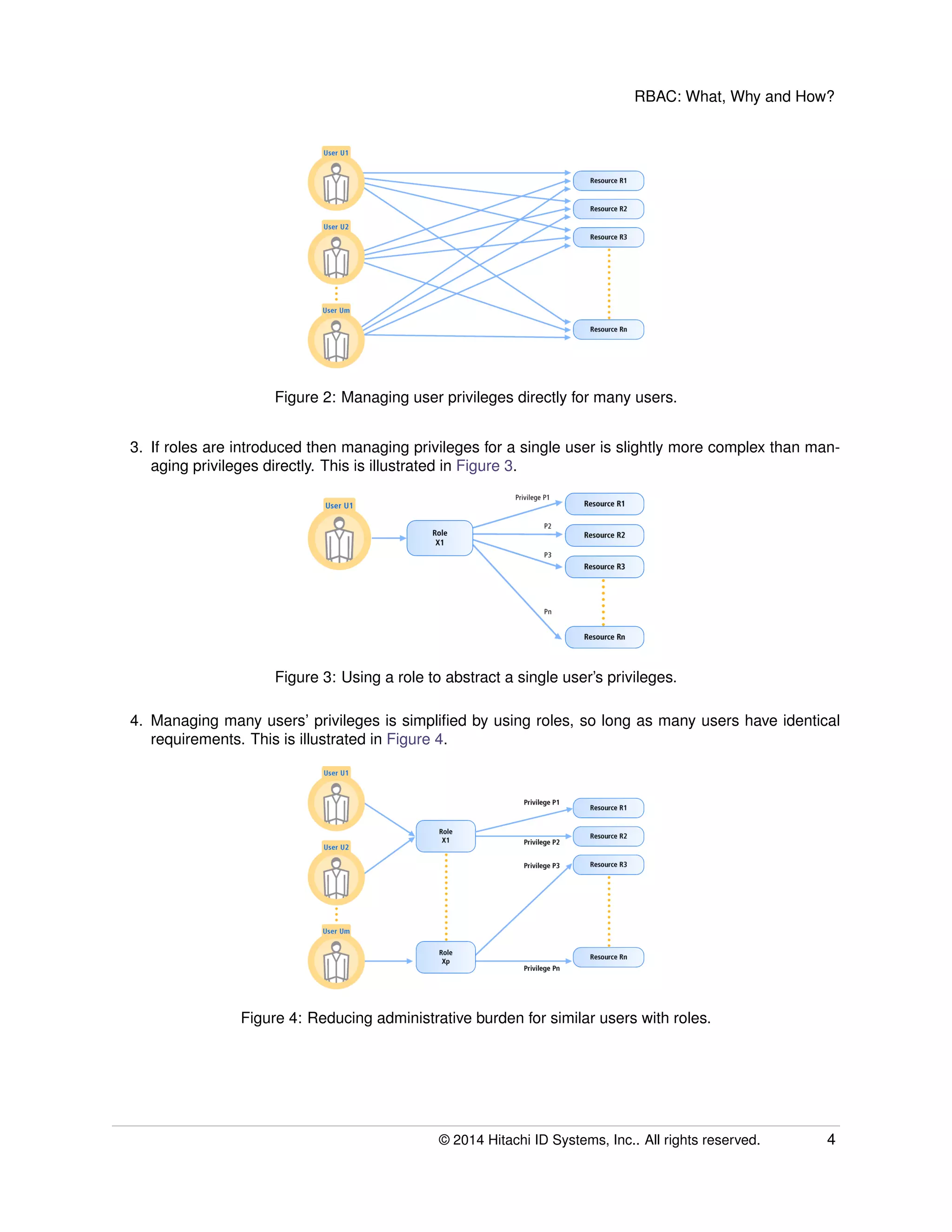
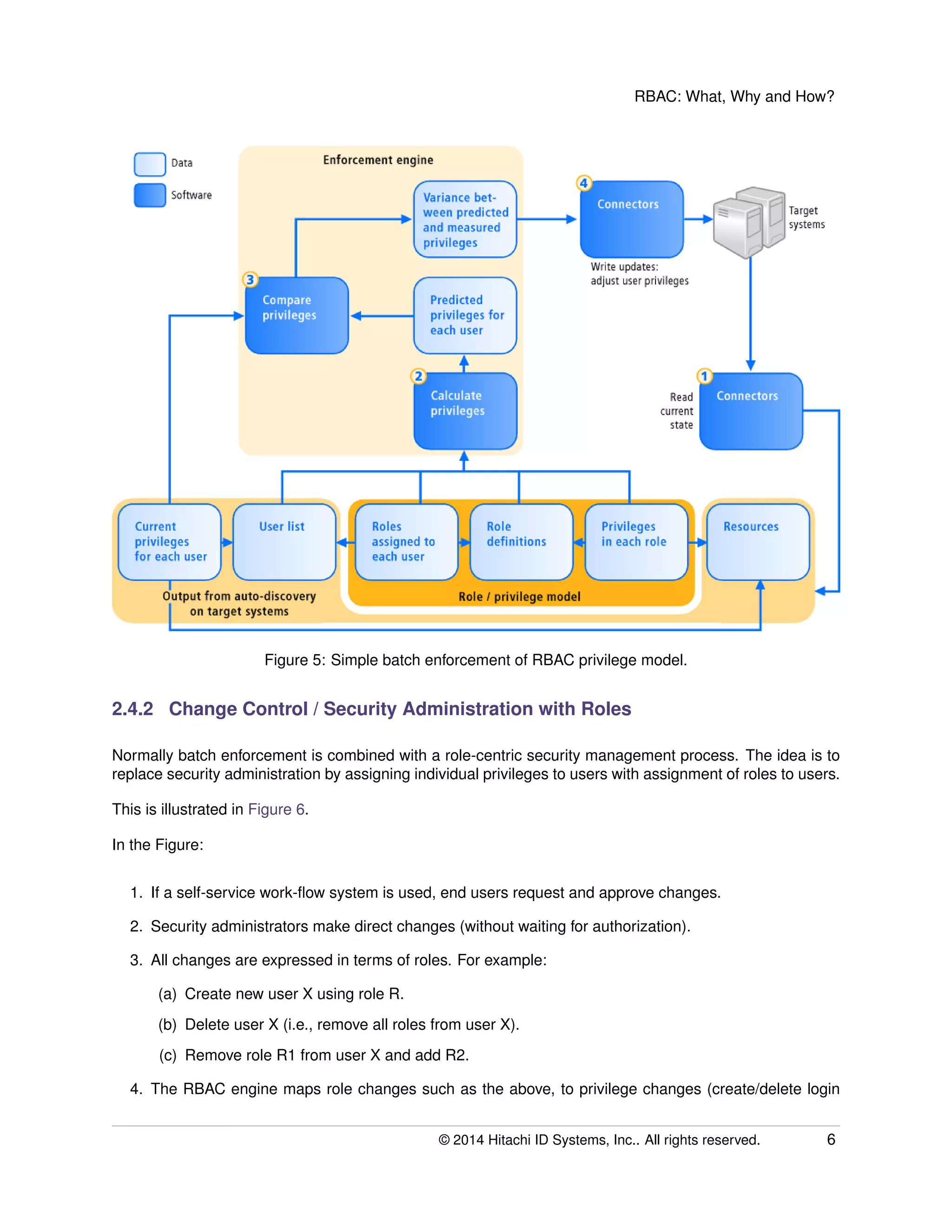
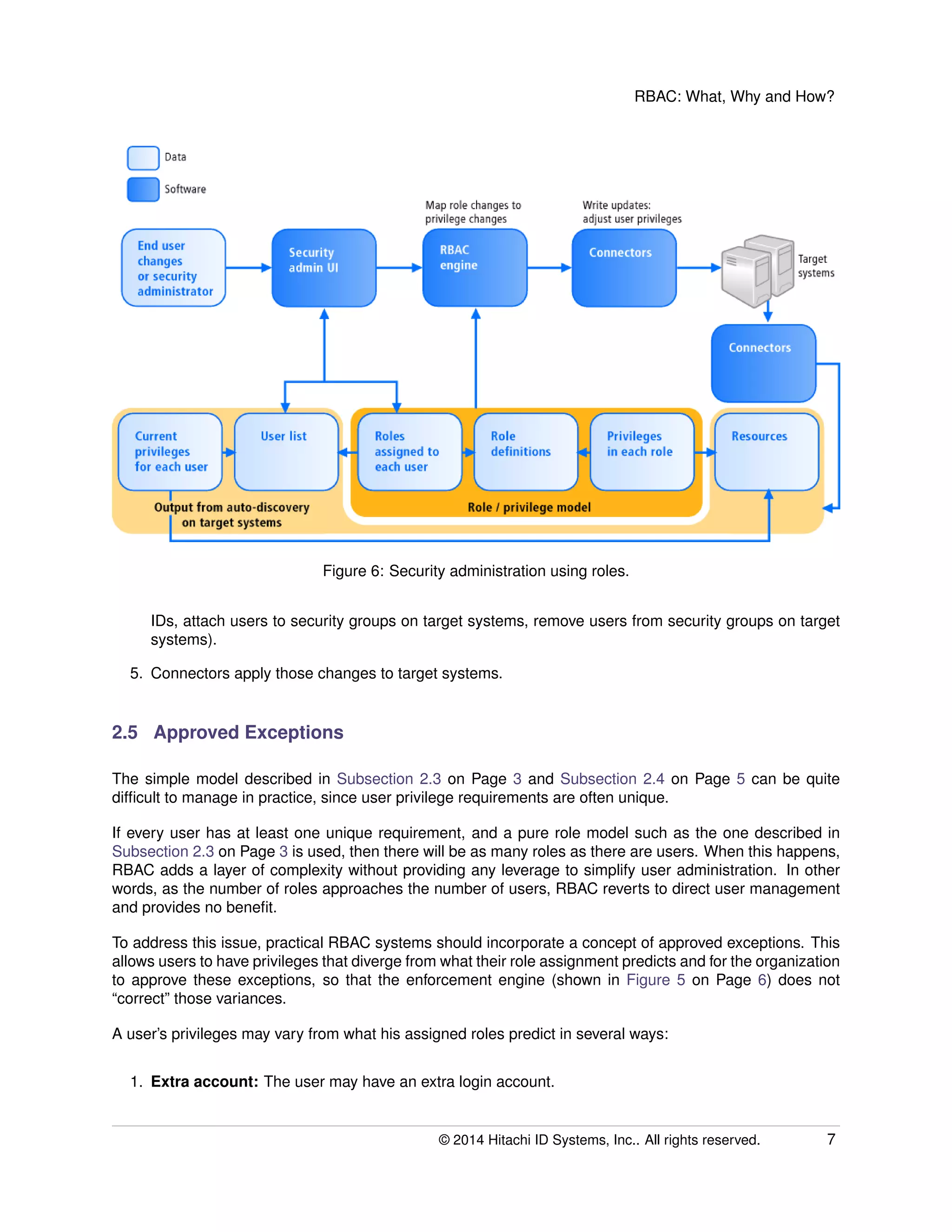
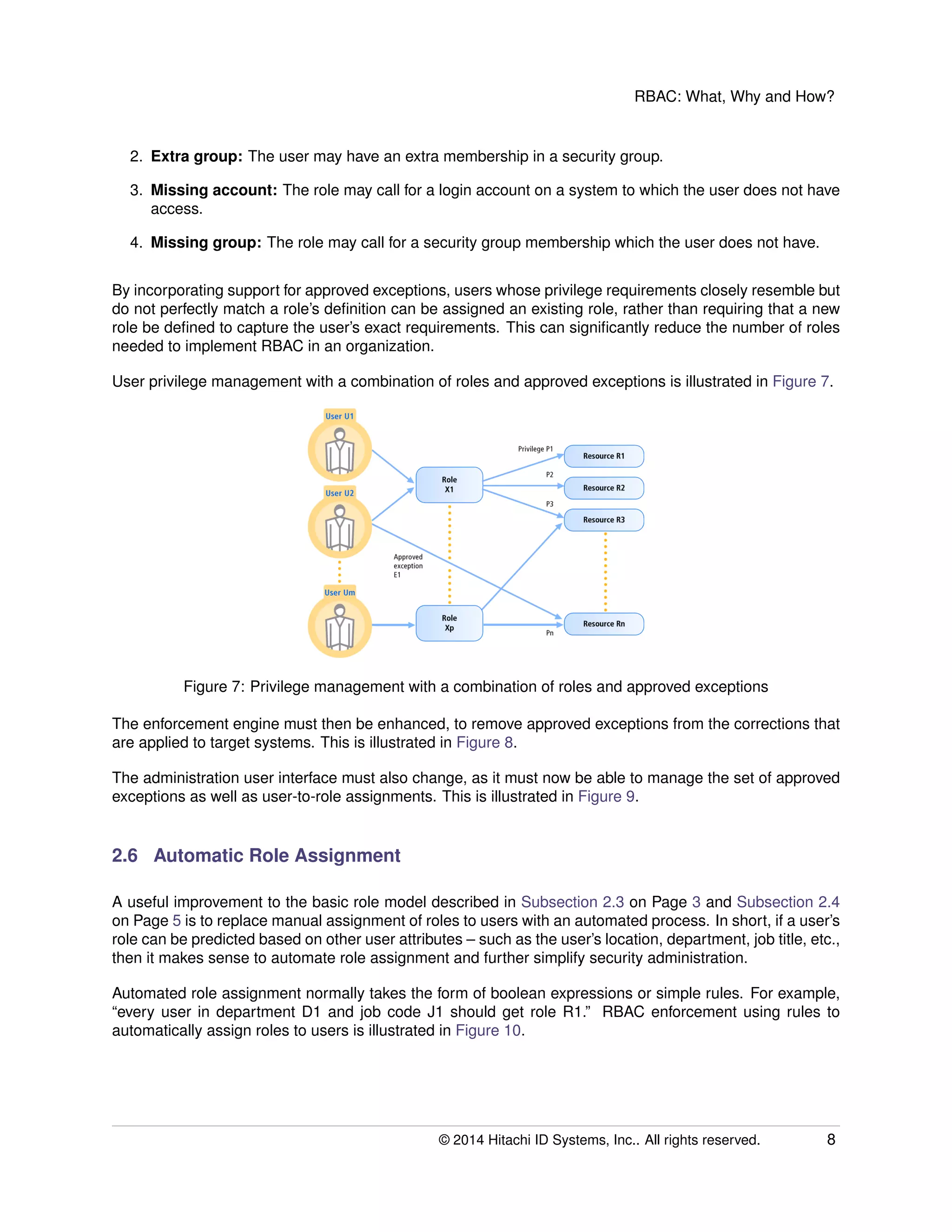
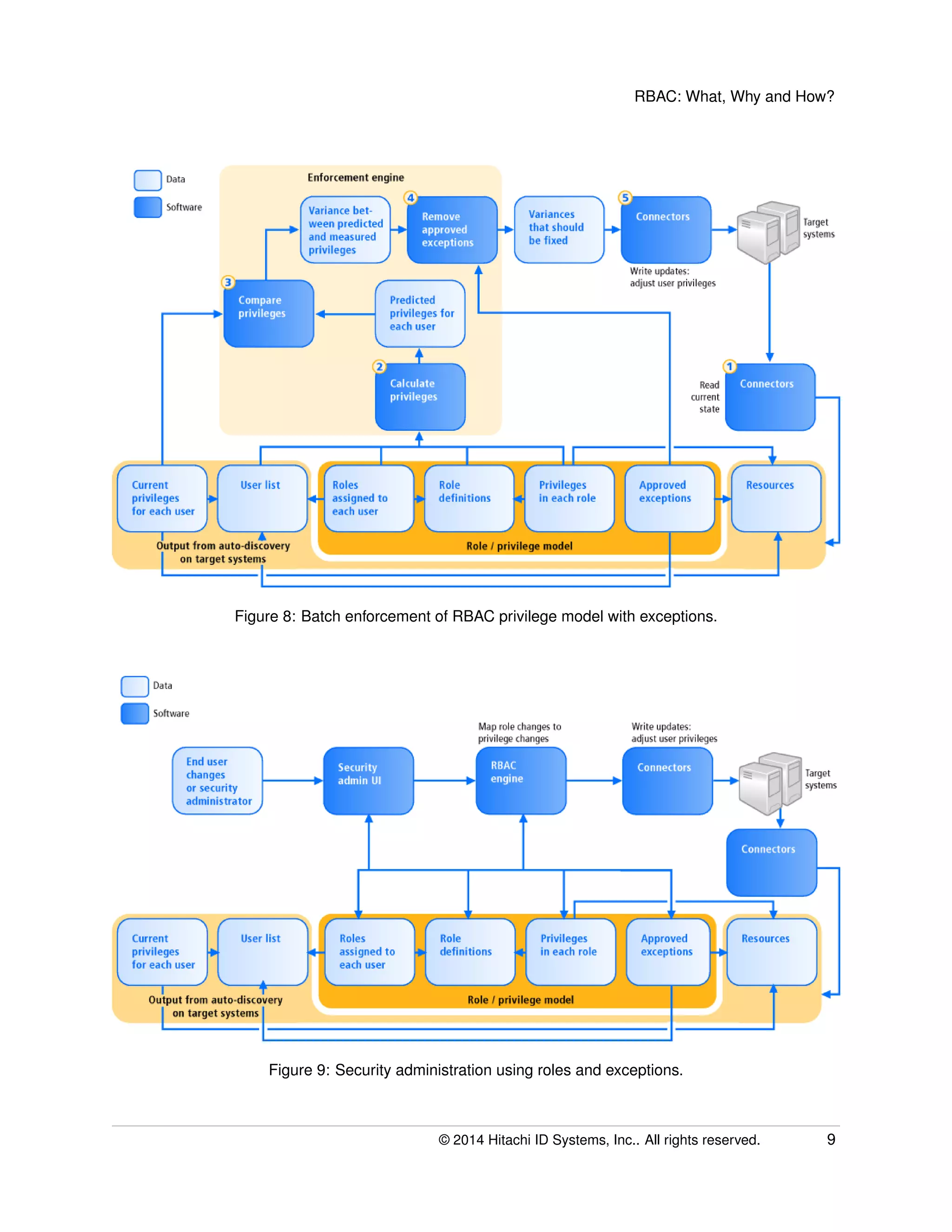
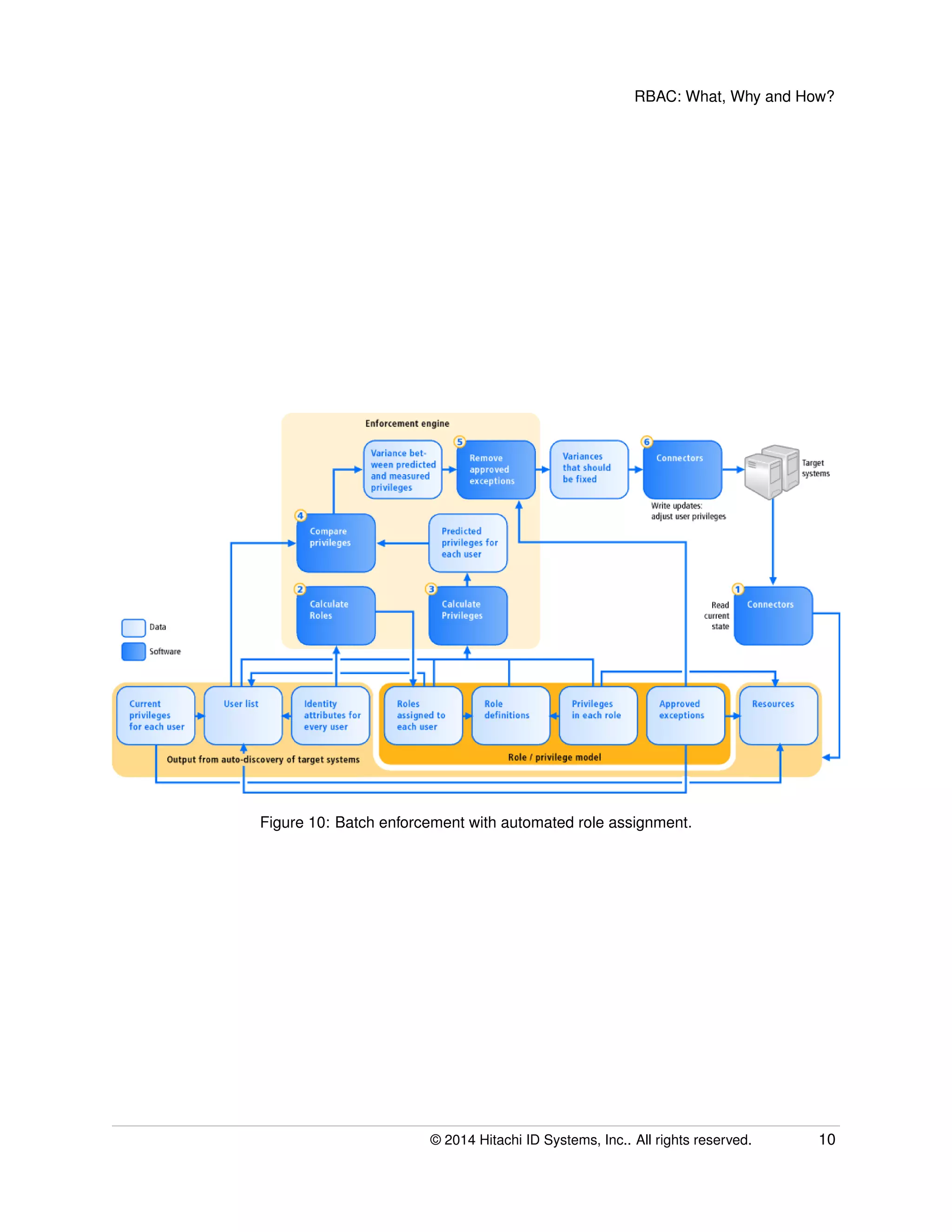
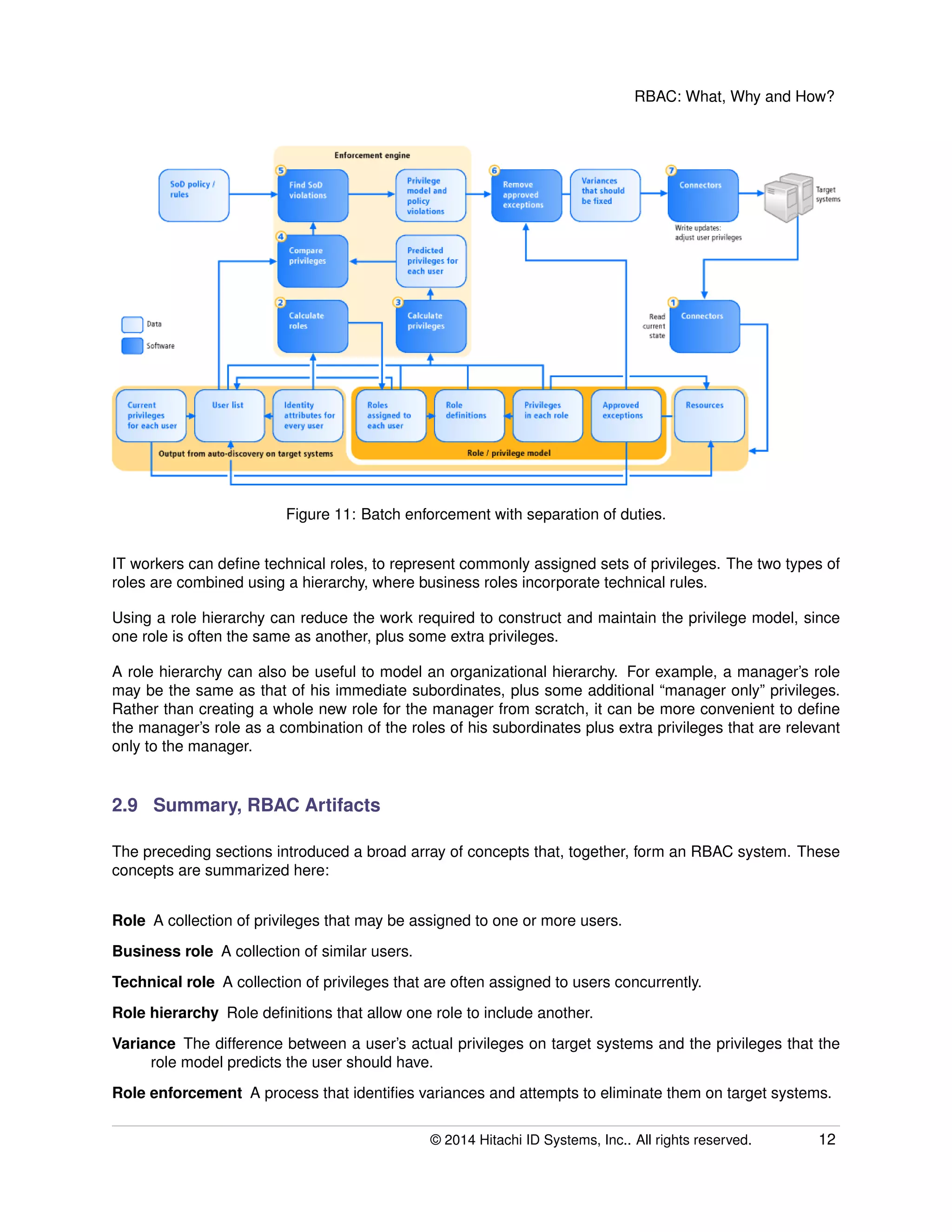
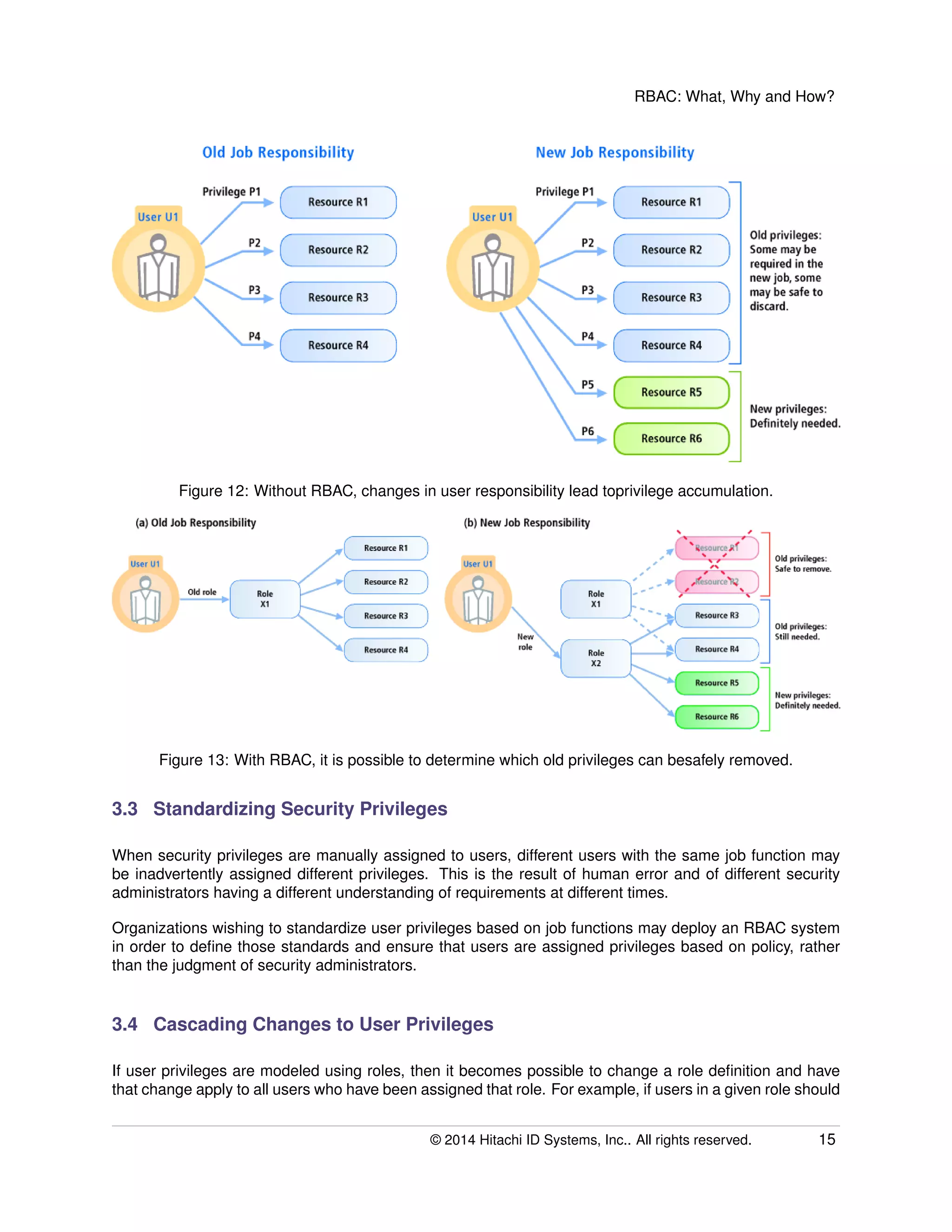
The document provides an overview of Role-Based Access Control (RBAC), its definitions, benefits, and implementation processes for managing user access to IT resources. It discusses the organizational impact of RBAC deployment, including maintaining the RBAC system and addressing individual user privilege exceptions. The text also outlines the simplification of security management through role assignments and the maintenance of compliance through batch enforcement and change control processes.