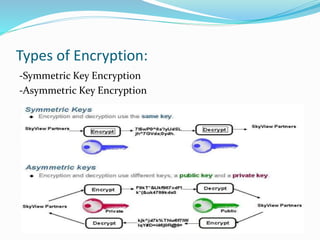
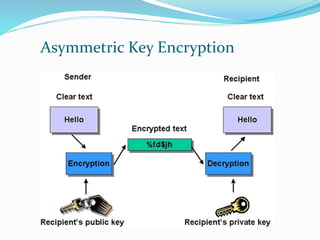
Encryption is the process of encoding messages or information so that only authorized parties can read it. There are two main types of encryption: symmetric key encryption which uses the same key to encrypt and decrypt, and asymmetric key encryption which uses a public key to encrypt and a private key to decrypt. While symmetric encryption is faster, asymmetric encryption is more secure since it does not require sharing the same key. Encryption is widely used to provide authentication, privacy, integrity, and accountability of data.