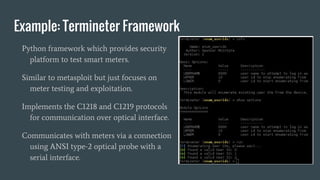
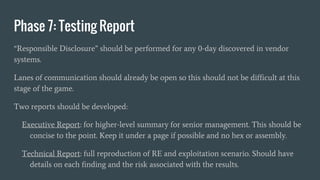
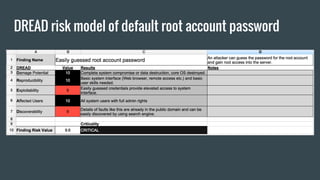
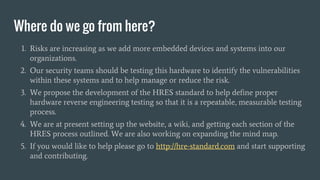
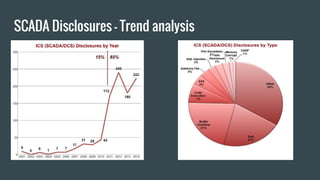
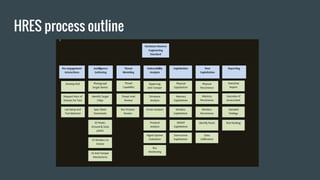
The document discusses hardware reverse engineering (RE) and proposes a Hardware Reverse Engineering Standard (HRES) process modeled after the Penetration Testing Execution Standard (PTES). The HRES process includes 7 phases: pre-engagement interactions, intelligence gathering, threat modeling, vulnerability analysis, exploitation, post-exploitation, and reporting. The goal is to define a standard for assessing embedded device and hardware security that provides measurable and repeatable testing beyond a basic vulnerability scan. Collaboration from the hardware security community is sought to further develop the HRES.


































![Phase 5: Exploitation
Physical Exploitation, Memory Exploitation, Wireless Exploitation, Management
System Exploitation, and Destructive Exploitation will all be avenues of attack.
Develop Proof-of-Concept exploits against discovered vulnerabilities to demonstrate
code execution and process redirection.
Bypass restrictions (firewall [Data Diodes] or IDS, access permissions, etc.) to show
that network controls can be bypassed.
If push comes to shove, assess creative exploit methods (social engineering) to
demonstrate the insider threat.](https://image.slidesharecdn.com/3a82fa90-2d2e-4855-b579-b915e5867f00-160429201714/85/Finding-the-needle-in-the-hardware-haystack-HRES-1-43-320.jpg)