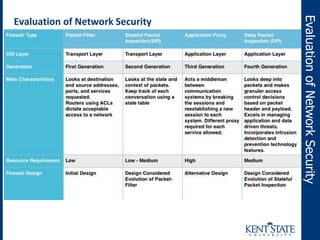
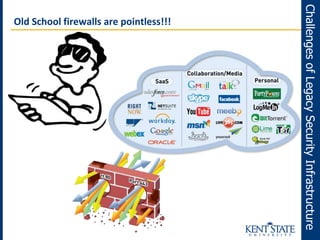
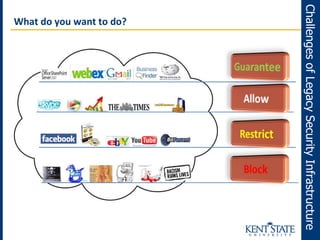
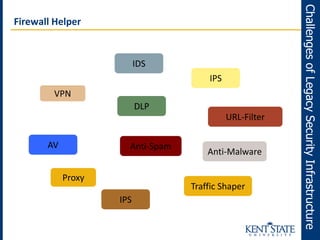
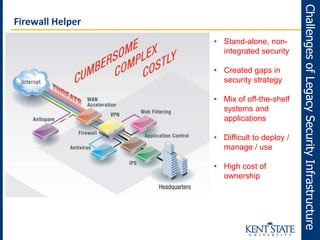
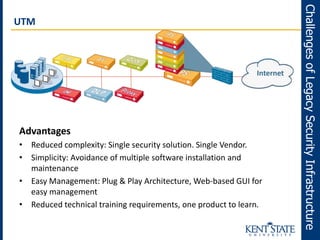
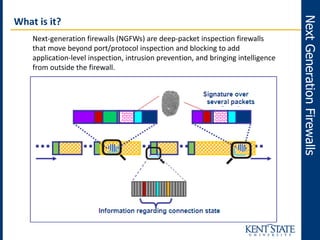
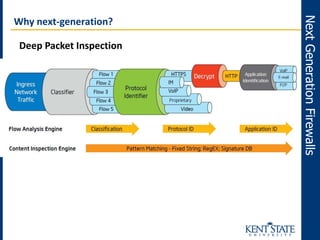
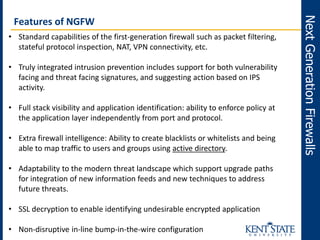
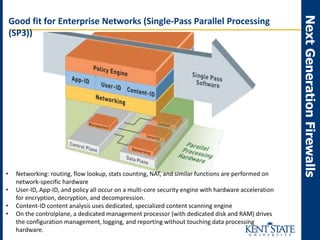
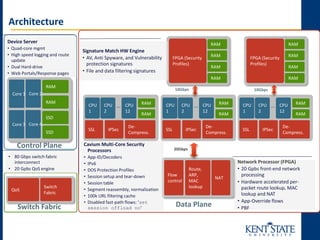
The document discusses the transition to next-generation firewalls (NGFWs), emphasizing their enhanced capabilities over traditional firewalls by integrating deep packet inspection, application-level control, and unified threat management. It outlines the limitations of legacy security infrastructure and highlights the benefits of NGFWs, including improved visibility, control, and simplified management. The author provides guidance on implementing NGFWs and key considerations for defining requirements, application identification, and policy controls.