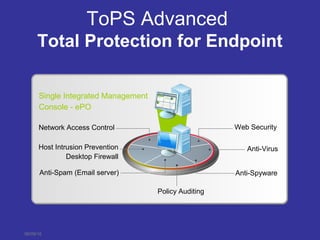
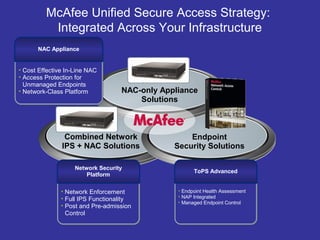
This document discusses Network Access Control (NAC) and how it works with other McAfee products to secure network access. NAC checks systems for health compliance against policies before and after network admission. It works with Microsoft NAP and McAfee NSP to enforce compliance for both managed and unmanaged systems. NAC is integrated into the McAfee ePolicy Orchestrator console and provides a unified way to control network access and security across endpoints, appliances, and network devices.