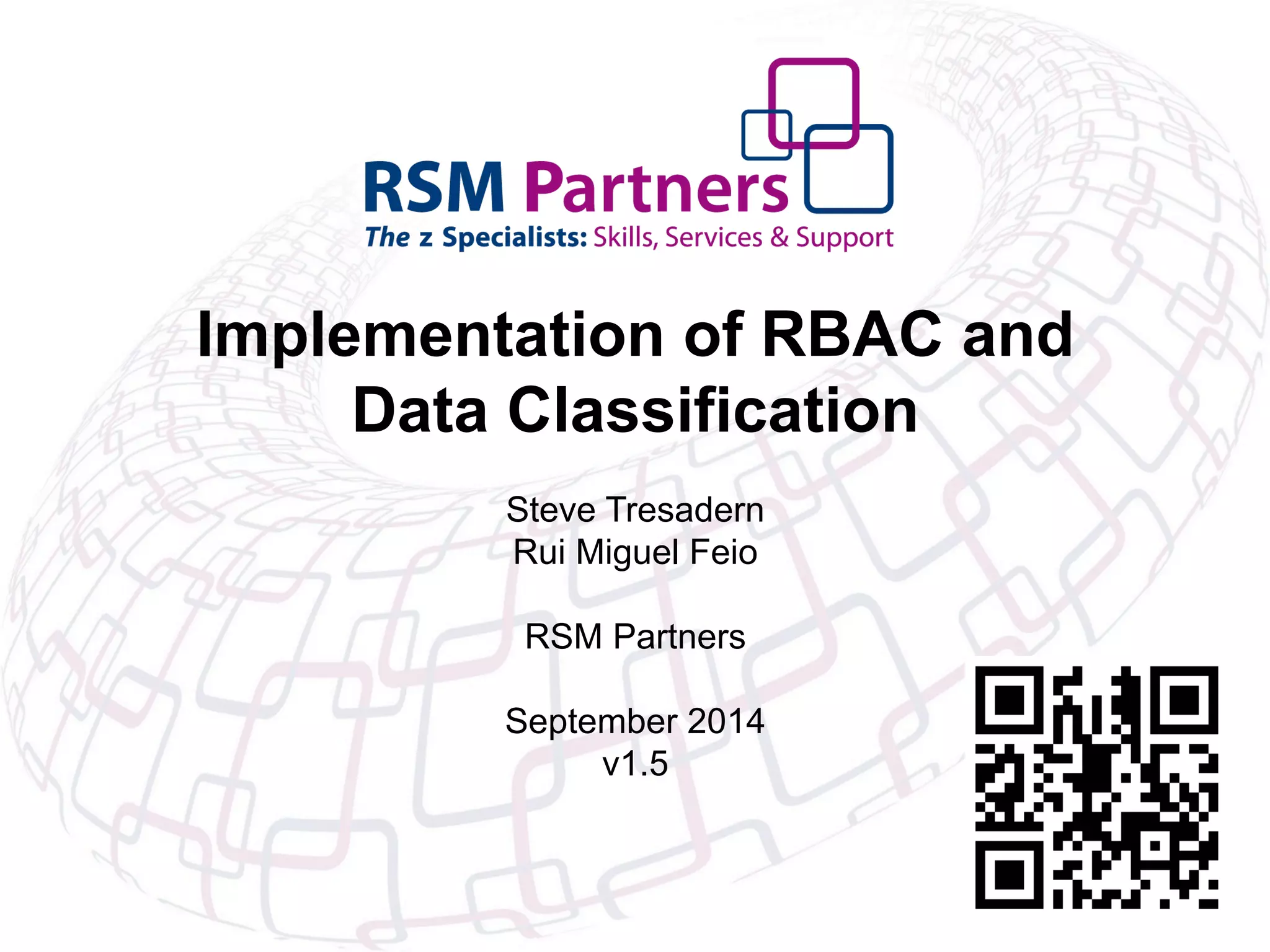
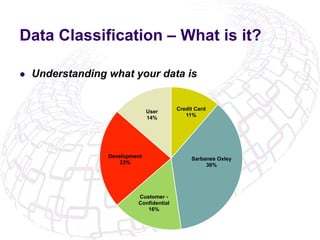
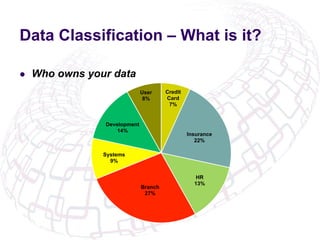
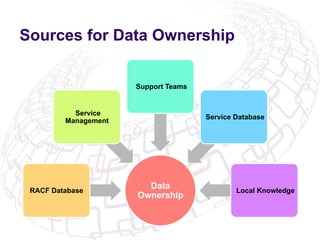
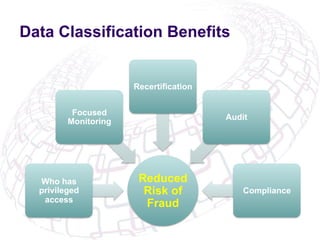
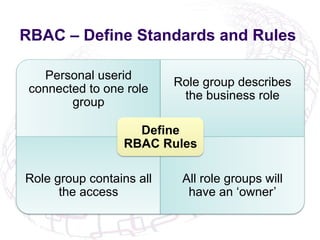
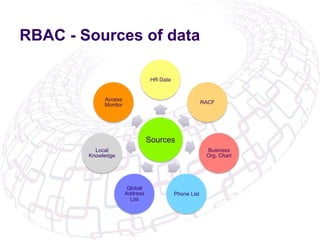
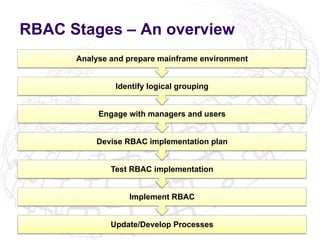
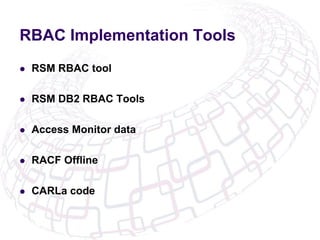
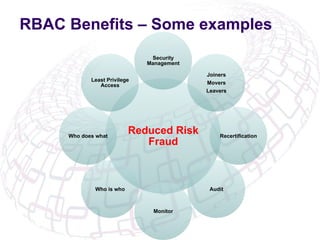
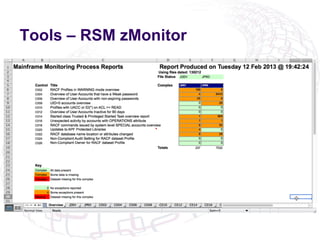
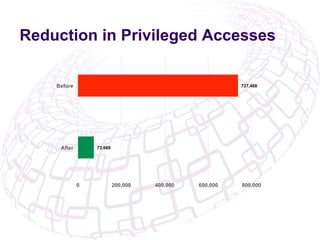
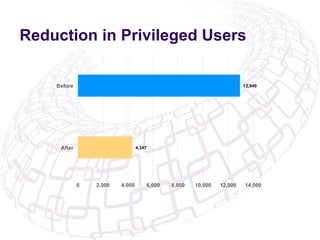
The document outlines the implementation of Role-Based Access Control (RBAC) and data classification strategies by RSM Partners, emphasizing the importance of data ownership and compliance. It highlights challenges and benefits associated with data classification and RBAC, including reduced fraud risk and improved security management. The report concludes with contact details for further inquiries.