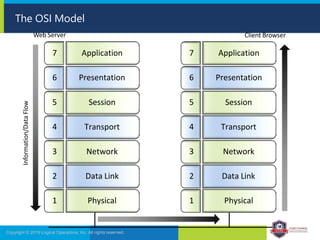
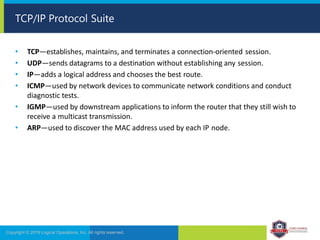
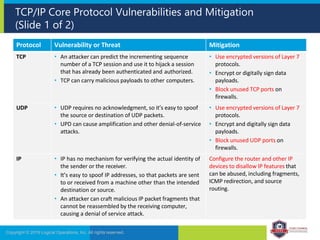
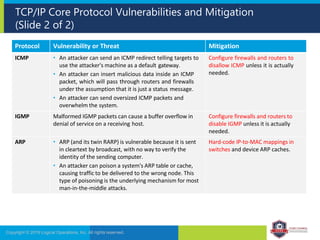
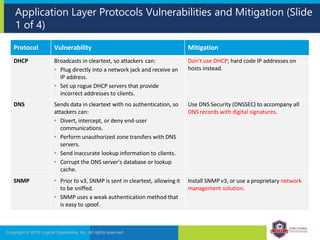
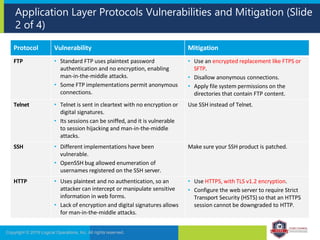
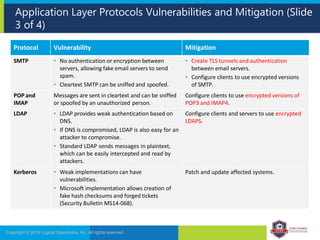
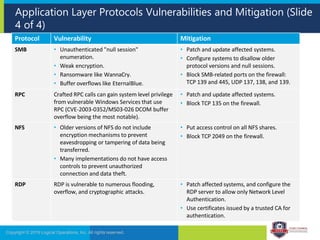
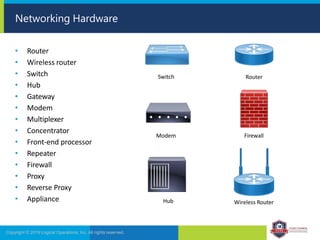
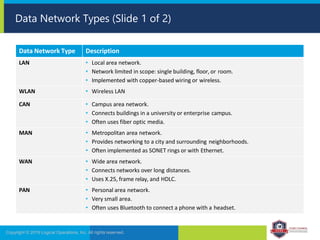
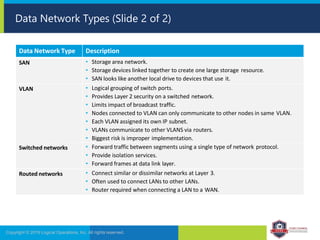
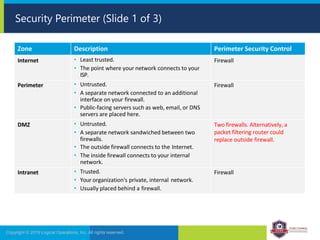
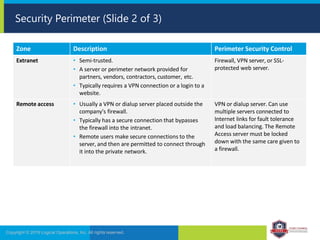
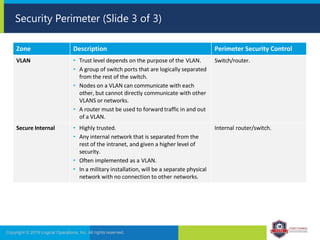
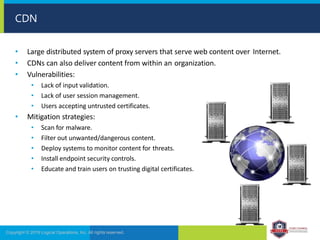
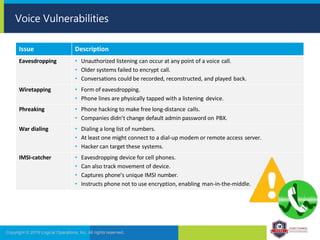
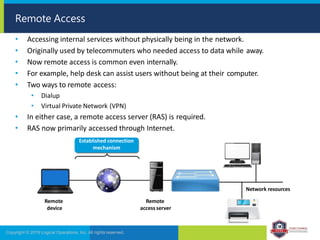
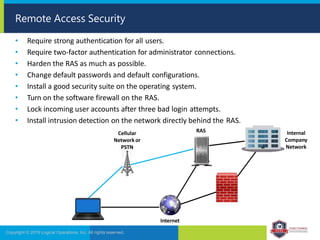
The document provides an overview of network security concepts and protocols. It discusses vulnerabilities in common network protocols like TCP, IP, and application layer protocols. It also summarizes network encryption protocols, wireless security protocols, different types of computer networks, and vulnerabilities in network routing hardware. The document is an educational resource for understanding essential network and communication security topics.