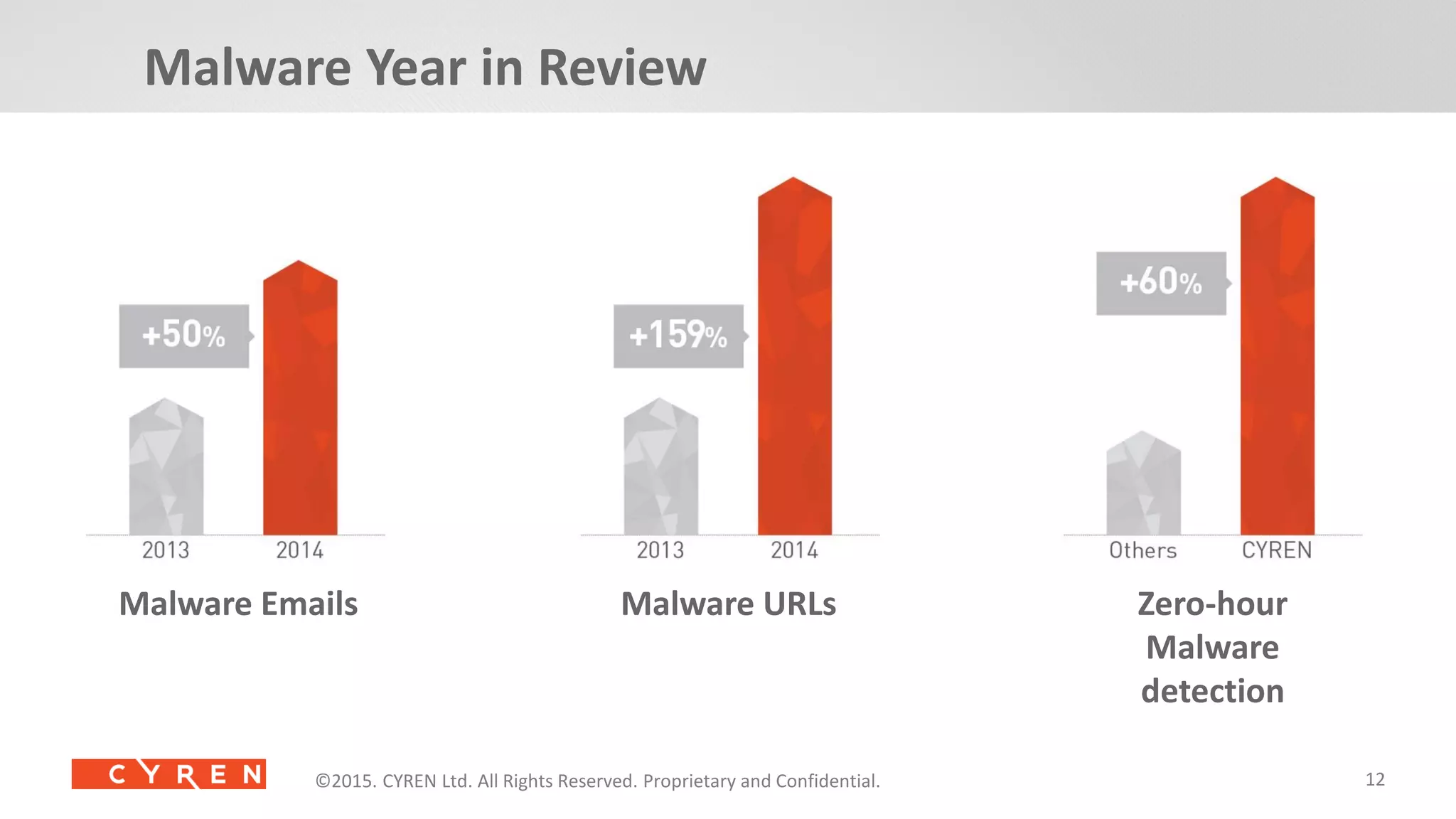
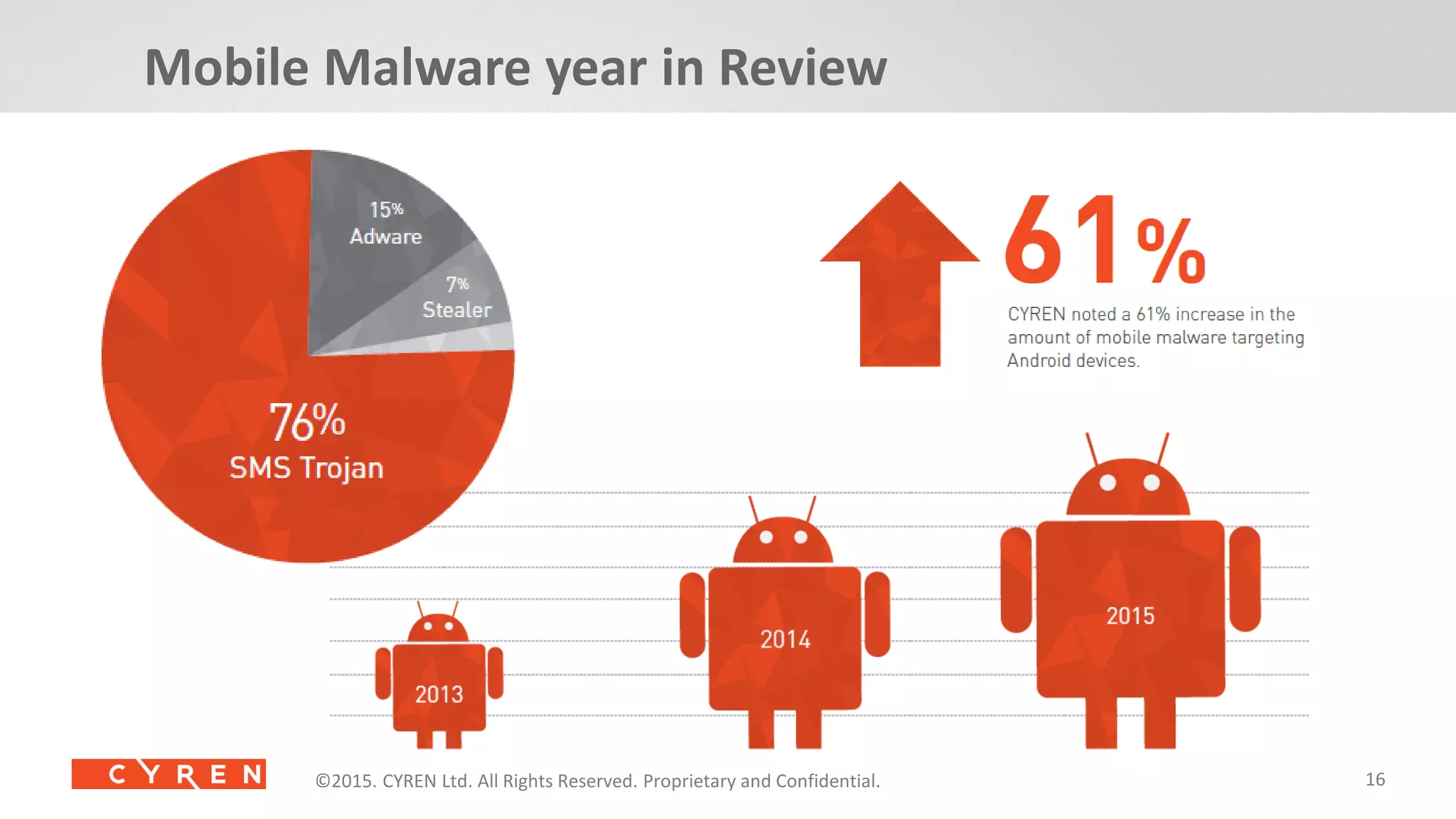
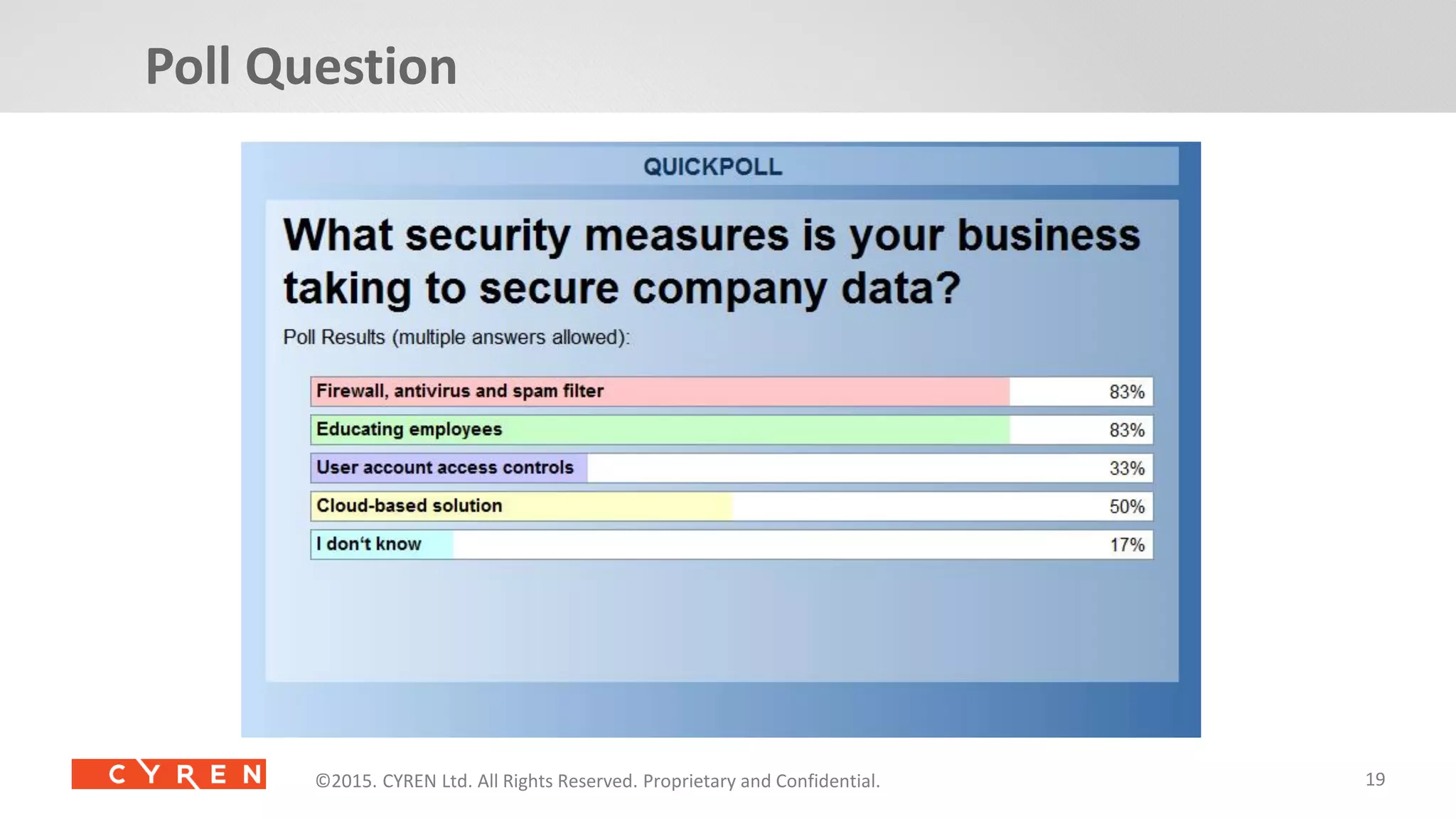
The document presents an overview of cybersecurity threats and trends in 2014, highlighting significant increases in cyberattacks and the evolving tactics of cybercriminals. It emphasizes the importance of utilizing cyber intelligence and advanced security solutions to protect enterprises from various threats, including malware, phishing, and mobile vulnerabilities. Additionally, it discusses the growing connections of industrial IoT devices and the potential consequences for security in 2015 and beyond.