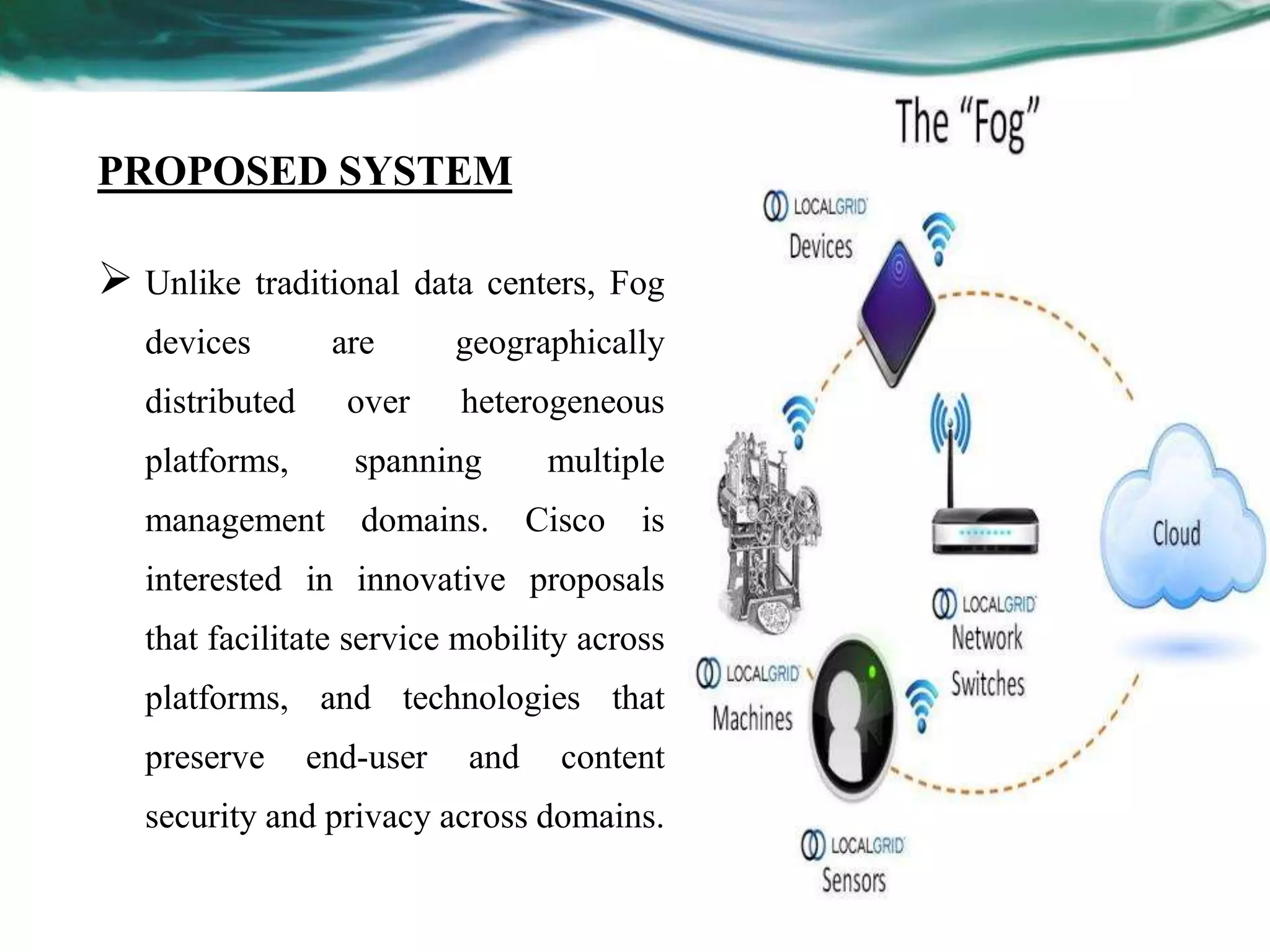
Fog computing extends cloud services to the network edge, providing data, compute, and application services closer to end-users, enhancing applications like smart grids and IoT. It addresses existing cloud computing limitations, such as security vulnerabilities and lack of user authorization verification, by introducing geographically distributed fog devices. The document discusses security and privacy challenges, including authentication issues and attacks like man-in-the-middle, while proposing future enhancements to improve fog computing capabilities.















![REFERENCES :
[1] F. Bonomi, “Connected vehicles, the internet of things, and fog com-
puting,” in The Eighth ACM International Workshop on Vehicular Inter-
Networking (VANET), Las Vegas, USA, 2011.
[2] F. Bonomi, R. Milito, J. Zhu, and S. Addepalli, “Fog computing and its
role in the internet of things,” in Proceedings of the First Edition of the MCC
Workshop on Mobile Cloud Computing, ser. MCC’12. ACM,2012, pp. 13–16.](https://image.slidesharecdn.com/semniar-150403021635-conversion-gate01/75/FOG-COMPUTING-17-2048.jpg)
