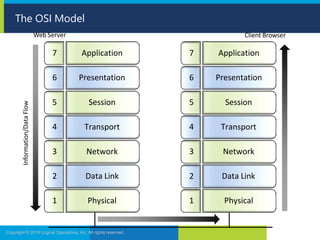
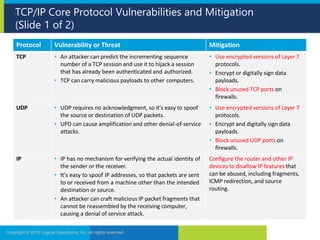
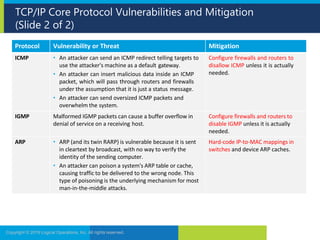
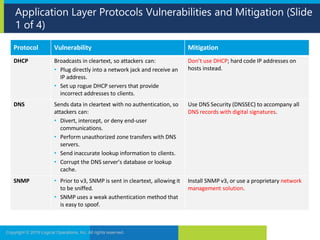
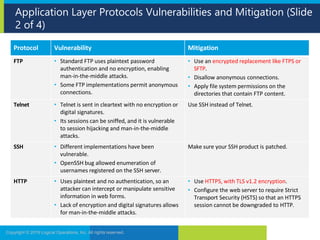
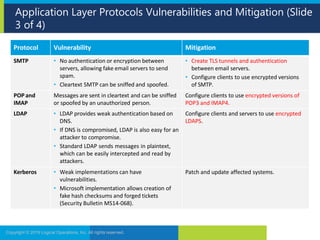
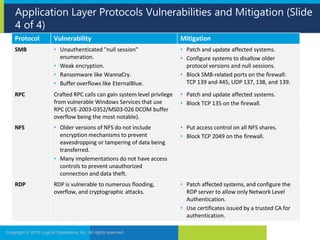
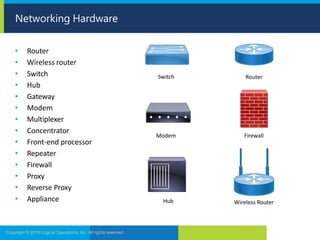
The document discusses network security and provides recommendations for securing various network components and protocols. It covers securing routers, endpoints, physical network devices, and wireless networks. It also describes common network attack vectors and vulnerabilities in protocols like TCP/IP, DNS, and SMB. Recommendations include using encryption, patching systems, firewalls, hardening devices, and disabling unneeded services.