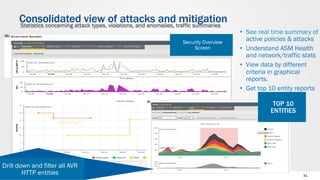
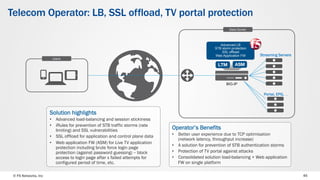
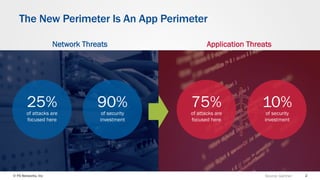
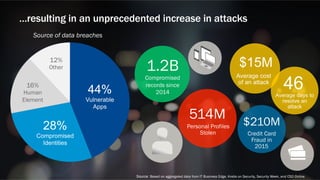
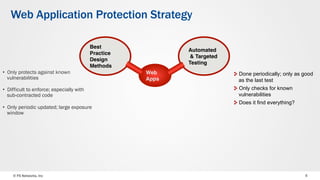
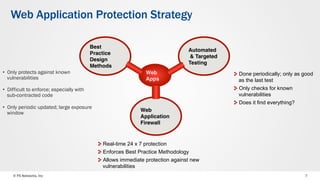
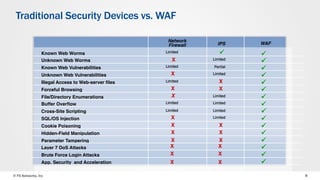
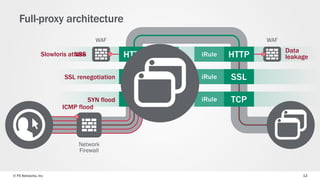
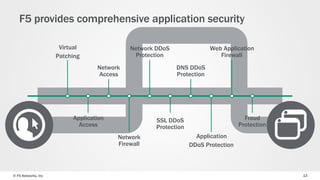
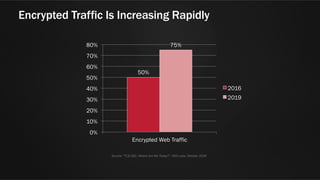
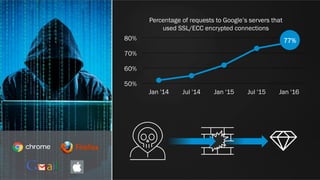
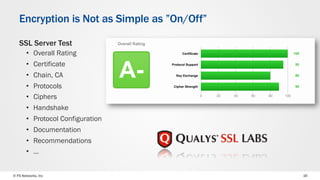
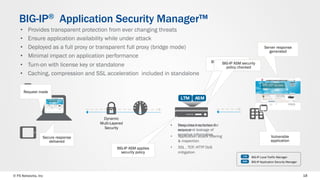
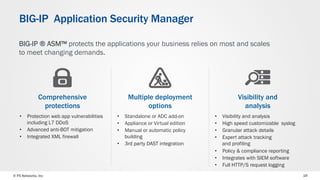
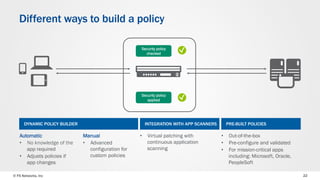
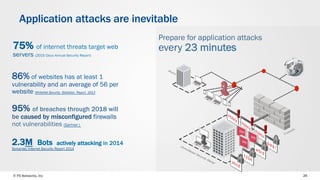
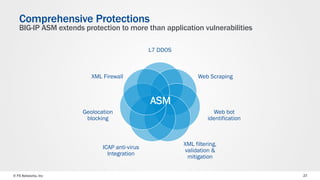
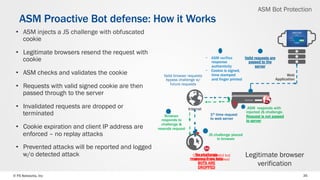
The document discusses web application security and the F5 BIG-IP Application Security Manager (ASM). It notes that most attacks are now targeted at web applications rather than networks. It then provides an overview of common web application attacks that ASM can protect against. The document discusses how ASM uses a positive security model to provide implicit protection against both known and unknown attacks. It also outlines the various deployment options and protections that ASM provides, such as bot detection, DDoS mitigation, and web application firewall capabilities.













![© F5 Networks, Inc 36
• iRules commands enable customized
action on bots detected
• Launches against Proactive Bot Defense
DoS events
• Provides the control needed to ensure
accuracy of threat detection
• Use it to …
o retrieve the data processed by Bot Defense mechanism,
o query and override URL qualification,
o force logging and challenges,
o Customize an HTML redirect
iRules enhanced Bot protection
Delivers increased granularity to the bot detection process
# EXAMPLE 1: Bypassing enforcement on URL pattern
when BOTDEFENSE_ACTION {
if {[HTTP::uri] starts_with "/t/"} {
log local0. "bypassing enforcement for URI [HTTP::uri]"
set res [BOTDEFENSE::action allow]
log local0. "set action to allow, result "$res""
log local0. "resulting action [BOTDEFENSE::action]
reason "[BOTDEFENSE::reason]""
}
}
# EXAMPLE 2: Instead of blocking the request with TCP RST,
respond with a
# blocking-page
when BOTDEFENSE_ACTION {
if {[BOTDEFENSE::action] eq "tcp_rst"} {
# if the custom_response action fails, the tcp_rst
action will remain,
# so we don't need to check the return string
in this case
BOTDEFENSE::action custom_response "sorryni am
blocking youn"
}
}
# EXAMPLE 3: Force the browser_challenge to be sent to the
client on the login
# page, even if the cookie is valid (may be used to force the
renewal of the
# Bot Defense cookie)
when BOTDEFENSE_ACTION {
if { ([HTTP::uri] eq "/t/login.php") &&
([BOTDEFENSE::action] eq "allow") &&
(not ([BOTDEFENSE::reason] starts_with "passed
browser challenge"))} {
BOTDEFENSE::action browser_challenge
}
}
ASM Bot Protection](https://image.slidesharecdn.com/f5applicationsecurityseminar-170518090226/85/F5-Web-Application-Security-36-320.jpg)