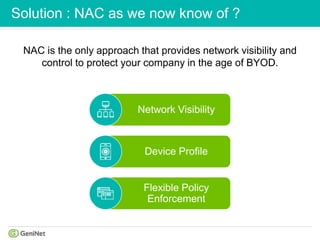
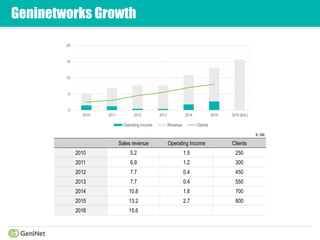
The document discusses Network Access Control (NAC) solutions for small and medium enterprises (SMEs) to gain visibility and control over devices on their networks in the age of "Bring Your Own Device" (BYOD). It introduces Genian NAC Business Edition as an affordable and easy-to-install NAC solution for SMEs to maintain an updated network inventory, block unauthorized devices, and enforce internal security policies on all connected devices. The solution addresses common problems that SMEs face with expensive and difficult to install traditional NAC solutions through an all-in-one appliance and subscription-based pricing model.