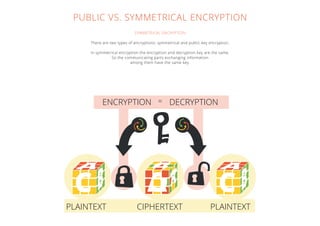
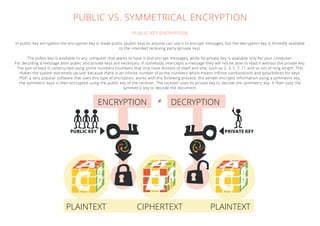
Encryption is a process of encoding information in a way that only authorized parties can read it. It was first used over 2000 years ago by Julius Caesar and ancient Greeks to hide military communications. There are two main types of encryption - symmetric encryption which uses the same key to encrypt and decrypt, and public-key encryption which uses a public key to encrypt and a private key to decrypt. Encryption is now widely used to protect data on computers and transmitted over networks by individuals, companies and governments.