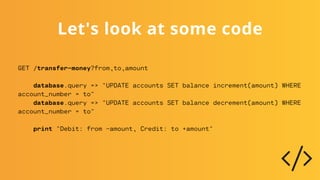
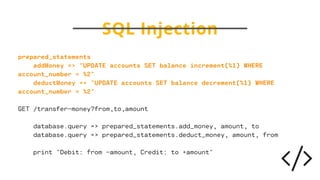
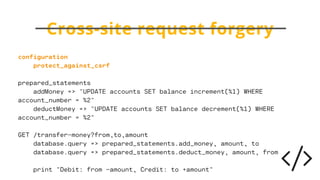
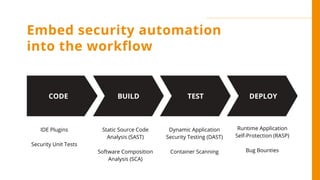
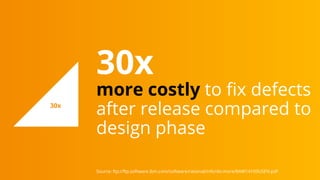
The document discusses the critical importance of secure coding practices in software development, highlighting various vulnerabilities such as SQL injection, cross-site scripting, and broken access control. It emphasizes the need for developers to utilize secure coding guidelines, adopt automated security measures, and maintain a culture of security awareness within their teams. Furthermore, it illustrates that proactive security measures can significantly reduce the risk of security incidents and the cost of fixing vulnerabilities post-release.