The document discusses several topics relating to cyber security foundations:
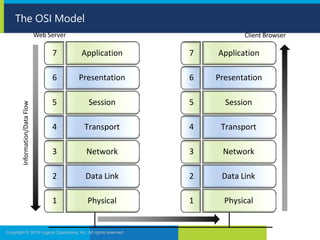
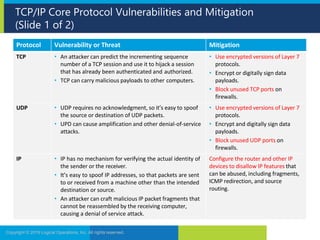
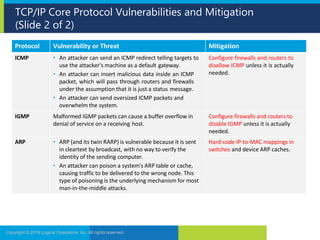
1. It outlines various network security concepts like the OSI model and vulnerabilities in core TCP/IP protocols that can be mitigated through encryption and firewall configuration.
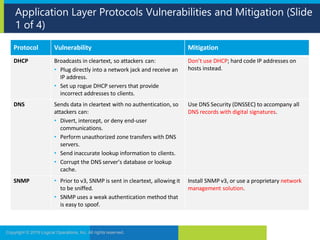
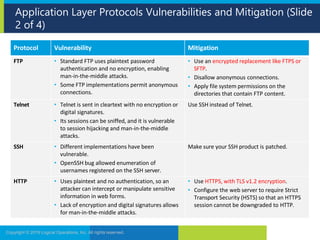
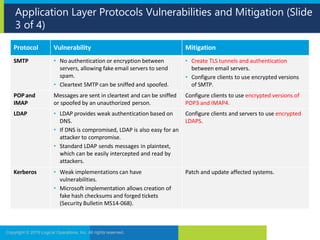
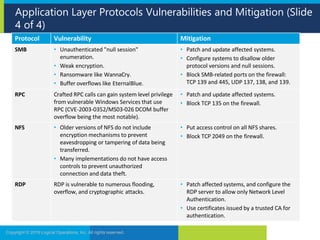
2. It then examines vulnerabilities and mitigations for several application layer protocols including DNS, HTTP, FTP and wireless protocols.
3. Router security best practices like access control lists and strong authentication are presented to prevent attacks like man-in-the-middle.
4. Endpoint security solutions using devices like firewalls, antivirus and encryption are recommended to secure mobile devices connecting to the network.
5. Finally, it stresses the importance of physical security for network devices through locking,