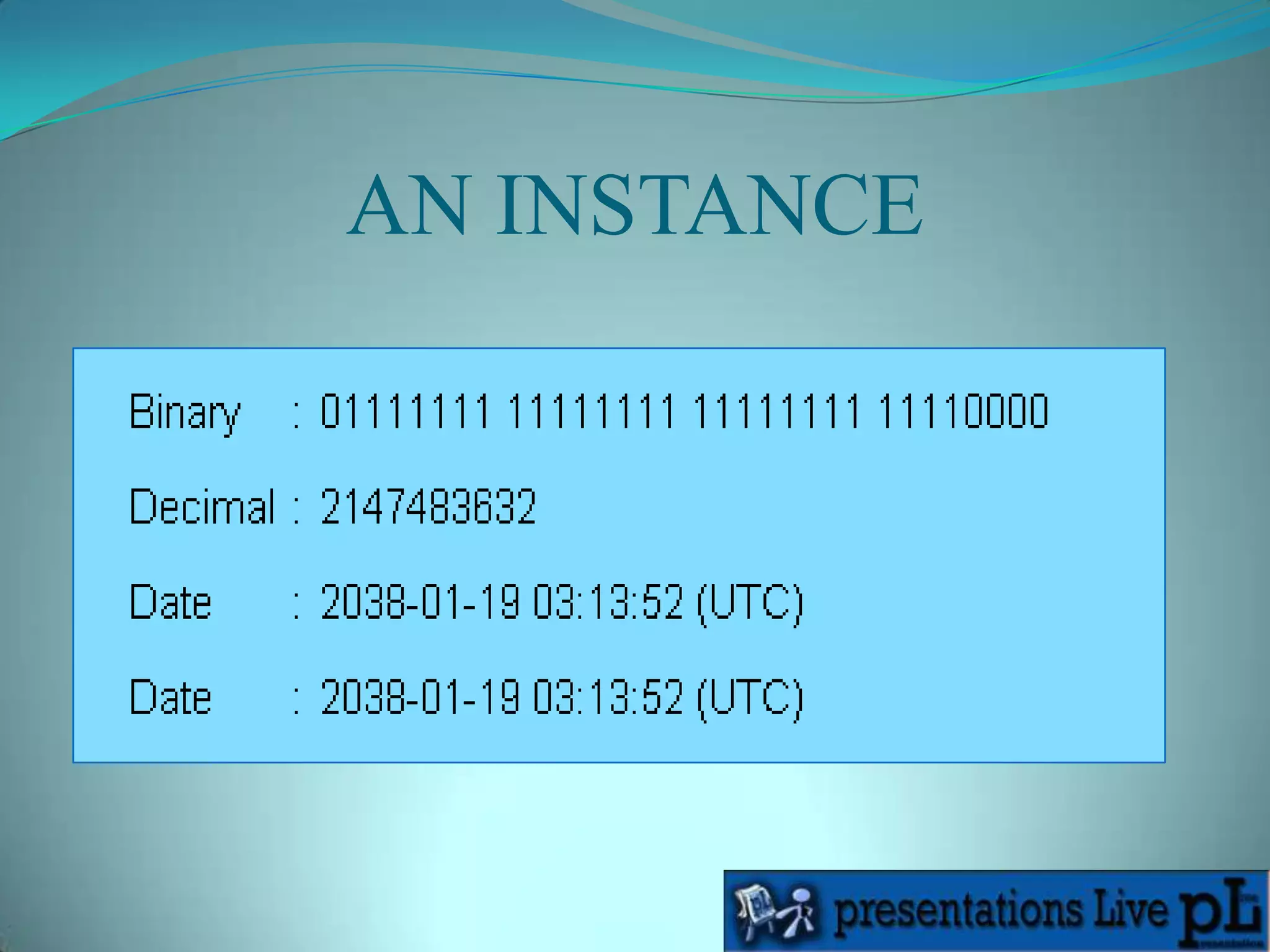
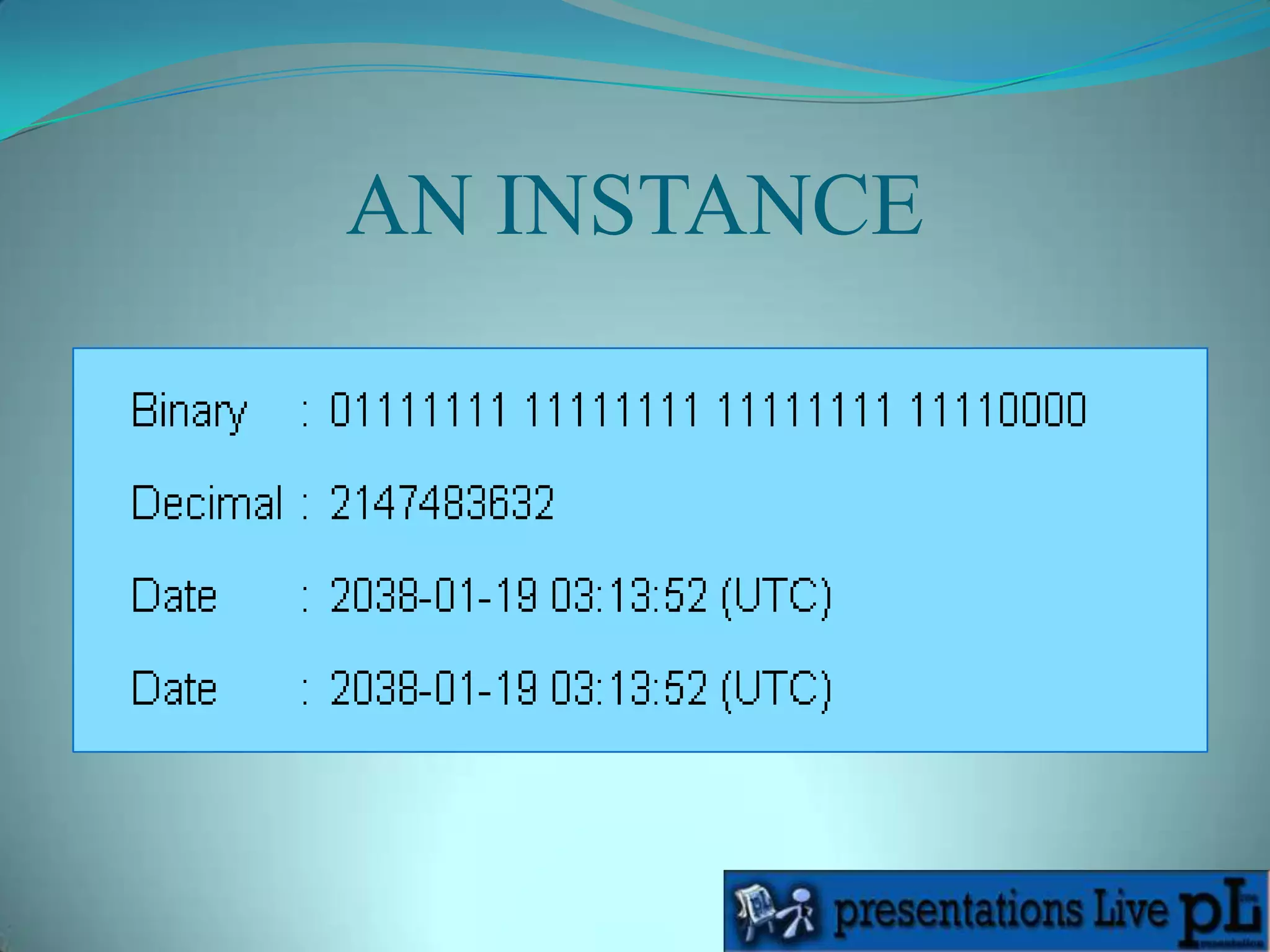
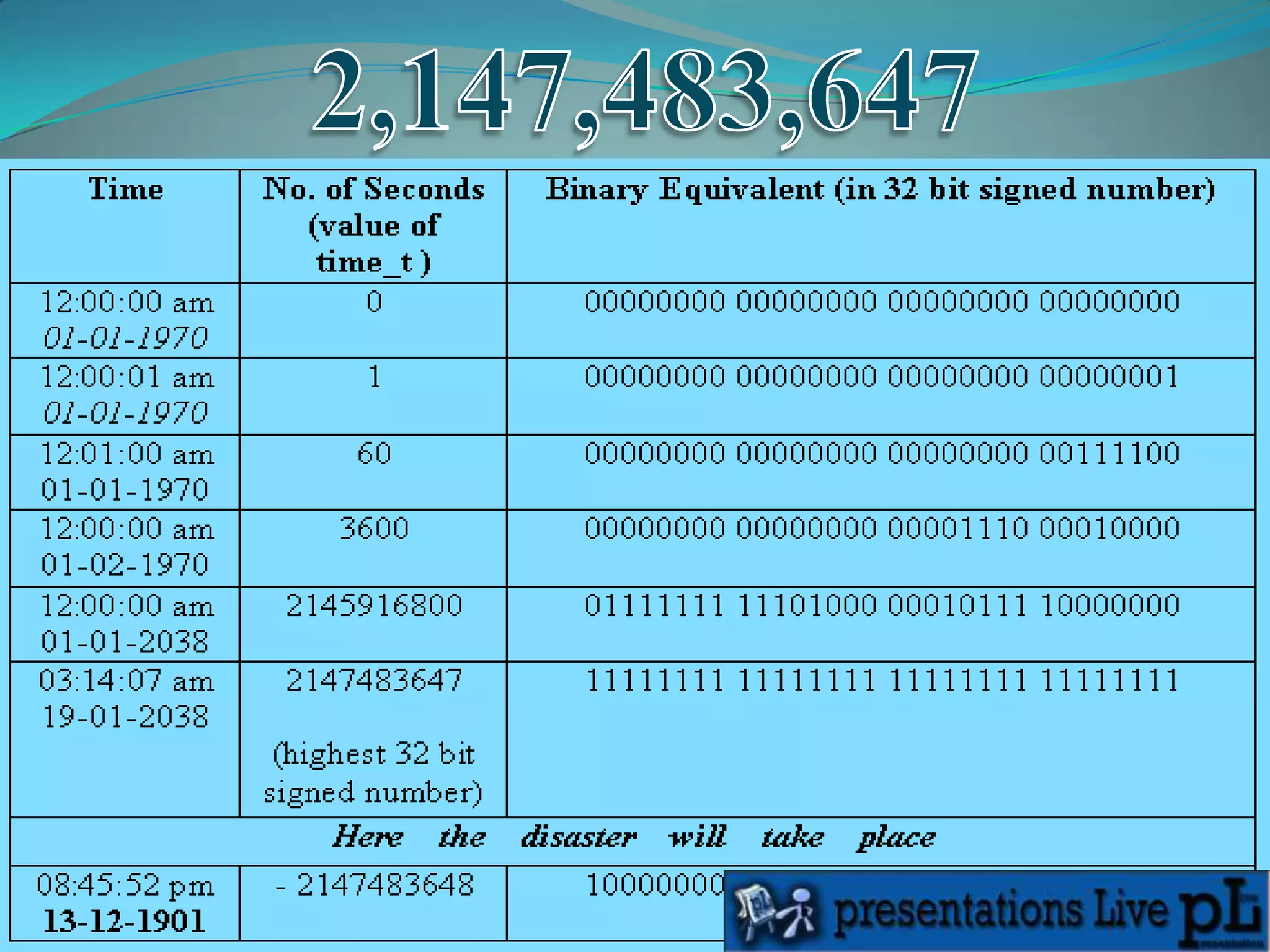
The Y2K38 problem refers to an issue that will occur in systems that store time as a 32-bit signed integer representing seconds since January 1st, 1970. This will overflow on January 19th, 2038 when the number becomes too large for 32 bits. After this point, times will wrap around and be interpreted as dates in 1901 instead of future dates, causing systems to fail. The solution is to update systems to use 64-bit integers or unsigned 32-bit integers to store time and avoid this overflow.