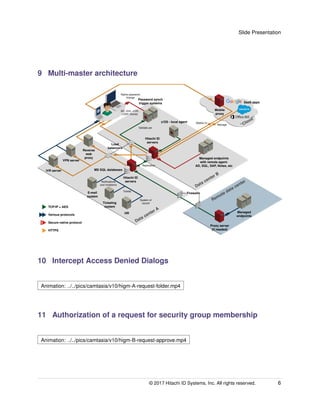
The document presents the Hitachi ID Group Manager, a tool for managing user lifecycle and security group memberships in both on-premises and cloud applications. It highlights the challenges posed by numerous security groups in medium to large AD environments and demonstrates how the tool facilitates self-service management for users, easing the administrative burden on IT. The solution aims to streamline access to network resources while allowing group owners to authorize member requests, enhancing overall security and efficiency.