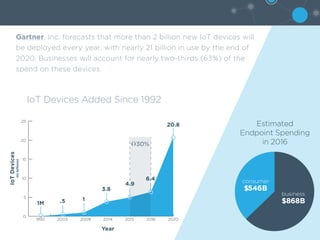
1) The number of IoT devices is expected to grow dramatically from around 6 billion in 2015 to over 21 billion by 2020, with businesses accounting for 63% of spending on these devices.
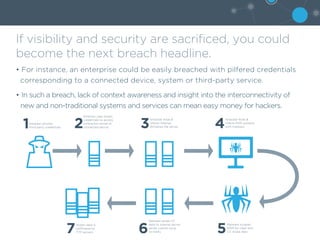
2) As IoT devices proliferate, increased visibility into these devices through profiling, monitoring, and flexible enforcement is needed to secure networks from threats. Network Access Control (NAC) can provide this visibility and control to protect enterprises.
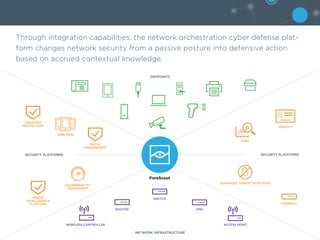
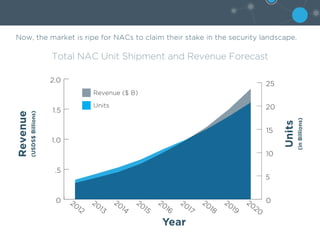
3) NAC provides essential context awareness and control capabilities to block, quarantine, or redirect compromised endpoints, and its integration abilities allow for improved network security orchestration across multiple environments including cloud and data centers.