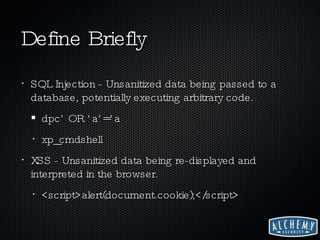
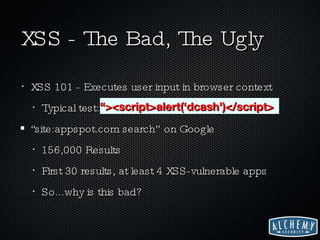
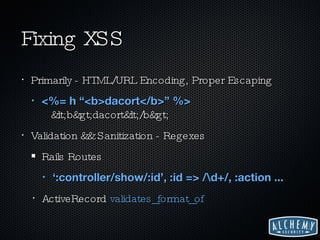
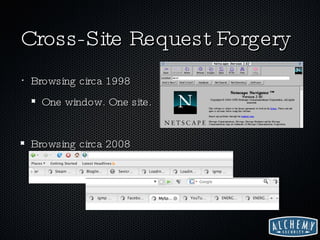
The document discusses web 2.0 security issues, focusing on vulnerabilities such as SQL injection and cross-site scripting (XSS), alongside compliance with data breach notification laws and Payment Card Industry (PCI) regulations. It emphasizes the importance of proper encoding, validation, and keeping software up-to-date to mitigate security risks. Additionally, the author provides insights on how web services should handle sensitive information and comply with legal requirements regarding data breaches.







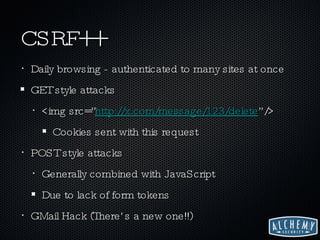
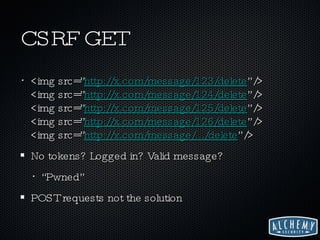



![What to Look For? Find input vectors Request.[Cookies|Form|QueryString] $_GET, $_POST, $_REQUEST (<-- careful) params[:id] Make sure output is protected Encoding to browser, Escaping to database, etc](https://image.slidesharecdn.com/hacking-in-web-2-1227746749549799-8/85/StartPad-Countdown-2-Startup-Security-Hacking-and-Compliance-in-a-Web-2-0-World-17-320.jpg)











![Thanks [email_address] http://xkcd.com/327/](https://image.slidesharecdn.com/hacking-in-web-2-1227746749549799-8/85/StartPad-Countdown-2-Startup-Security-Hacking-and-Compliance-in-a-Web-2-0-World-30-320.jpg)