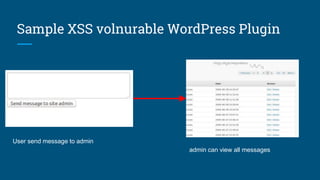
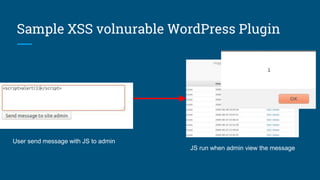
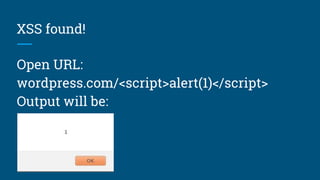
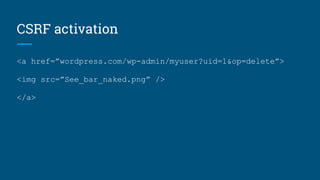
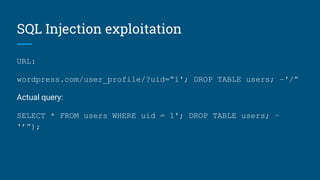
The document discusses various security vulnerabilities in WordPress, including XSS, CSRF, and SQL injection. It highlights specific examples of vulnerable plugins and emphasizes the importance of input validation, sanitization, and regular updates. Additionally, it provides resources and tips for enhancing WordPress security.







![XSS issues coming from unexpected places
<?php
//404 page
Print “You came from {$_SERVER['HTTP_REFERER']}, but you
got 404.”;
die;](https://image.slidesharecdn.com/wordpress-160331155630/85/WordPress-Security-101-for-developers-11-320.jpg)
![XSS breach safe
<?php
//404 page
$safe_output = echo esc_url( $_SERVER['HTTP_REFERER'] );
Print “You came from $safe_output, but you got 404.”;
die;](https://image.slidesharecdn.com/wordpress-160331155630/85/WordPress-Security-101-for-developers-13-320.jpg)





![SQL Injection example
Code at site:
$account_id = $ _GET[‘uid’];
$myrows =
$wpdb->get_results("SELECT * FROM users WHERE uid =
$account_id”);
//Display users](https://image.slidesharecdn.com/wordpress-160331155630/85/WordPress-Security-101-for-developers-20-320.jpg)



![App code that cause server changes:
function _avatar_uploader_view() {
$filename = $_GET['file'];
$filename = drupal_basename($filename);
$upload_dir = _avatar_uploader_tmp_path();
$file = $upload_dir . '/' . $filename;
$type = file_get_mimetype($file); //php 5.2
header("Content-Type: $type");
echo file_get_contents($file);
exit;
}](https://image.slidesharecdn.com/wordpress-160331155630/85/WordPress-Security-101-for-developers-25-320.jpg)