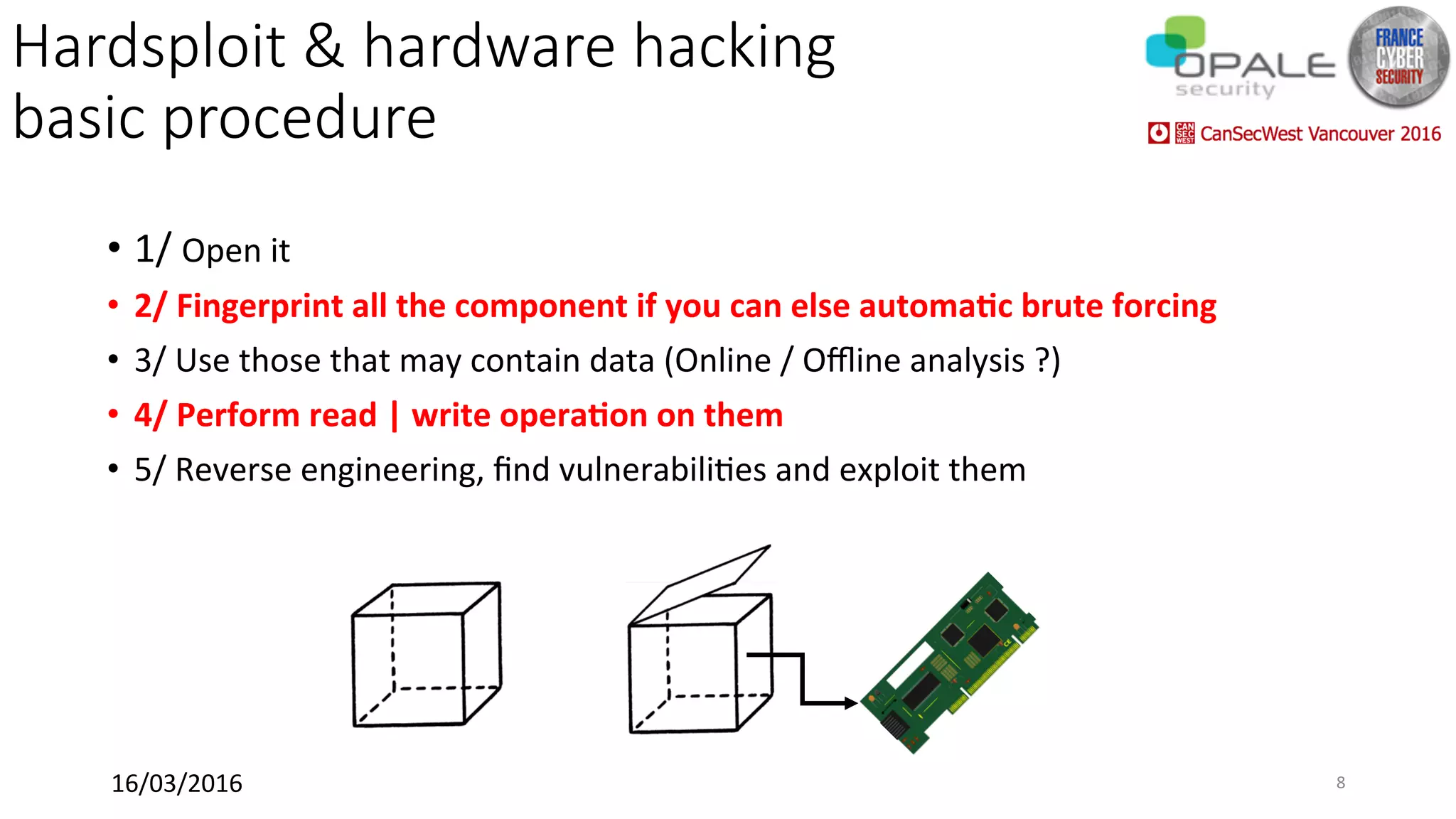
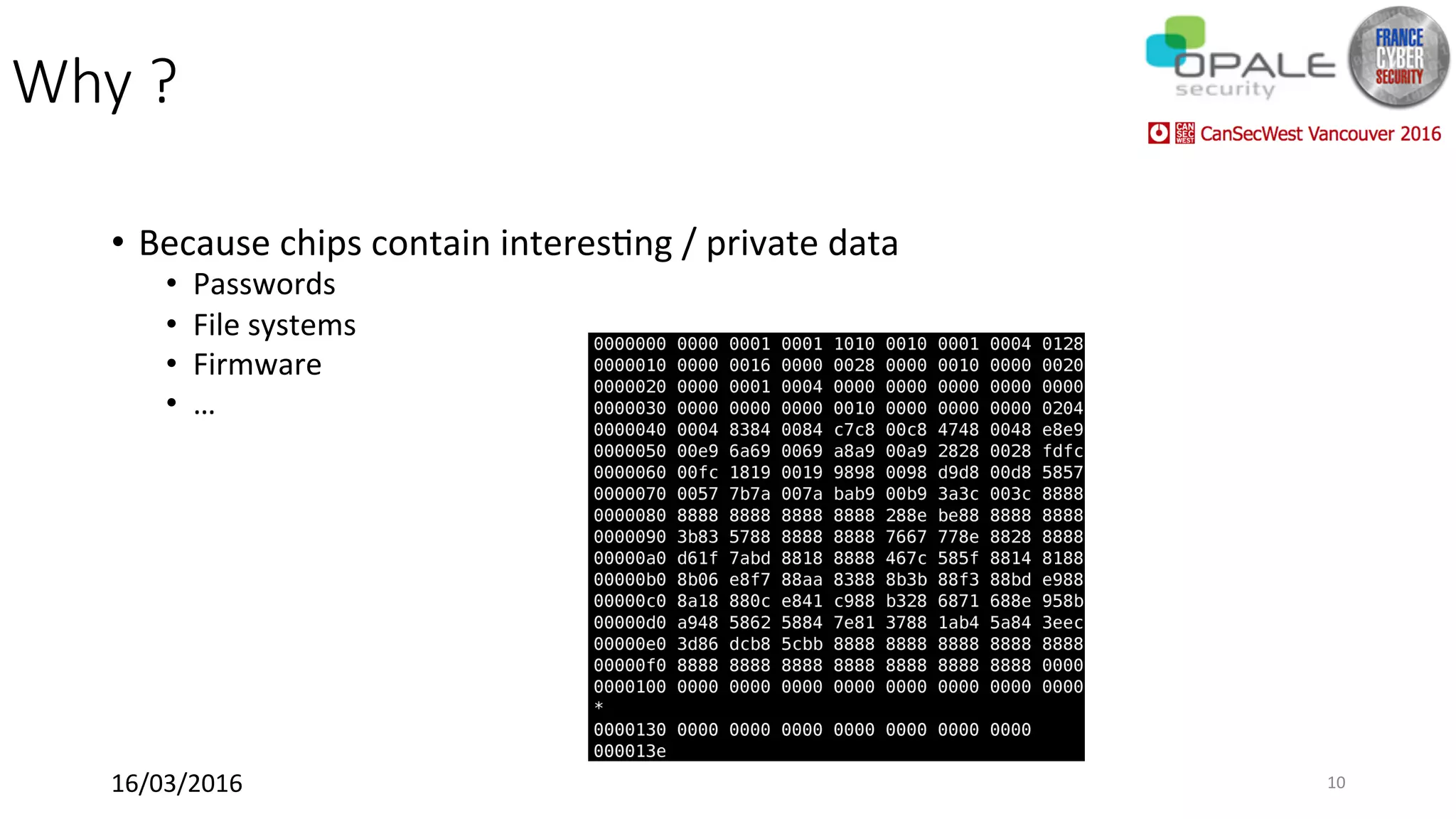
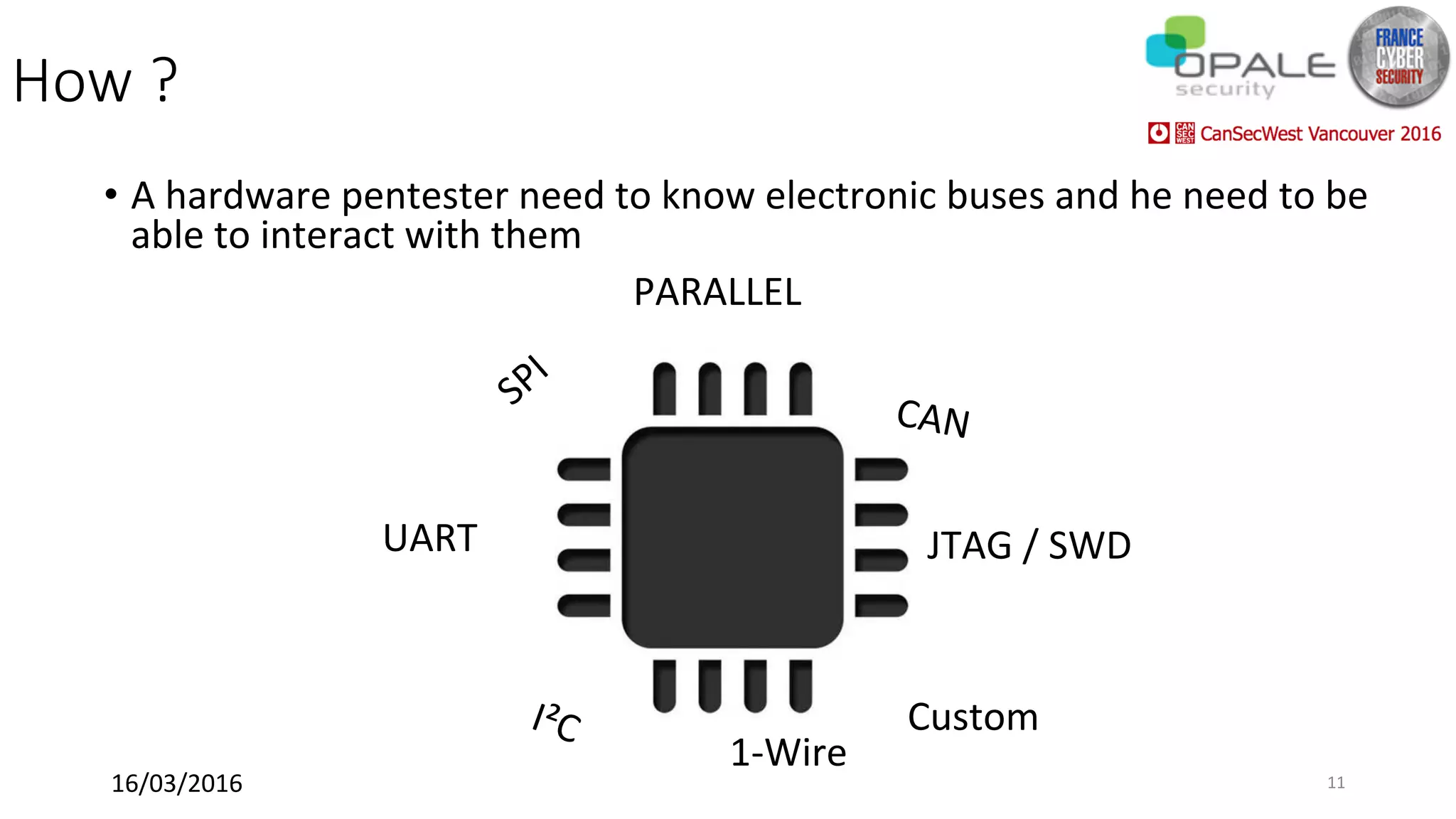
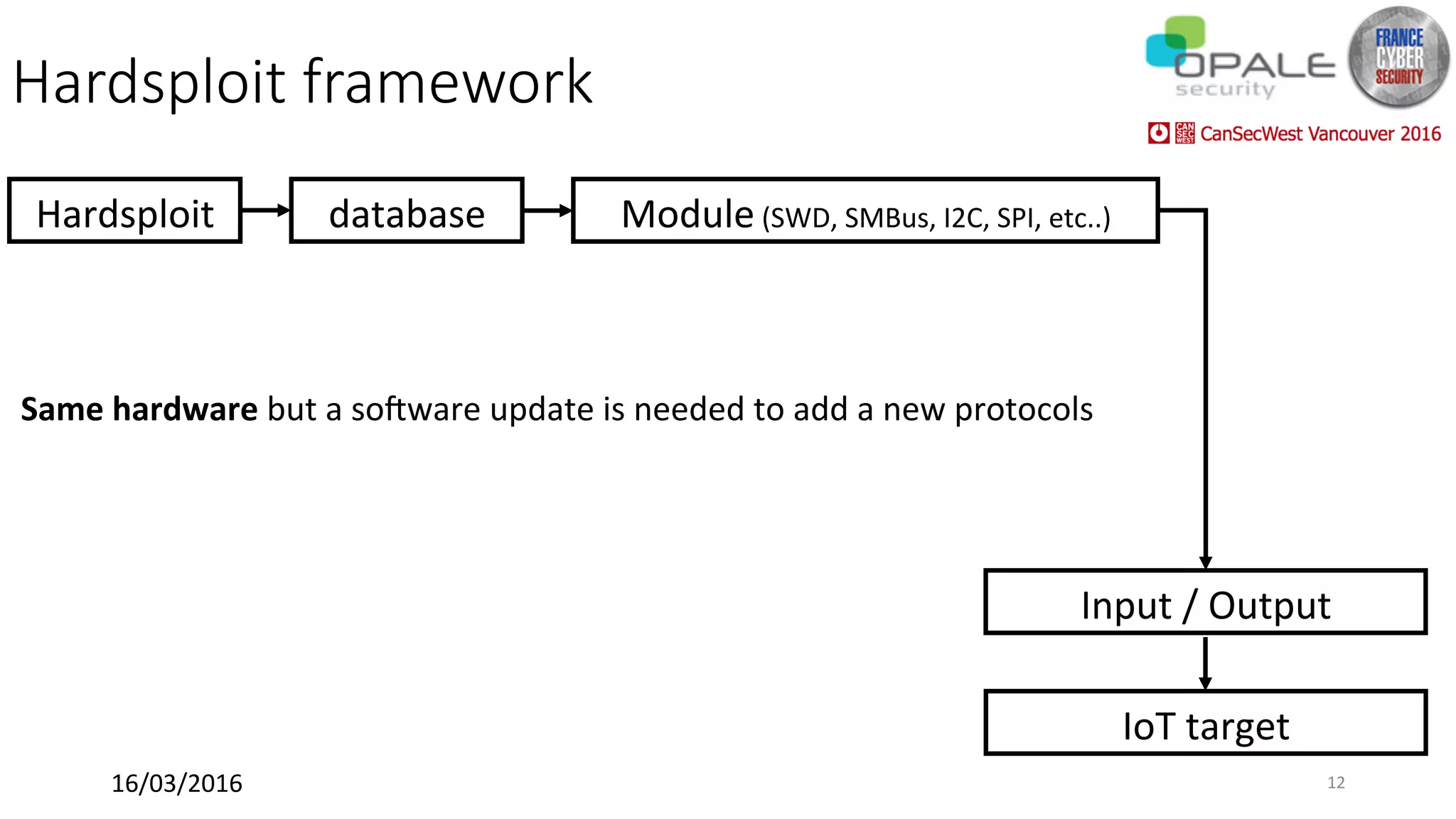
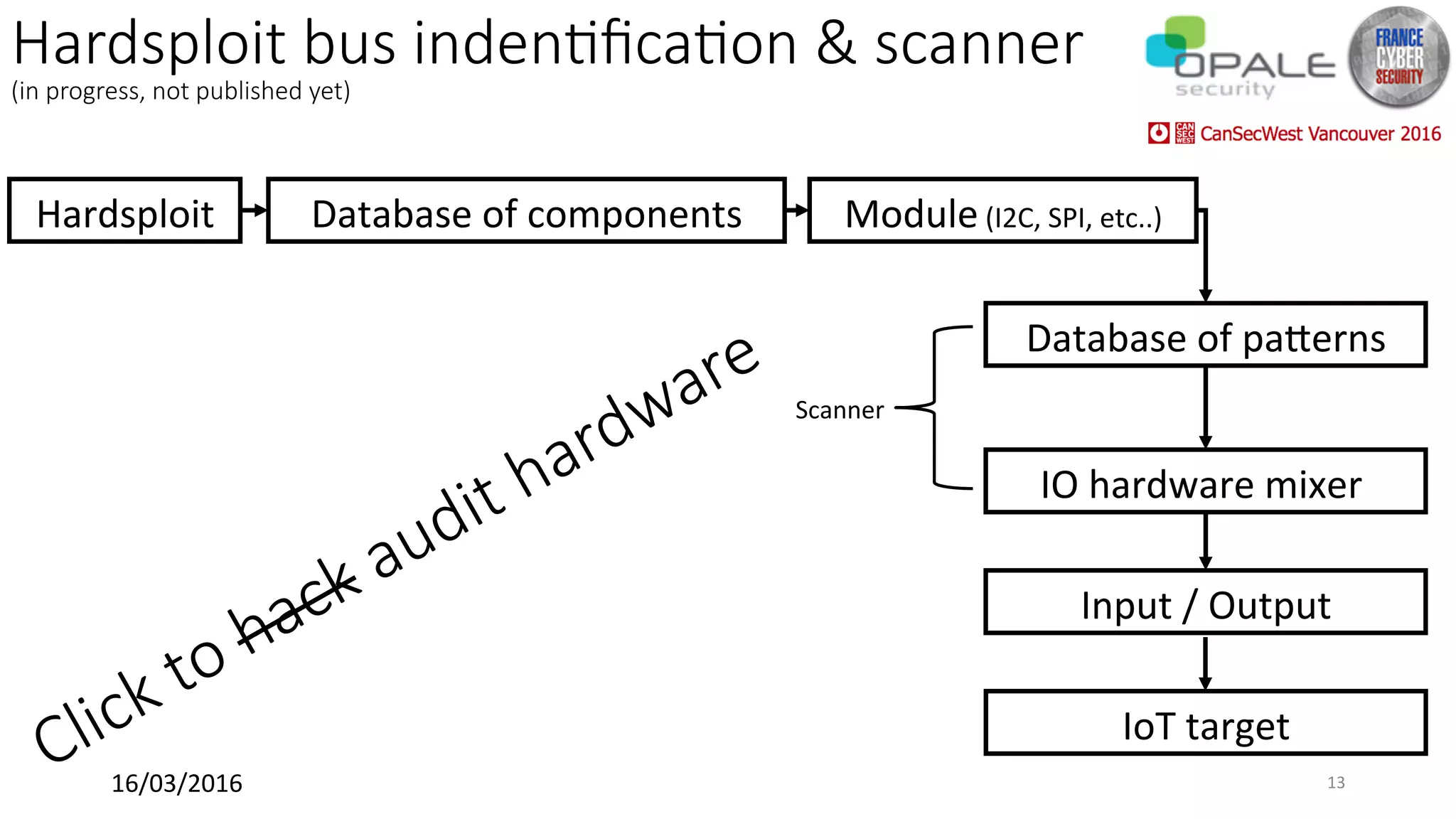
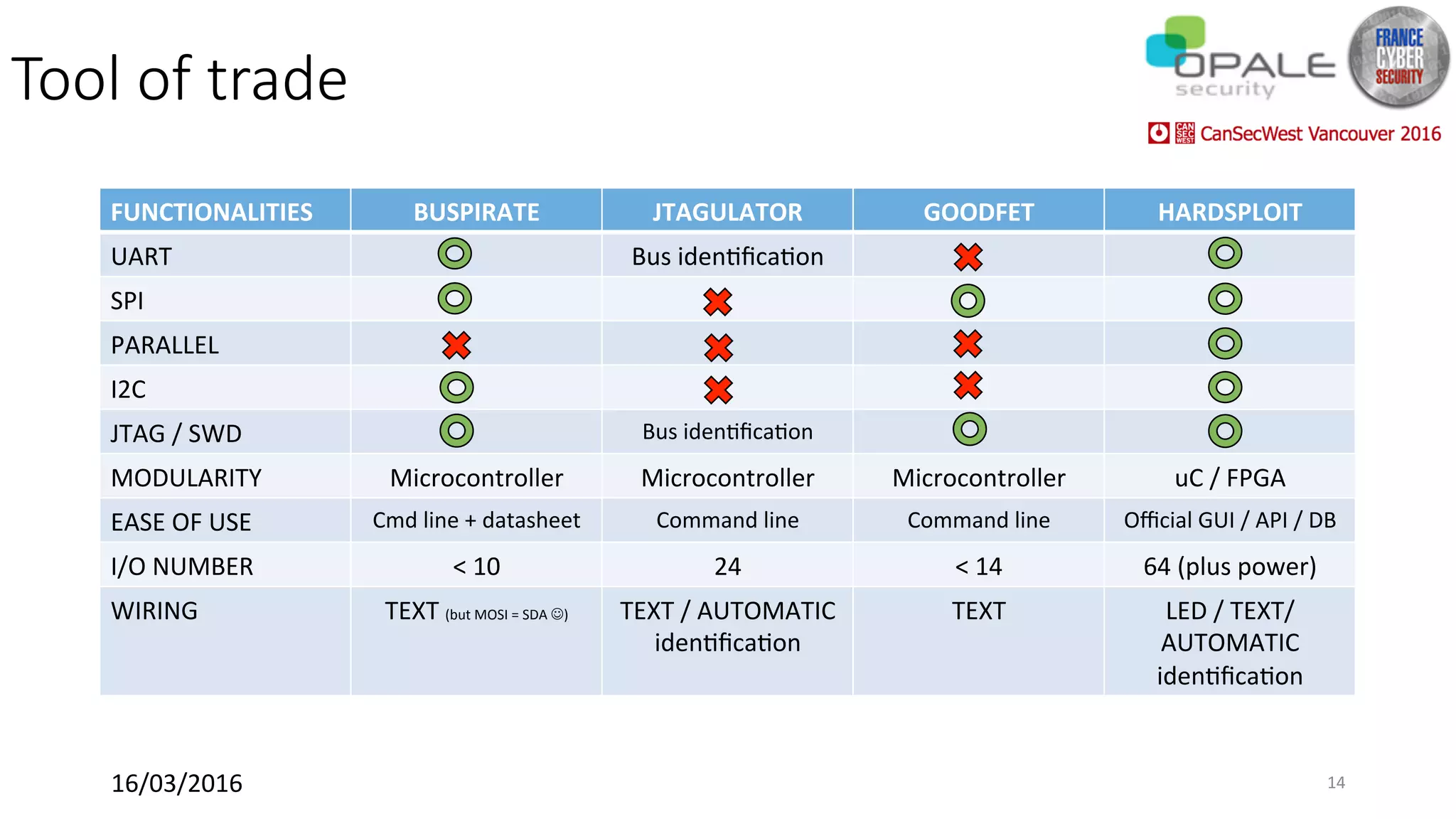
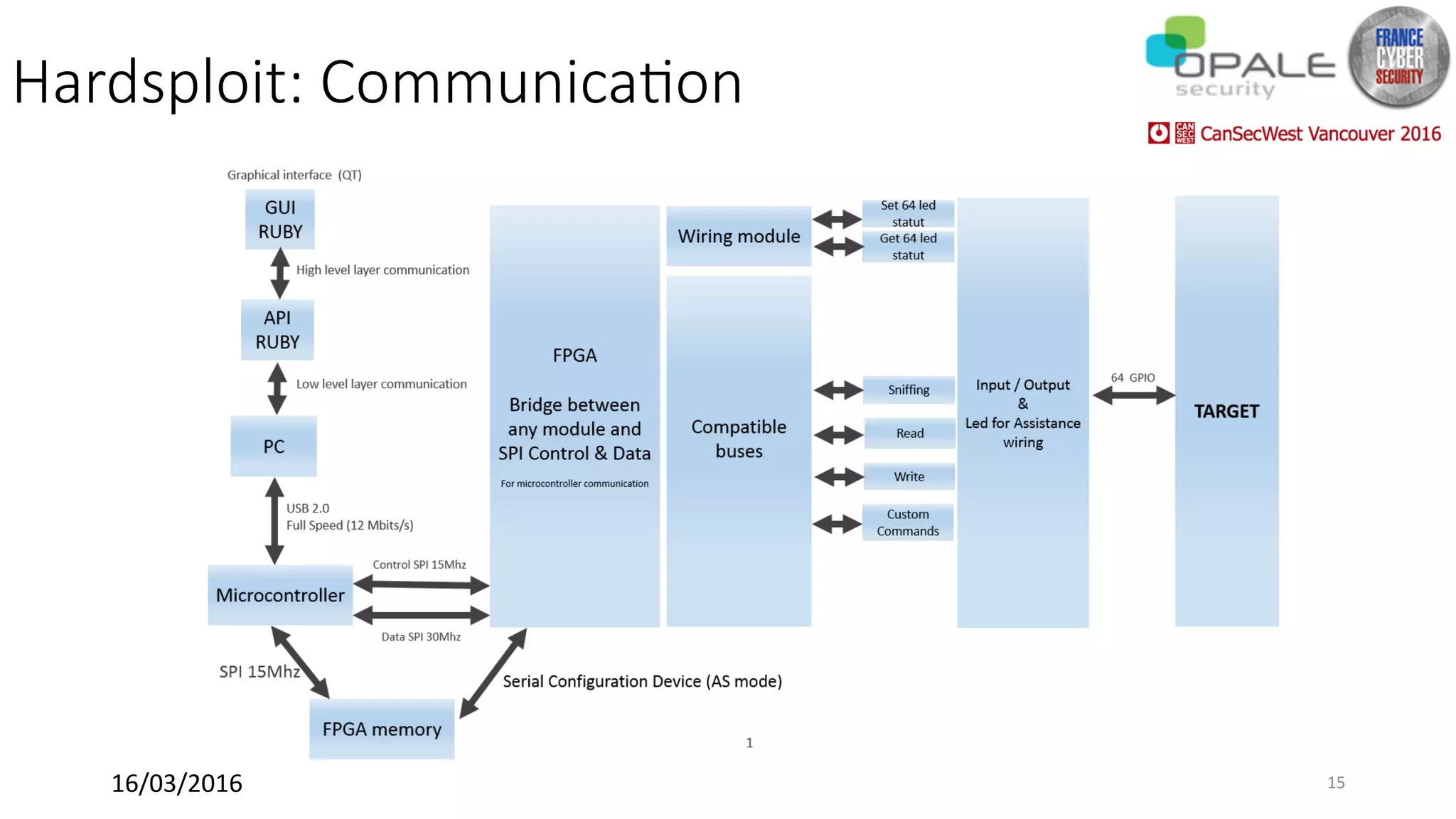
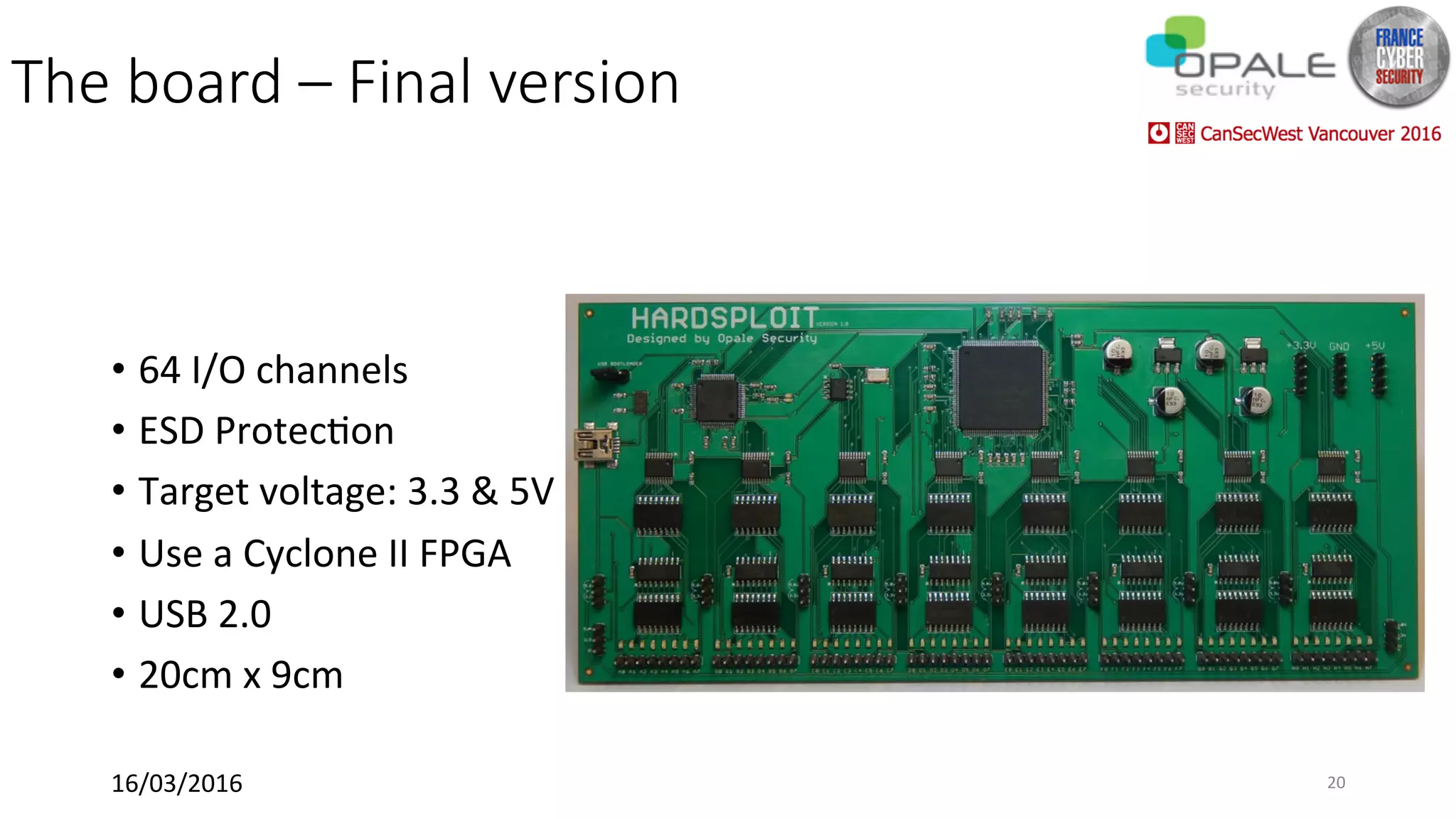
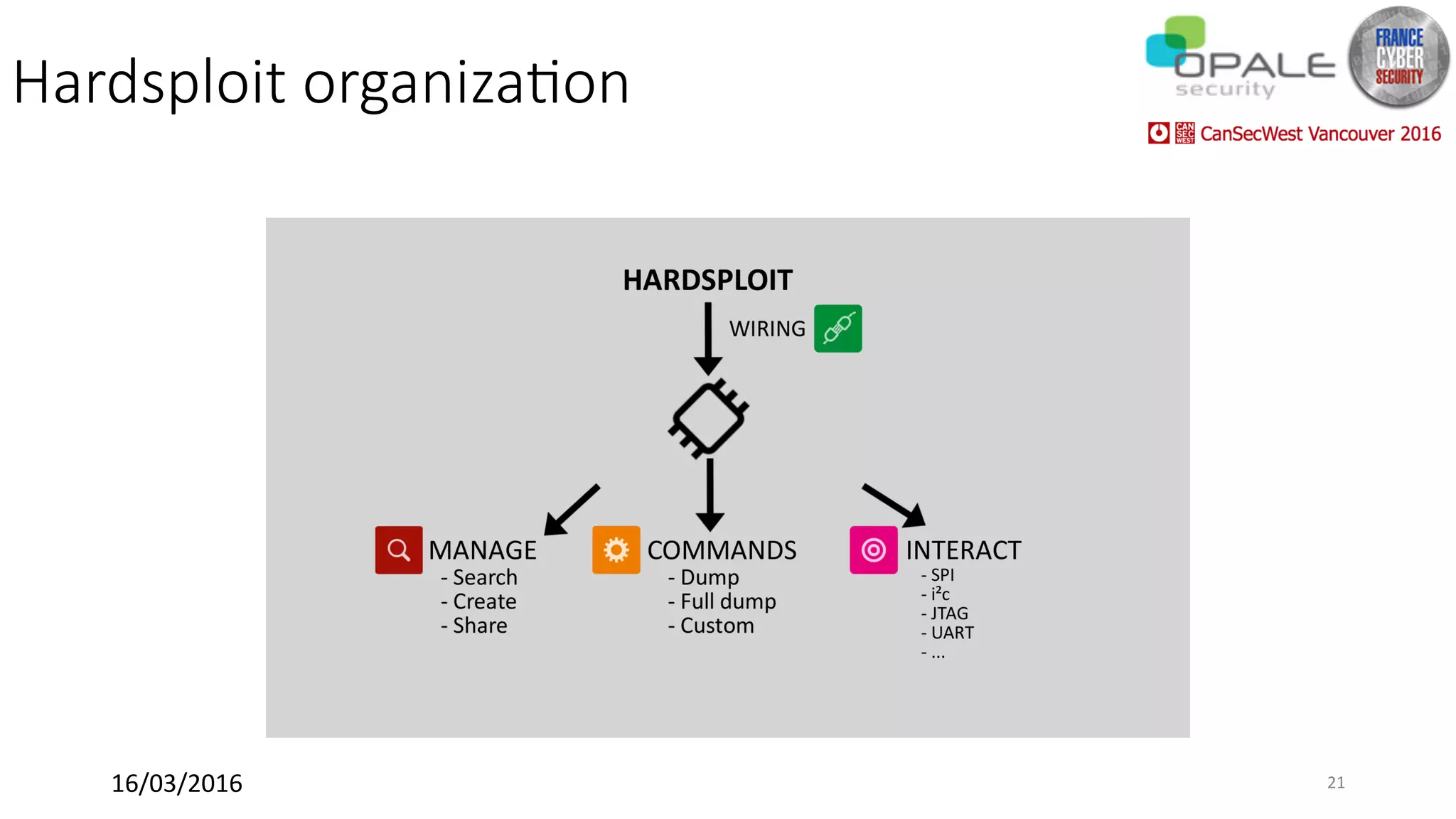
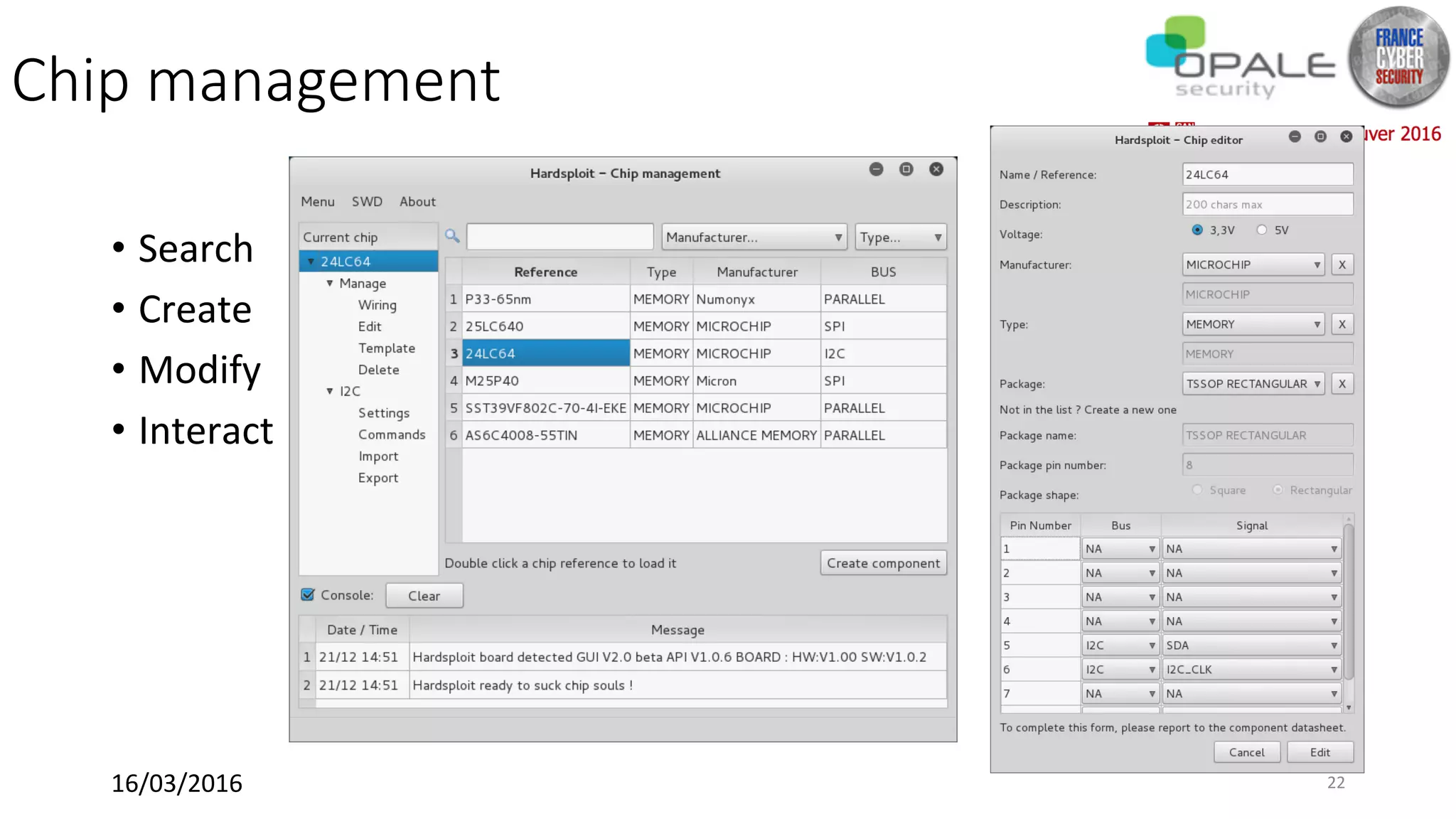
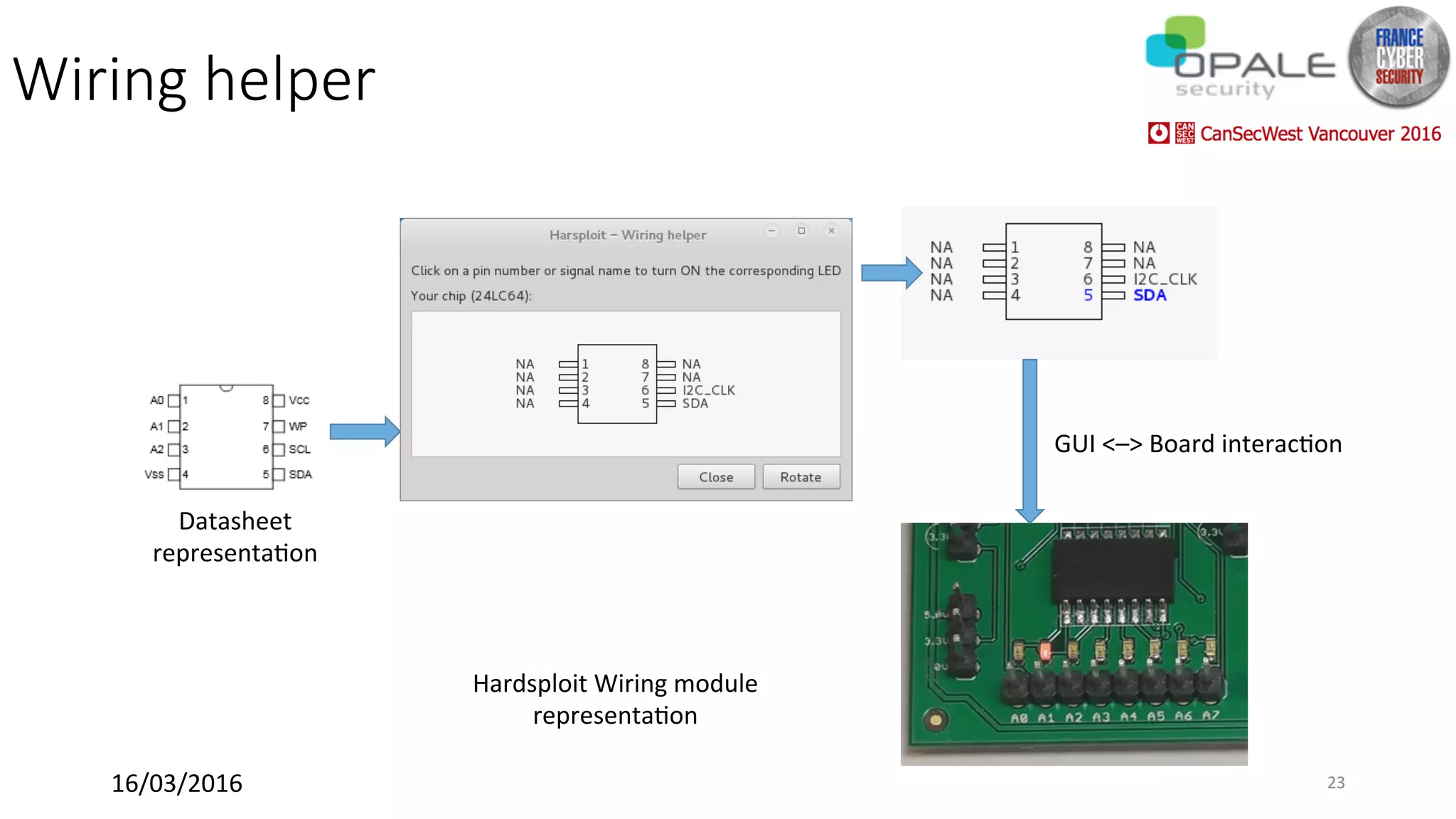
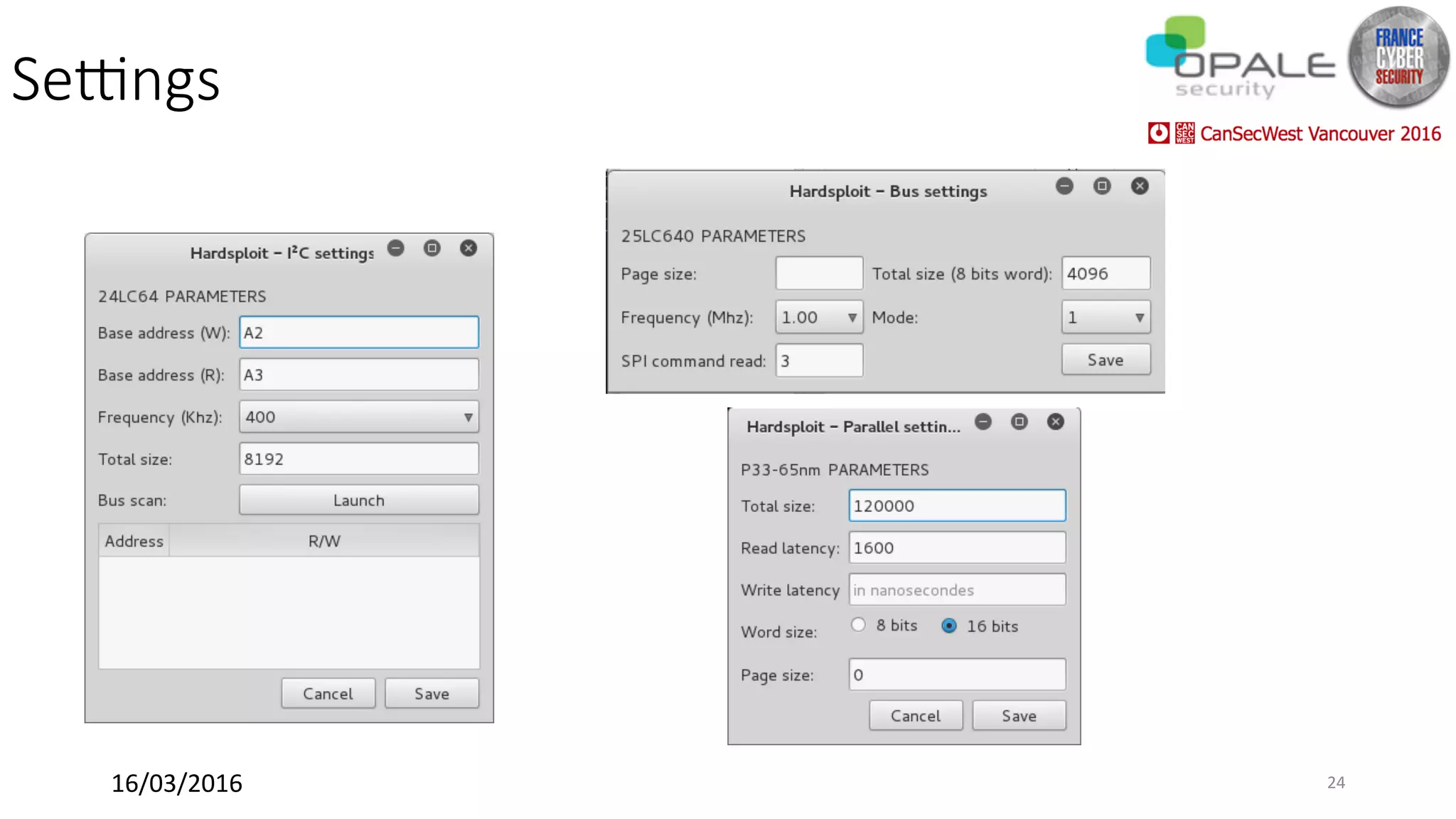
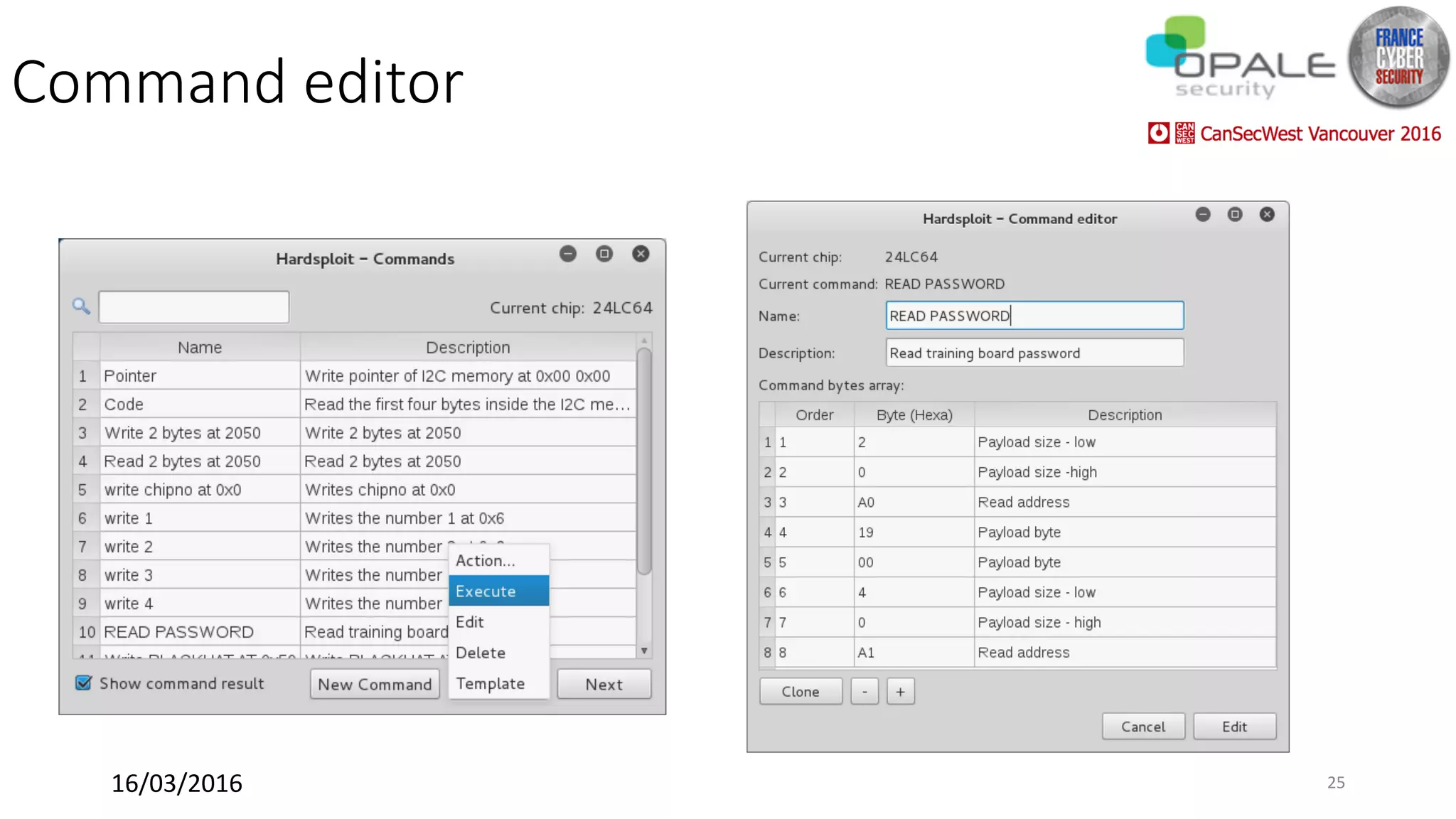
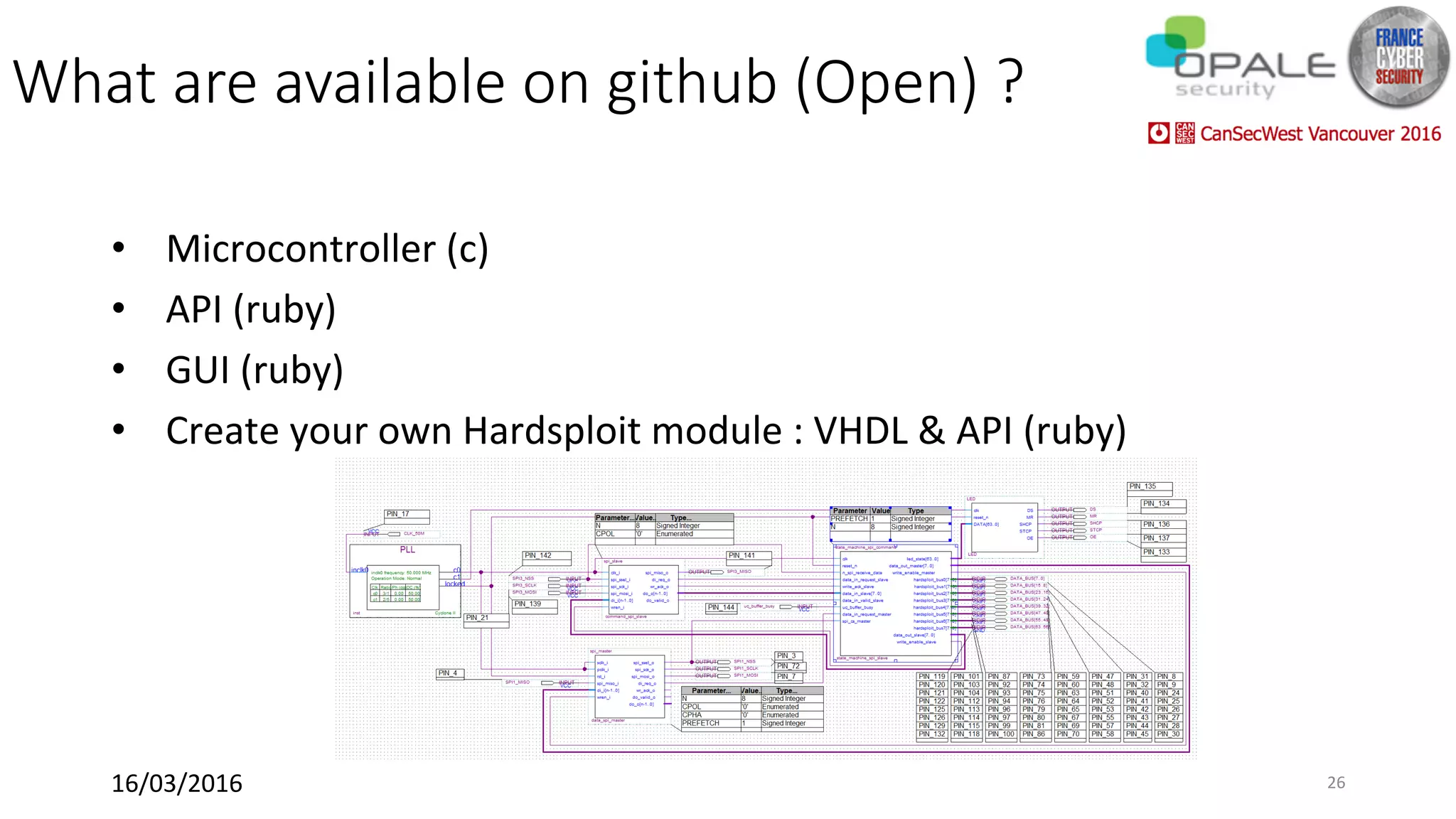
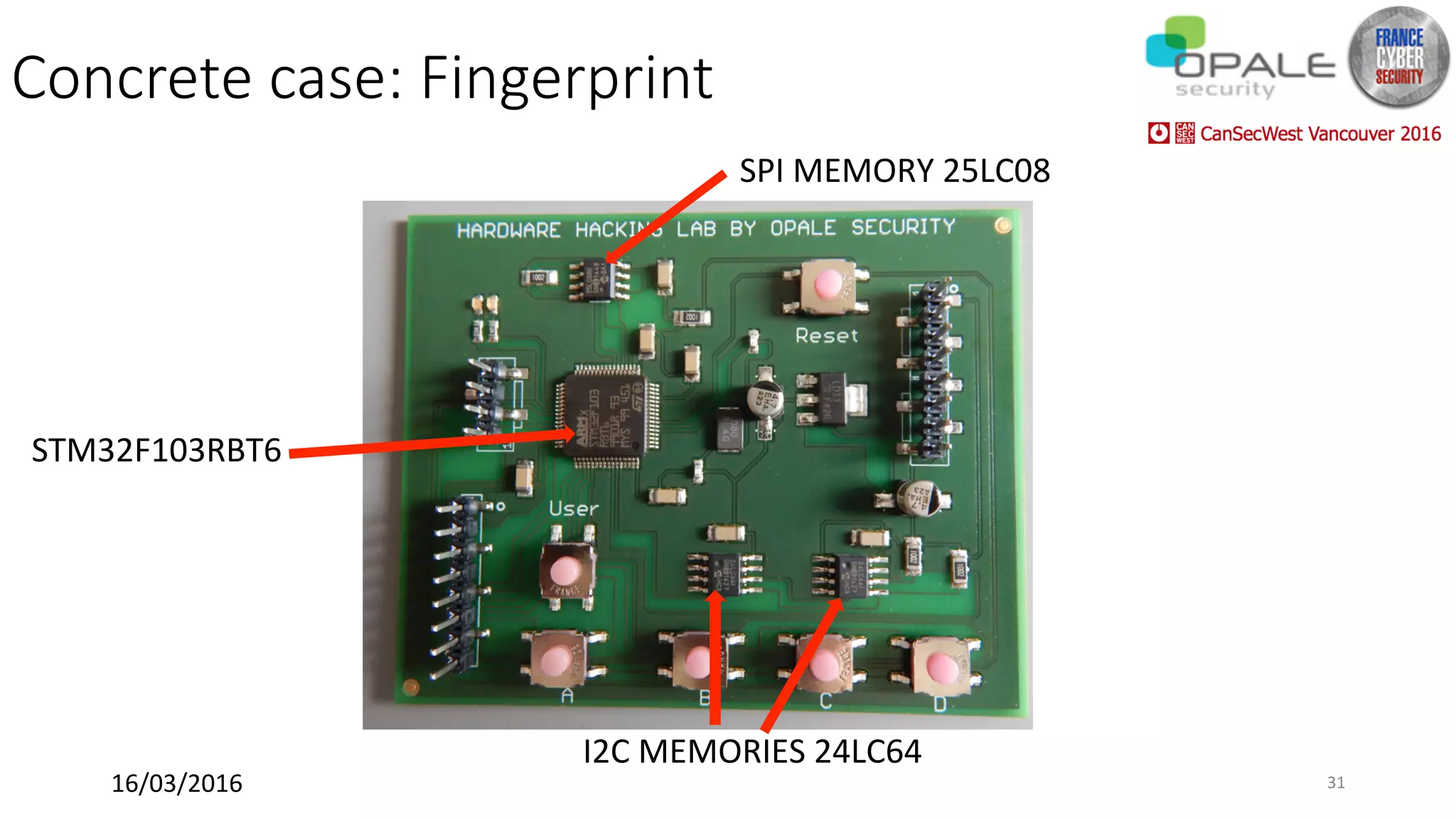
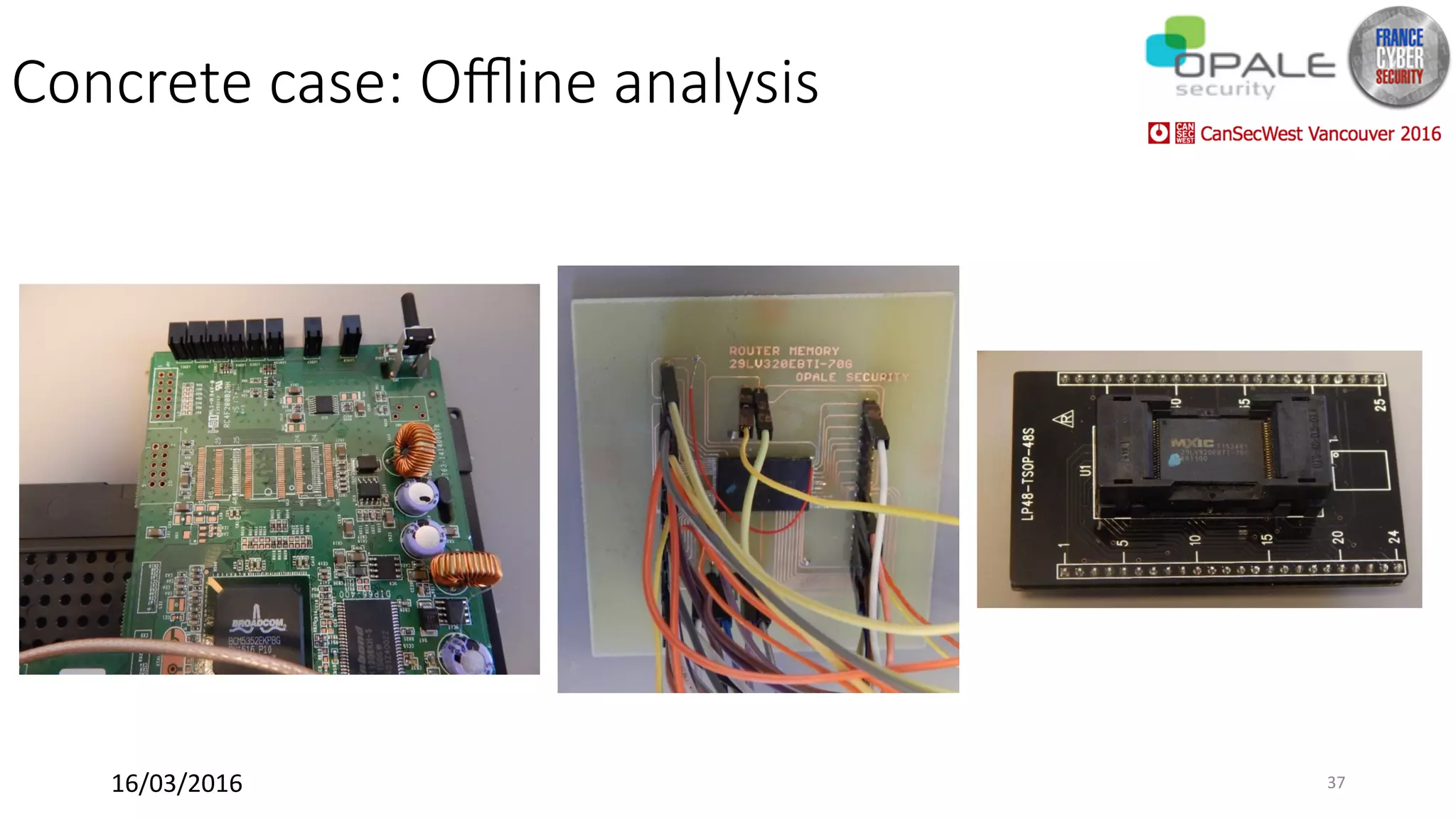
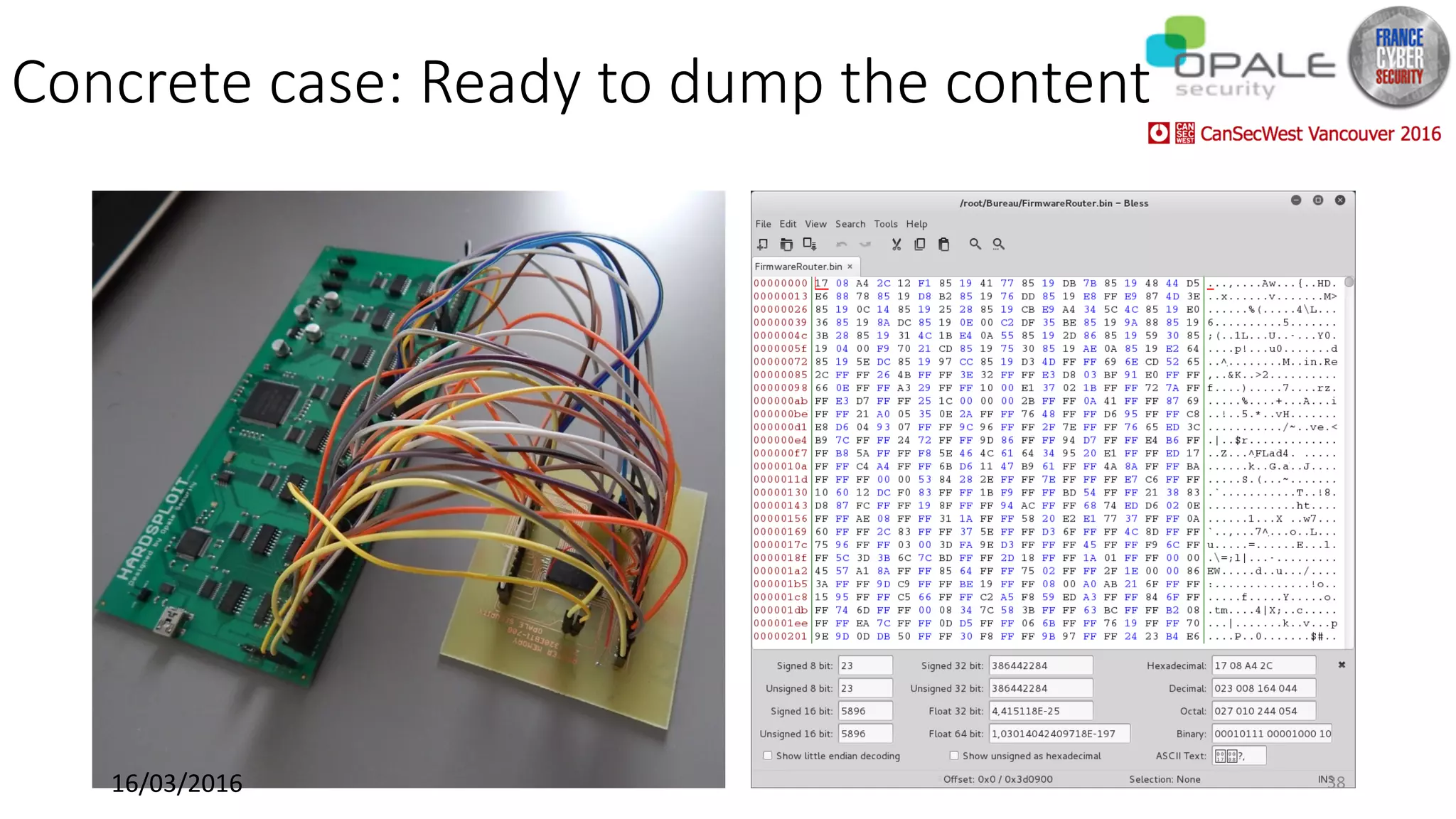
Hardsploit is a framework and hardware device that allows security researchers to audit and pentest hardware devices like IoT systems. It functions as a bridge between hardware interfaces and software testing tools. The framework includes a programmable hardware board with 64 I/O channels that can communicate over various protocols to analyze components, dump memory, and exploit vulnerabilities found in hardware. The goal of Hardsploit is to advance the field of hardware security testing and evaluation.