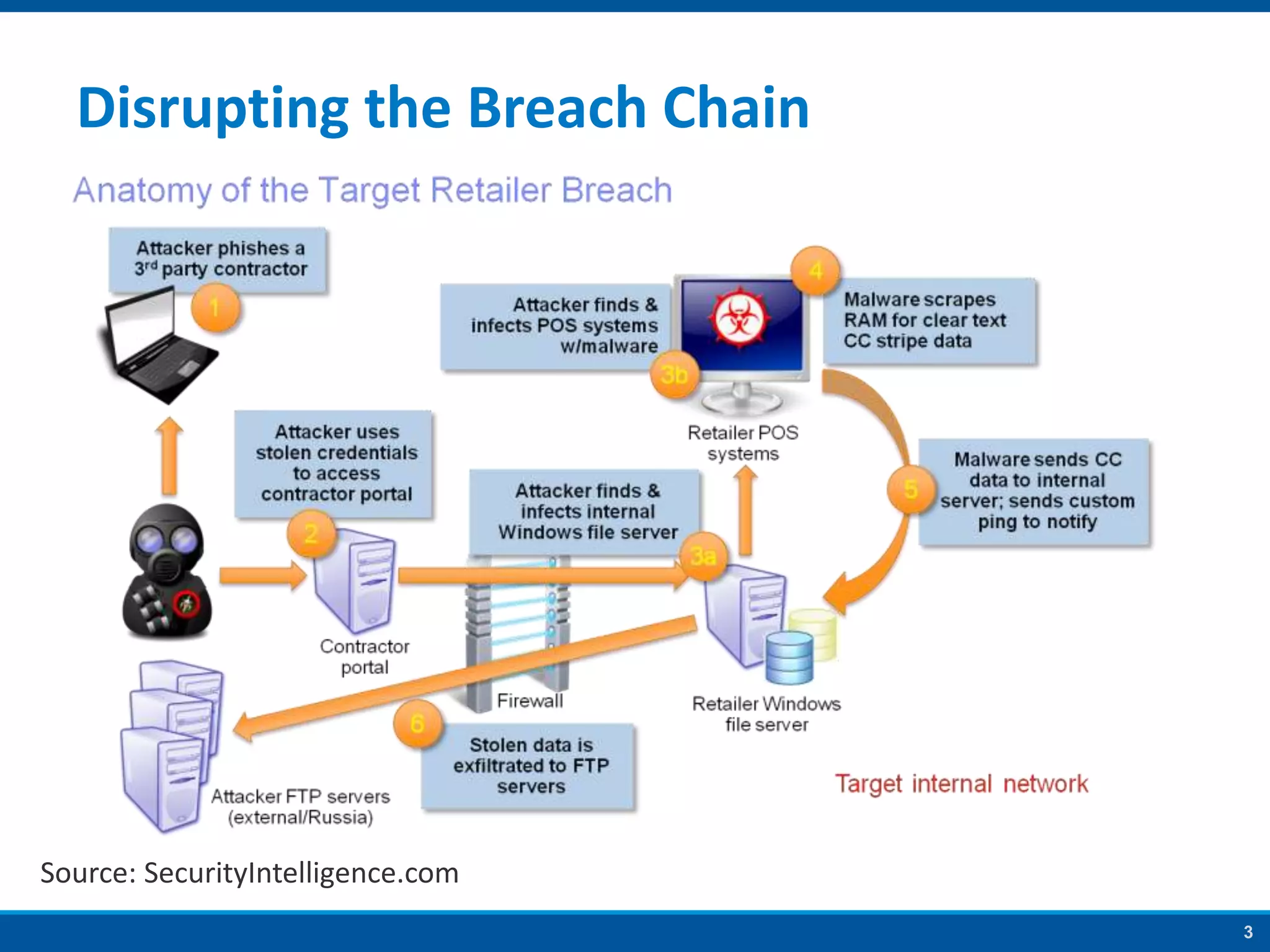
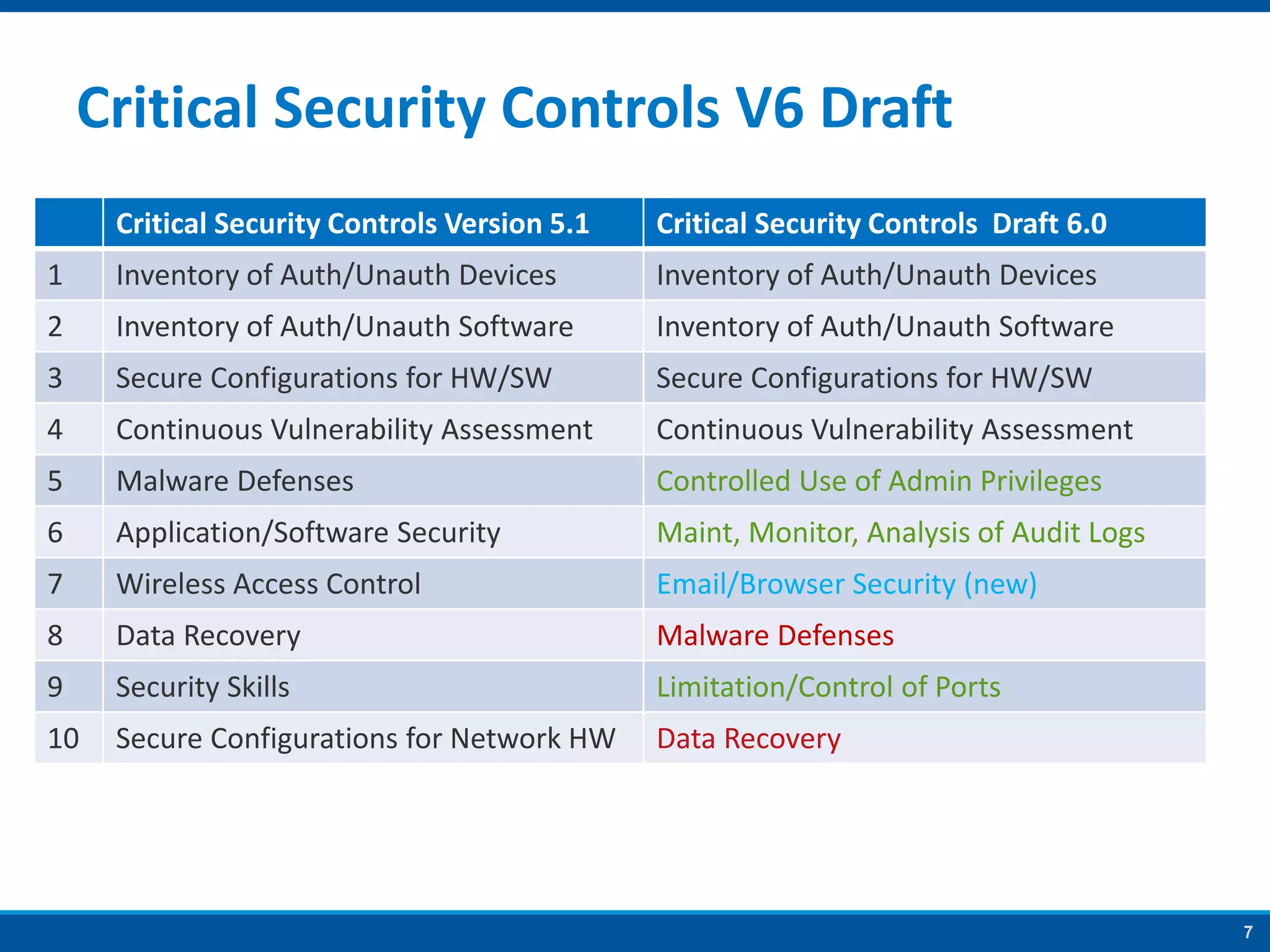
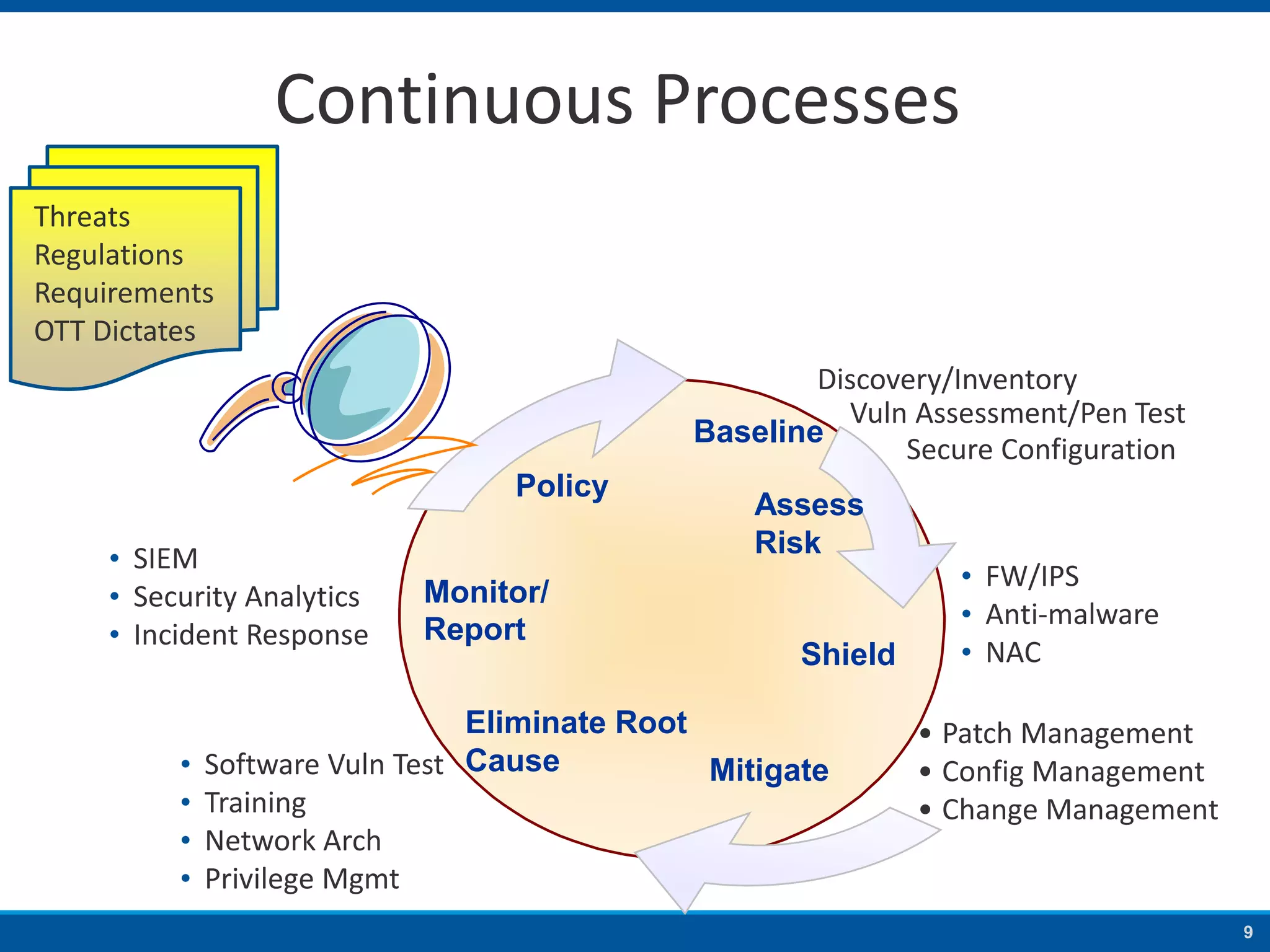
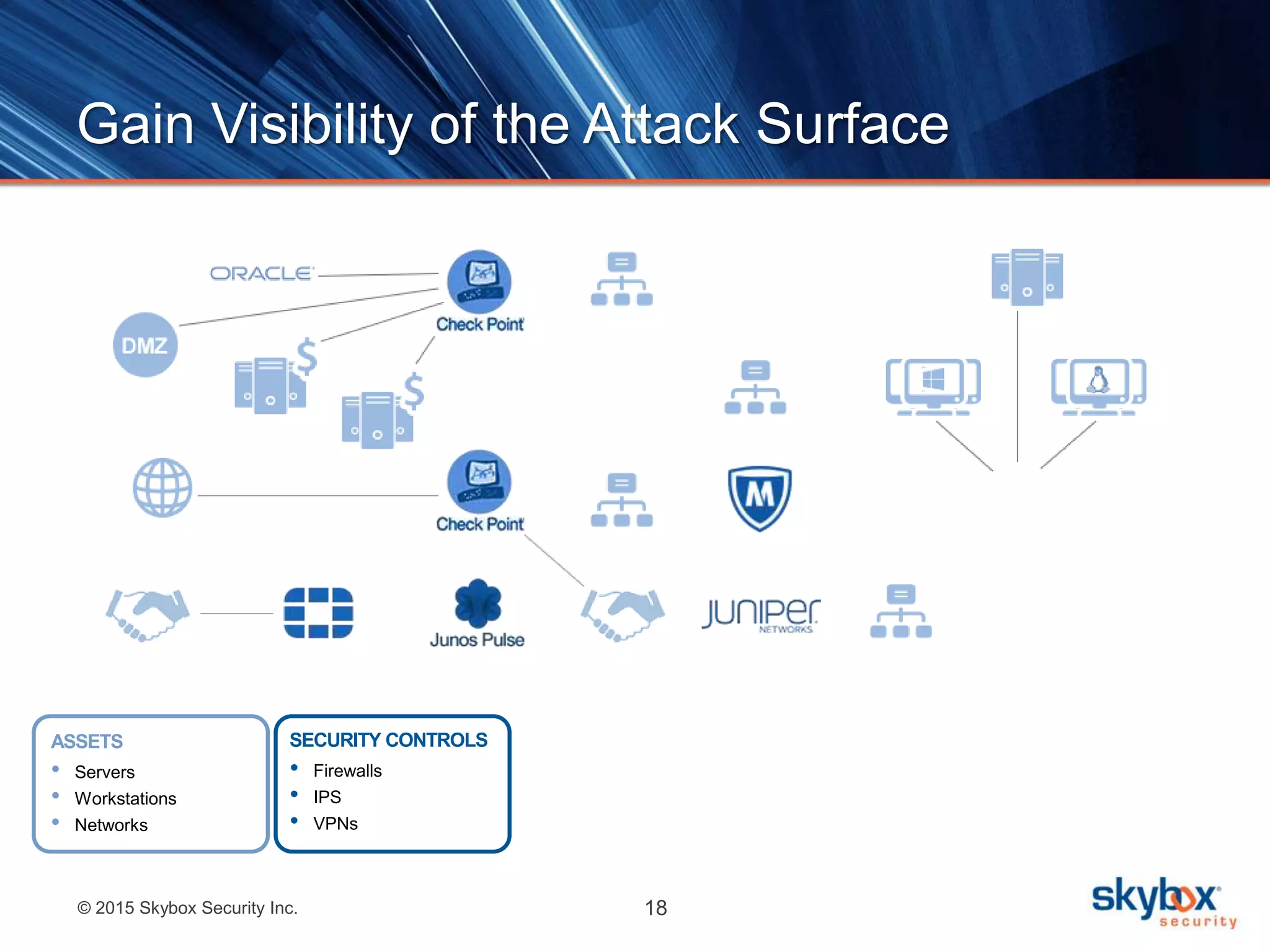
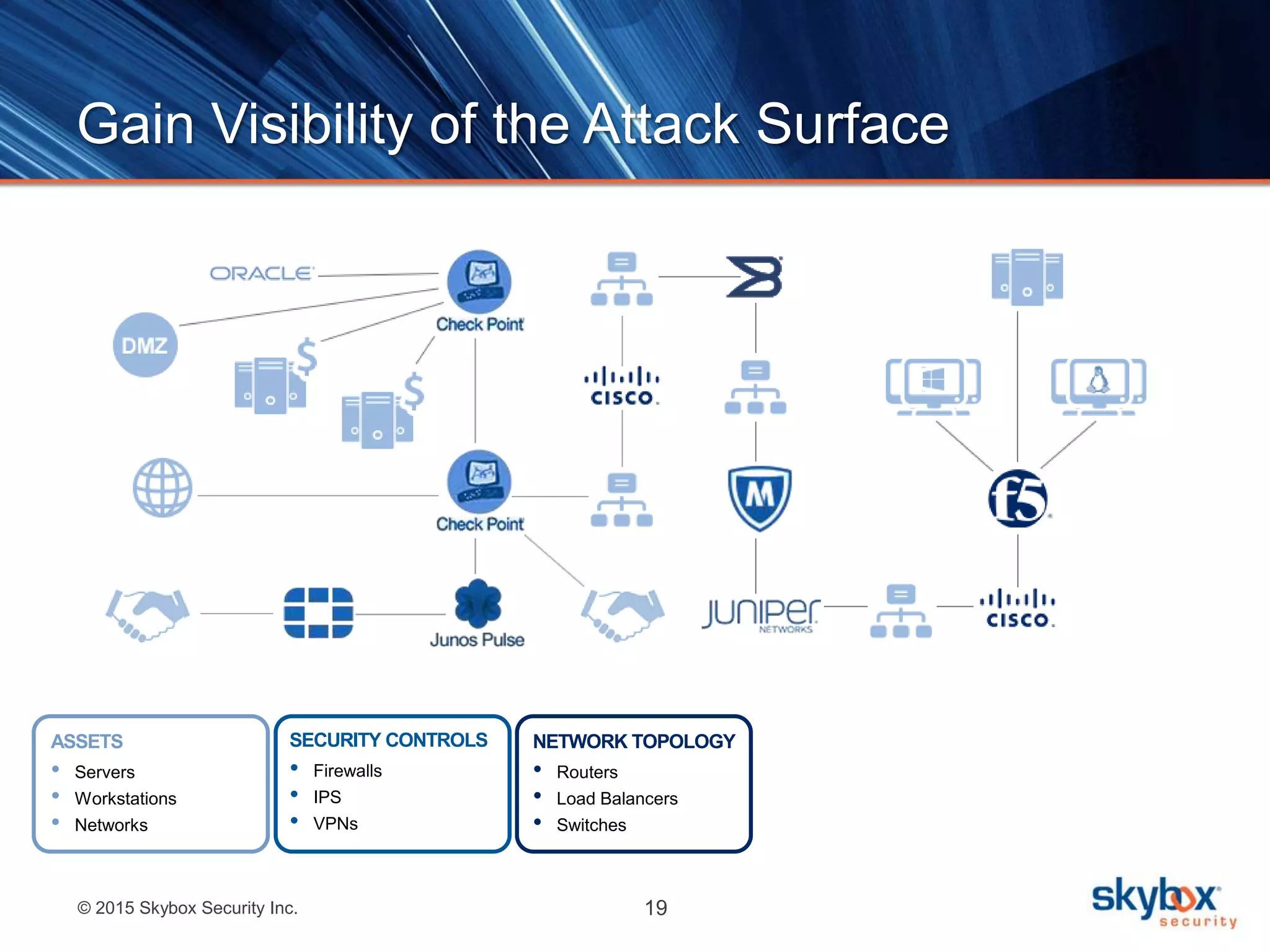
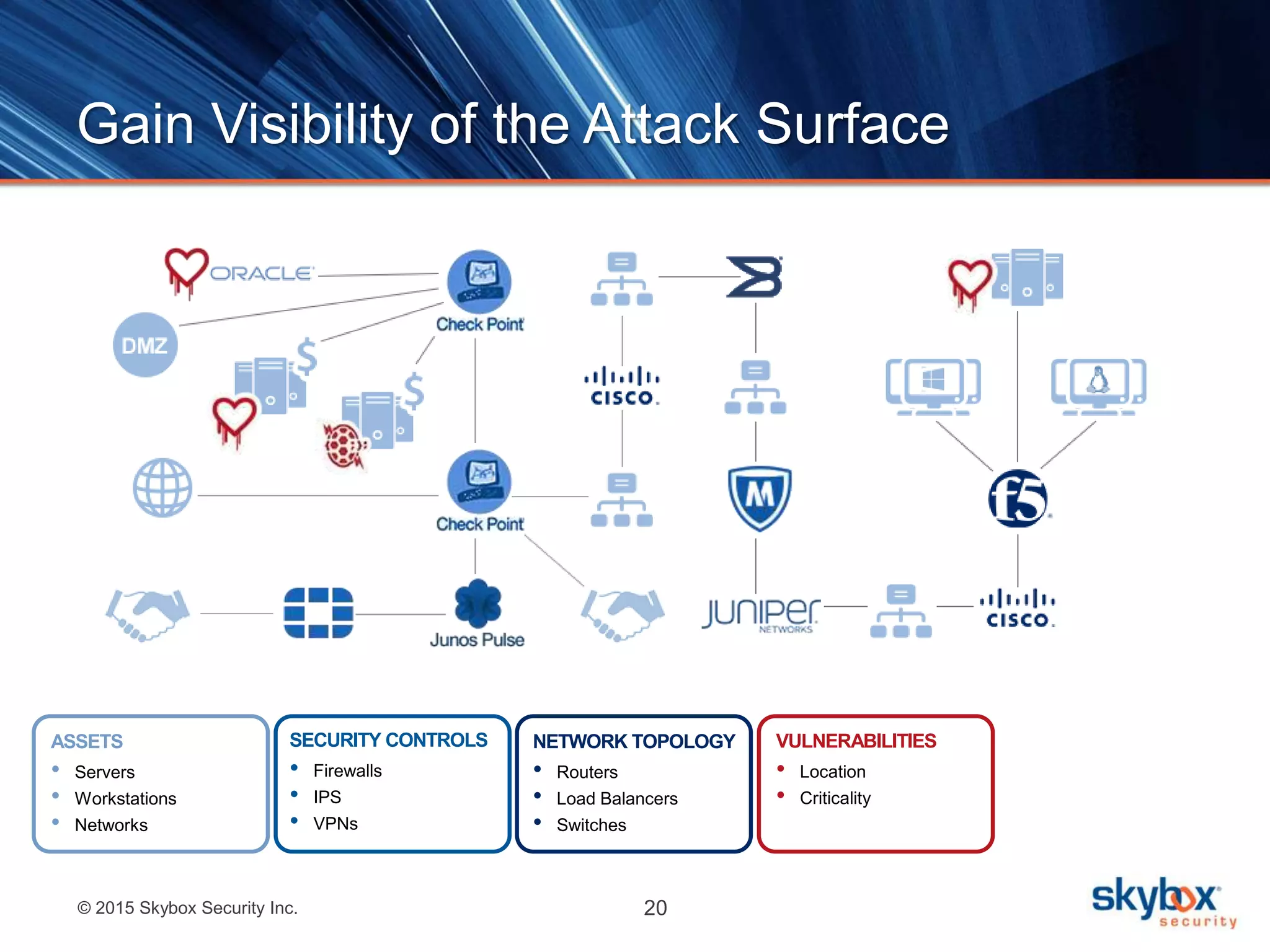
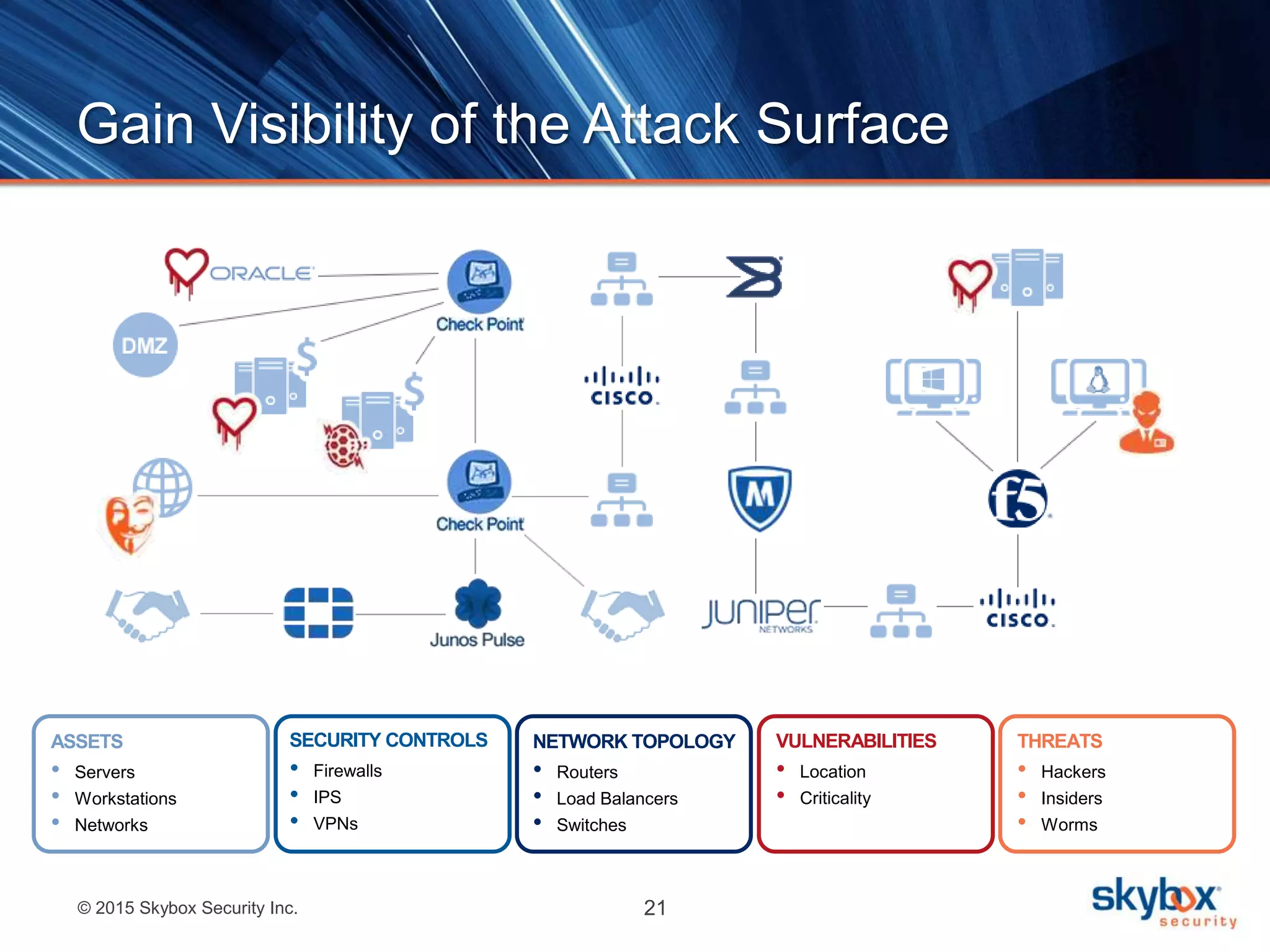
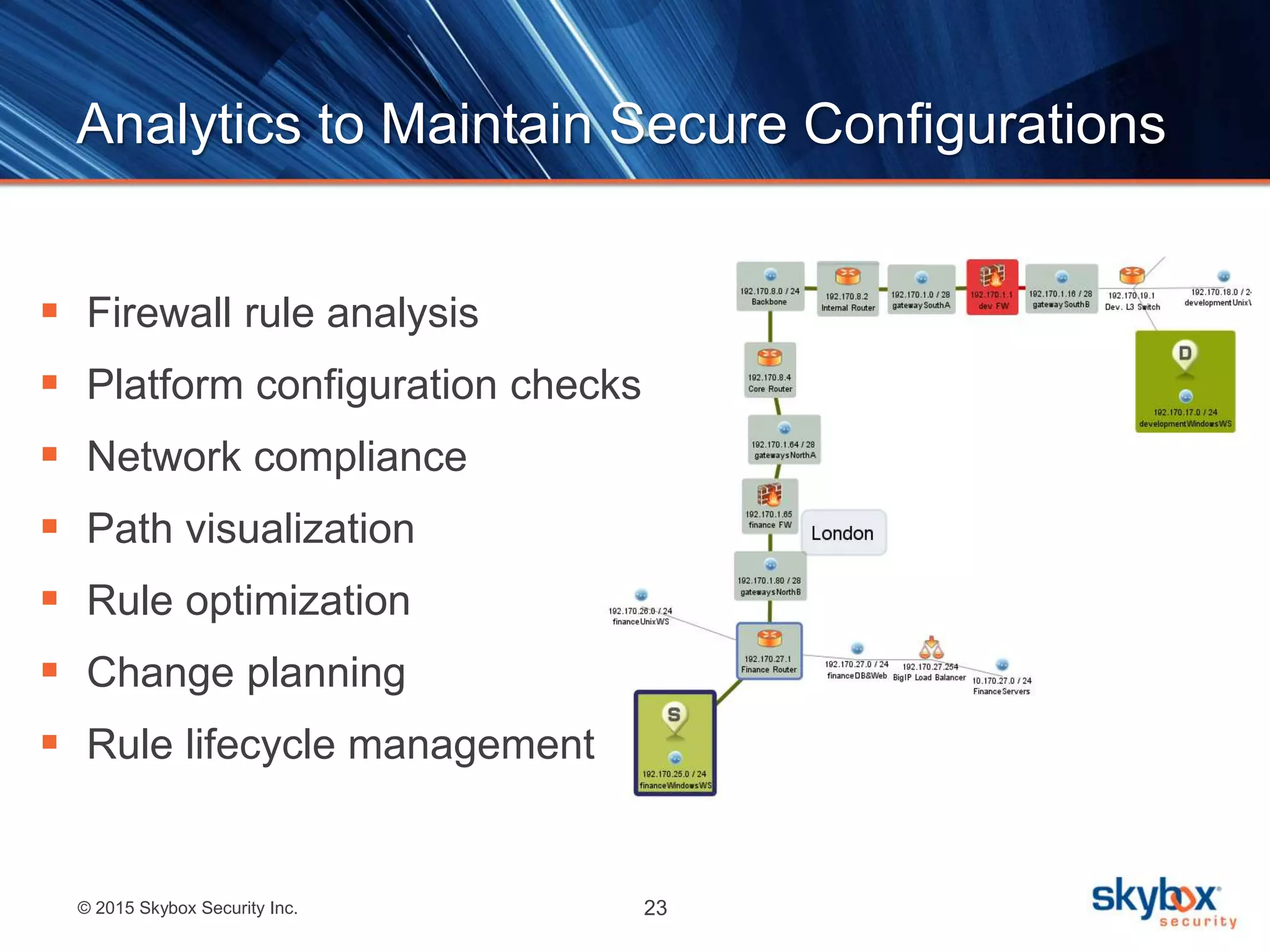
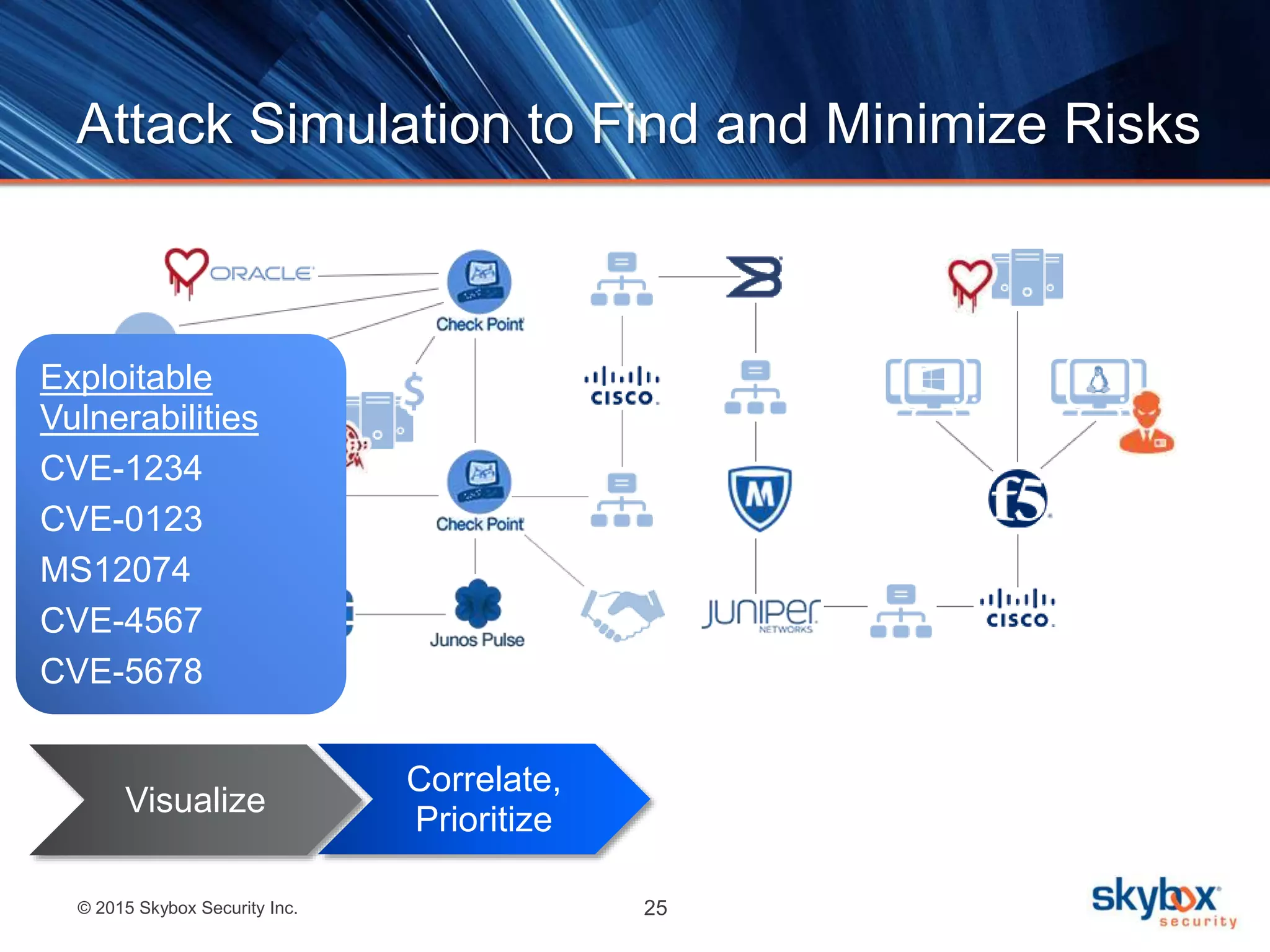
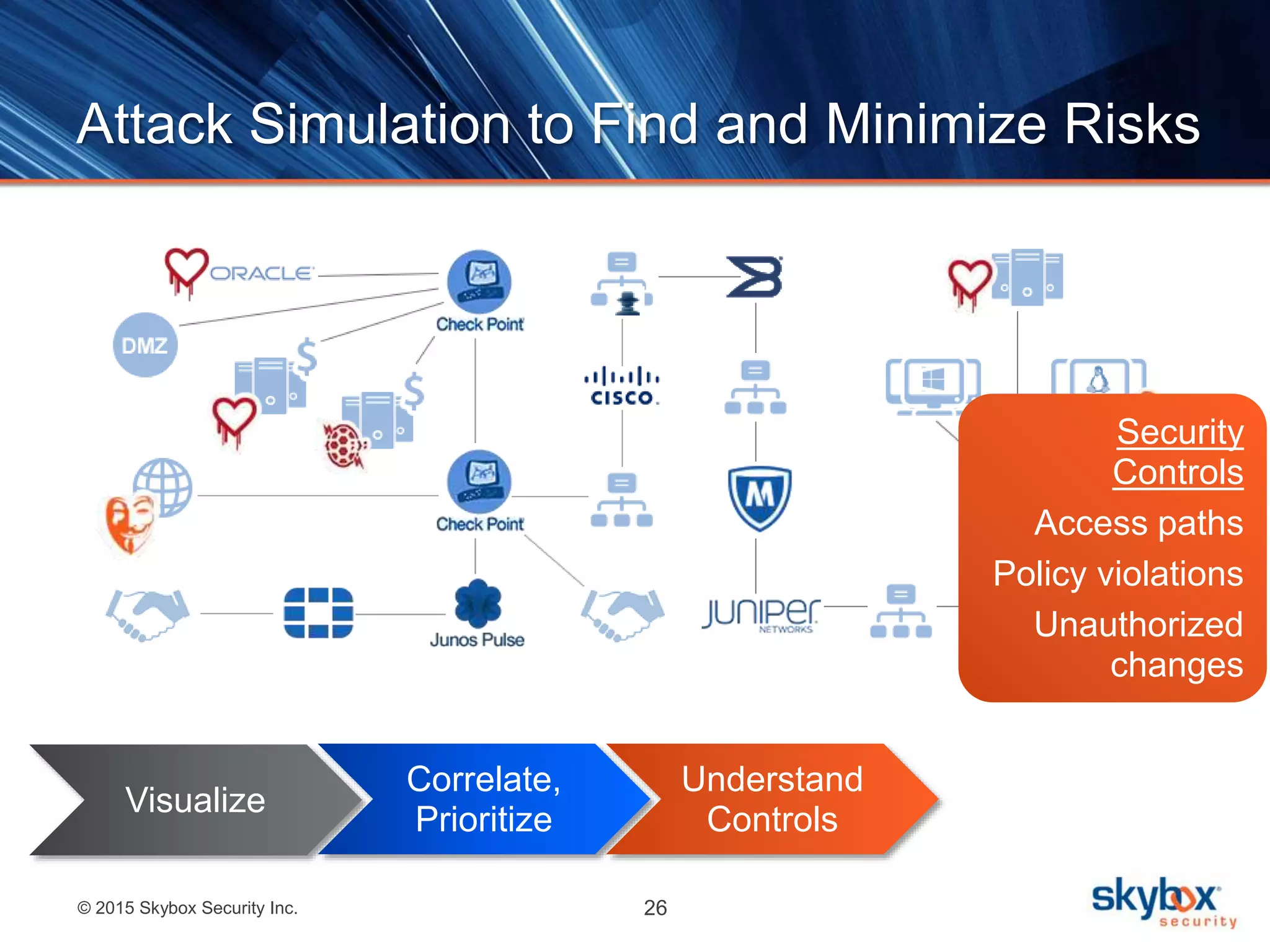
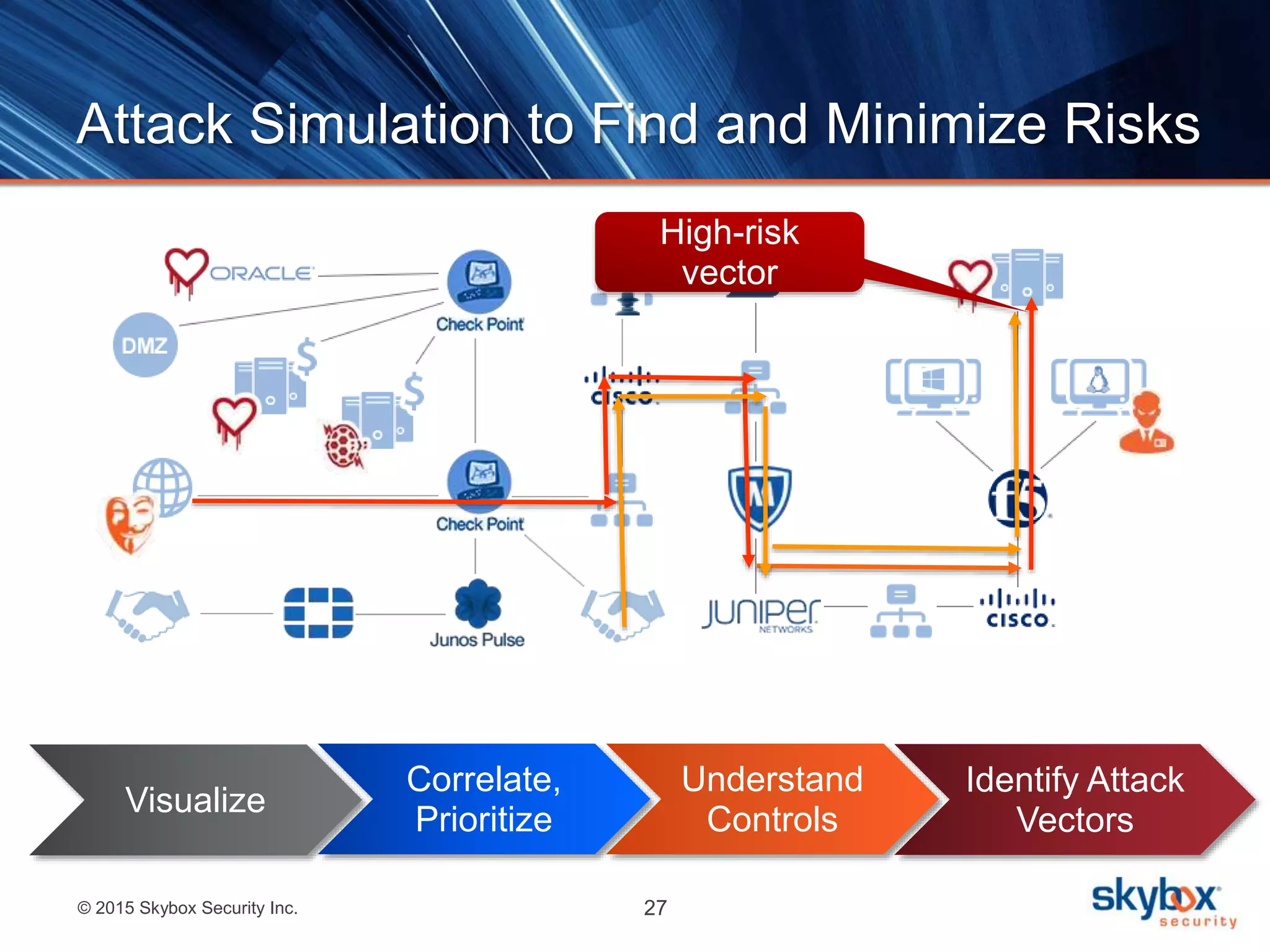
The document discusses strategies to address SANS Critical Controls 10 and 11, focusing on secure network configurations and management of services. It emphasizes the importance of effective security zones, preventing breaches, and maintaining rigorous management processes to reduce vulnerabilities. The document also provides historical context for critical security controls and highlights challenges associated with implementing these controls in complex network environments.