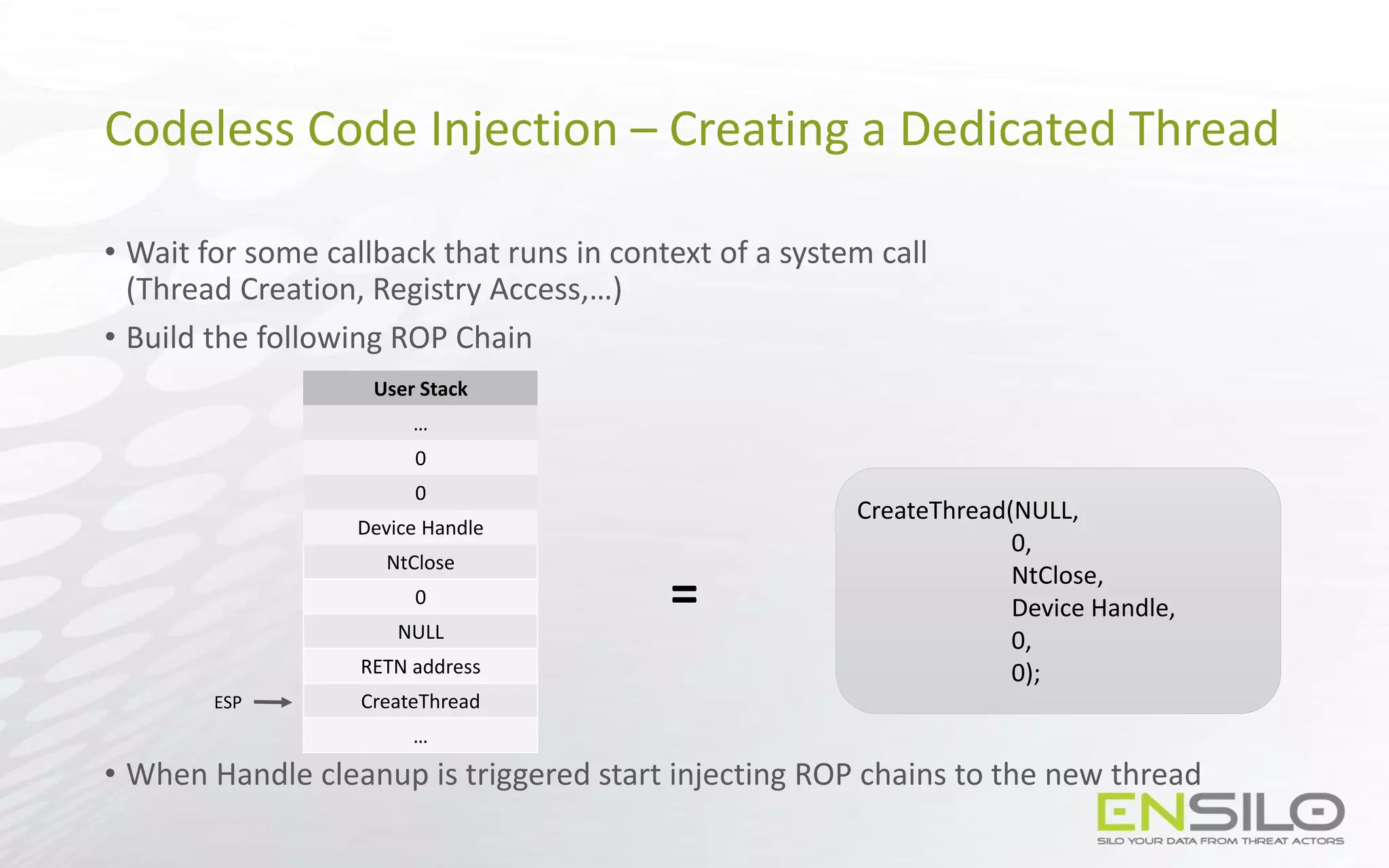
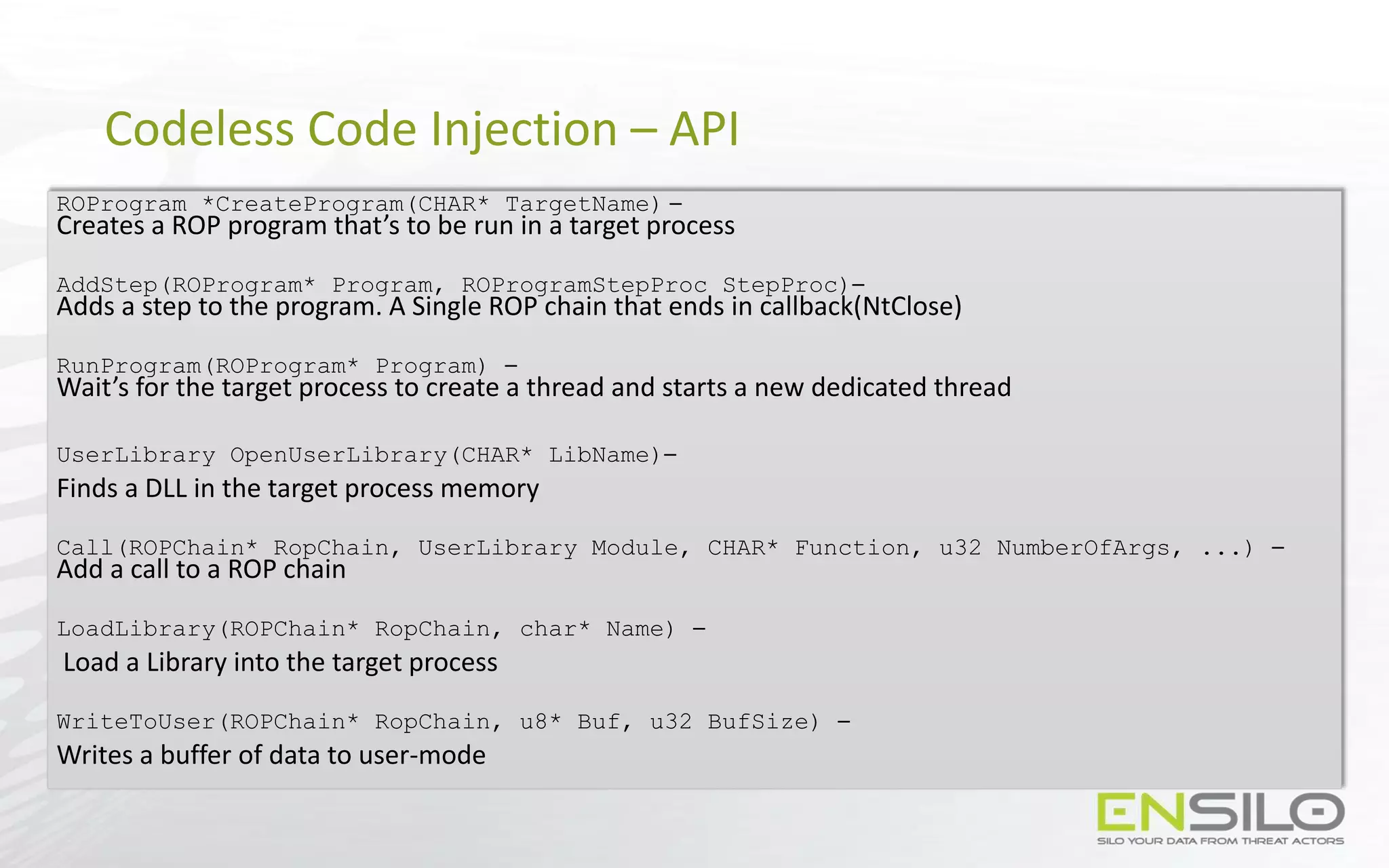
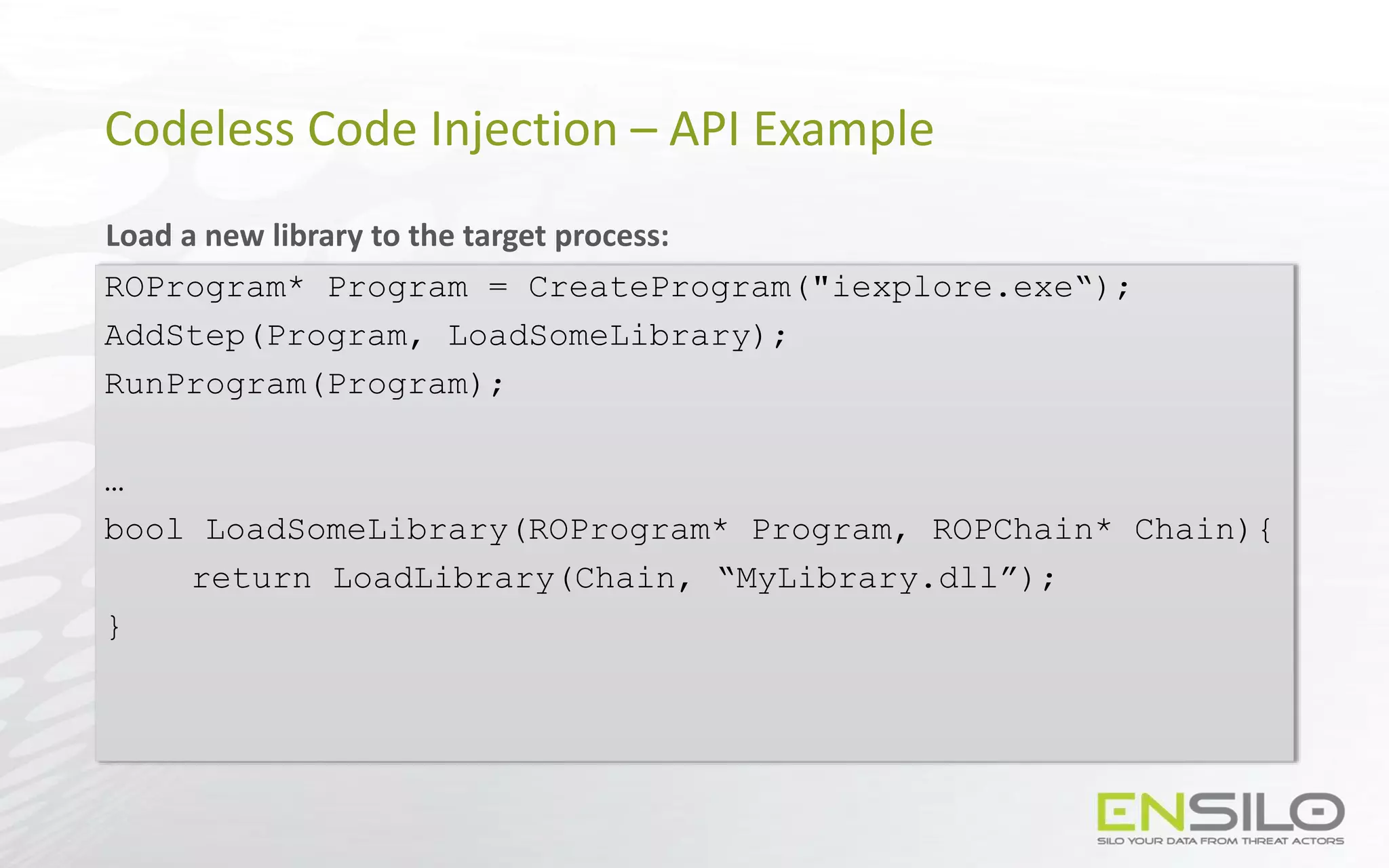
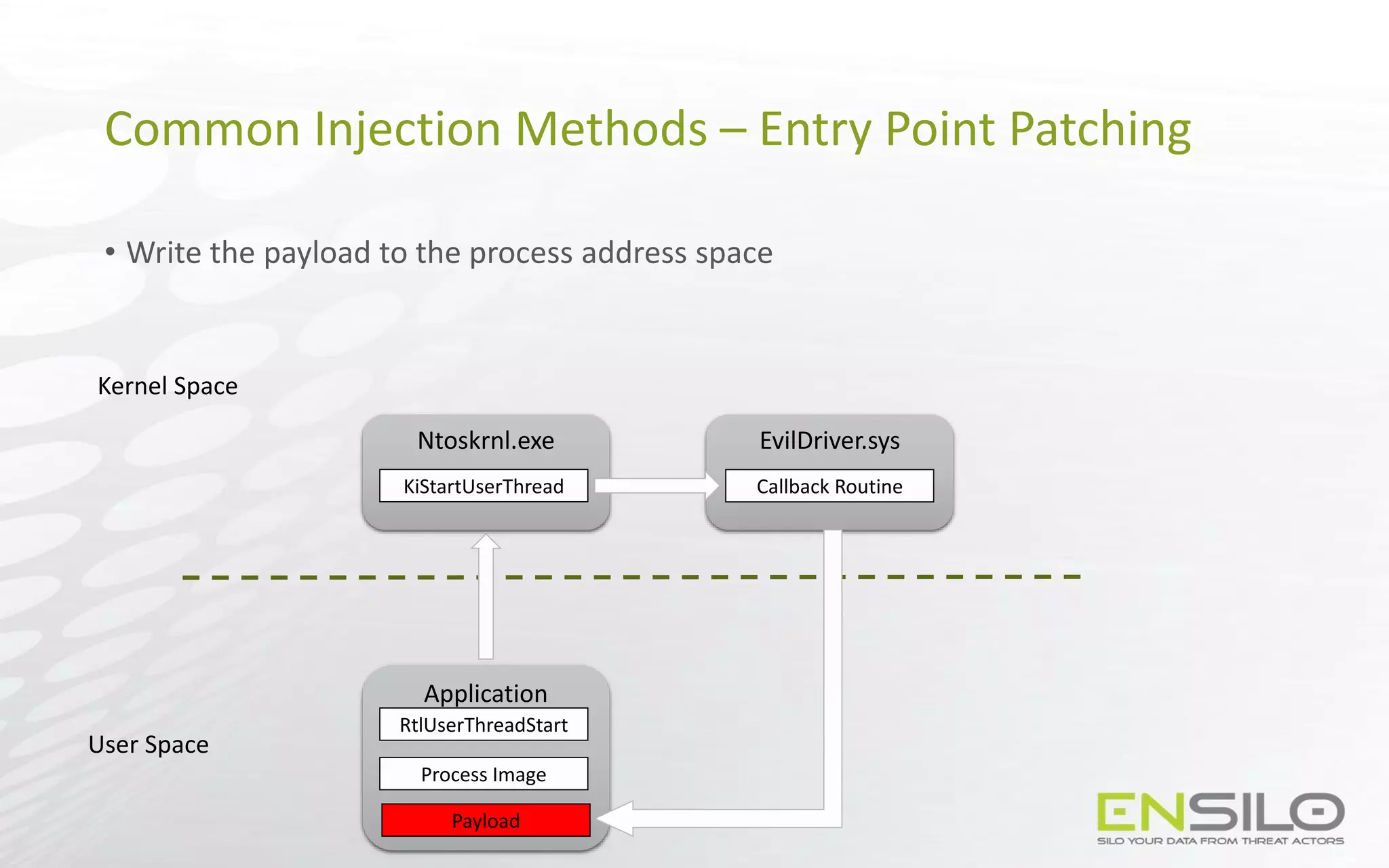
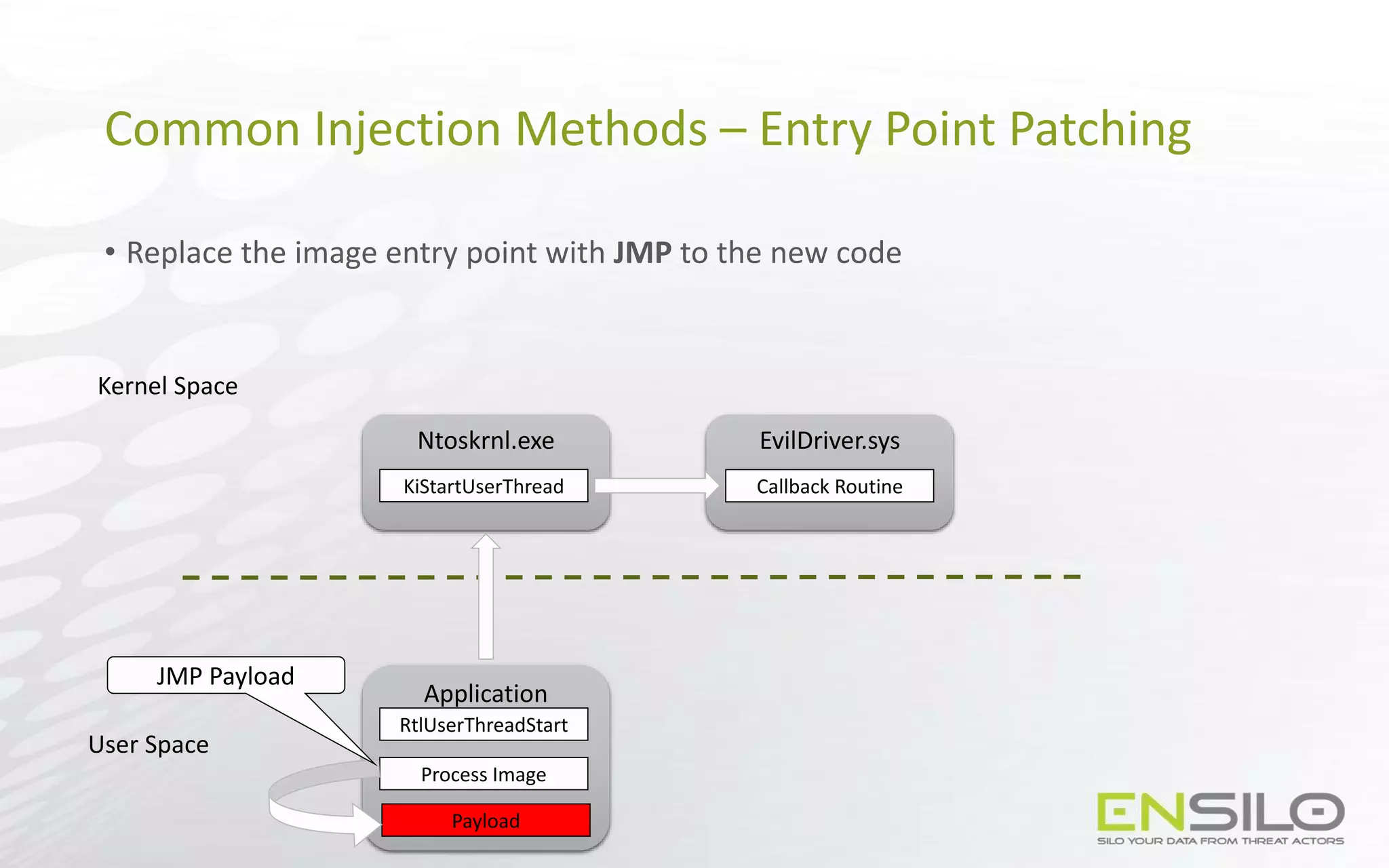
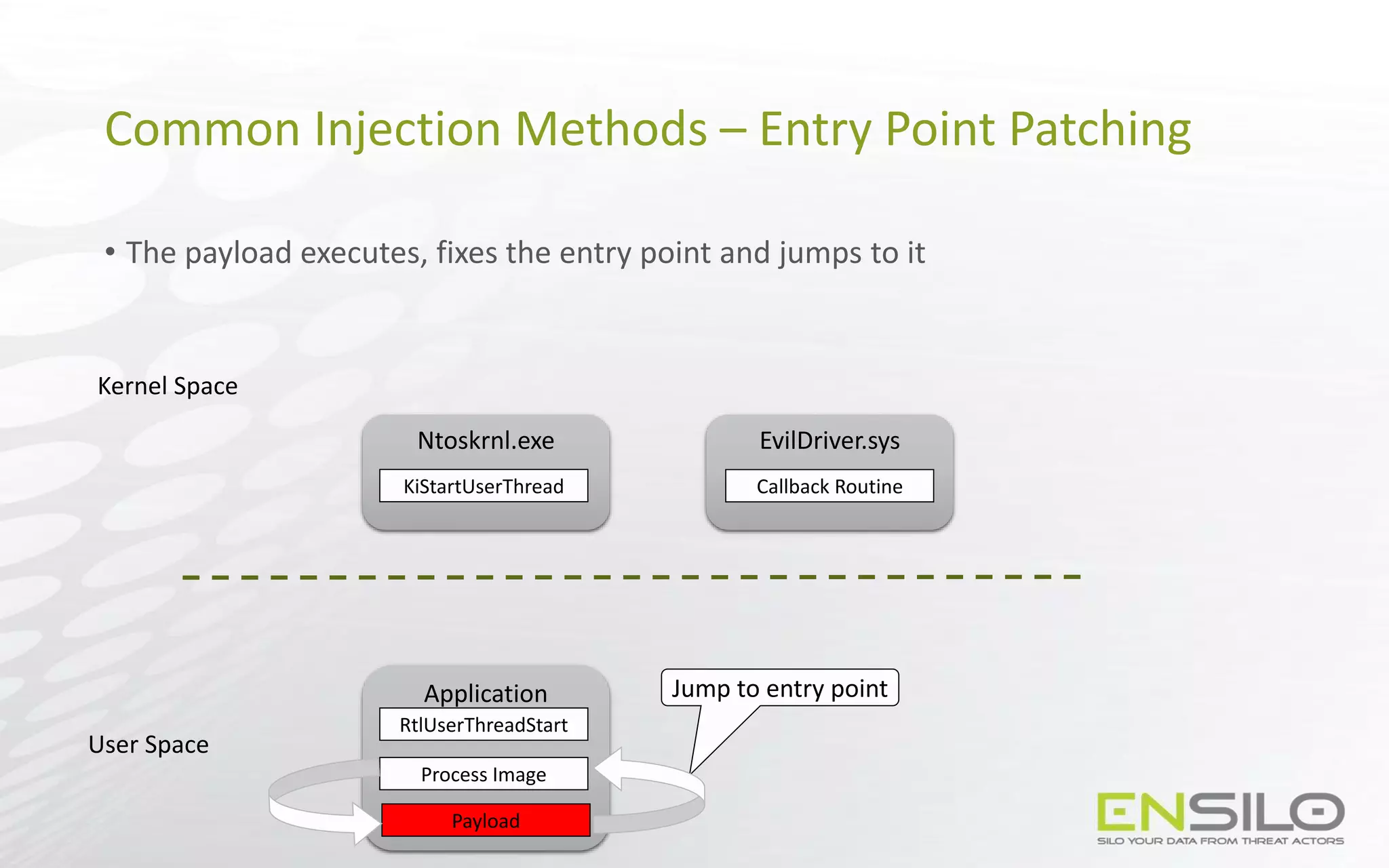
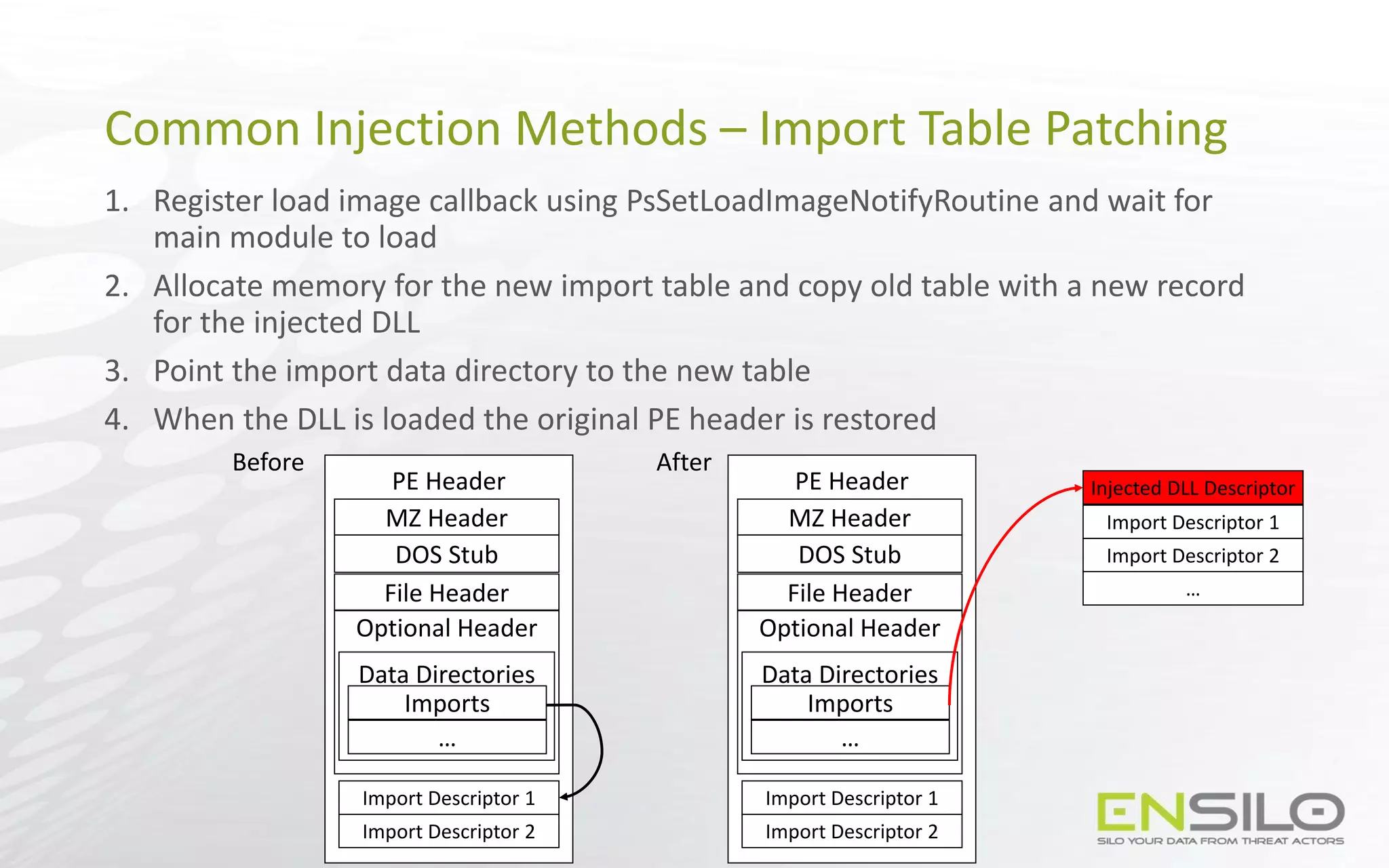
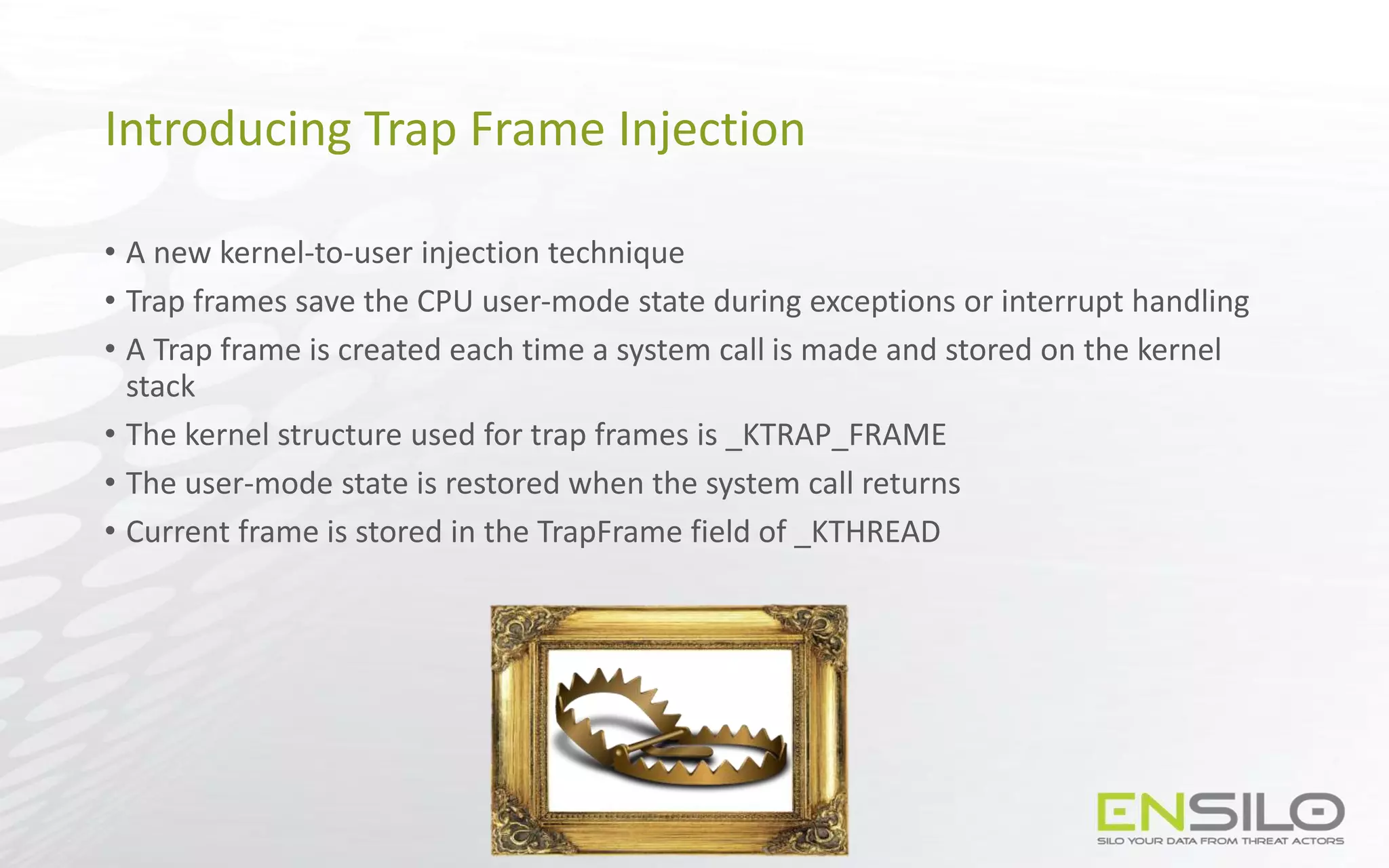
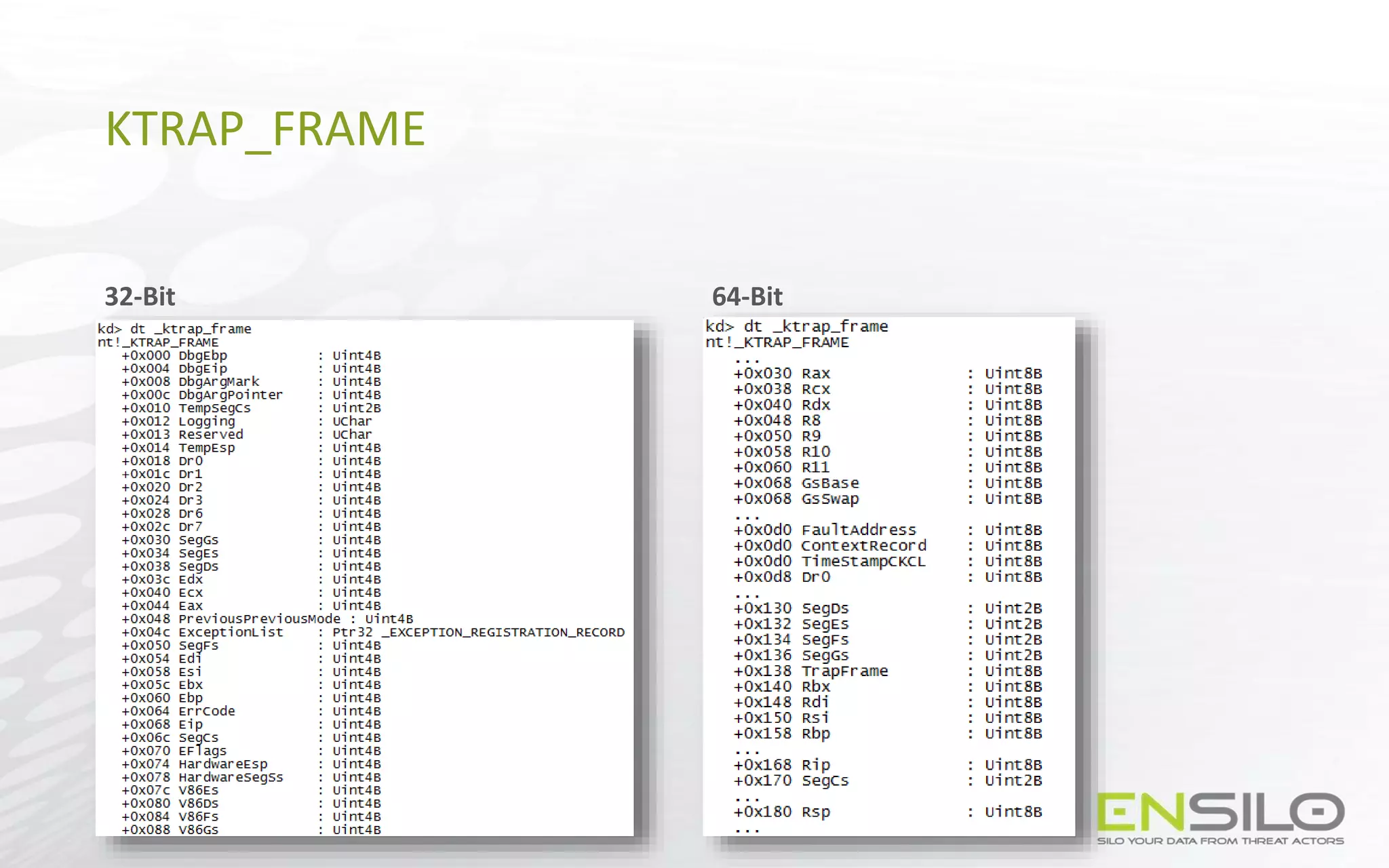
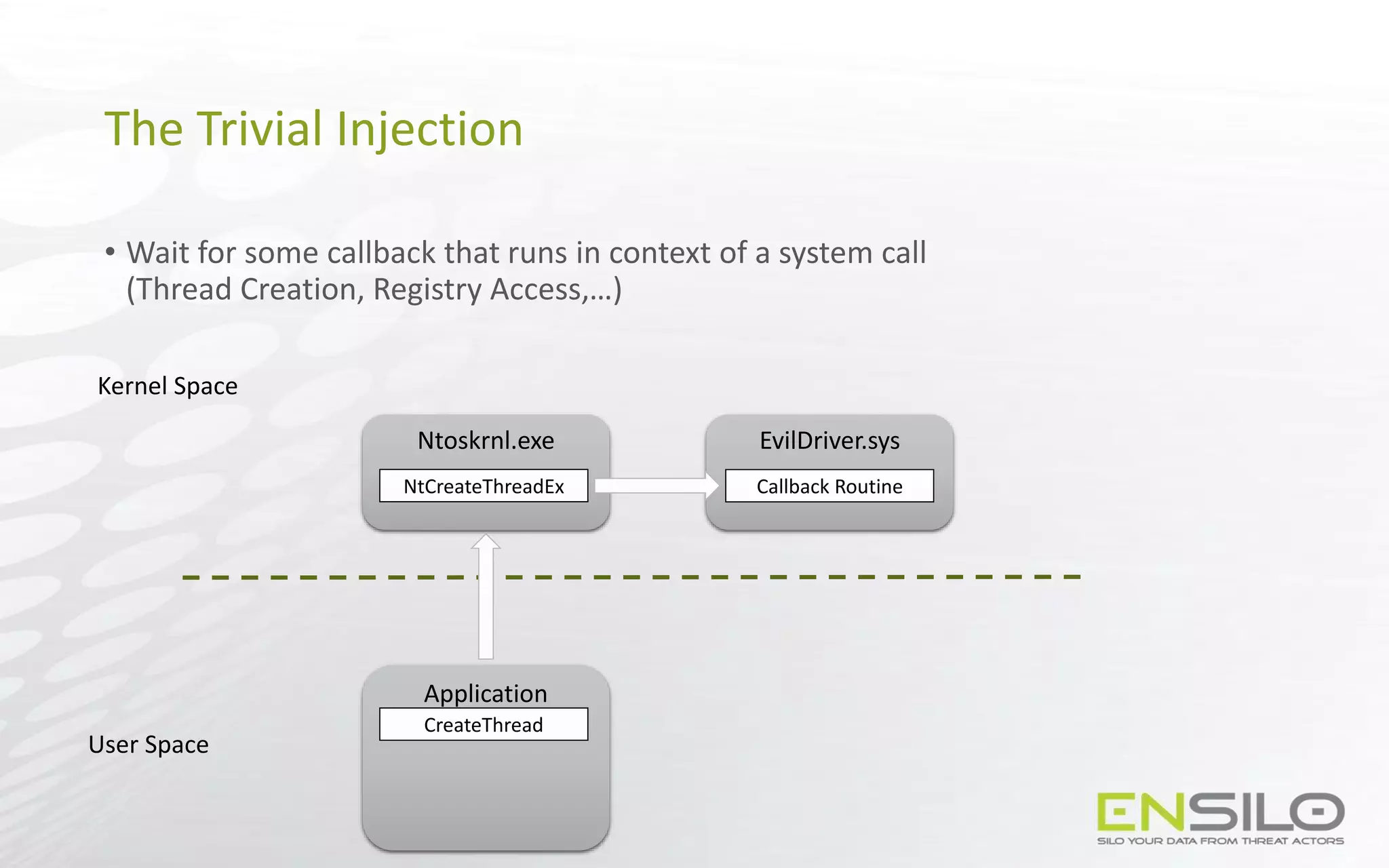
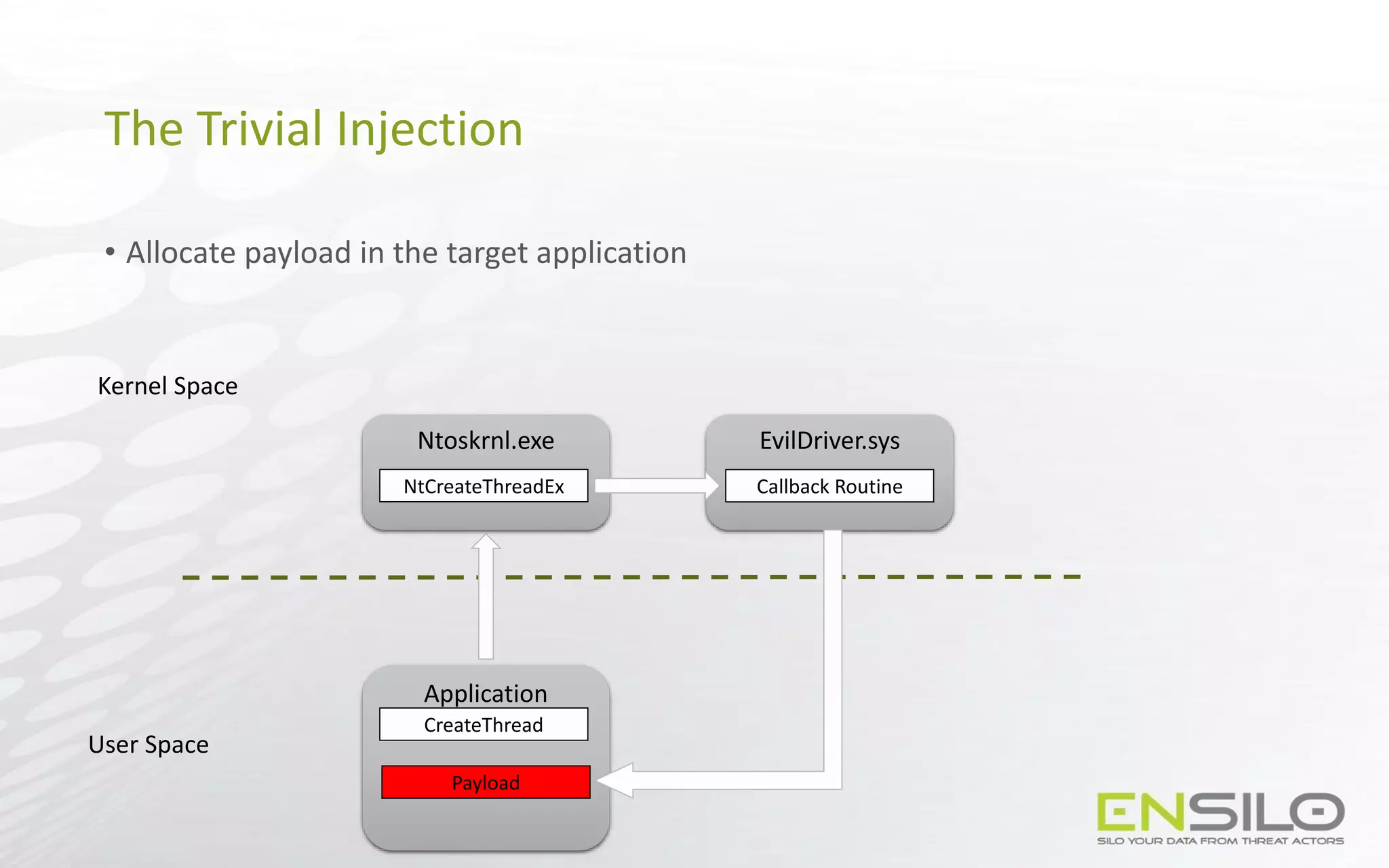
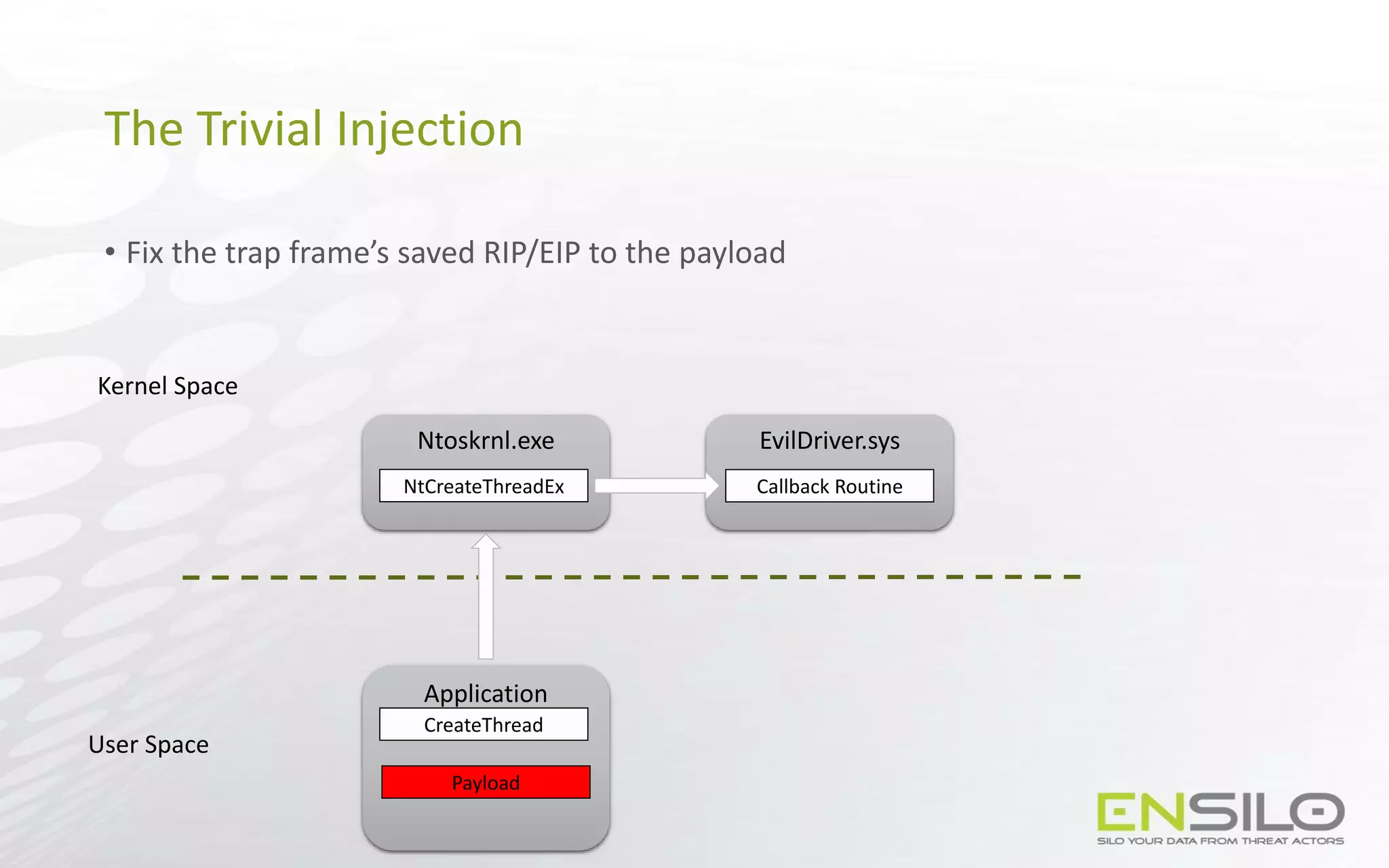
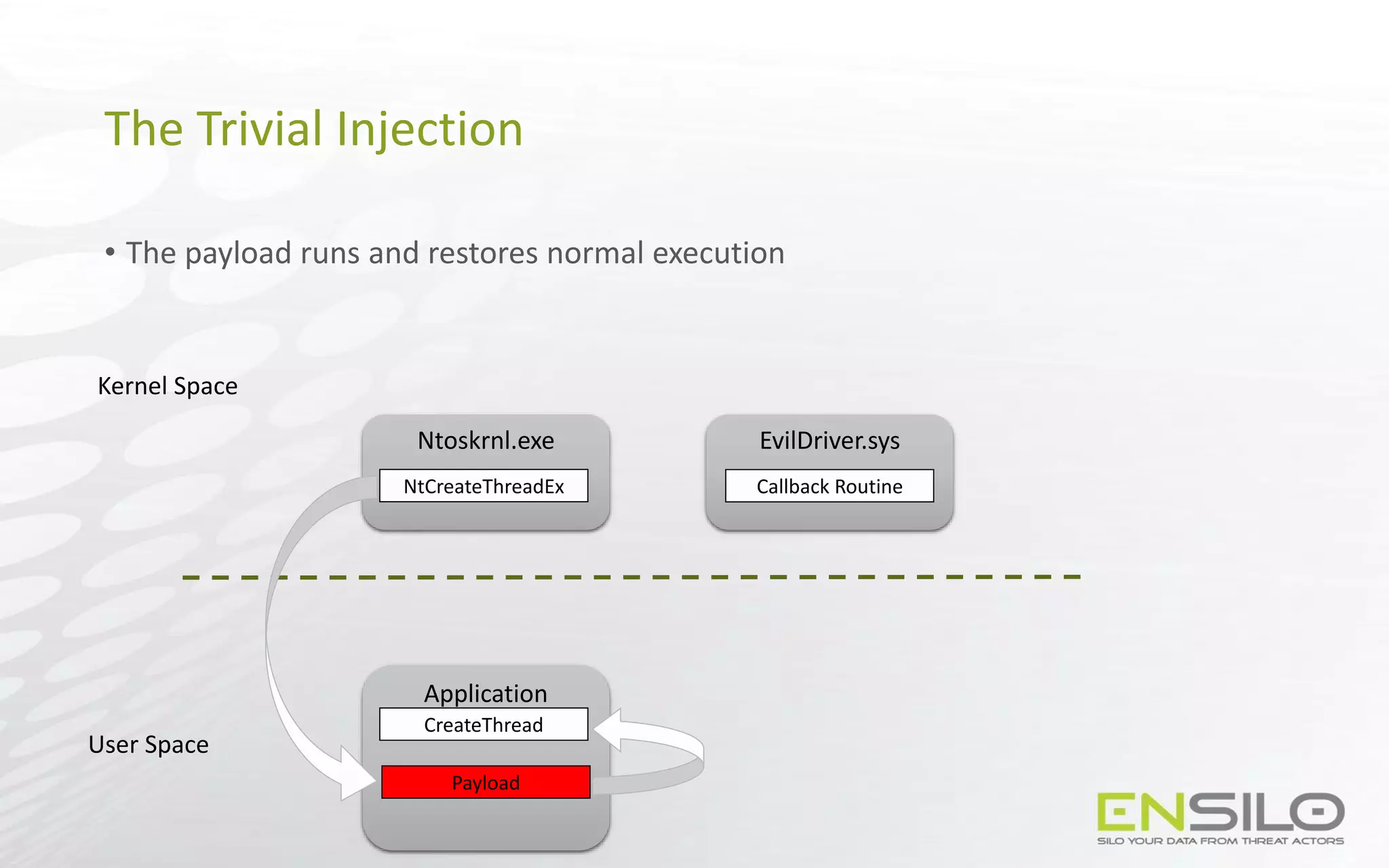
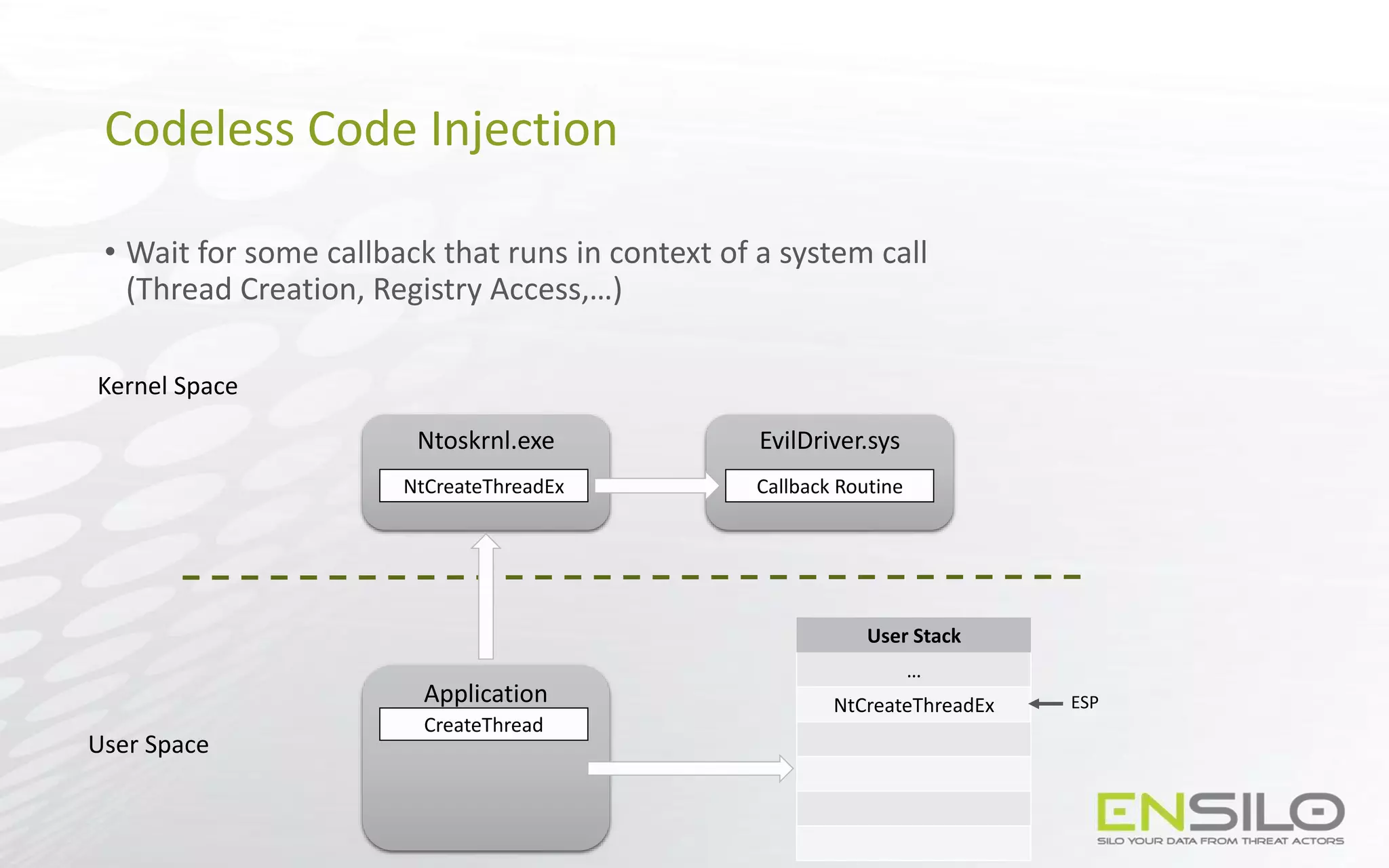
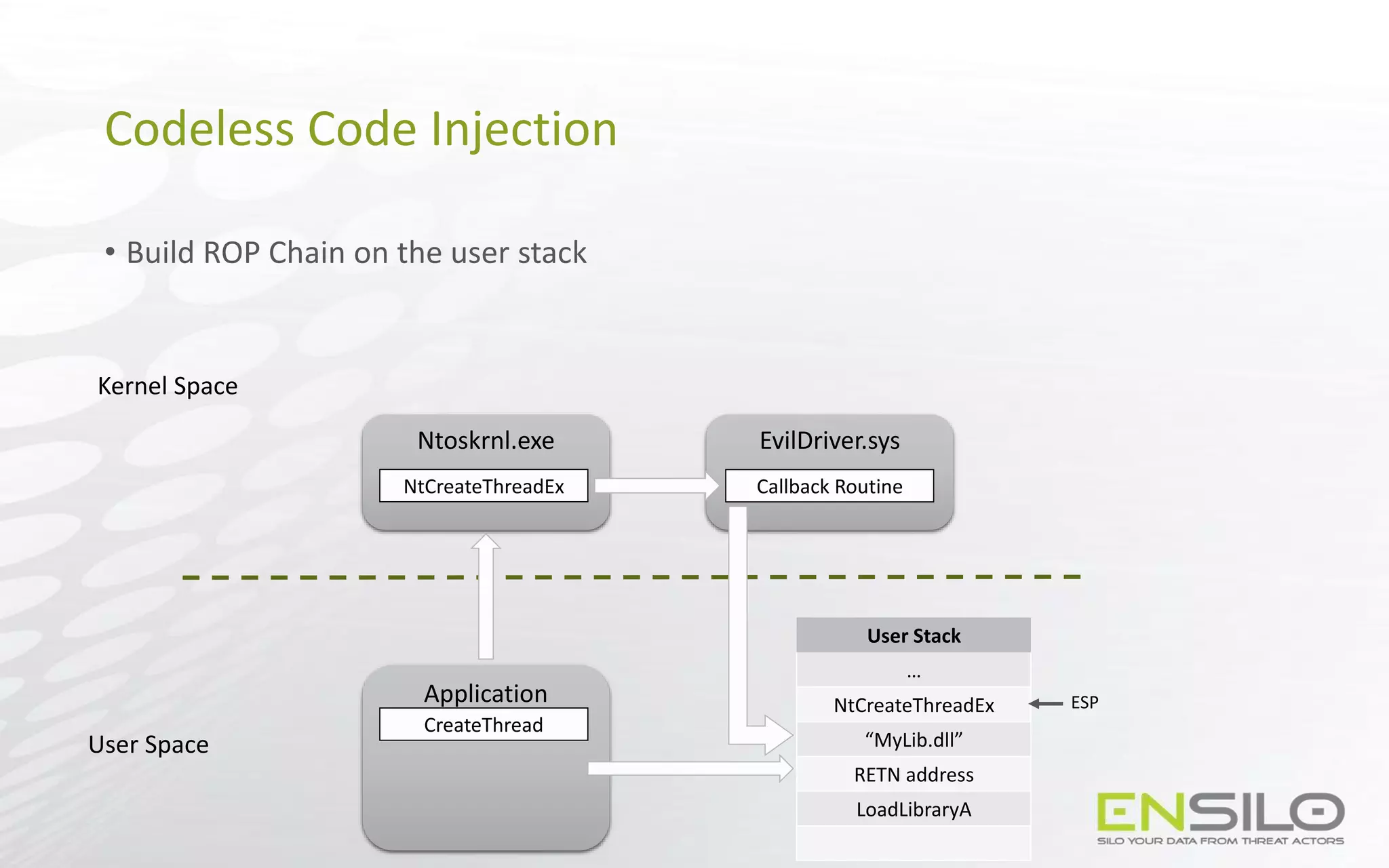
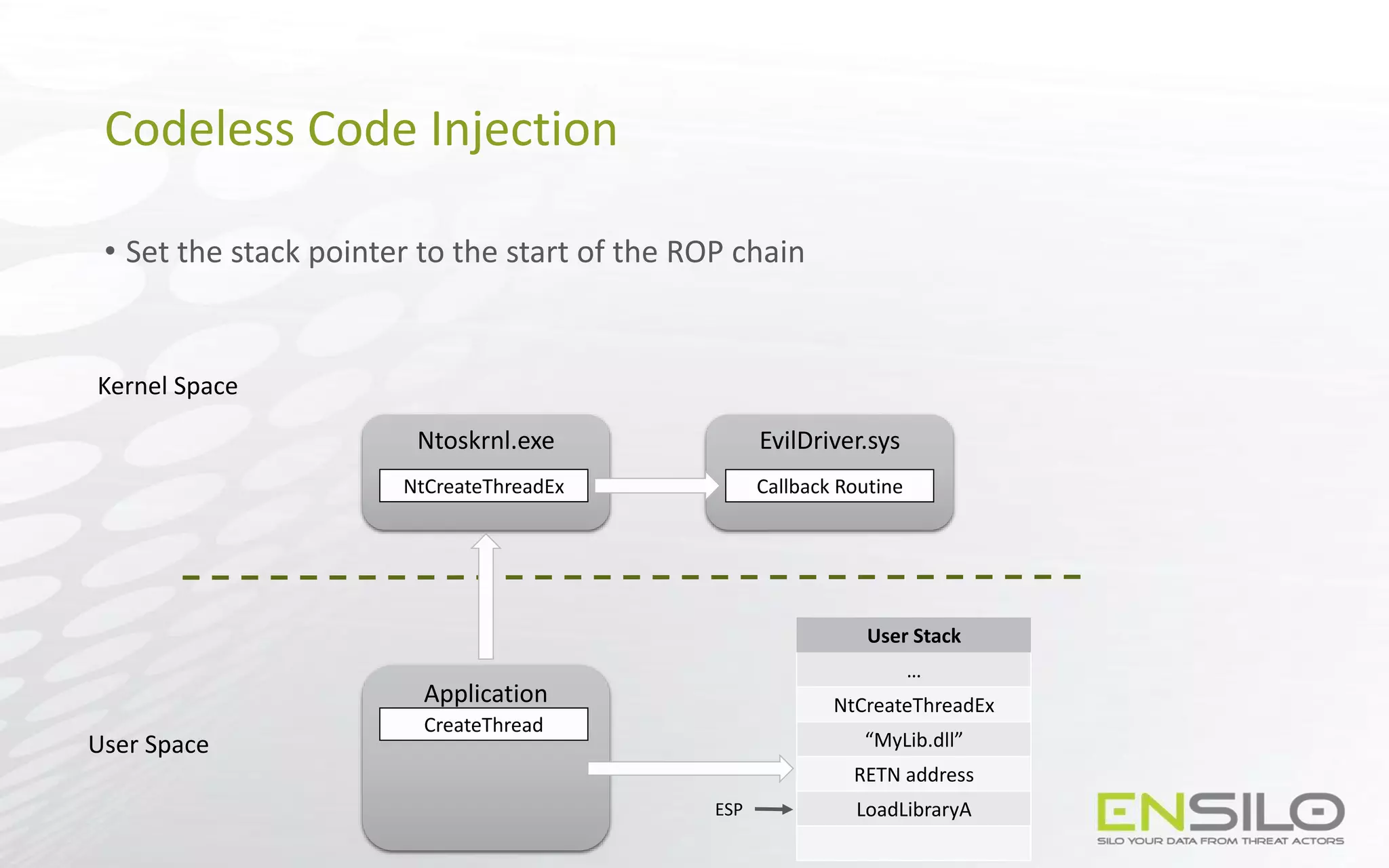
This document discusses techniques for injecting code into processes without directly writing code to the target process's memory. It introduces a technique called "Trap Frame Injection" which hijacks the CPU's user mode state that is stored in trap frames during system calls. It also presents a "Codeless Code Injection" technique which builds ROP chains on the user stack and manipulates the stack pointer to trigger execution without direct code writes. Challenges with this approach like getting return values and avoiding deadlocks are also outlined along with solutions like using a device handle callback or creating a dedicated thread.












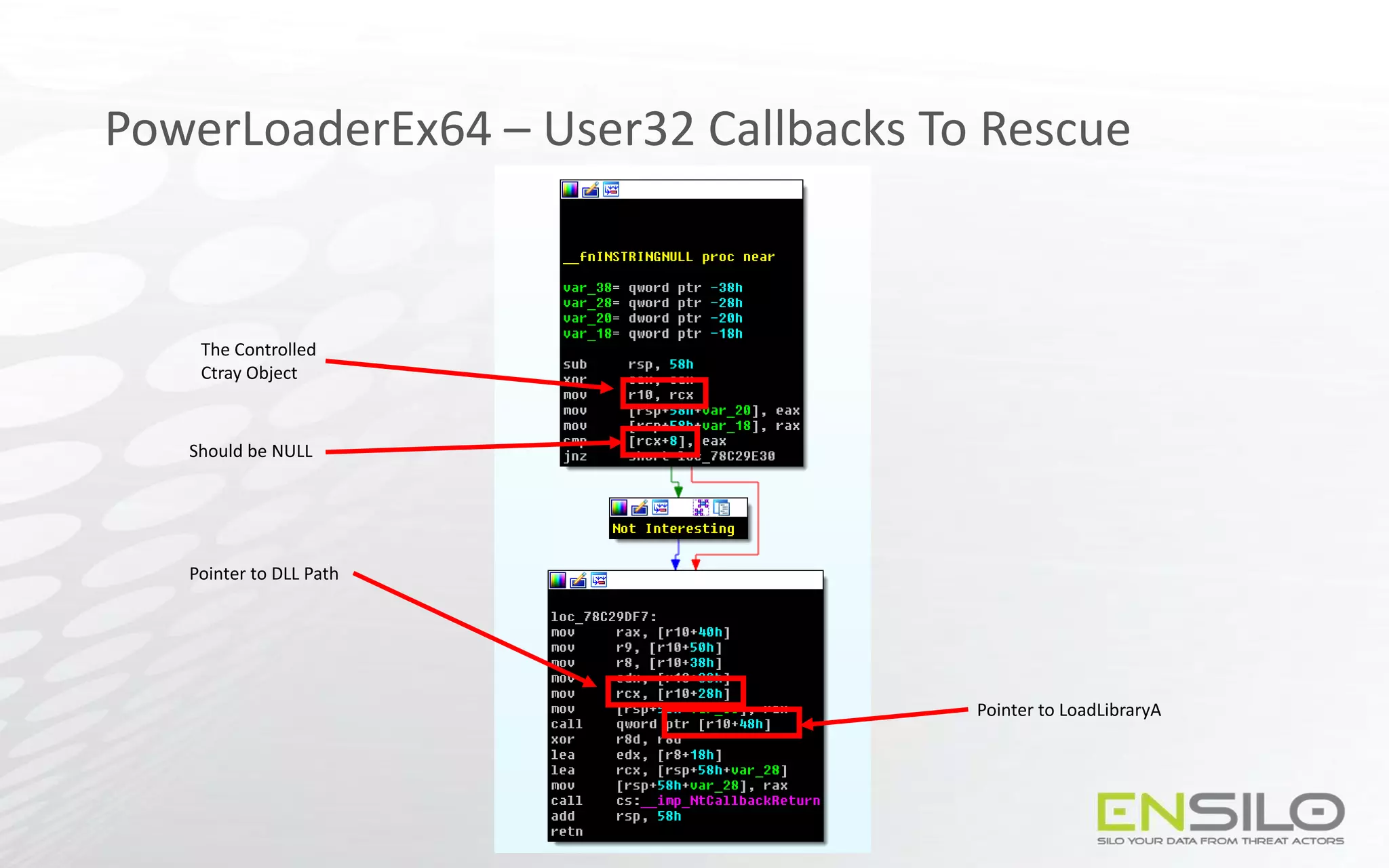








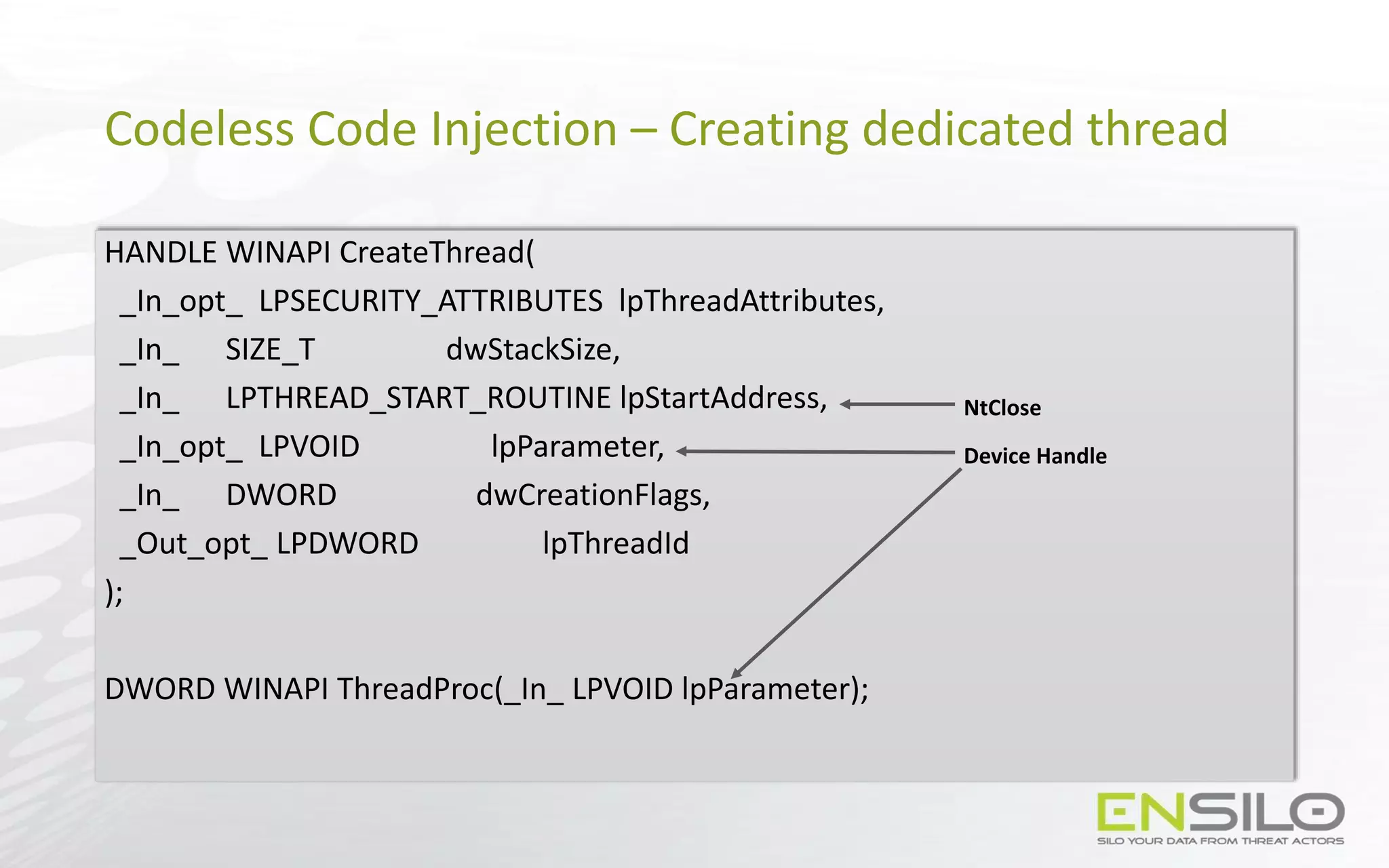
![Codeless Code Injection - NtClose as a callback
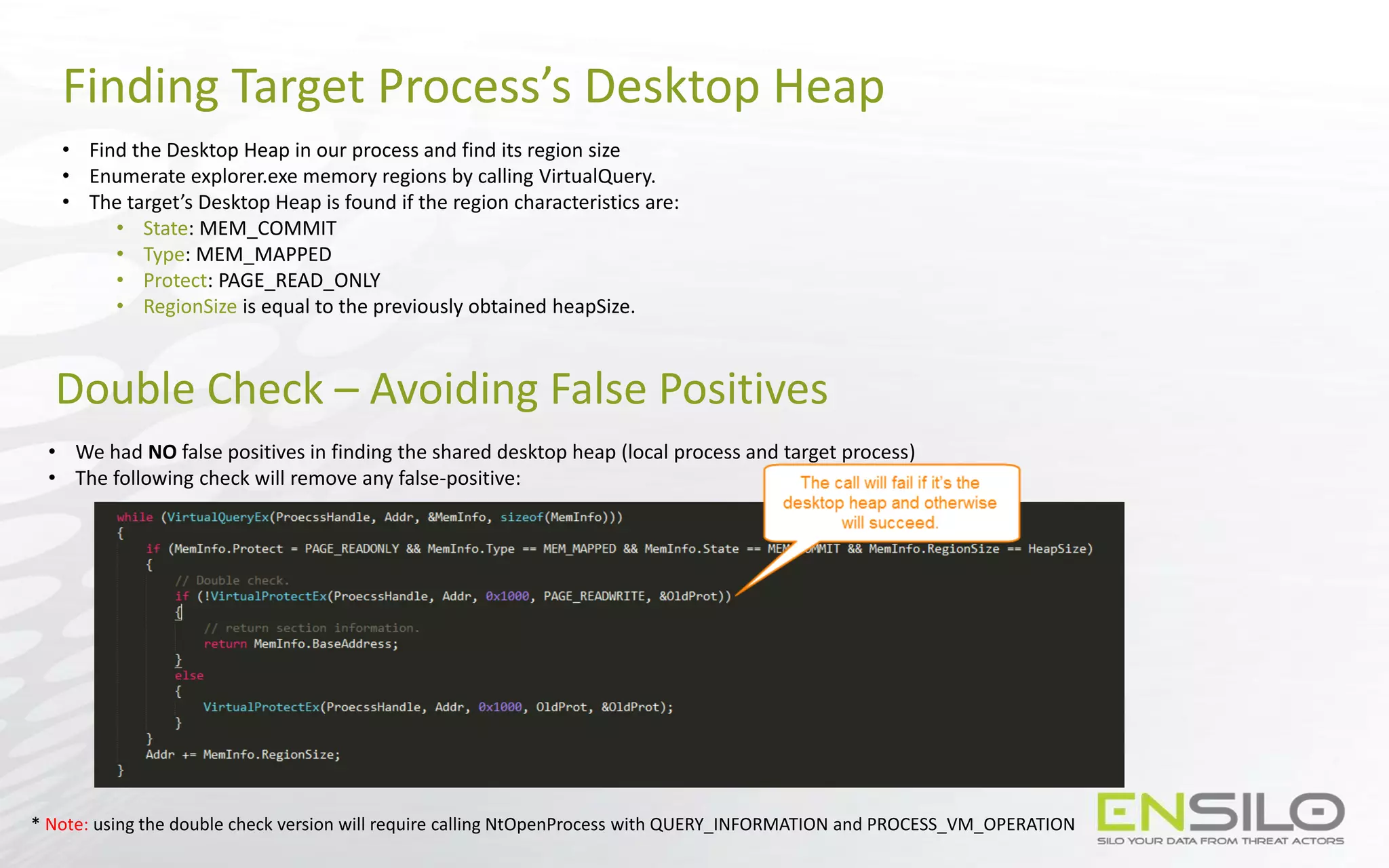
• Create a device using IoCreateDevice
• Whenever we require a callback, create a handle for the device in the target process
• Build the following ROP chain:
User Stack
…
Device Handle
RETN address
NtClose
MOV [EDX], EAX Gadget
Writable Location
POP EDX Gadget
…
ESP
=
MOV EDX, ADDRESS
MOV [EDX], EAX
NtClose(DeviceHandle)](https://image.slidesharecdn.com/codelesscodeinjections-150812130732-lva1-app6891/75/Injection-on-Steroids-Codeless-code-injection-and-0-day-techniques-46-2048.jpg)
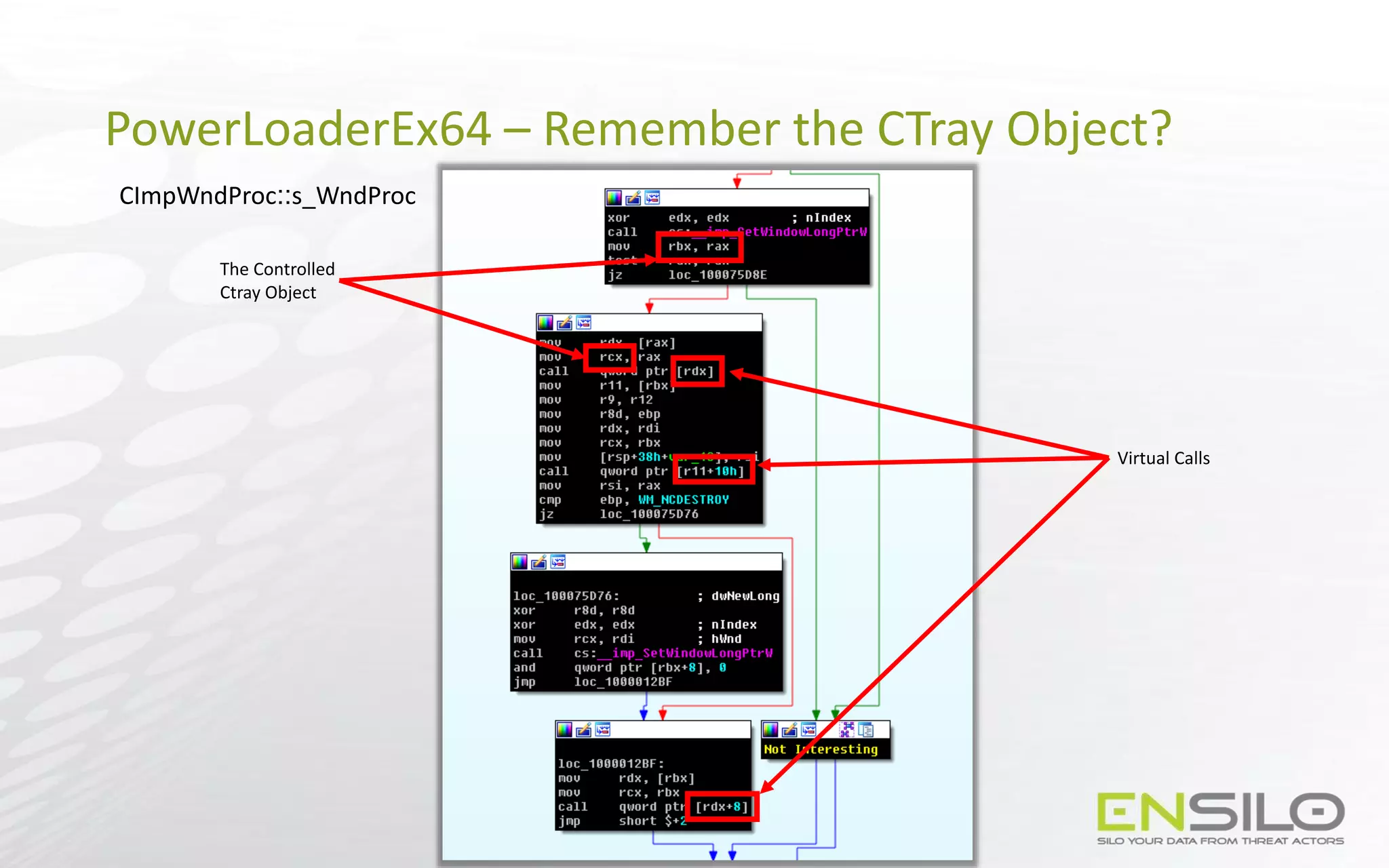
![Codeless Code Injection - NtClose as a callback
• When NtClose(Device Handle) is executed then the IRP_MJ_CLEANUP handler will be
called
• The required data will reside in the target address
* moving EAX to some register is not safe because of WOW64
ESP
User Stack
…
Device Handle
RETN address
NtClose
MOV [EDX], EAX Gadget
Writable Location
POP EDX Gadget
…](https://image.slidesharecdn.com/codelesscodeinjections-150812130732-lva1-app6891/75/Injection-on-Steroids-Codeless-code-injection-and-0-day-techniques-47-2048.jpg)