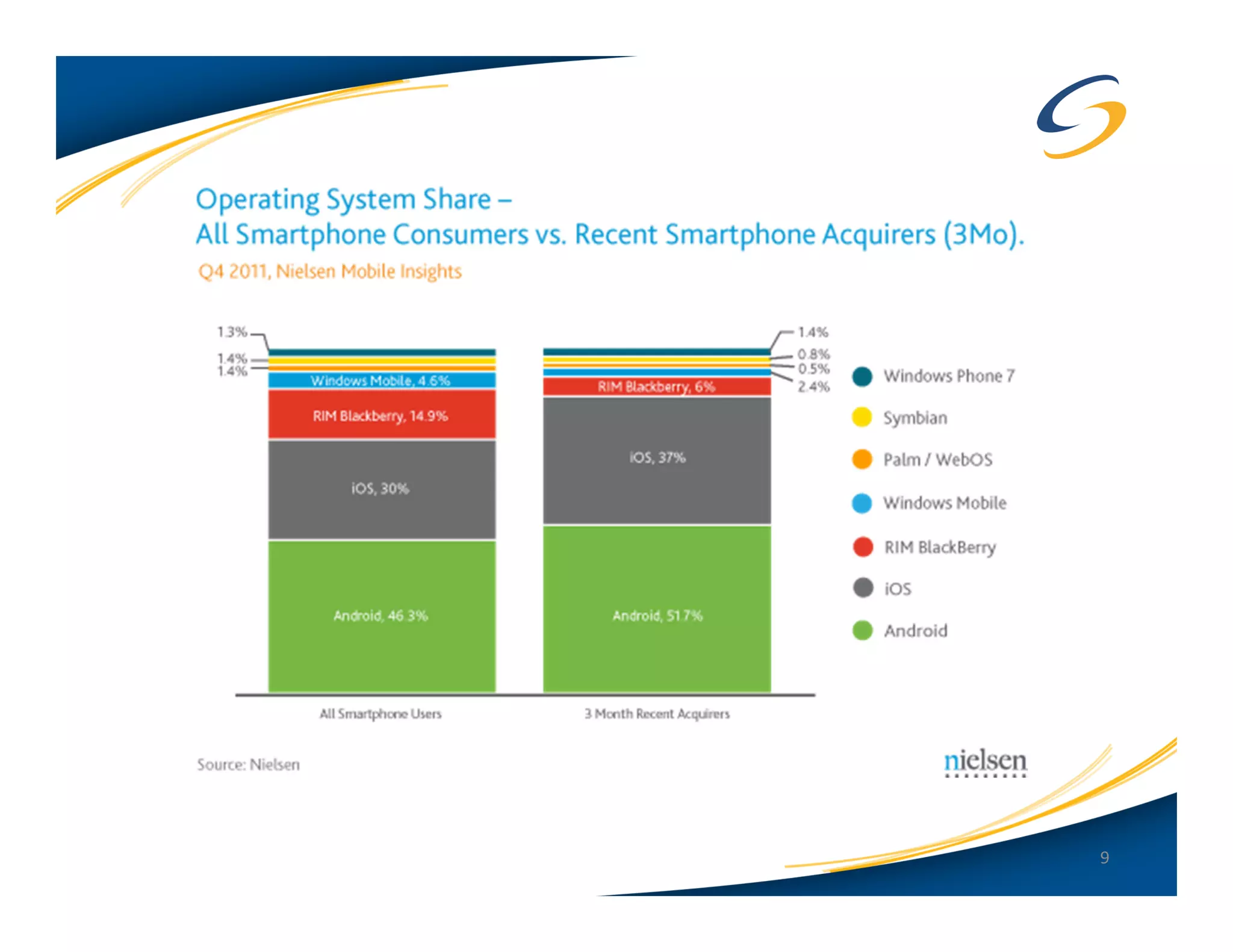
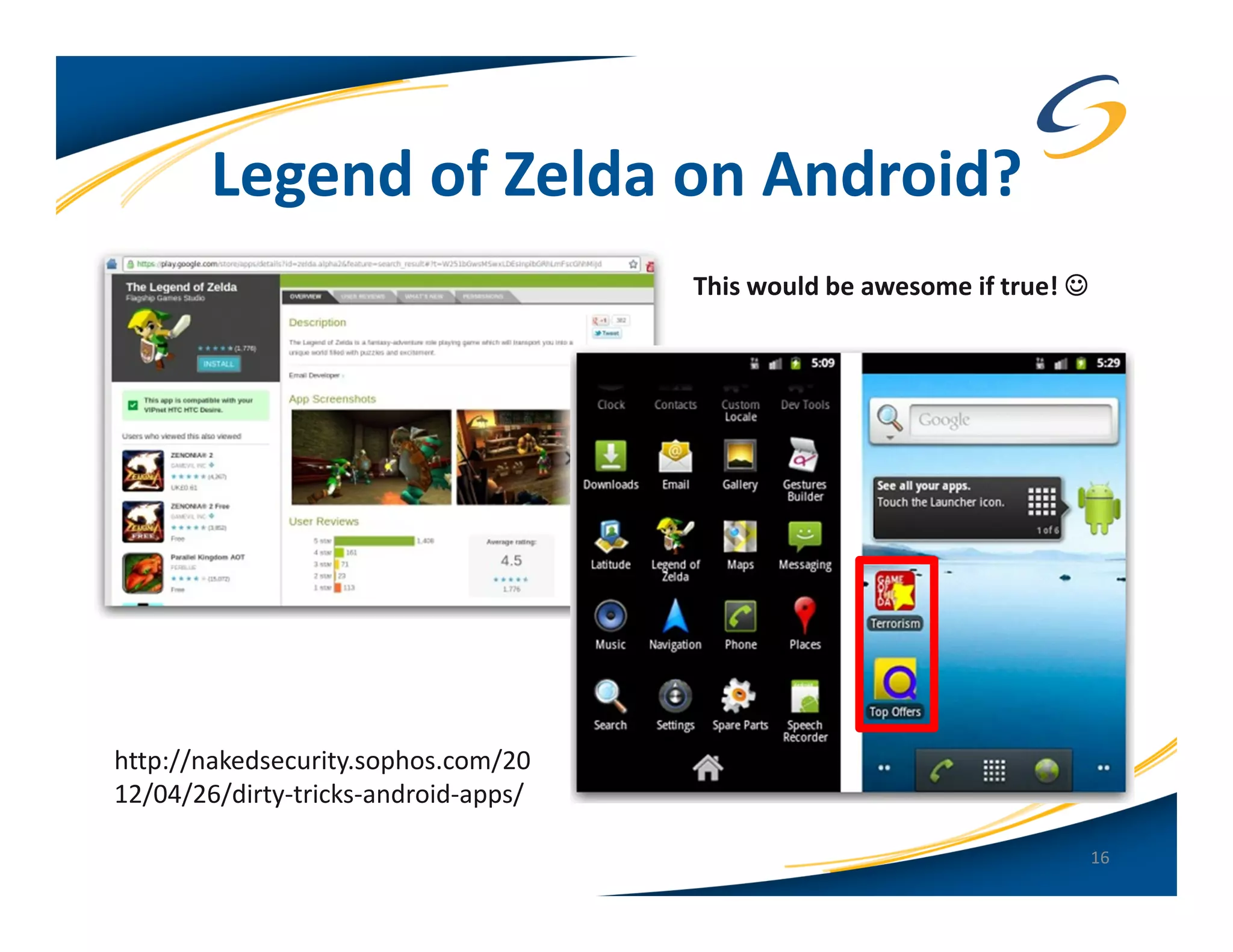
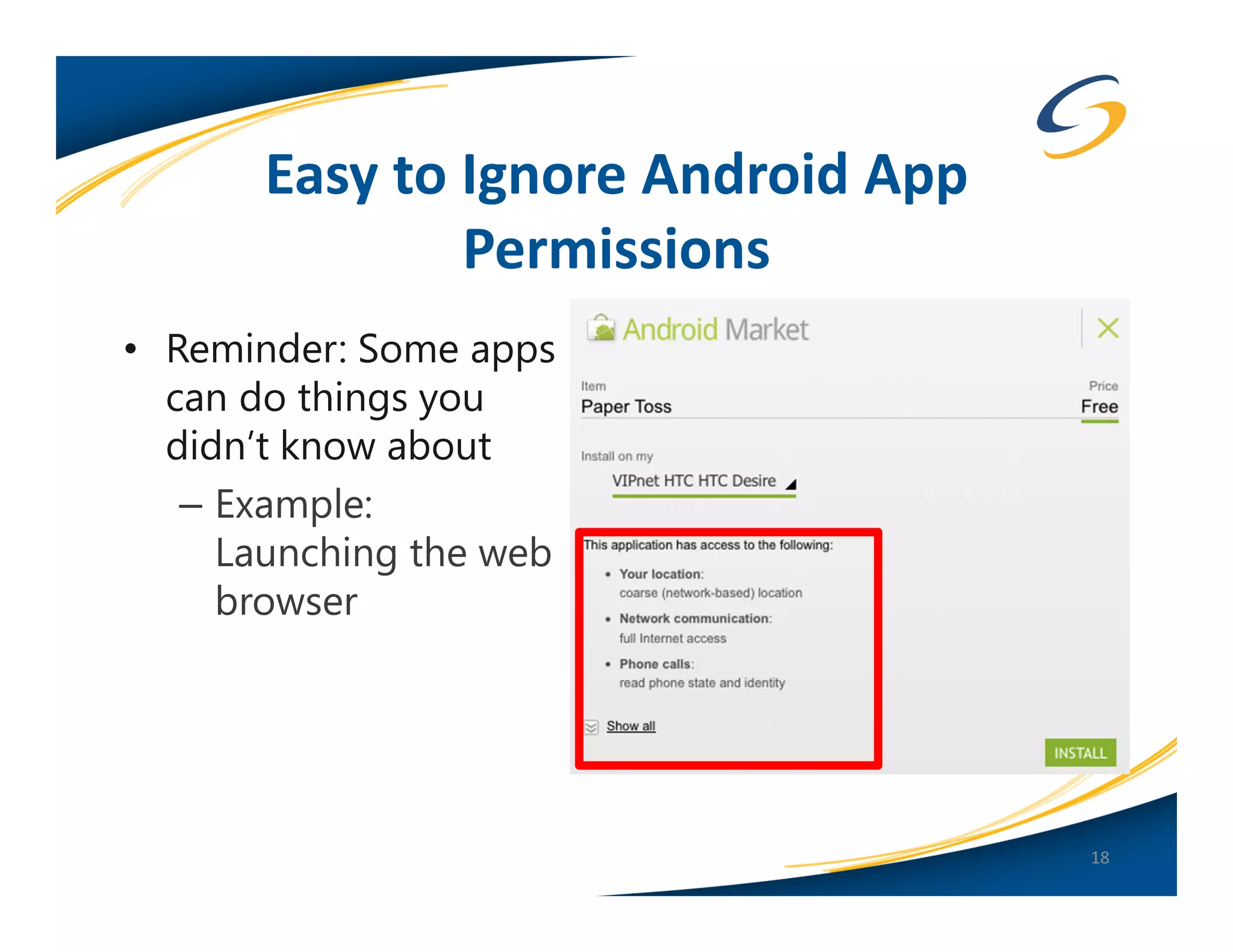
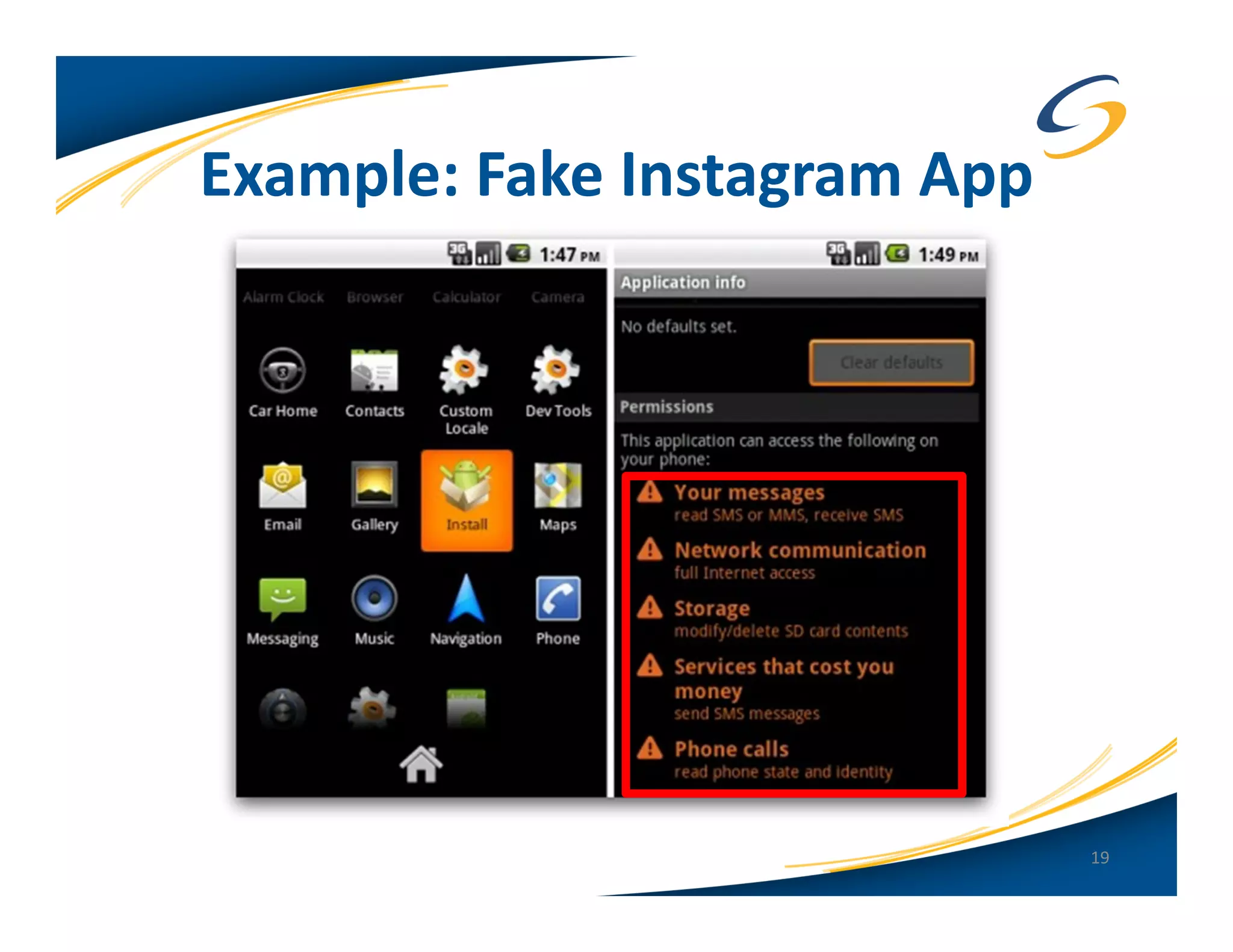
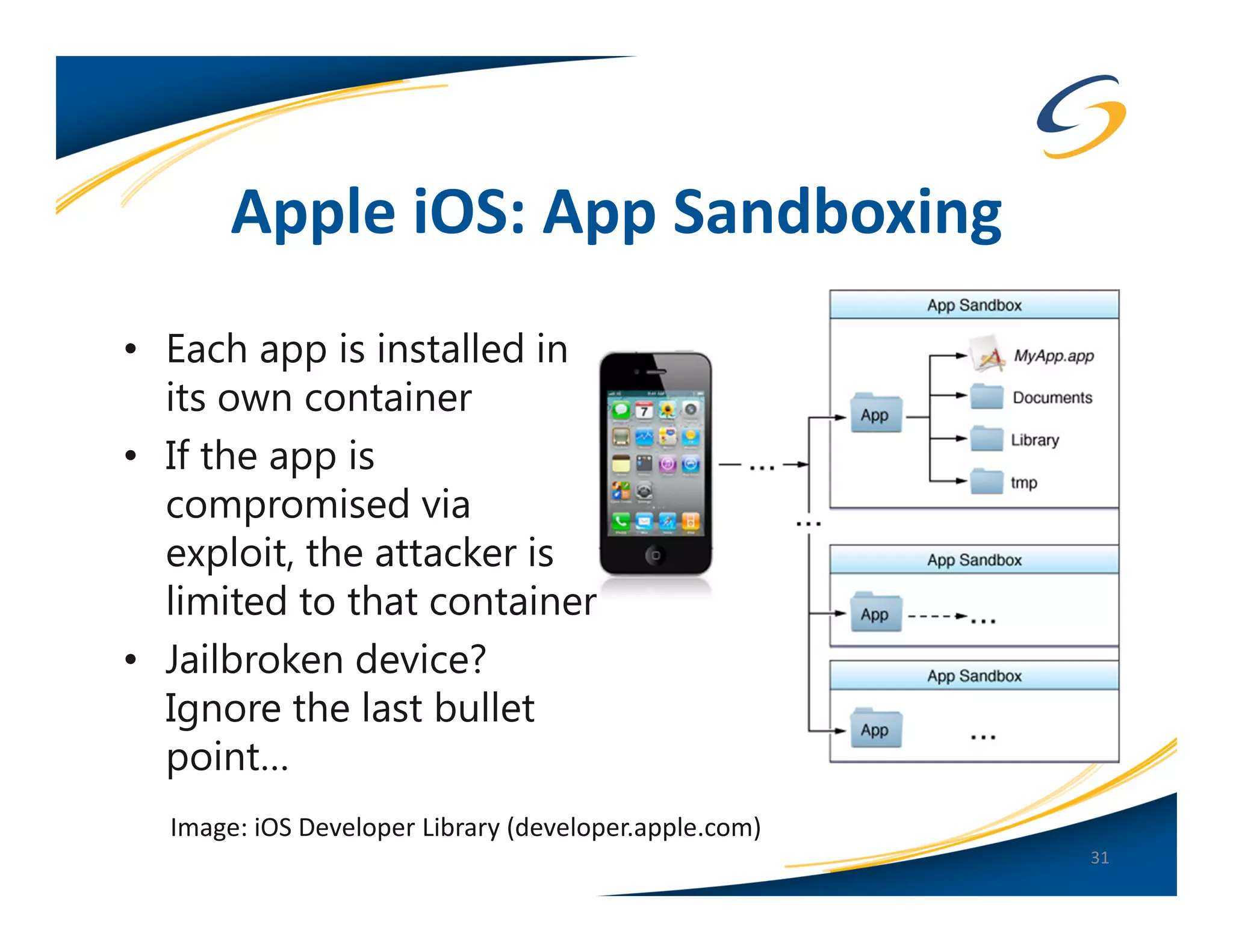
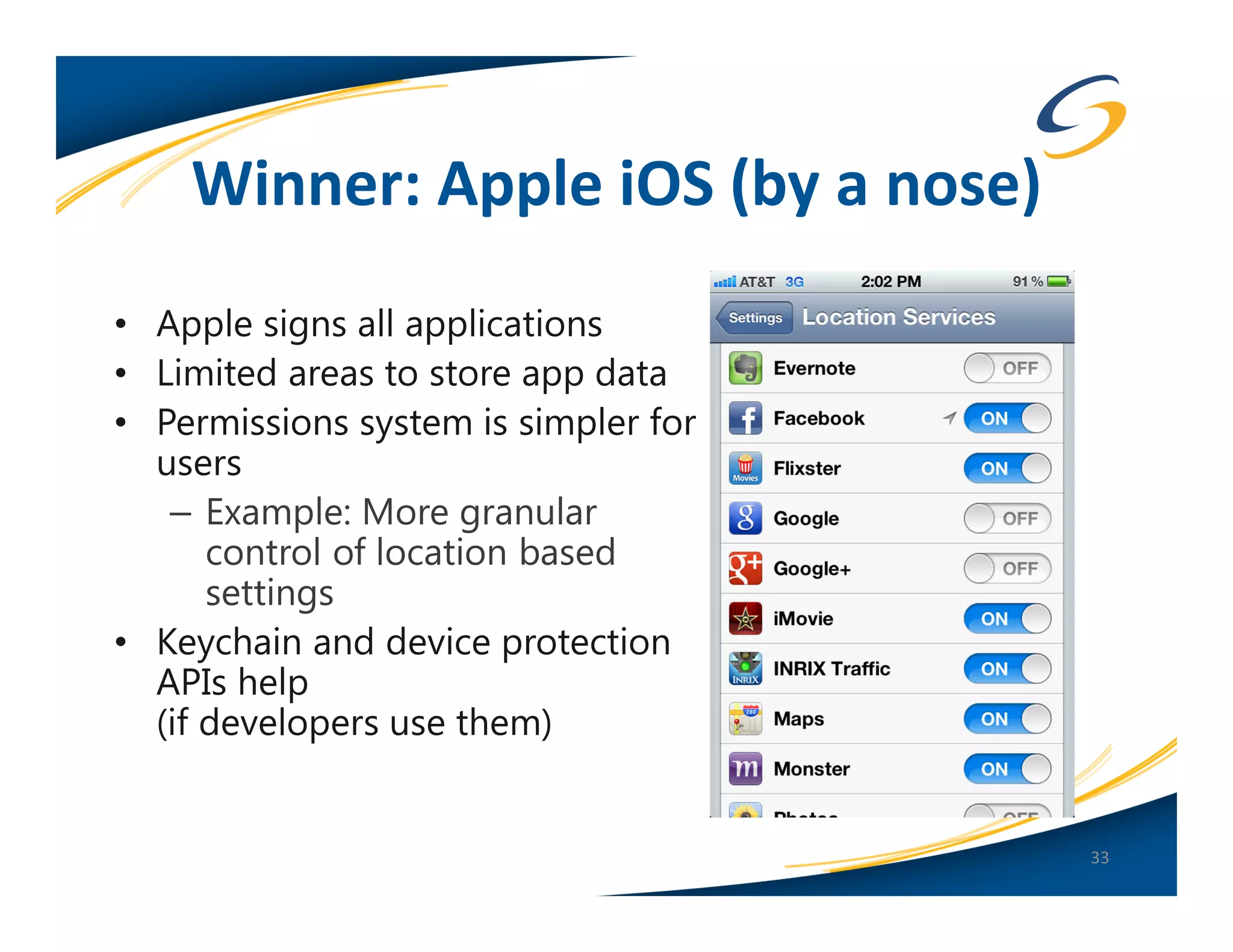
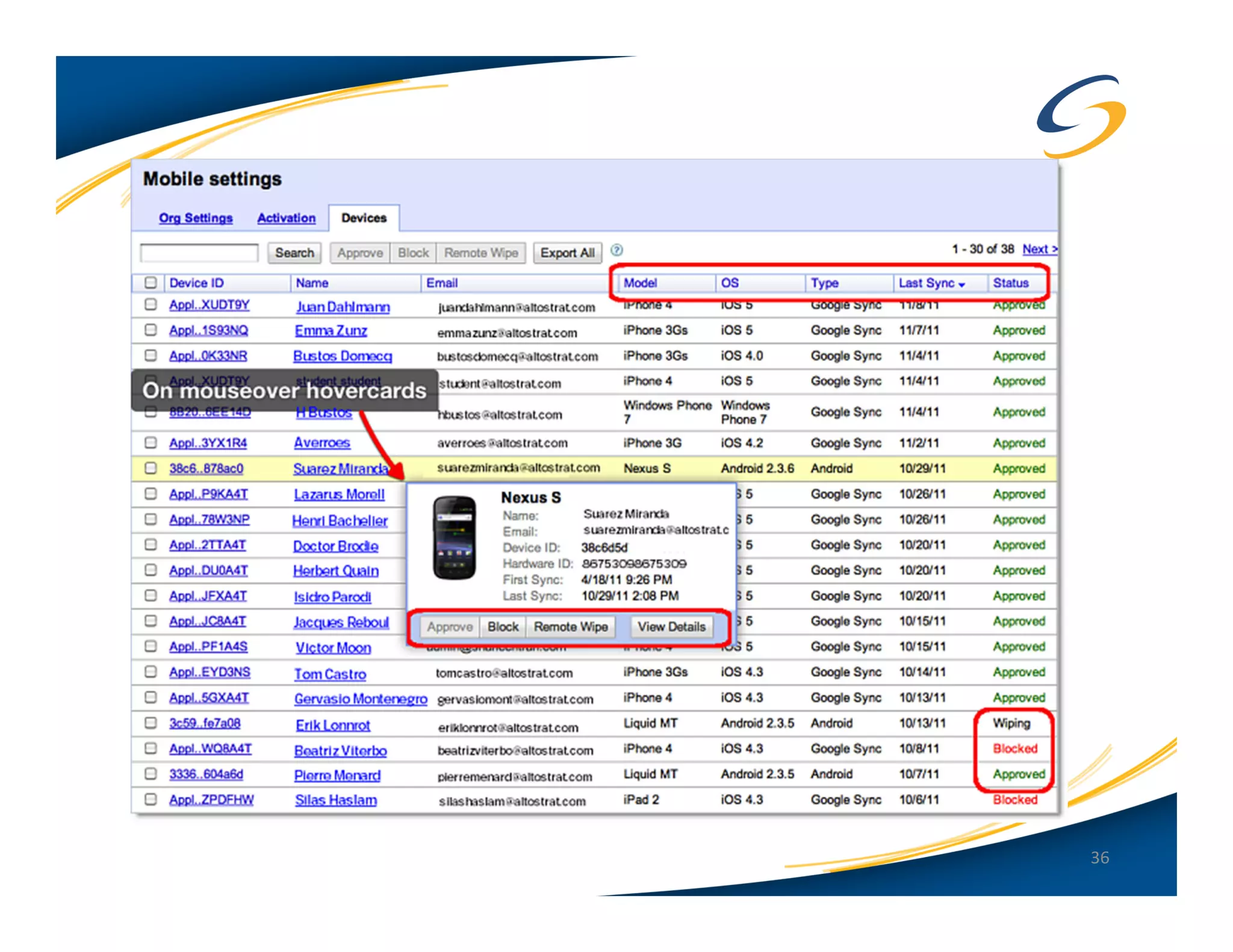
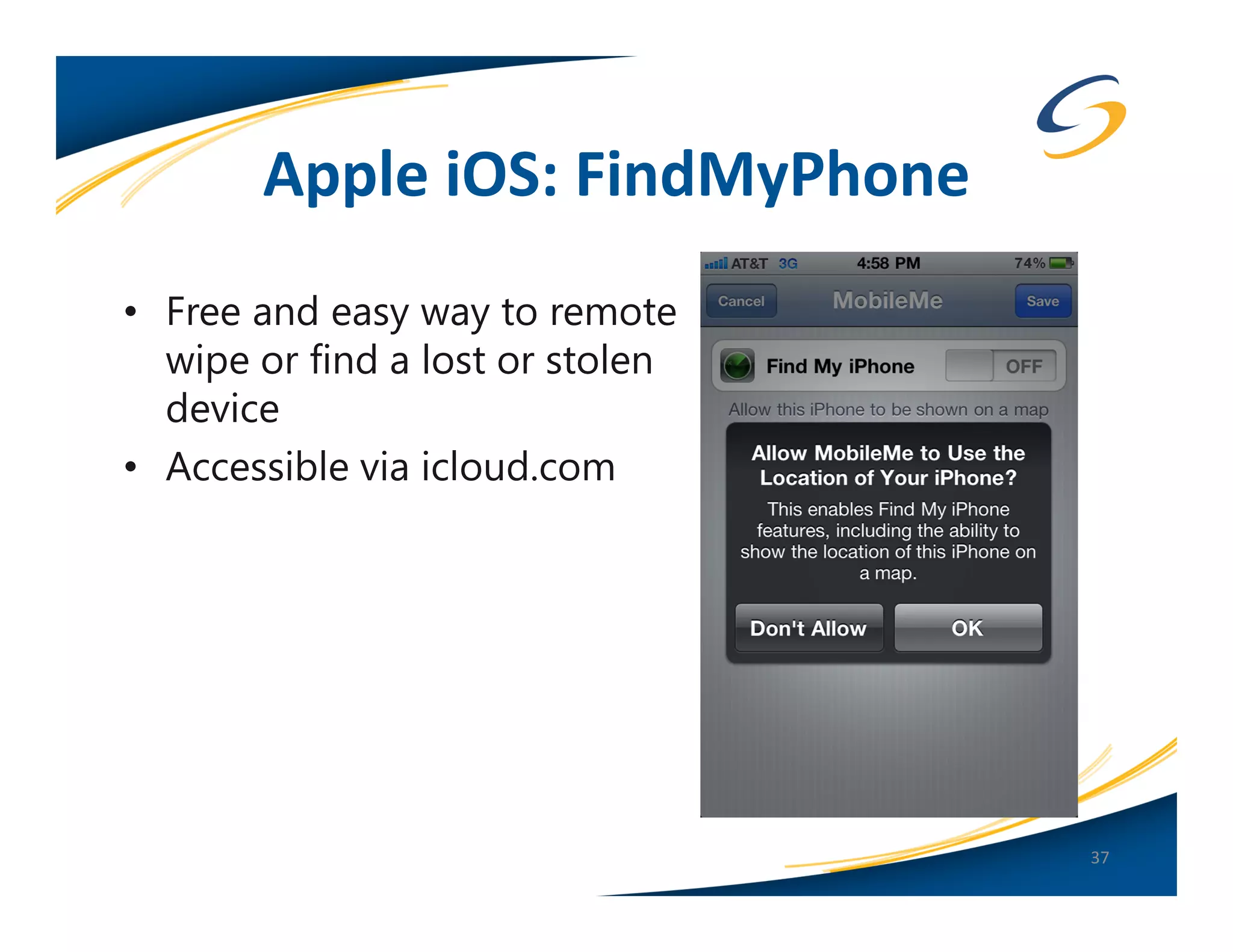
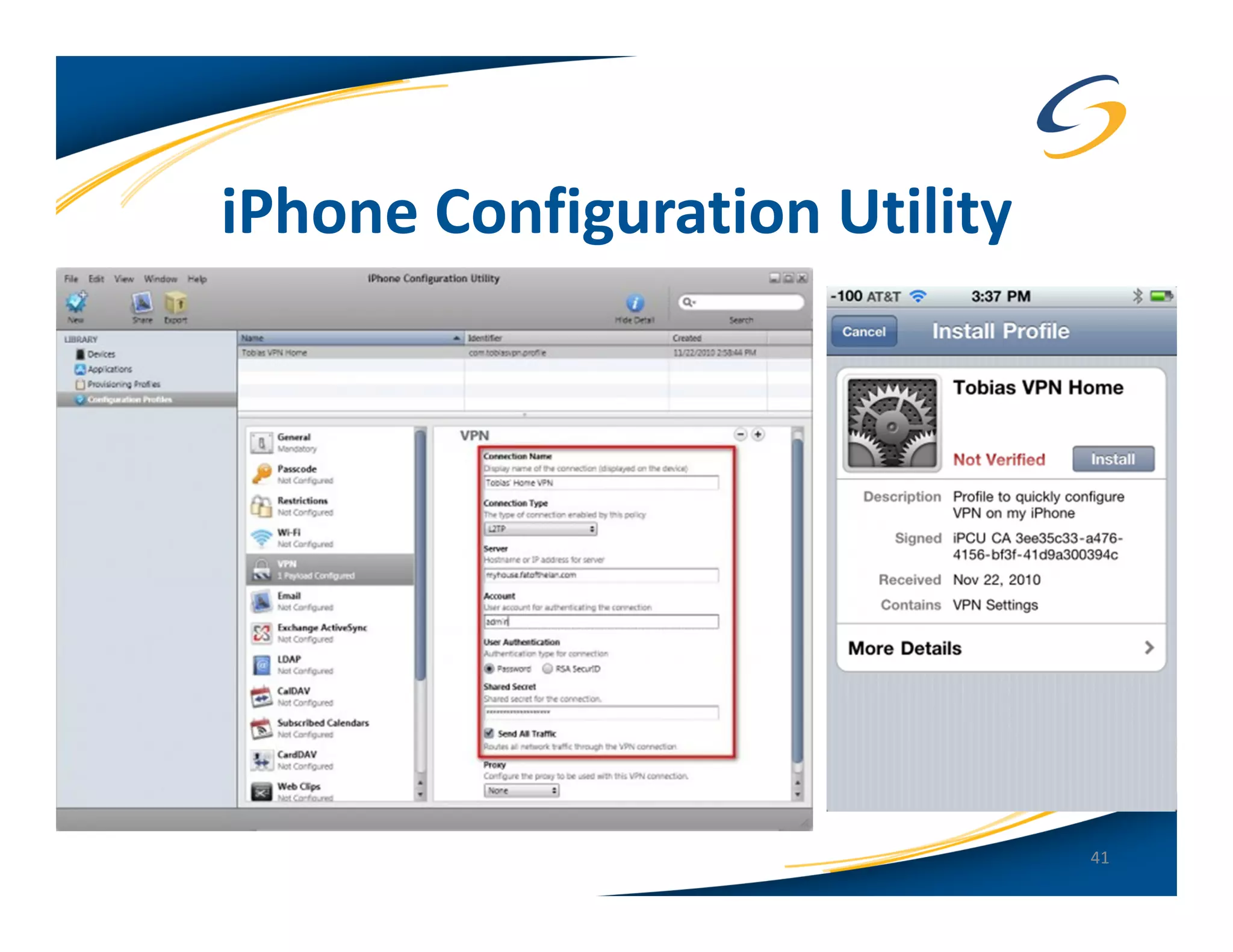
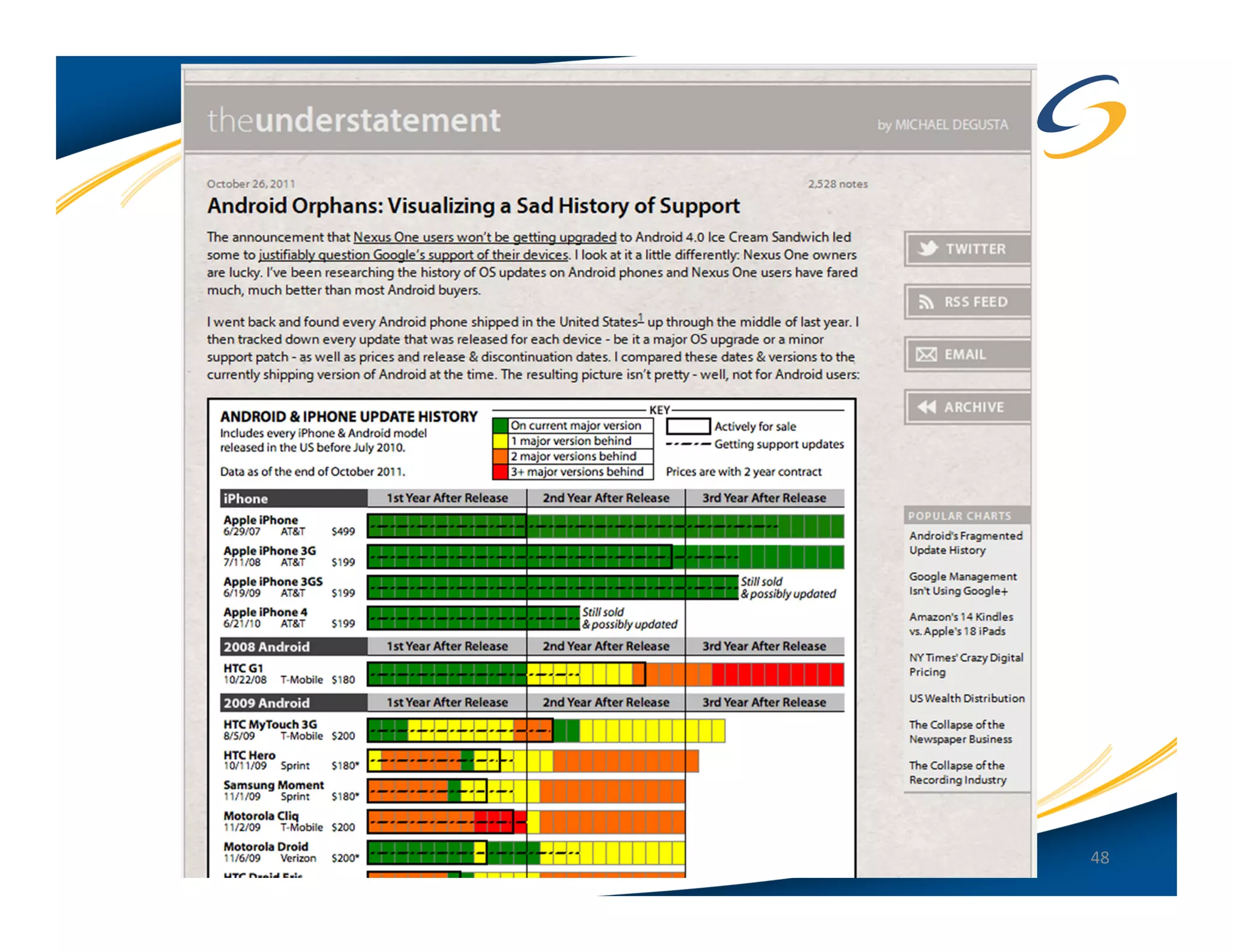
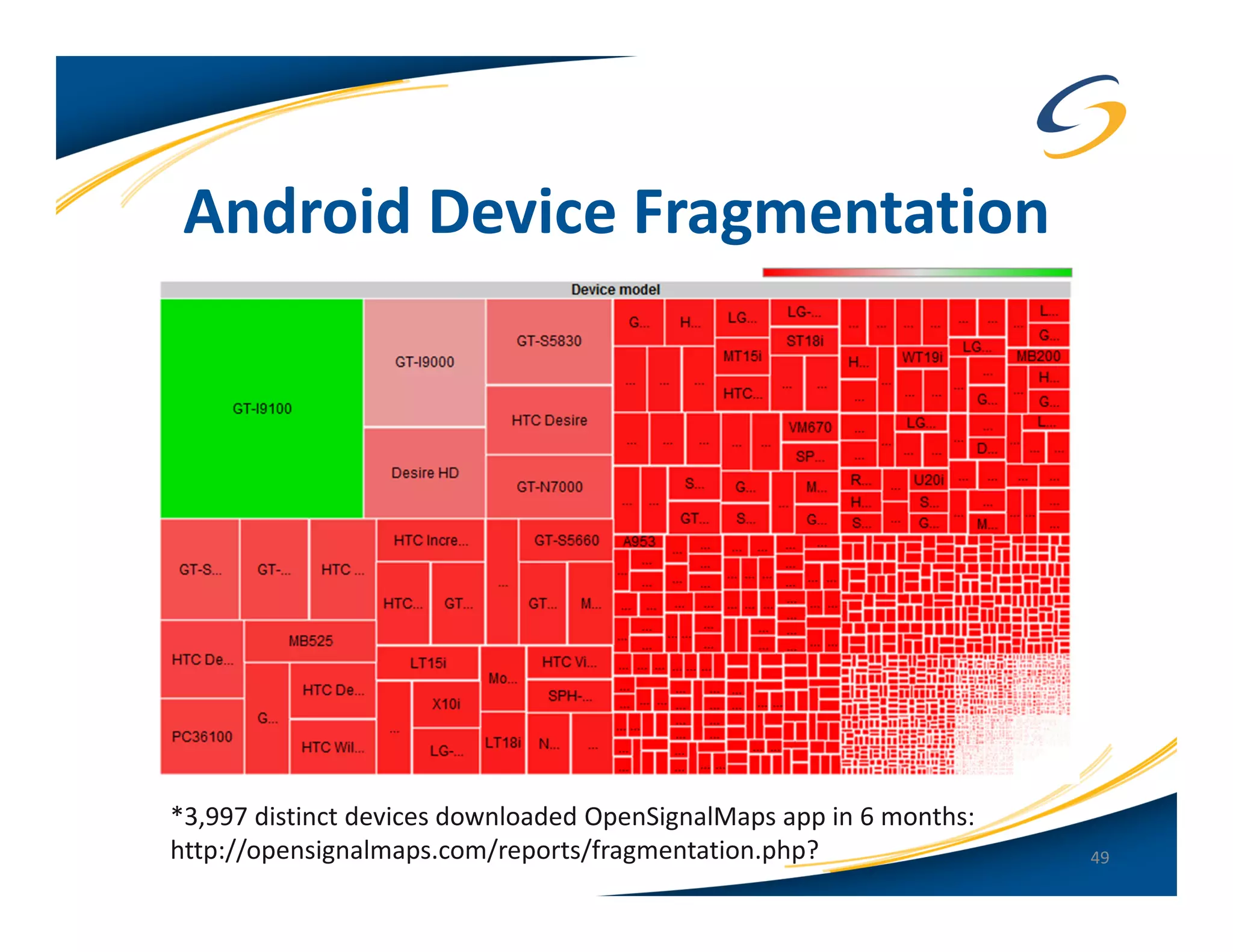
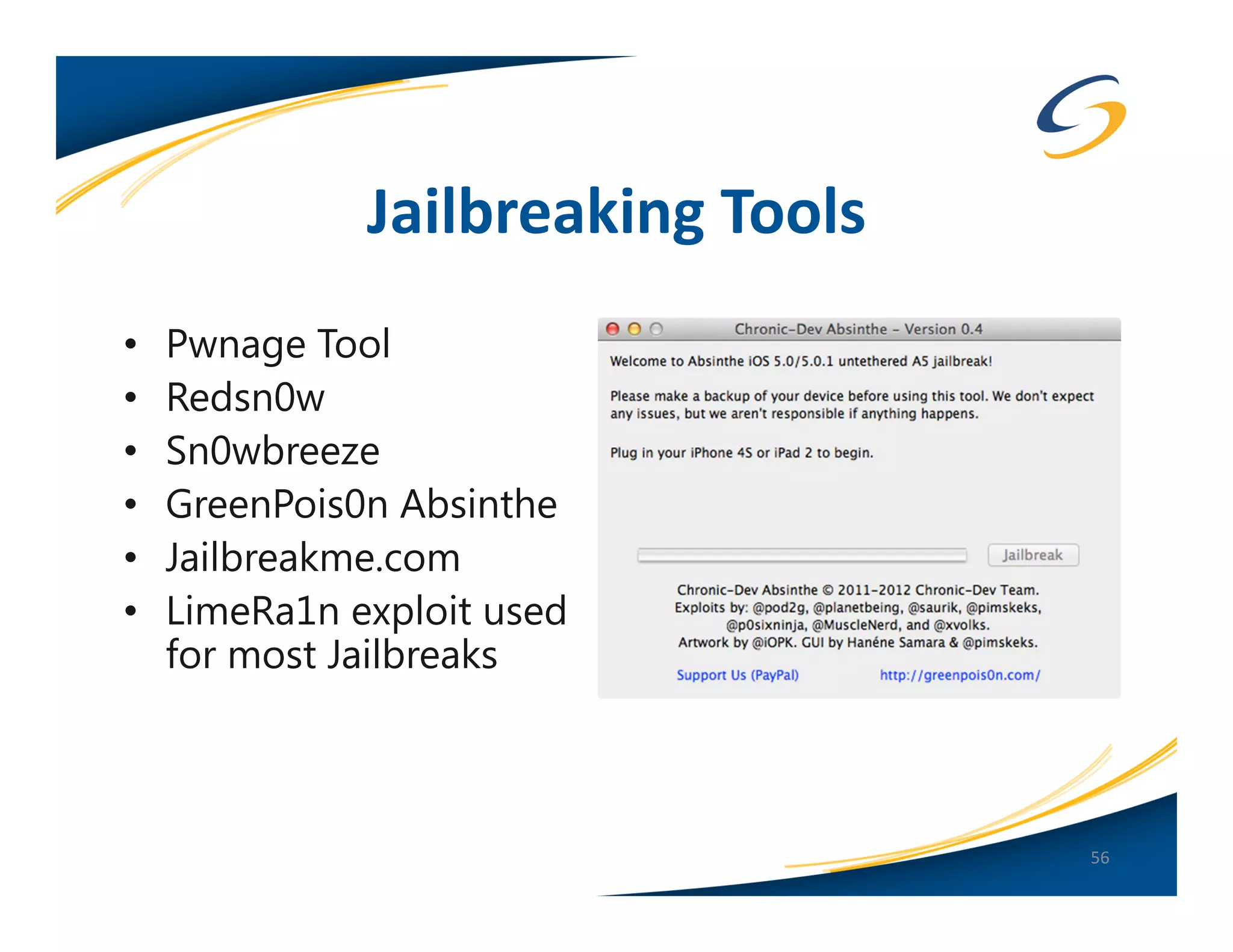
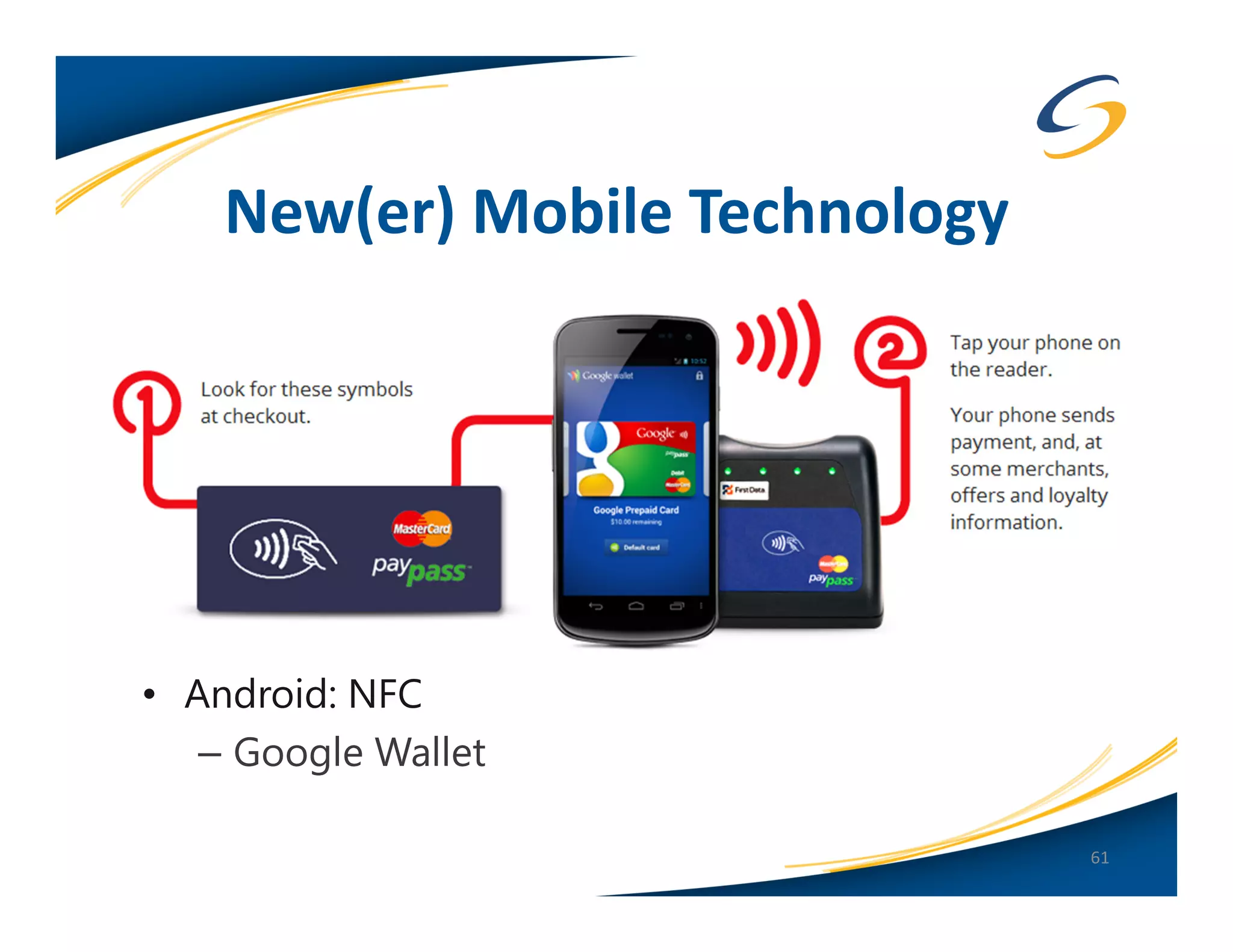
The document presents a comprehensive comparison between Android and Apple iOS security, highlighting key statistics, current versions, and security concerns. It discusses the effectiveness of app stores, malware prevalence, remote wipe capabilities, encryption practices, and the implications of device jailbreaking and rooting. Overall, it concludes that Apple iOS currently offers better security measures than Android, though both platforms face unique challenges.