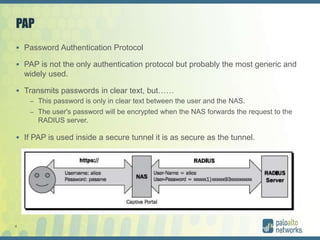
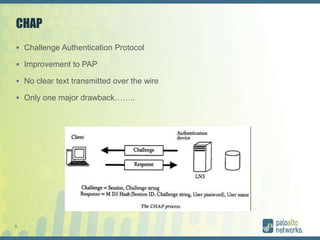
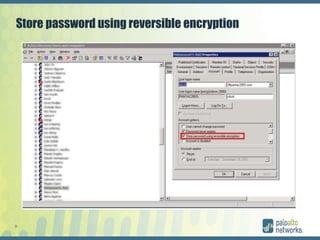
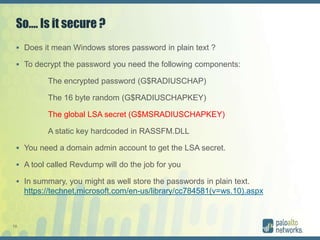
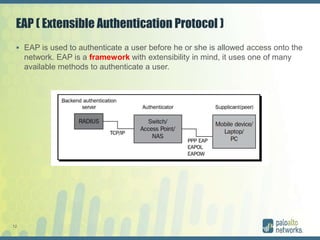
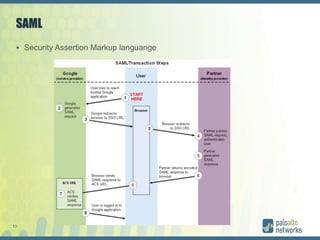
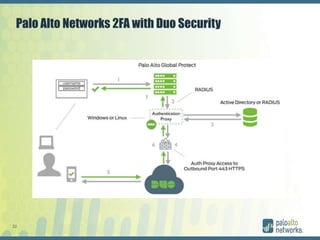
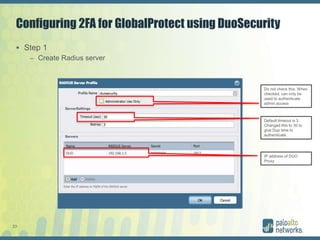
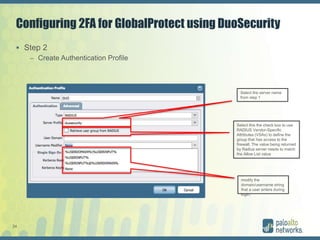
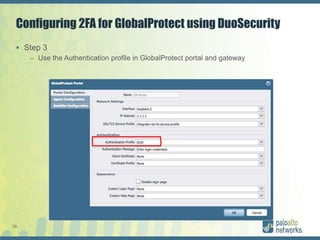
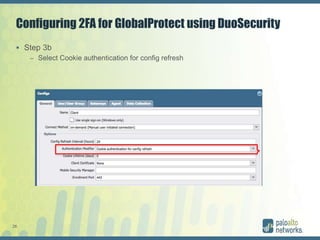
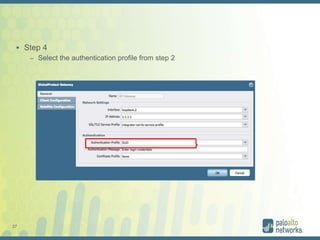
The document discusses authentication methods for Palo Alto Networks firewalls, including PAP, CHAP, MS-CHAP, EAP, SAML, and RADIUS VSA. It provides details on configuring two-factor authentication for GlobalProtect using Duo Security, including creating a RADIUS server, authentication profile, and selecting the profile for GlobalProtect portal and gateway. The document concludes with notes on a live demo of the 2FA configuration.









![28
Duo Proxy configuration
[radius_client]
host=192.168.1.5
secret=pass123
port=1812
[radius_server_auto]
ikey=---------
skey=-------------
api_host=api-0e0dfbb4.duosecurity.com
radius_ip_1=192.168.1.2
radius_secret_1=pass123
failmode=safe
factors=auto
client=radius_client
port=1817](https://image.slidesharecdn.com/paloaltonetworksauthentication-151231024358/85/Palo-Alto-Networks-authentication-28-320.jpg)


