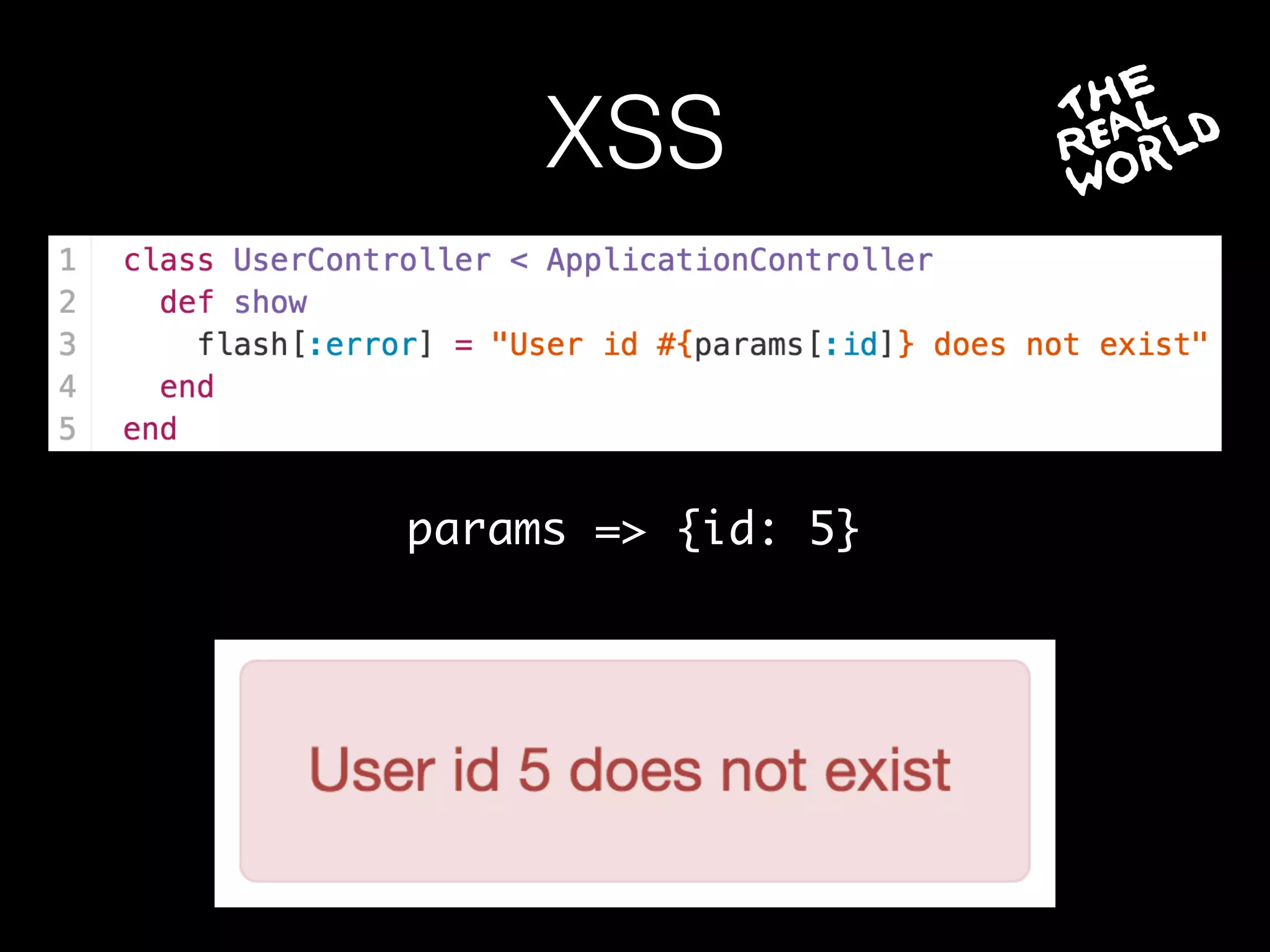
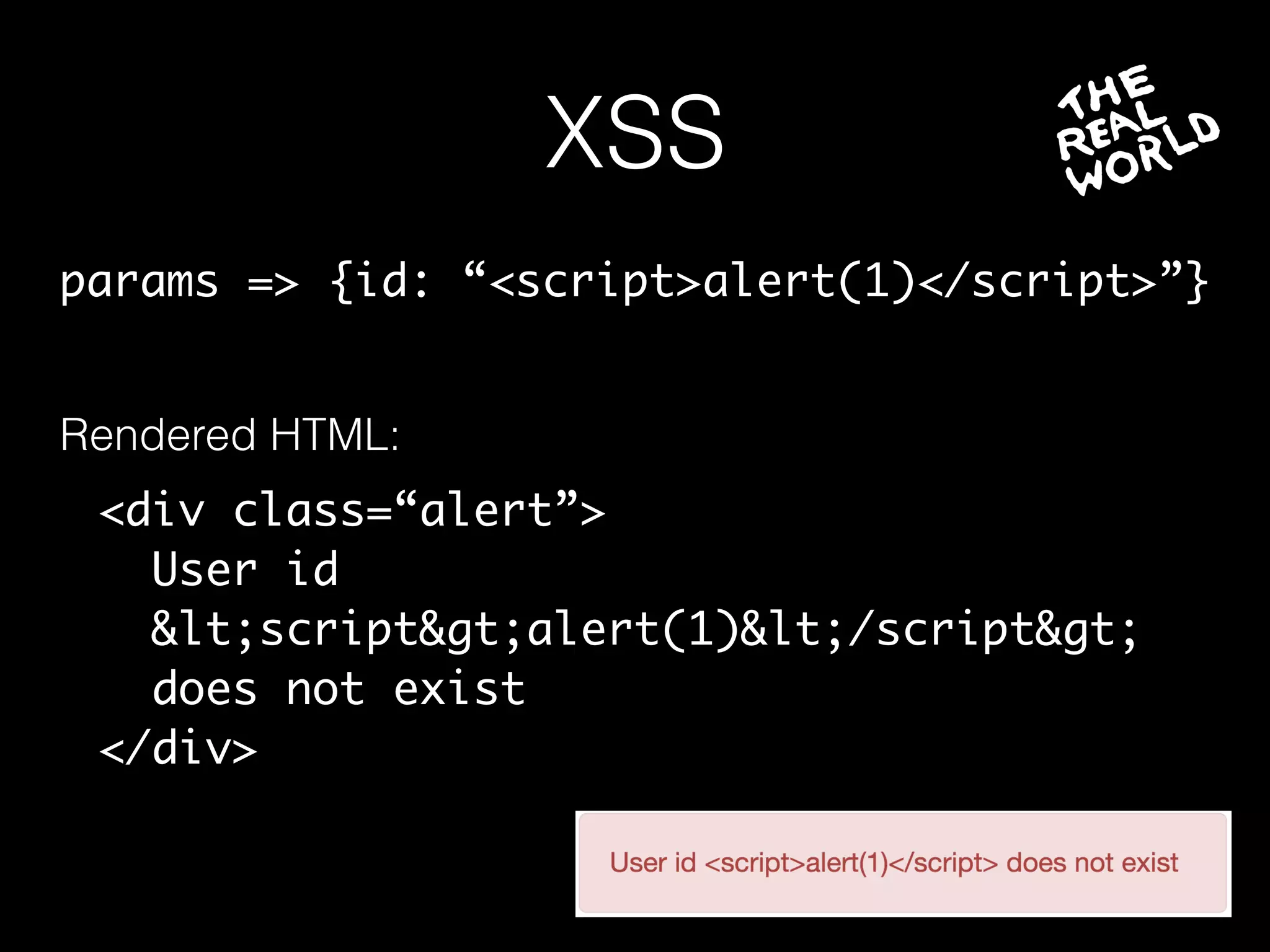
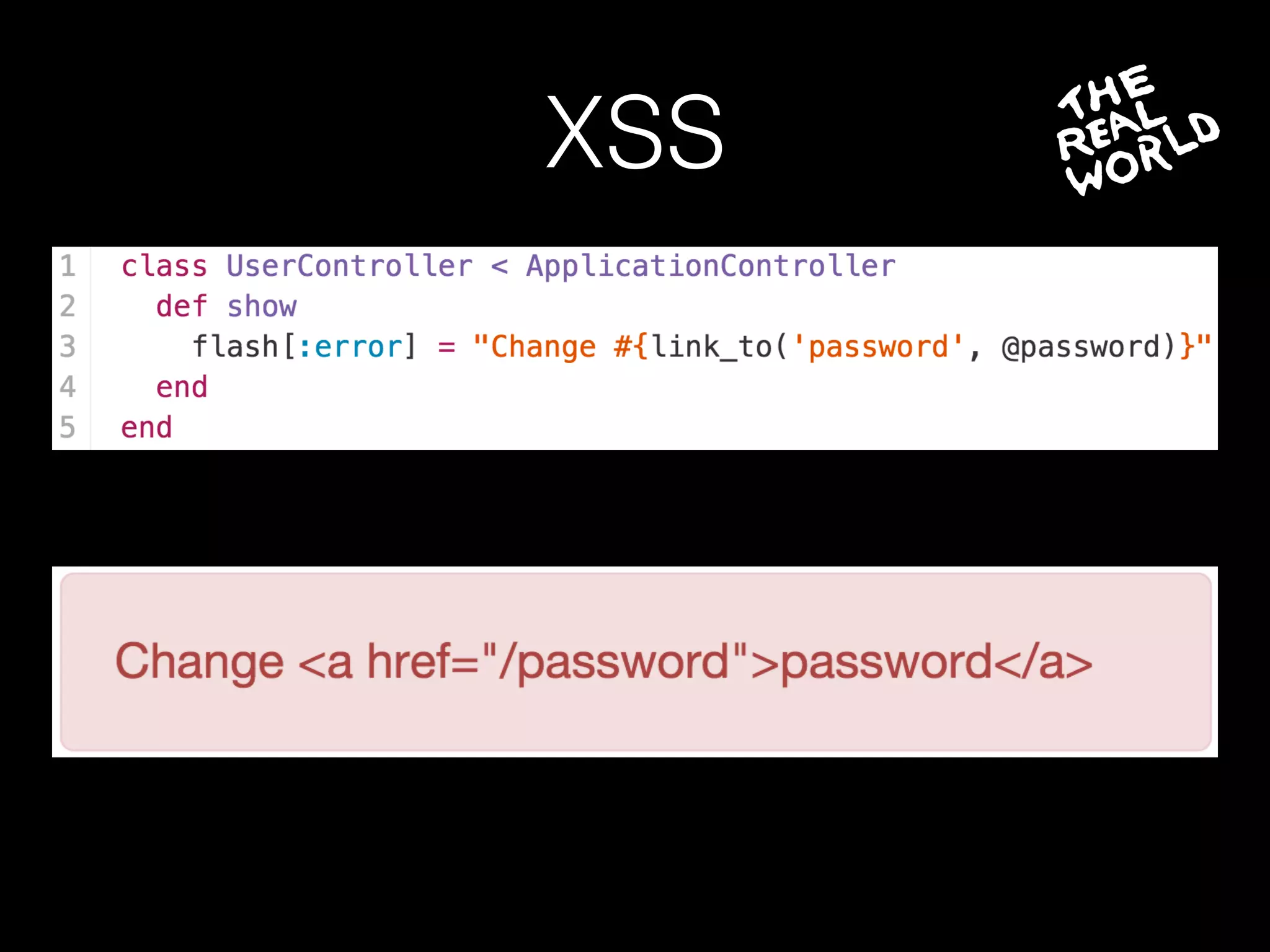
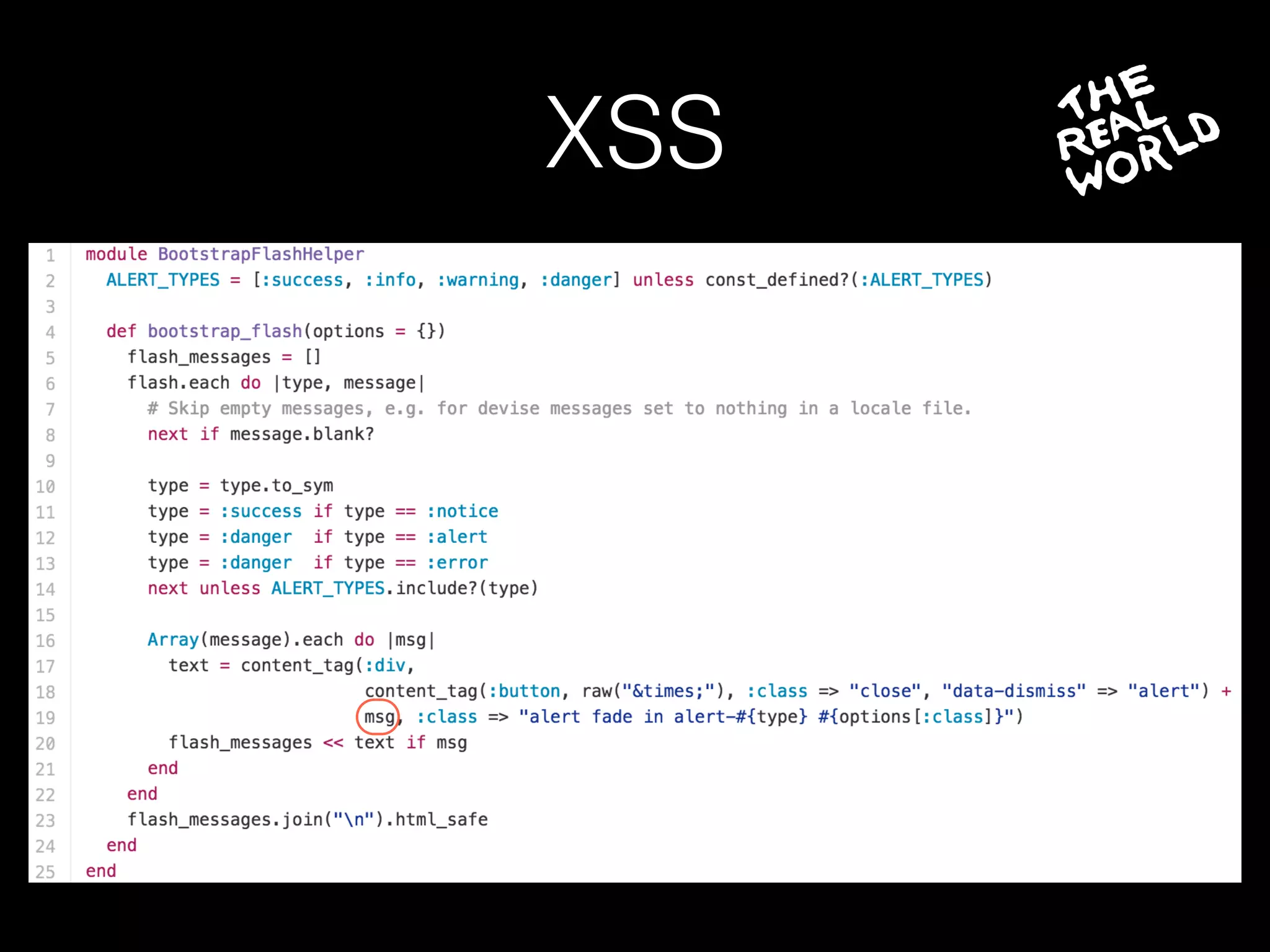
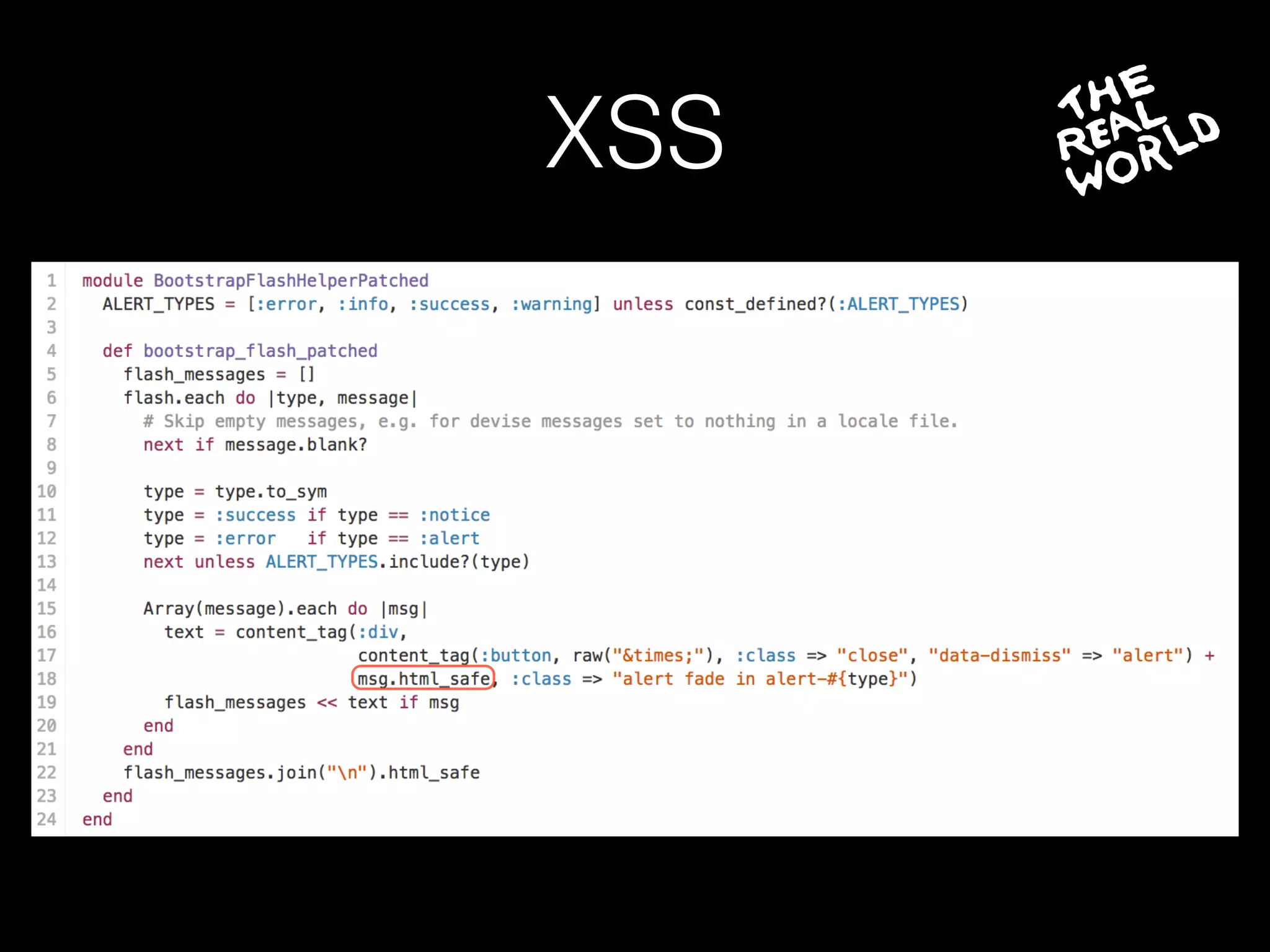
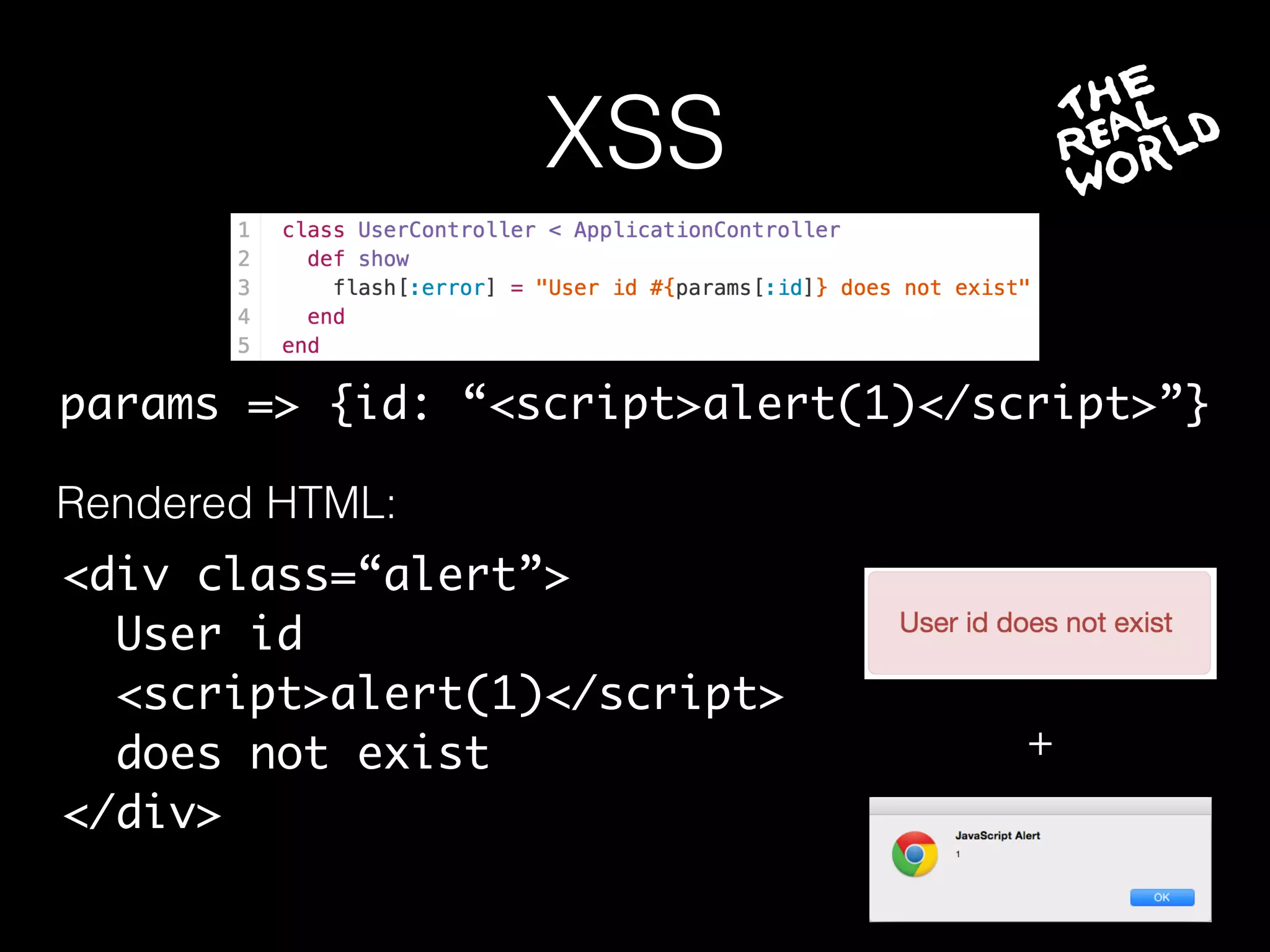
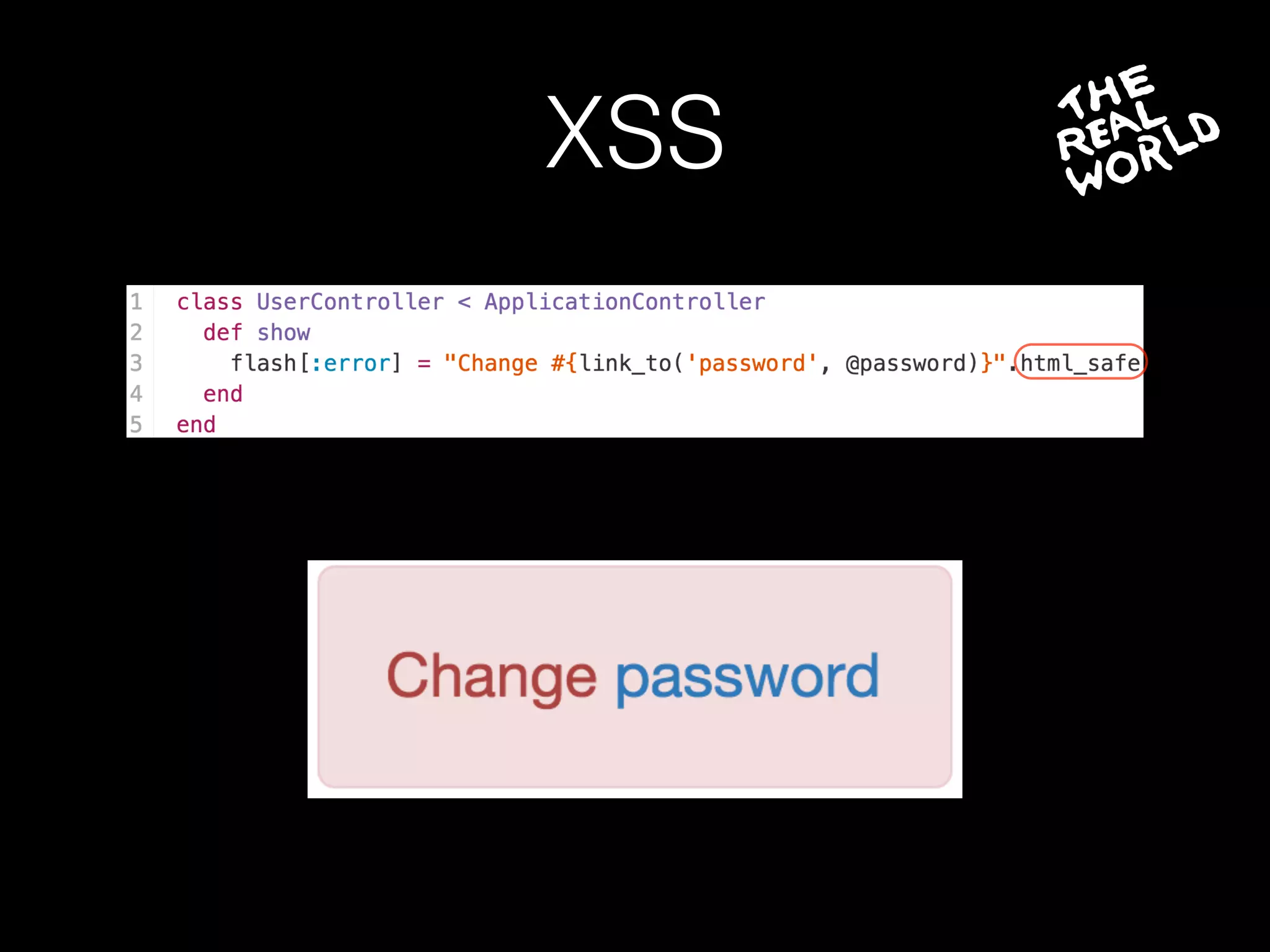
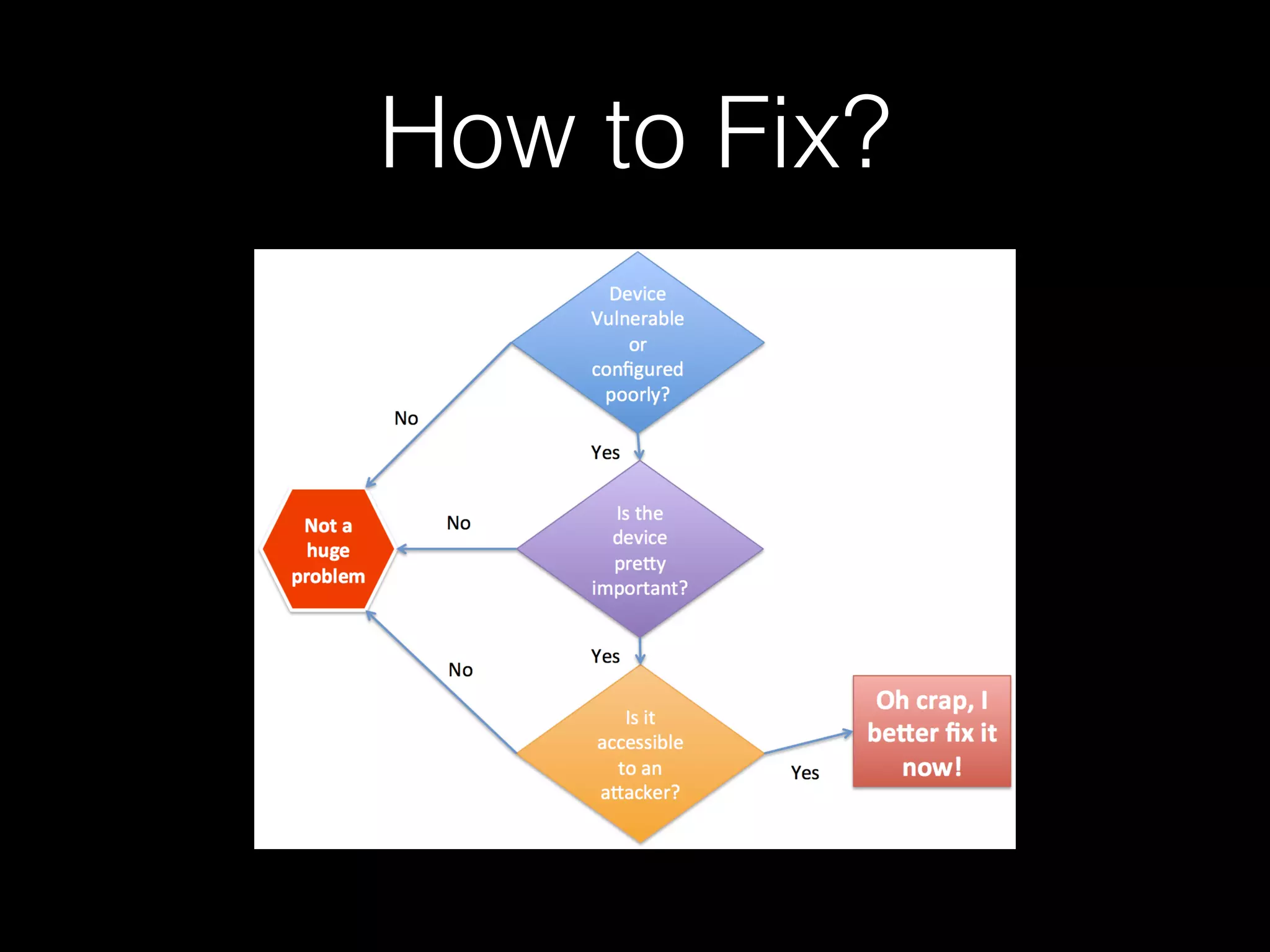
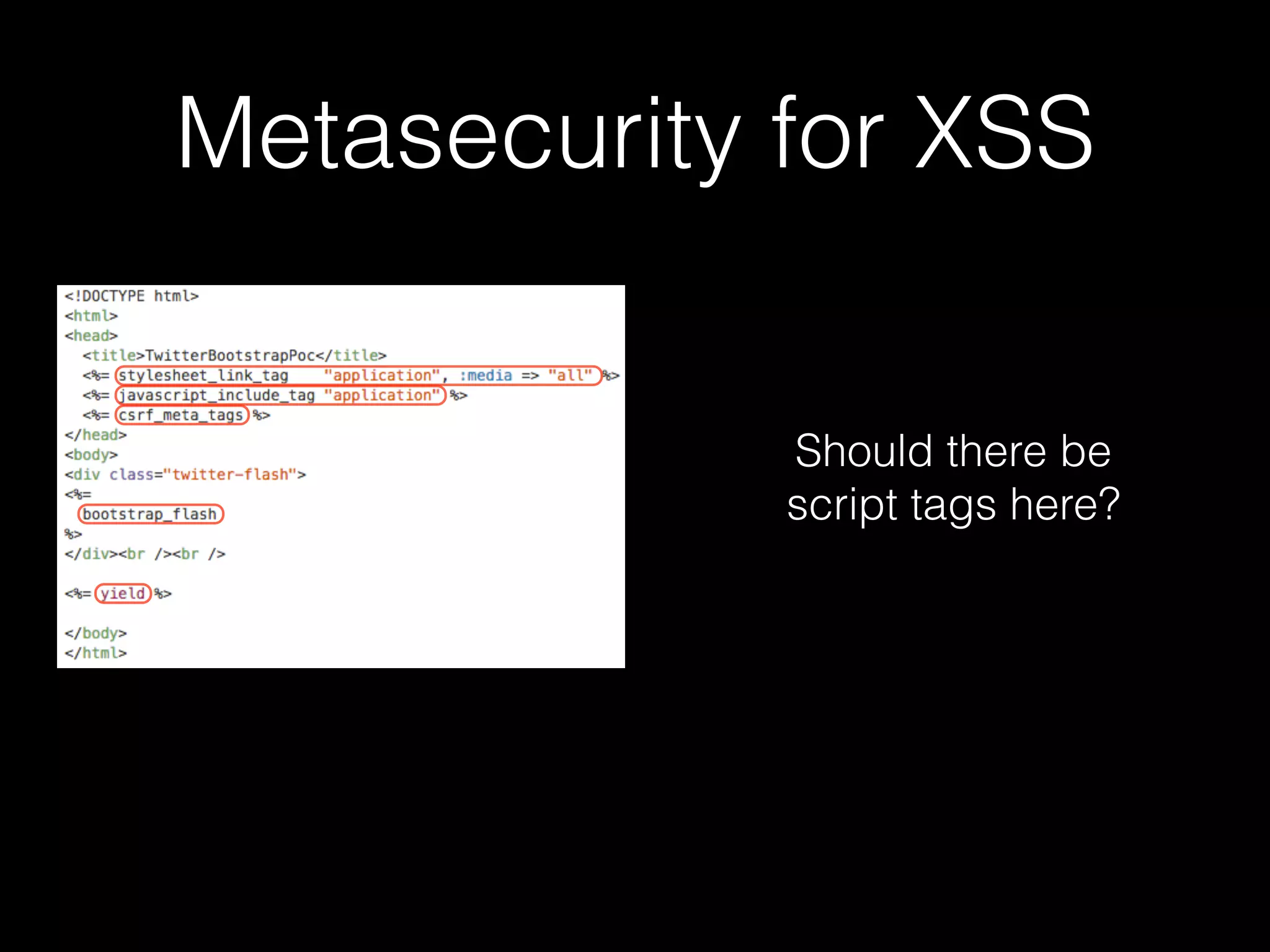
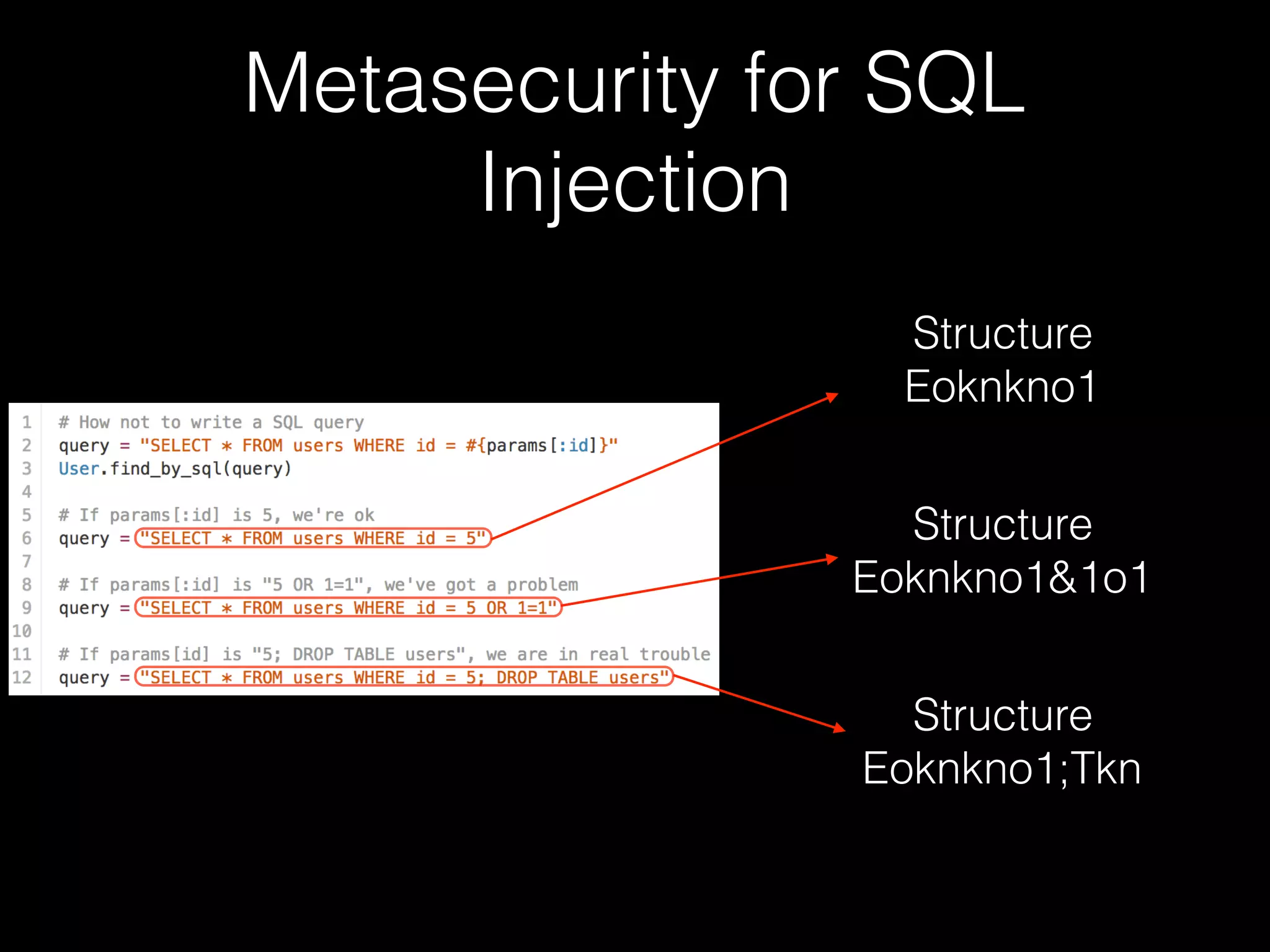
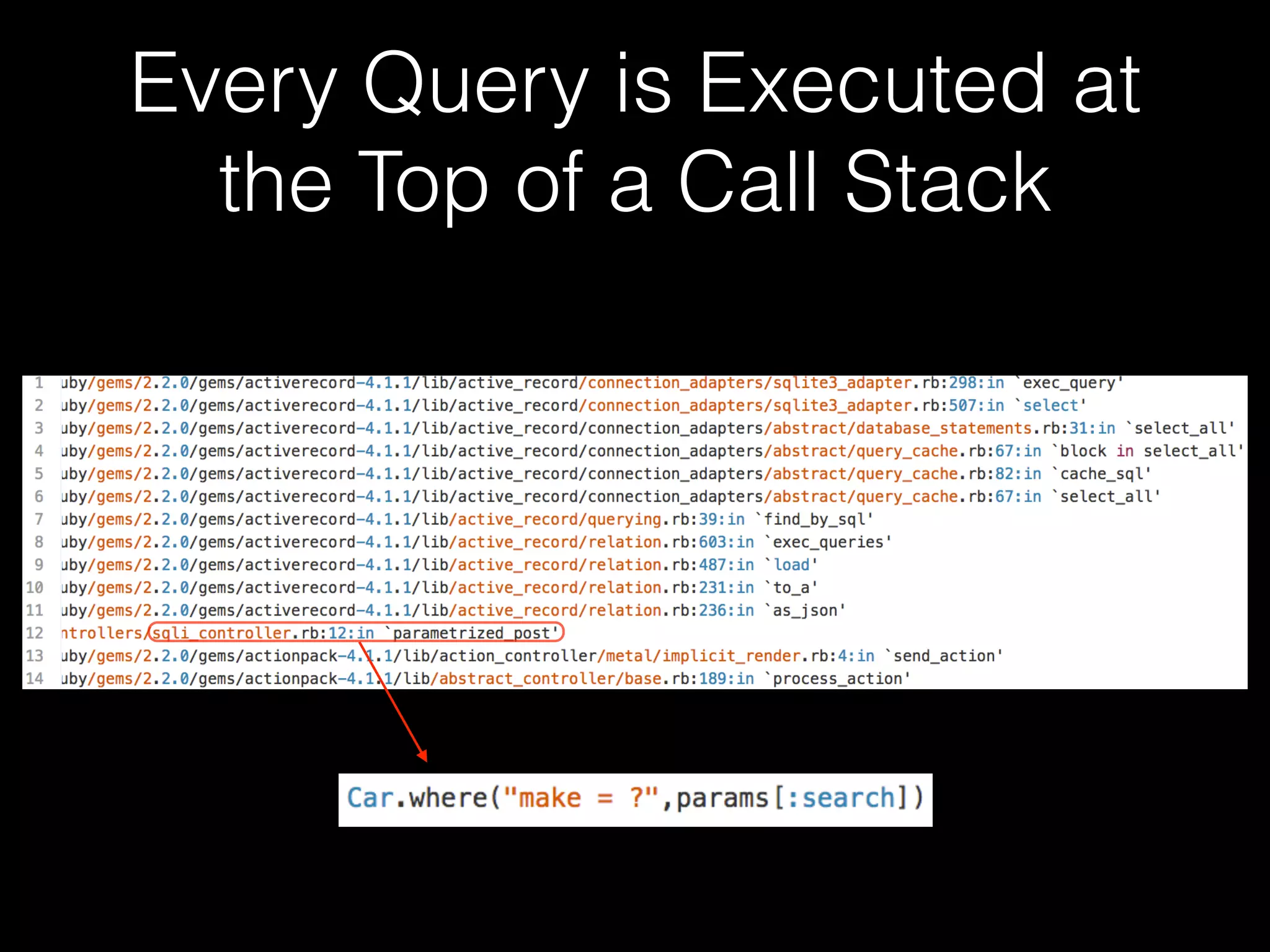
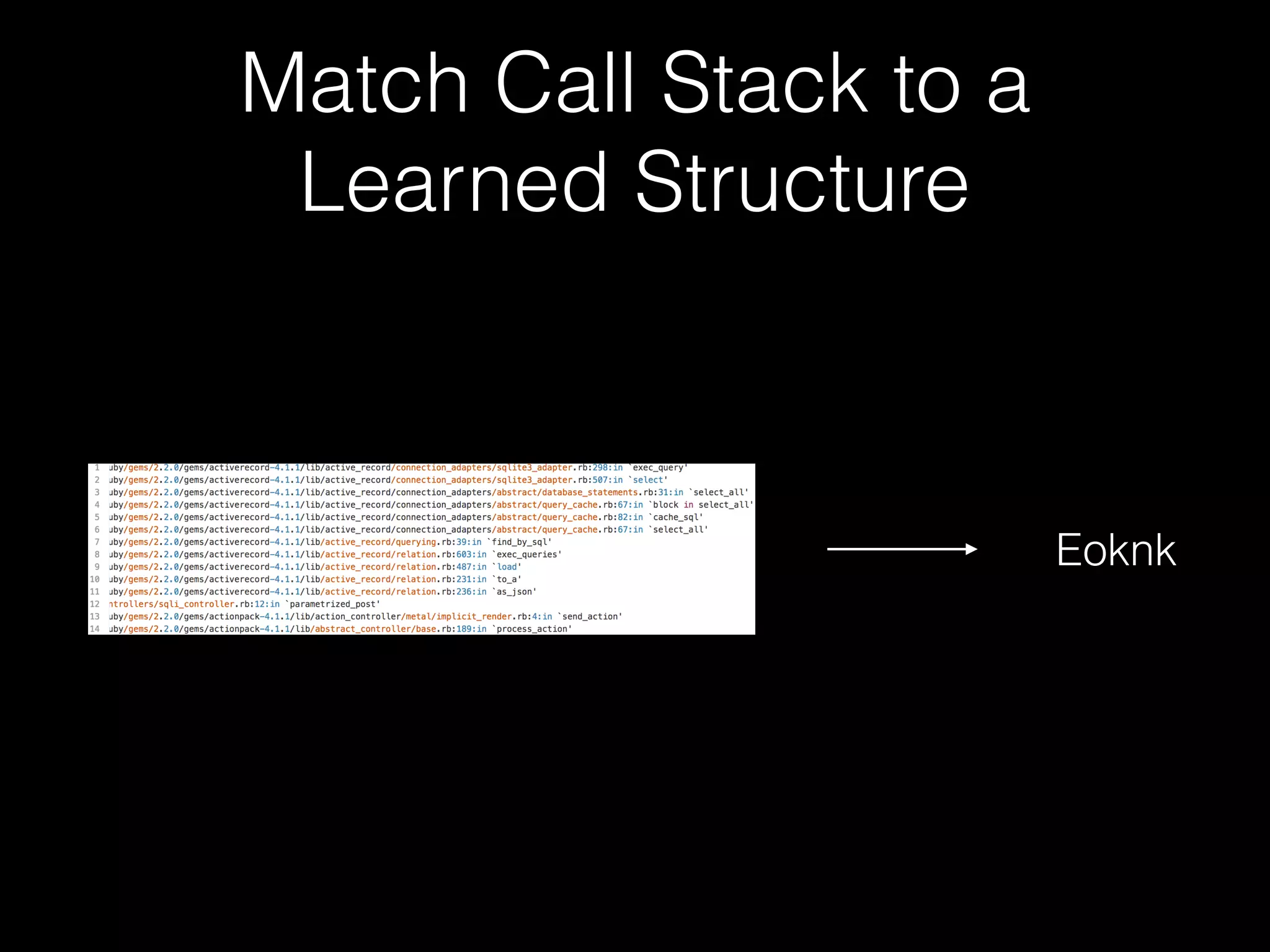
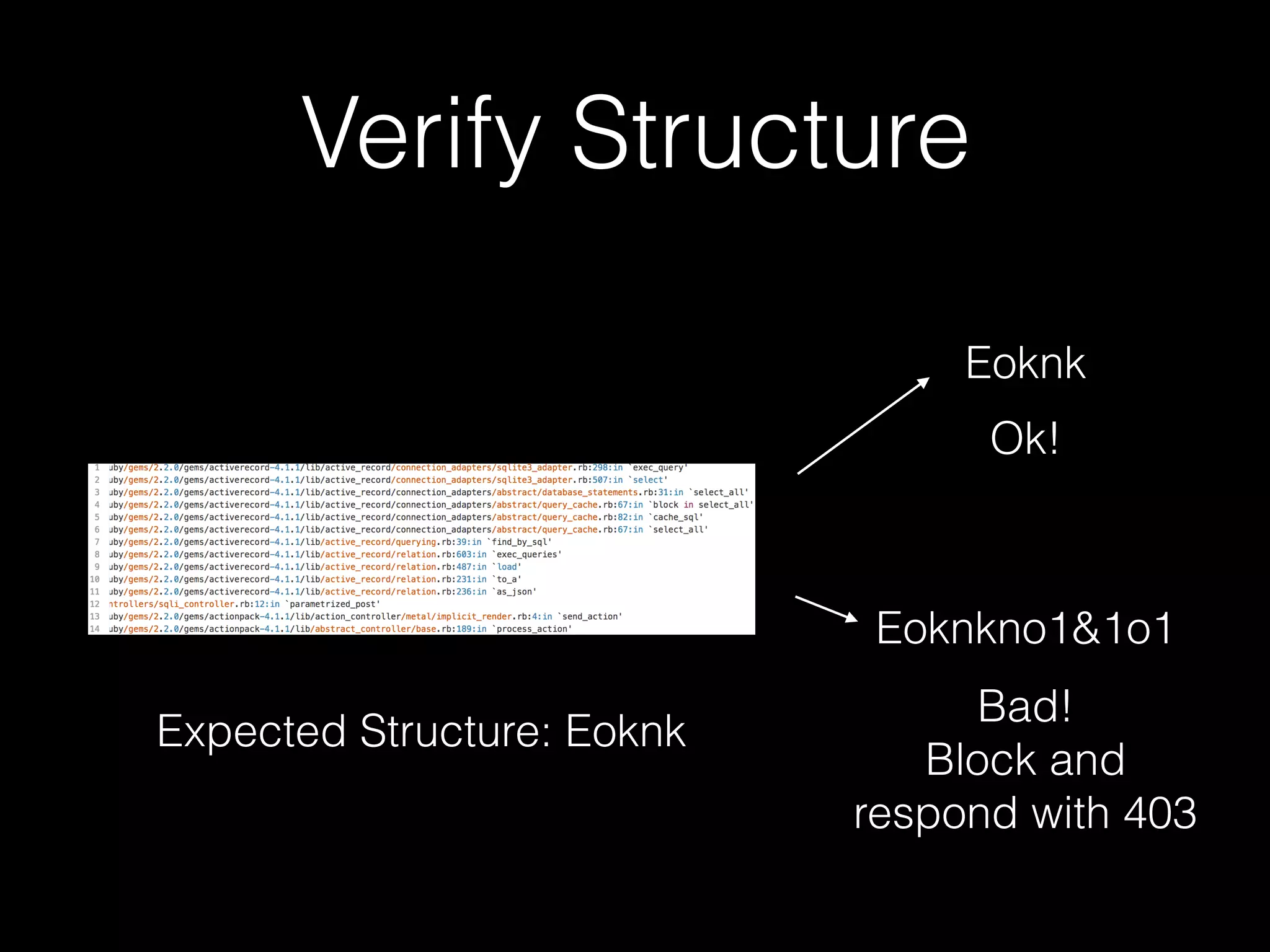
The document discusses the prevalence of web application vulnerabilities, including SQL injection and cross-site scripting (XSS), and the average time vulnerabilities remain undisclosed. It highlights the importance of implementing web application firewalls and various defensive coding practices to mitigate risks. Additionally, it mentions Immun.io as a solution for automated protection against various types of attacks and emphasizes the need for ongoing security audits and education.