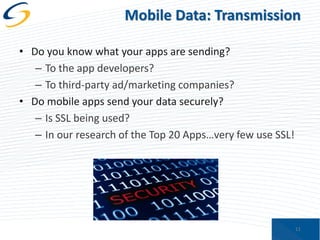
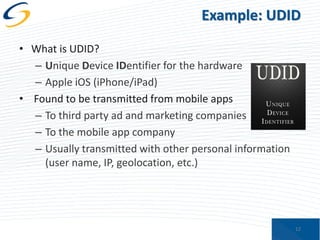
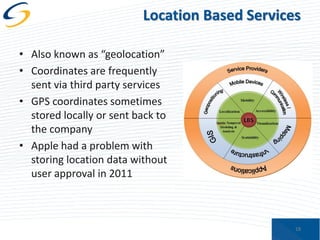
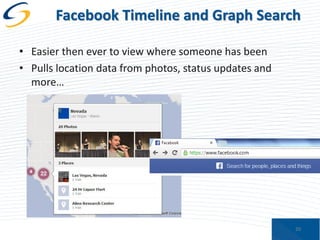
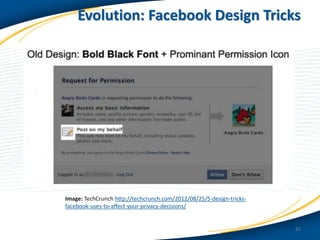
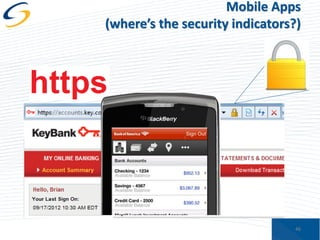
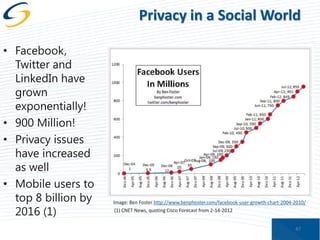
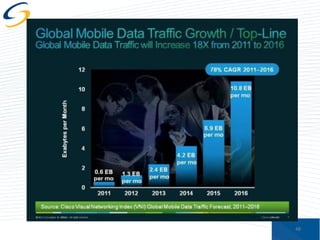
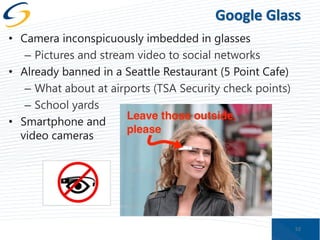
The document discusses the implications of privacy in the context of social media and mobile technology, highlighting issues such as data harvesting, location tracking, and the confusion surrounding app privacy policies. It emphasizes the need for both consumers and businesses to take personal responsibility in managing privacy and security, while also noting the challenges related to regulatory frameworks. The presenters advocate for a new paradigm where consumers actively read and understand privacy policies, and businesses implement better data protection practices.




































![Tom Eston: teston@securestate.com
Twitter: @agent0x0
Brian Dean: bdean@securestate.com
[Mostly off the grid
]
61](https://image.slidesharecdn.com/privacyexposed-dean-eston-msi-mobilesecurityconference-131213143503-phpapp01/85/Privacy-Exposed-Ramifications-of-Social-Media-and-Mobile-Technology-61-320.jpg)