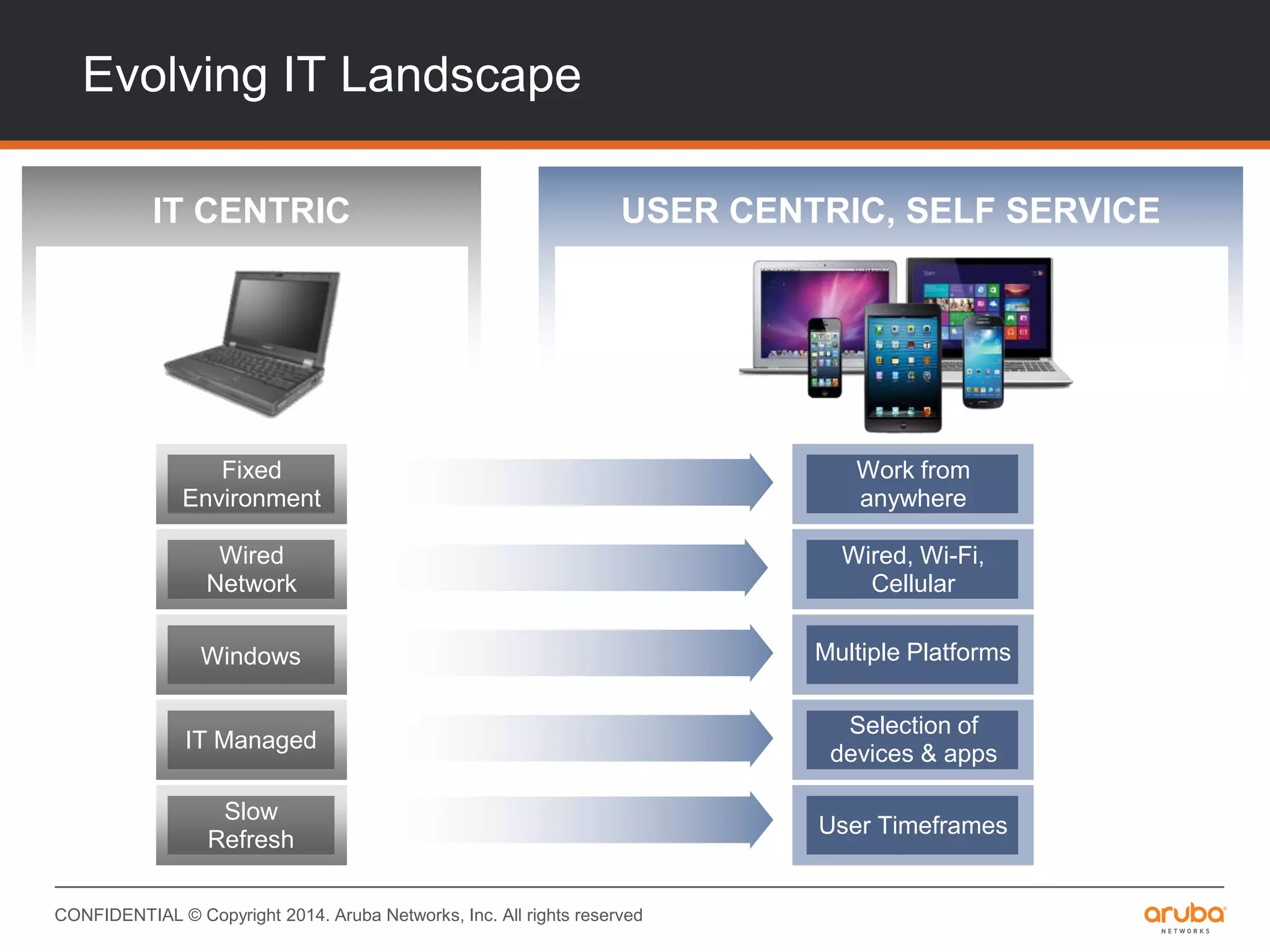
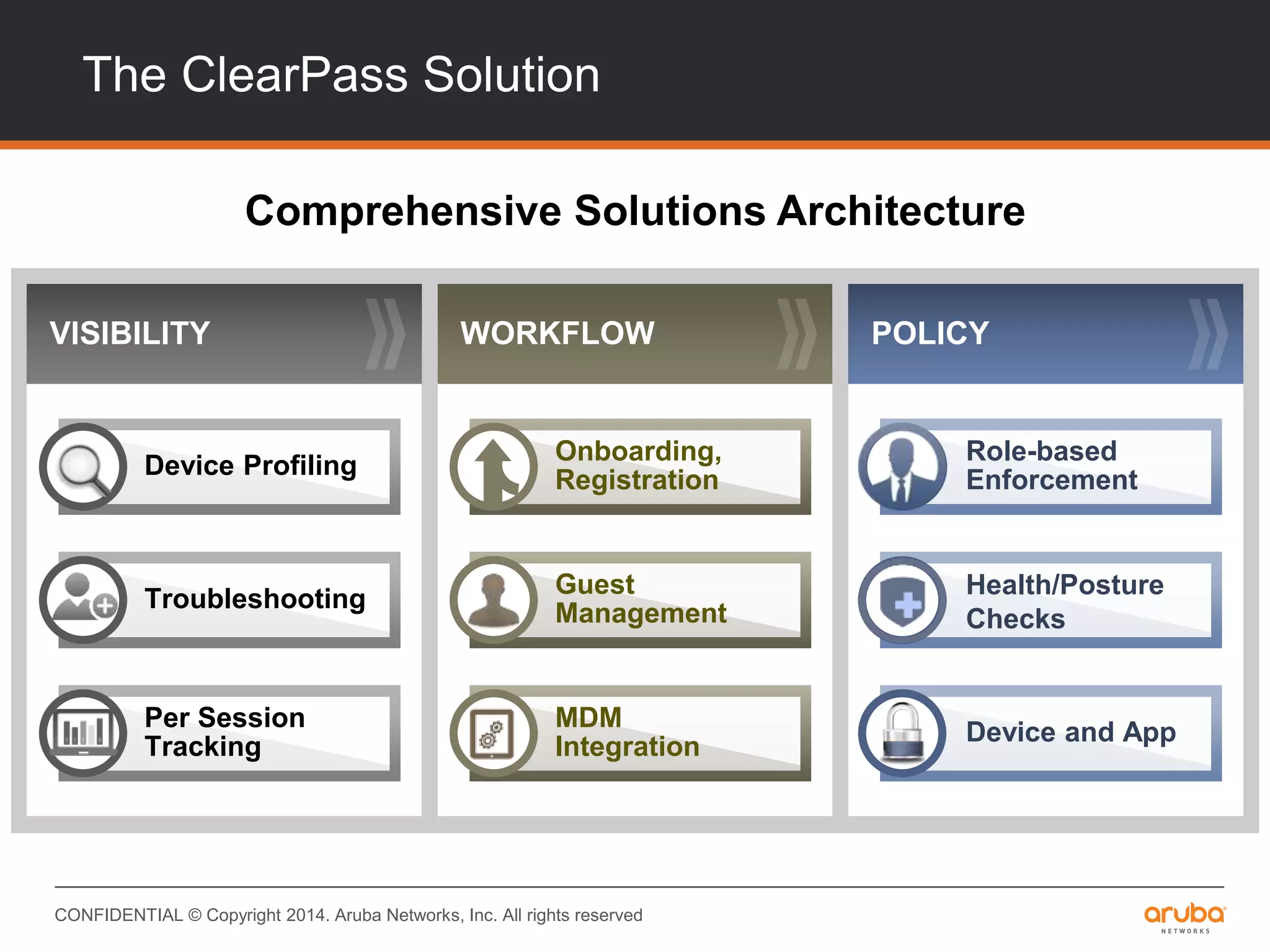
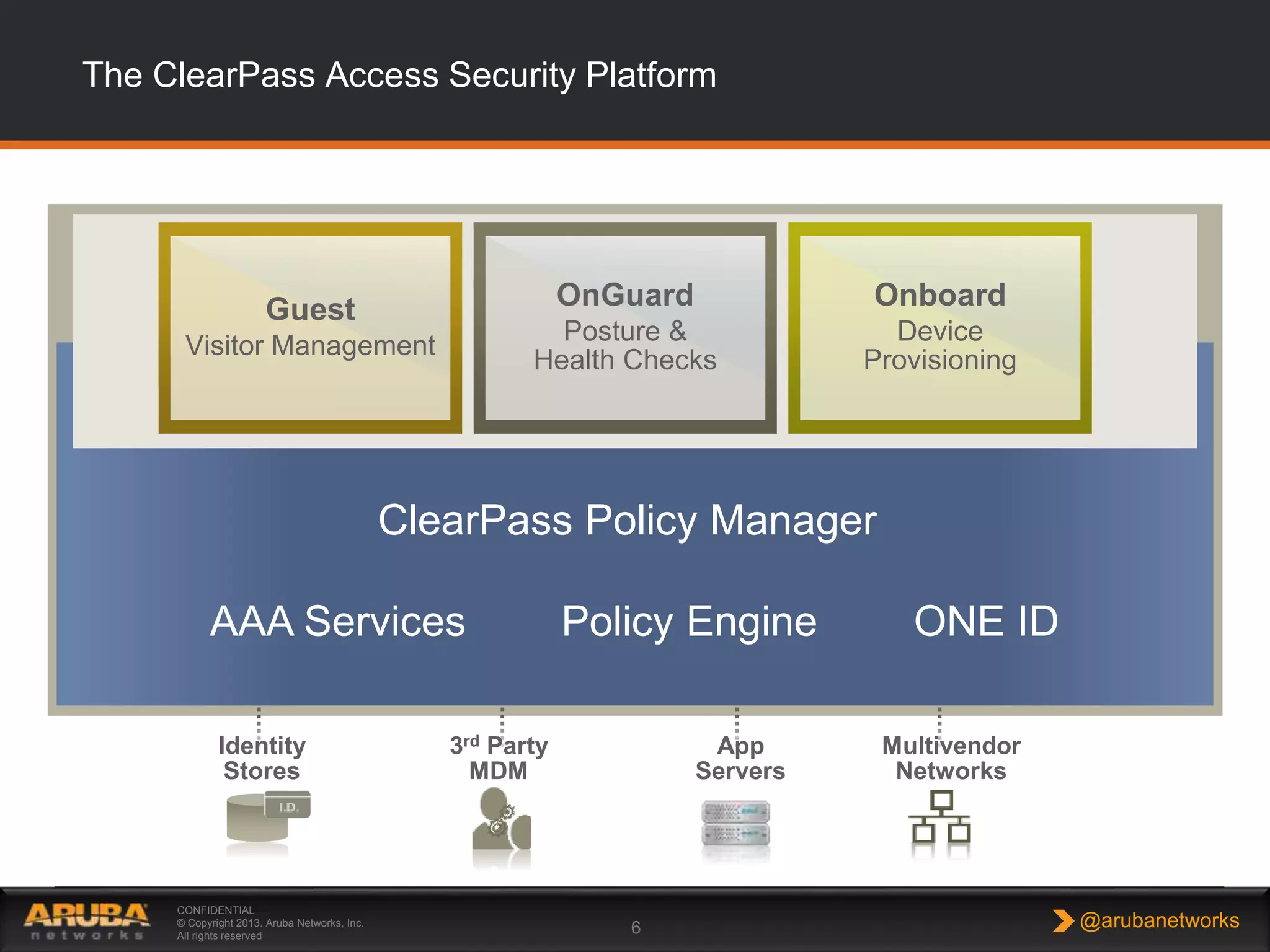
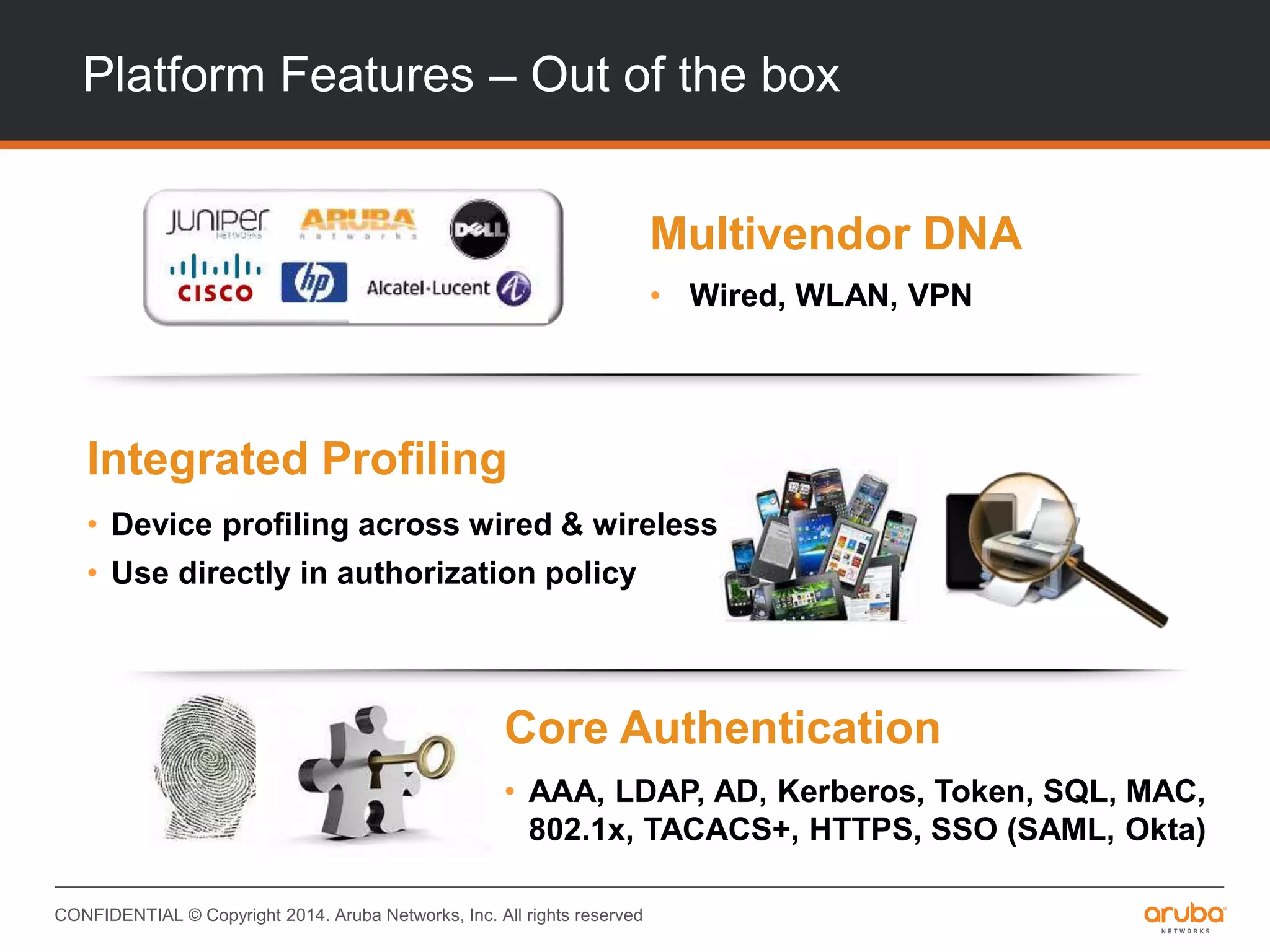
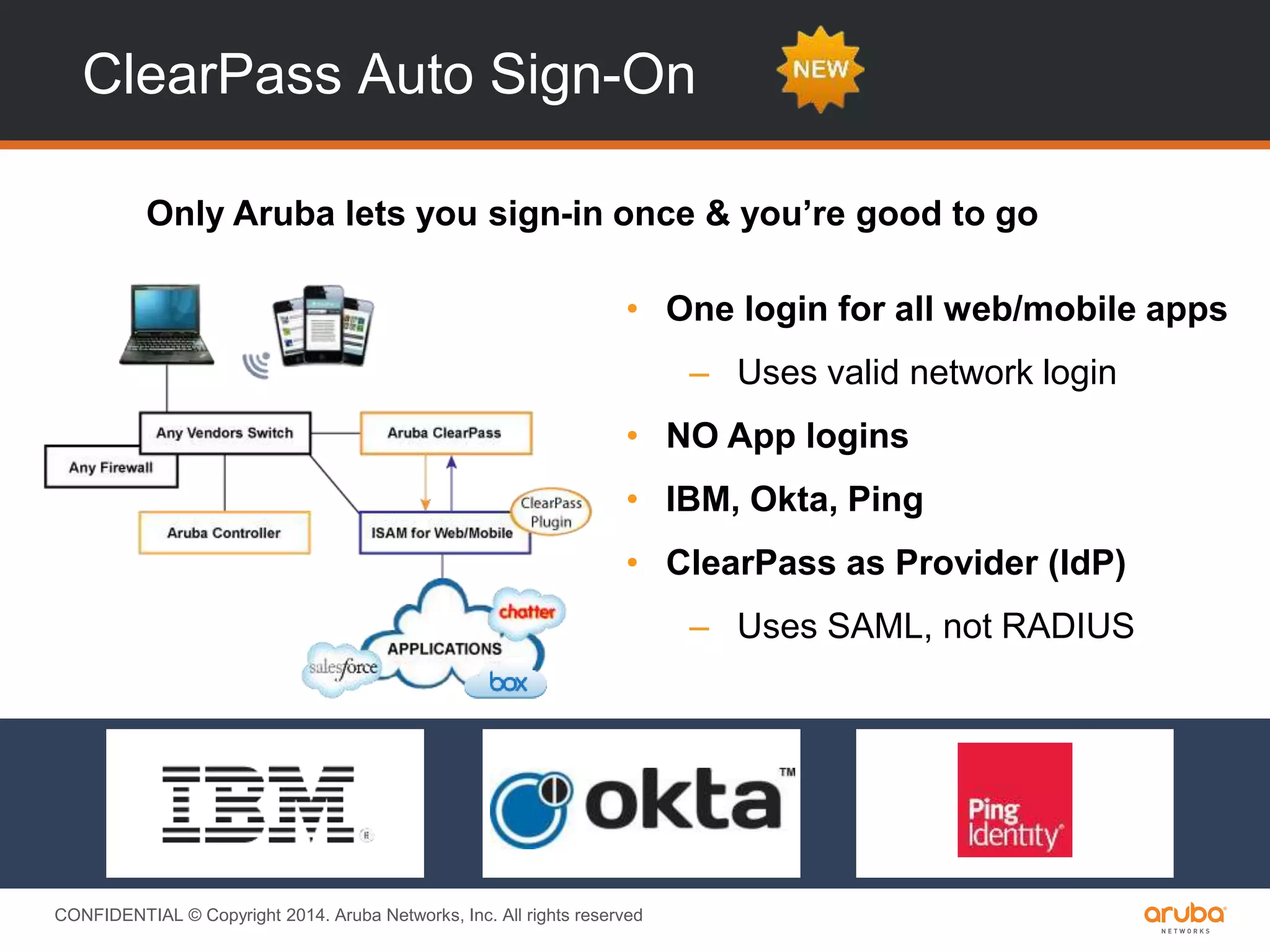
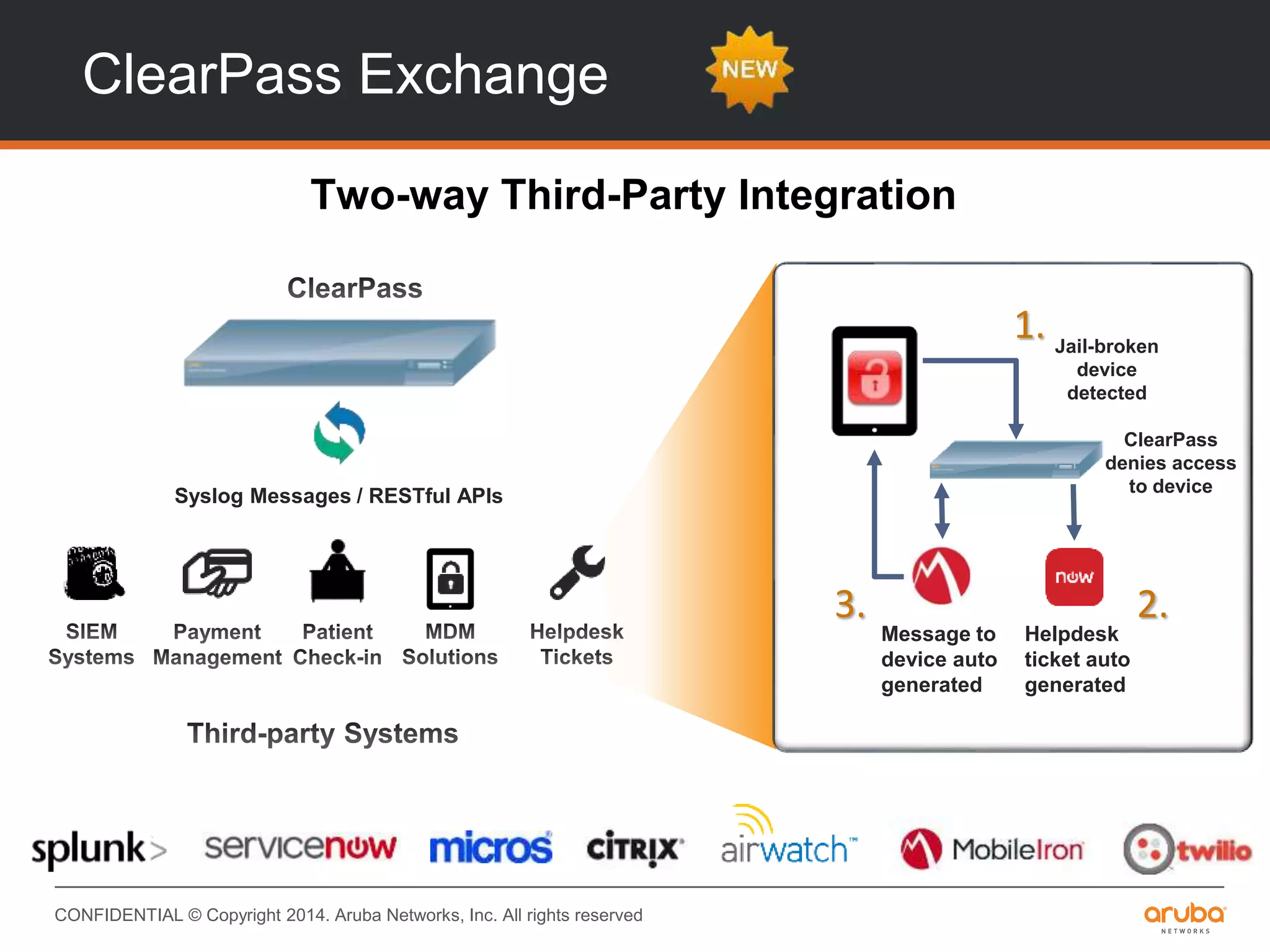
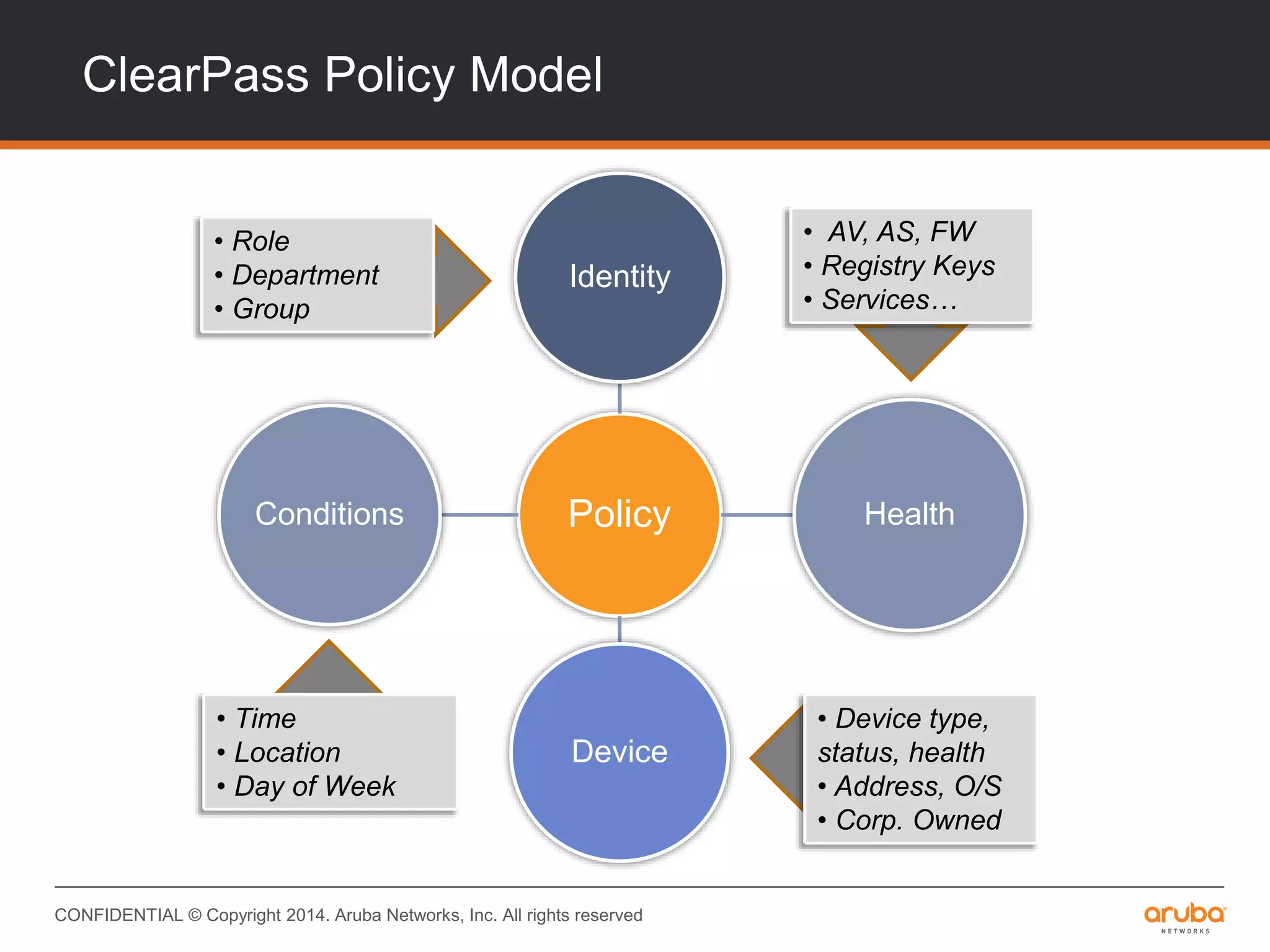
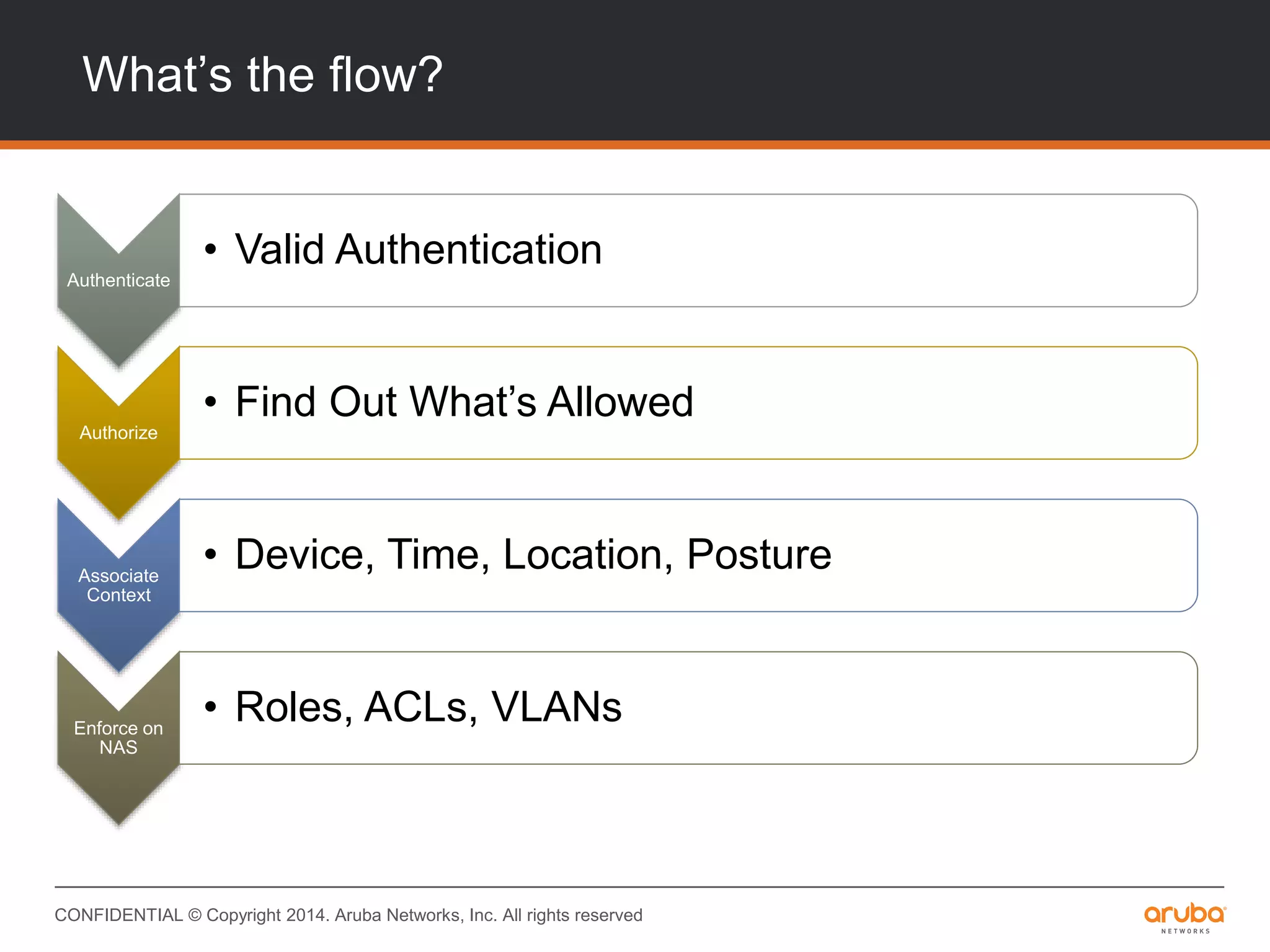
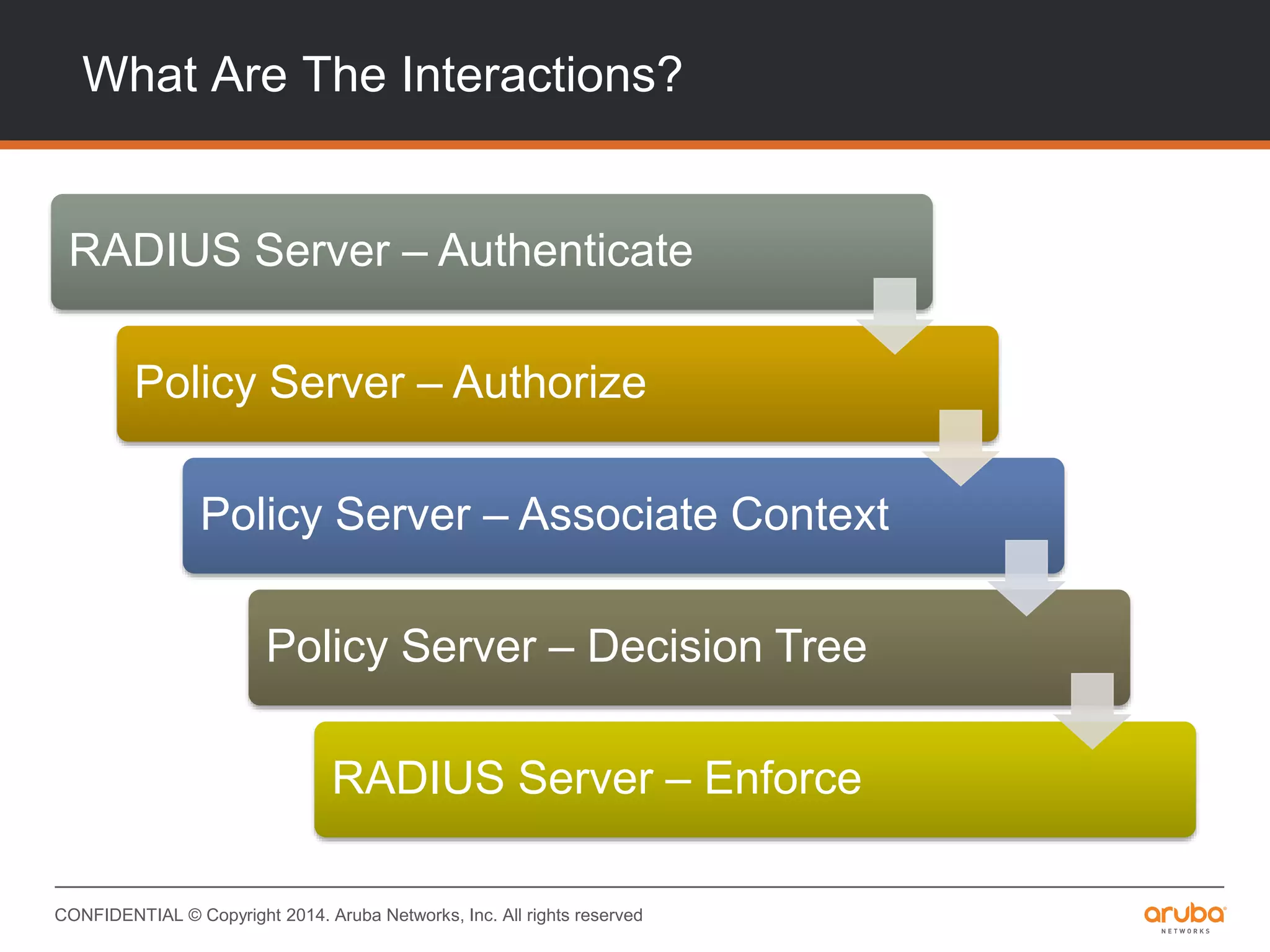
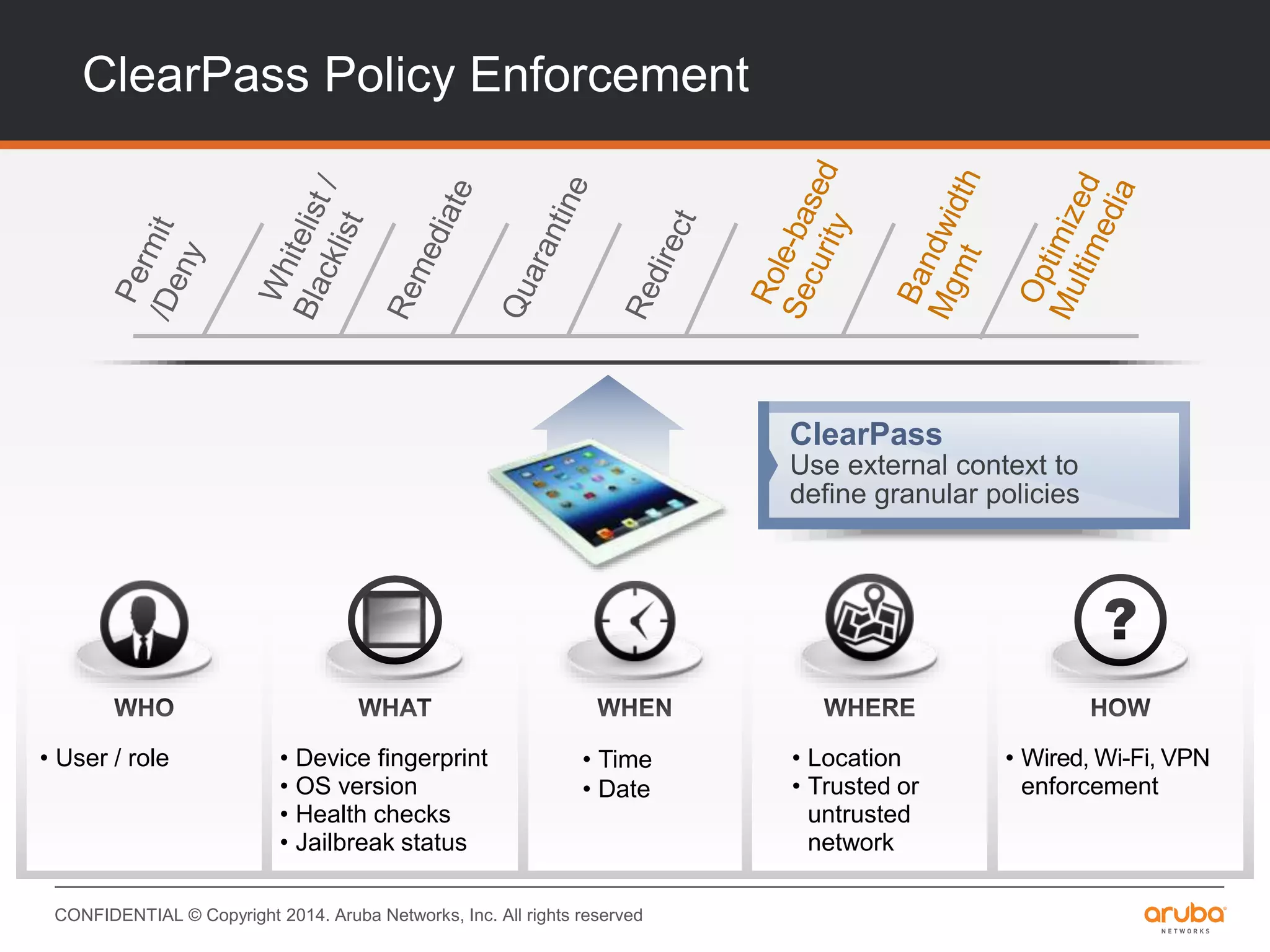
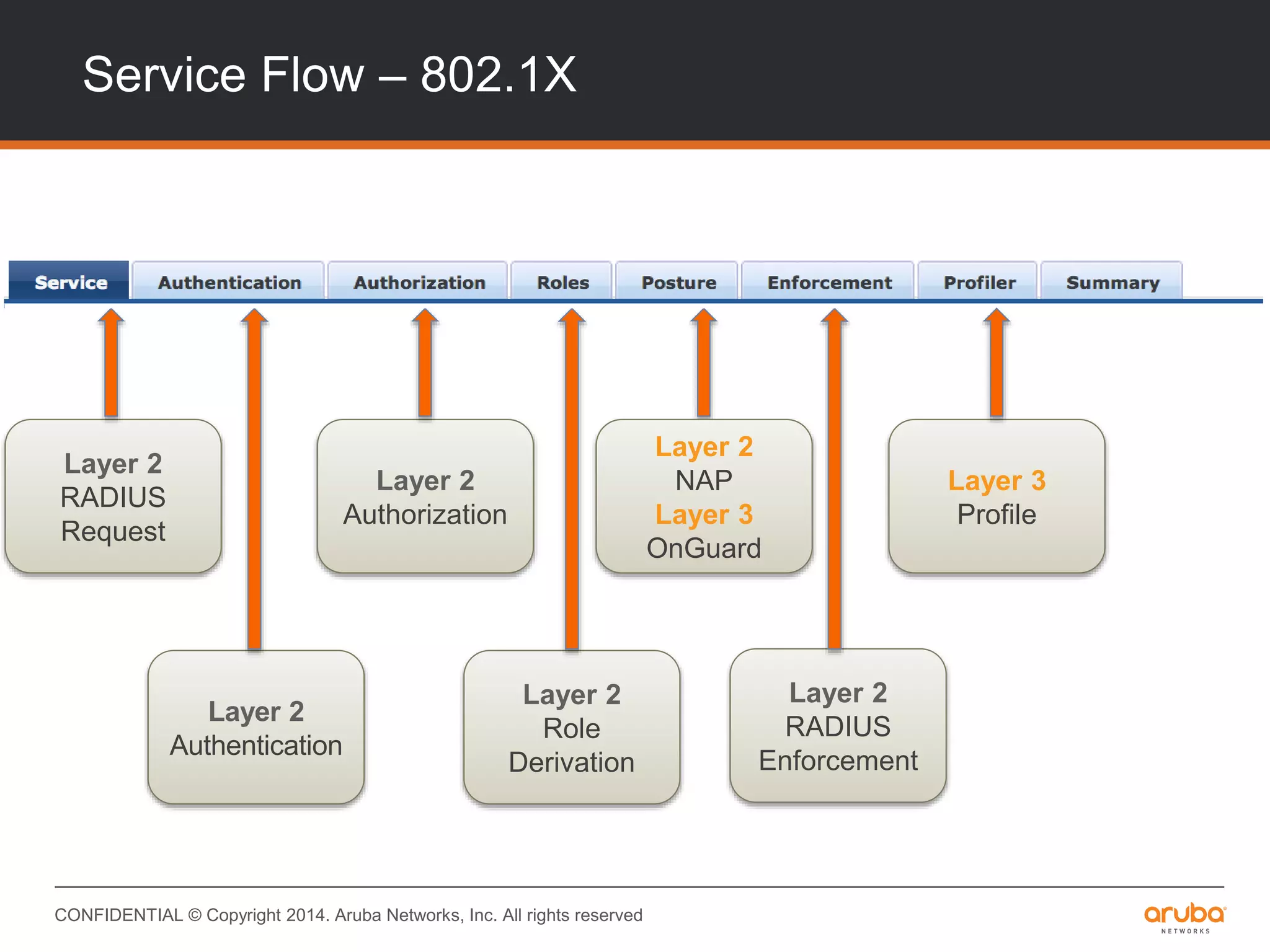
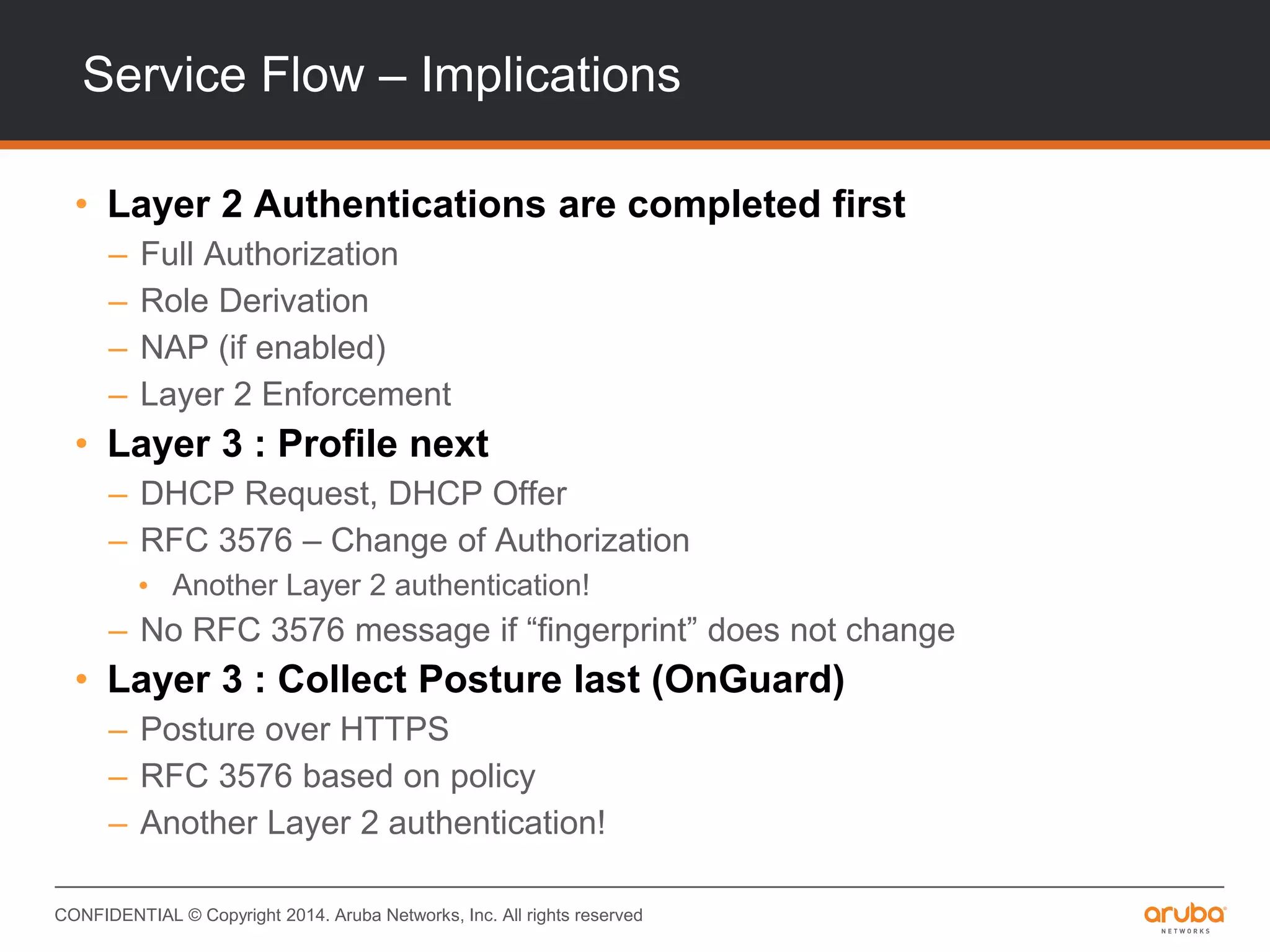
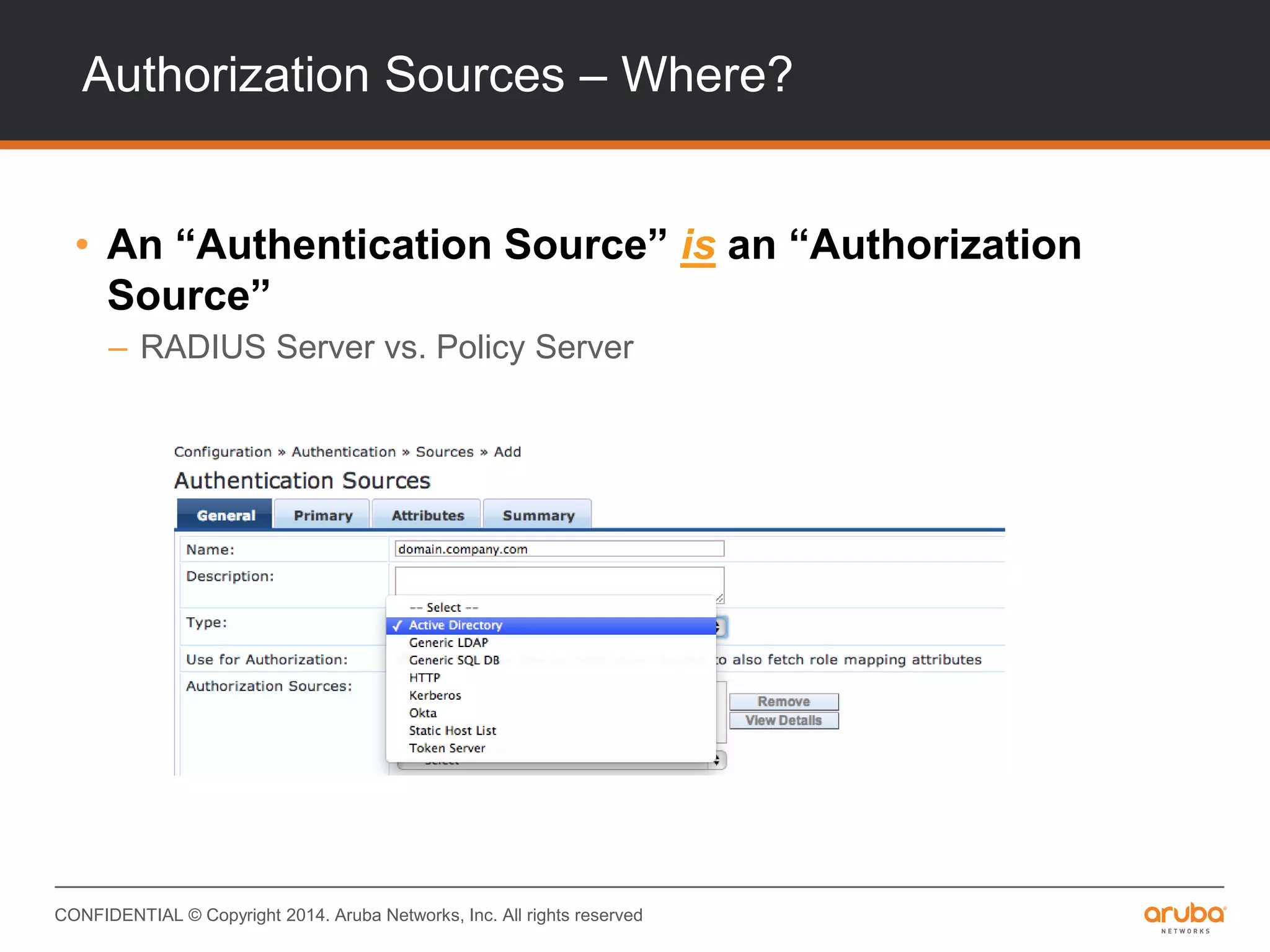
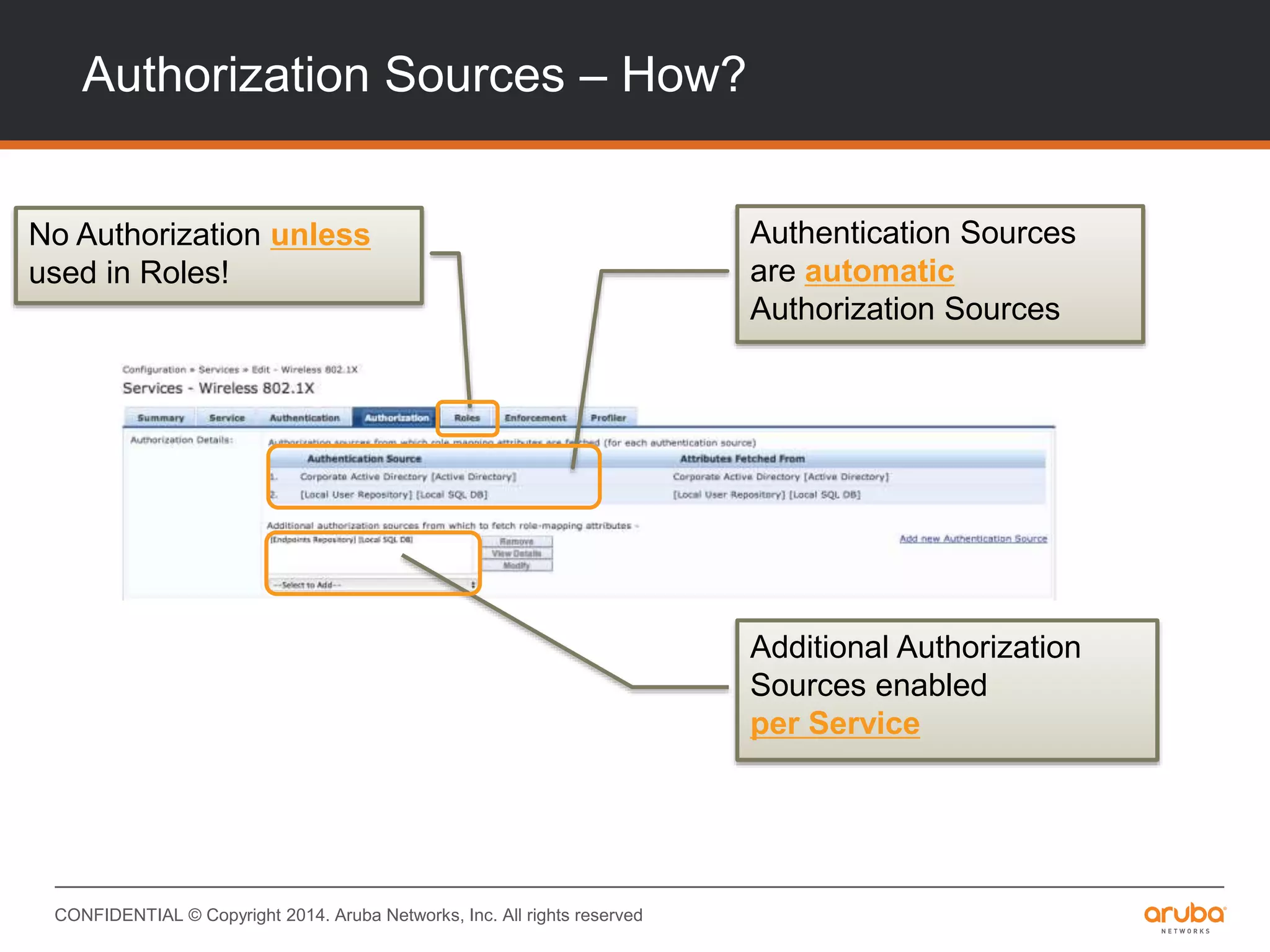
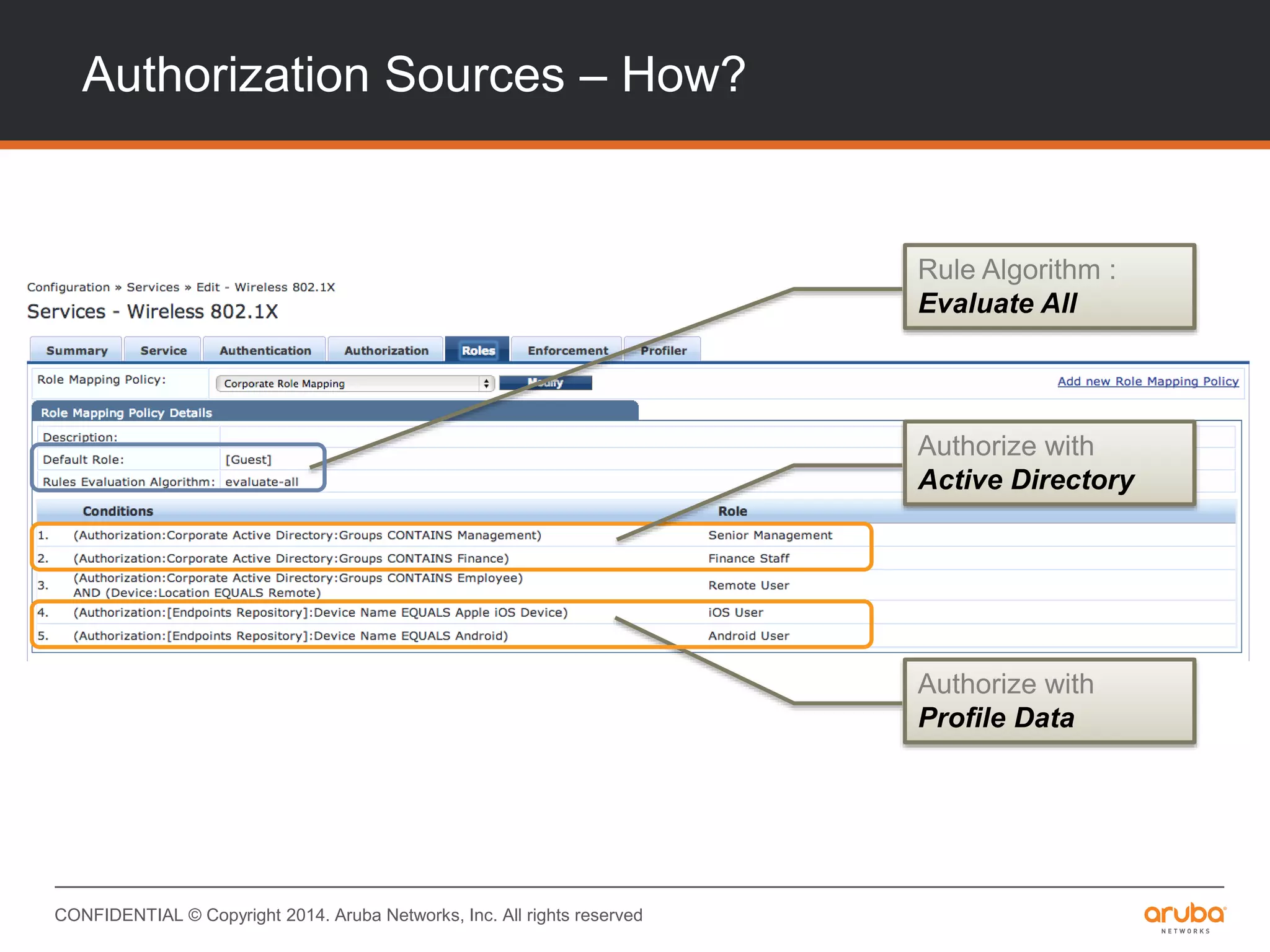
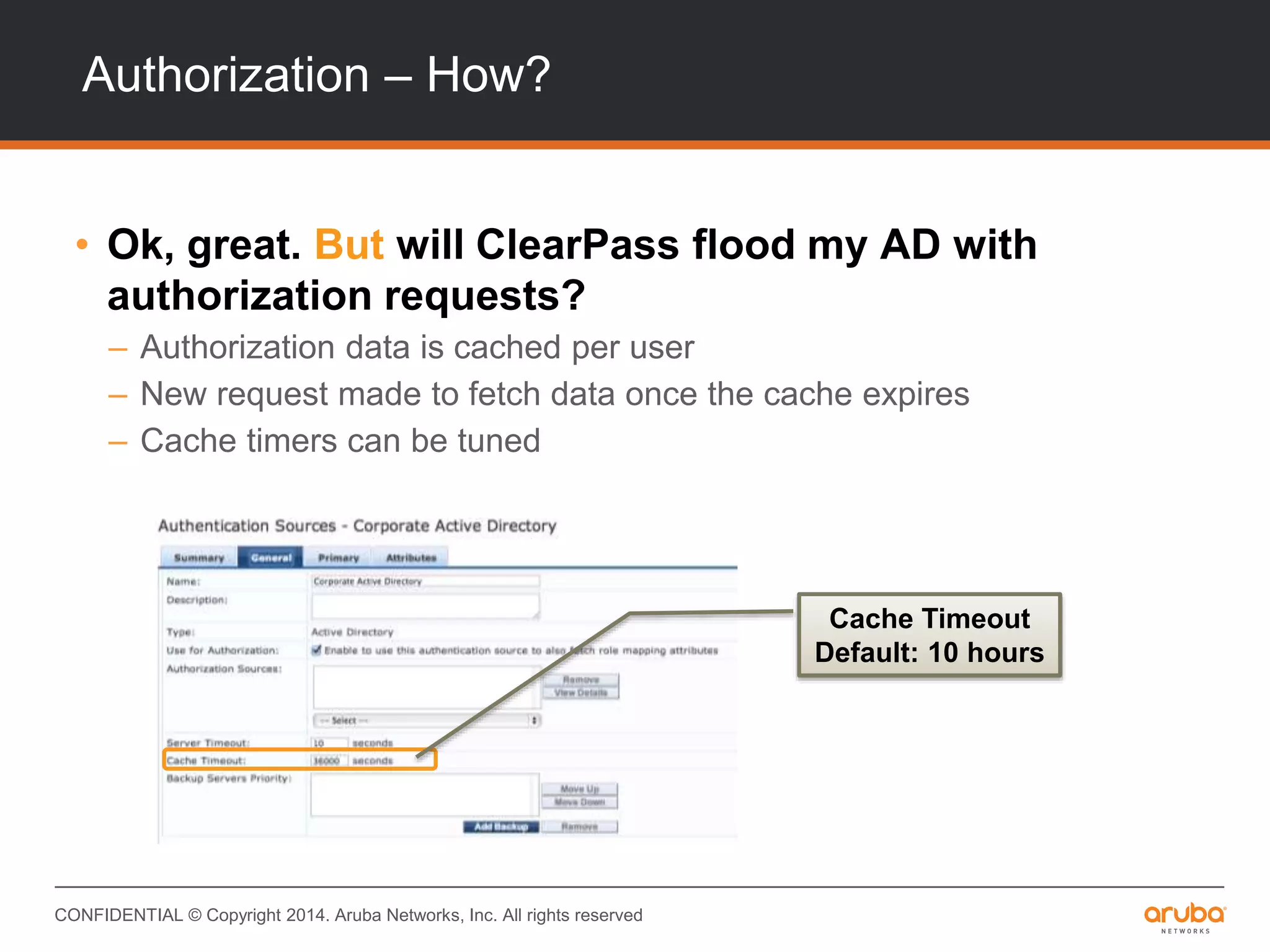
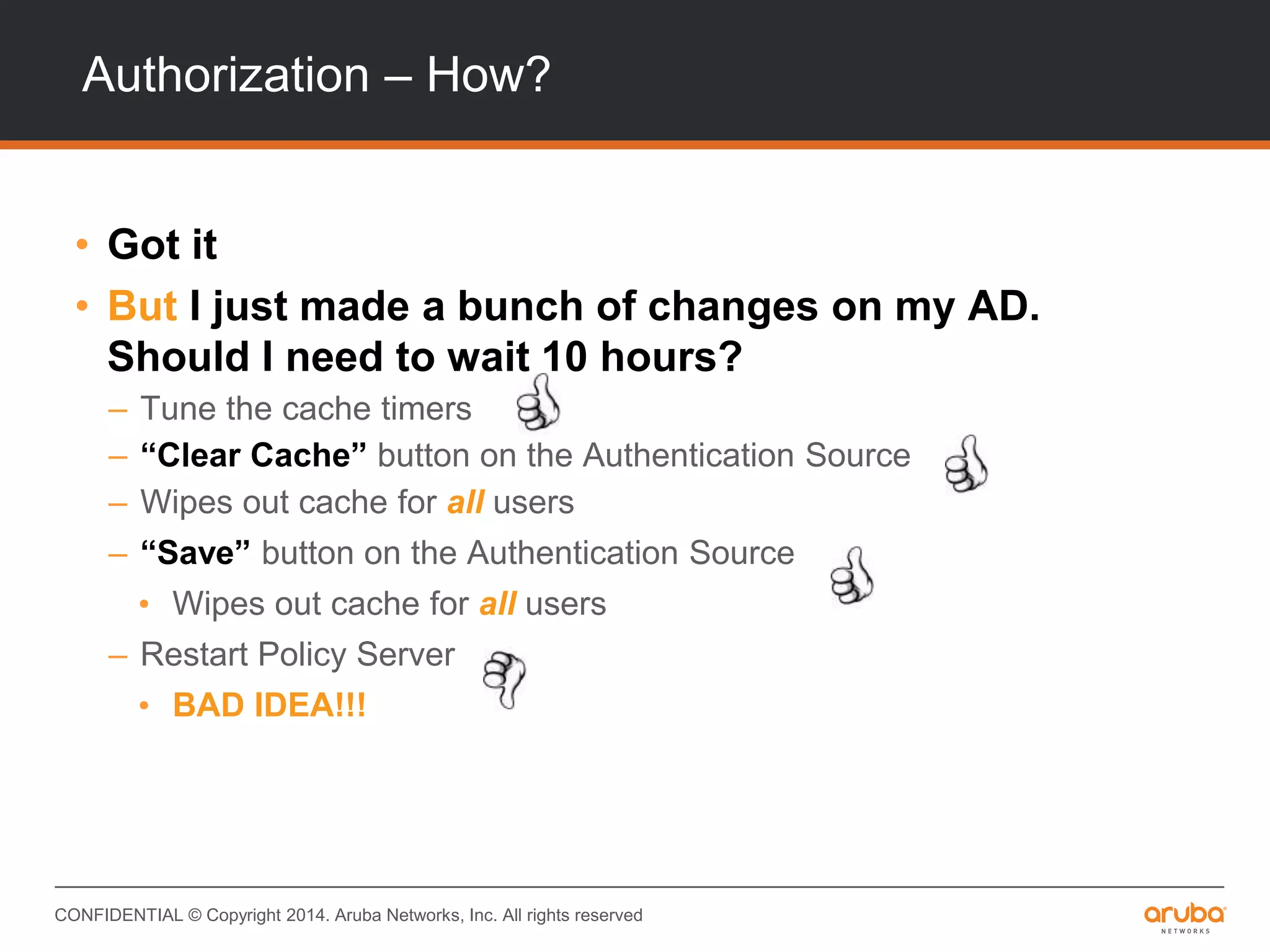
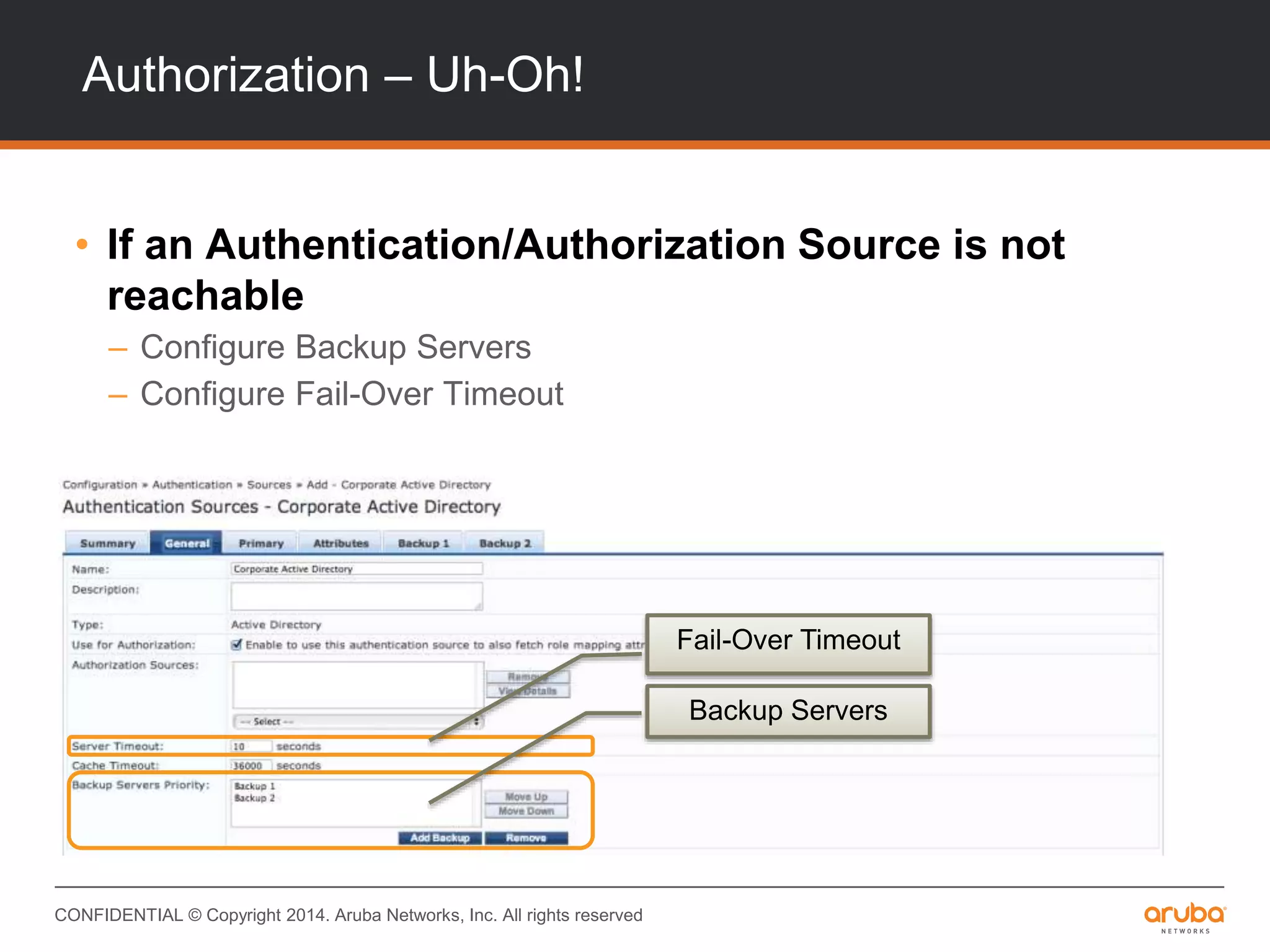
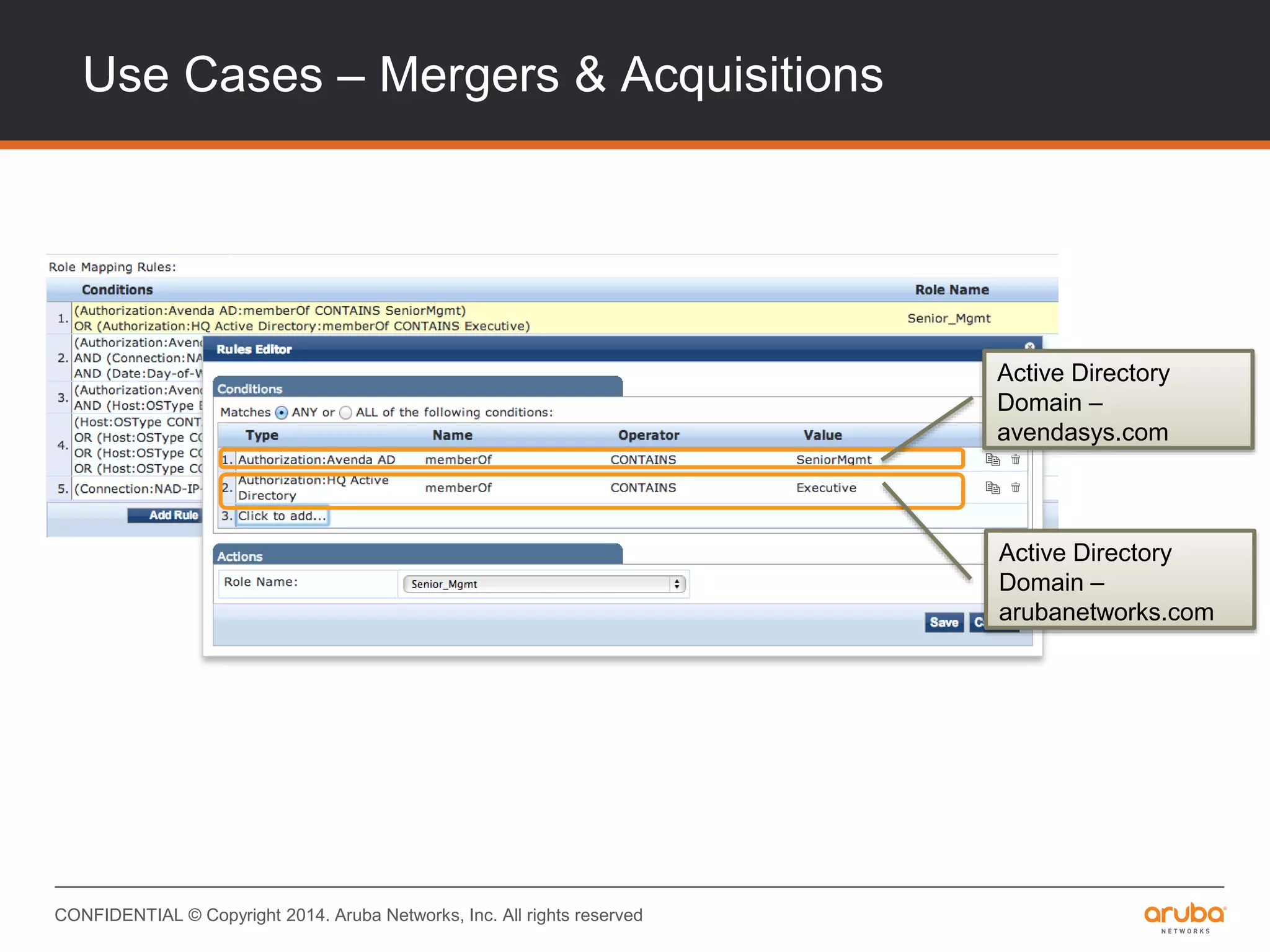
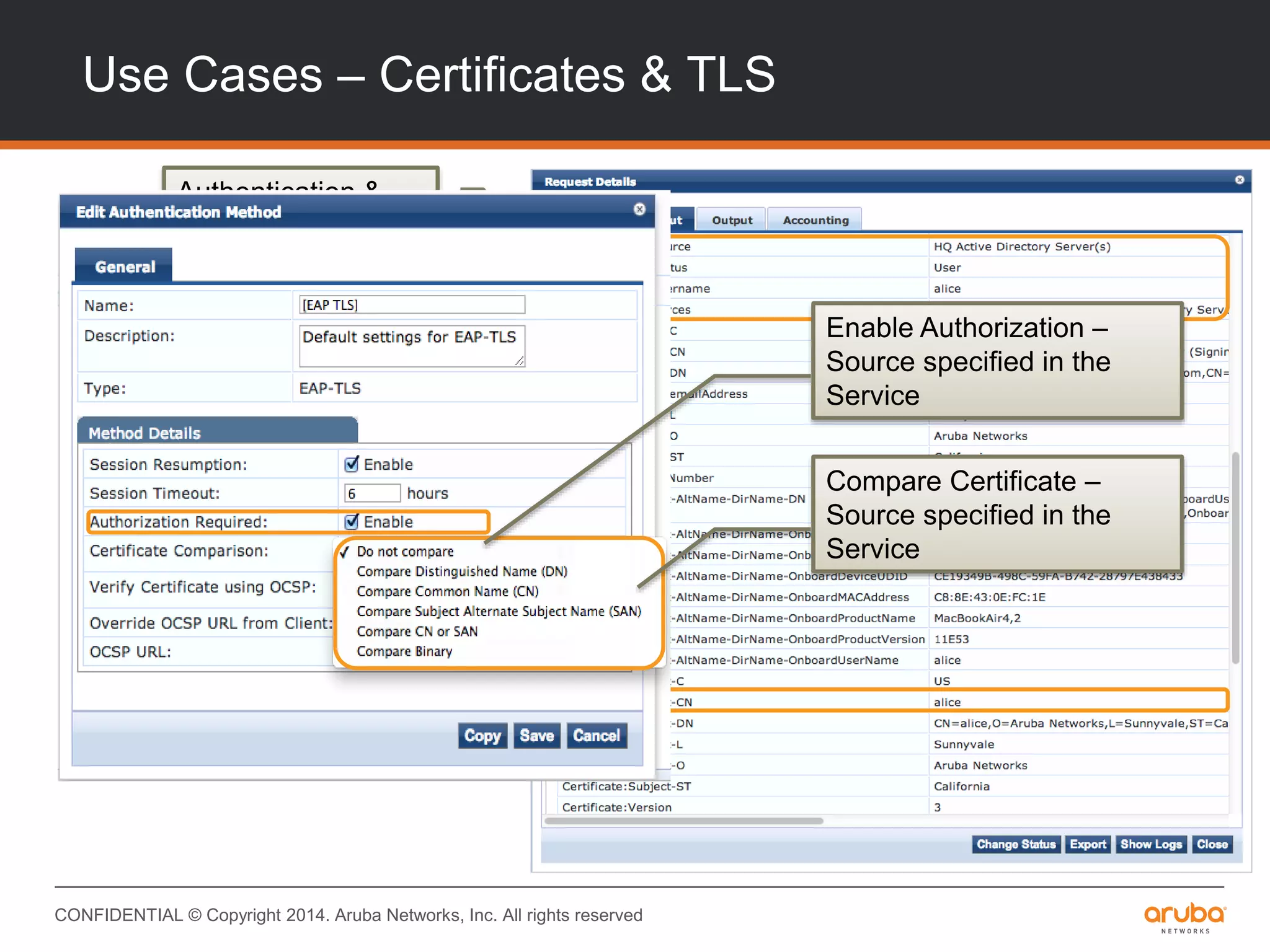
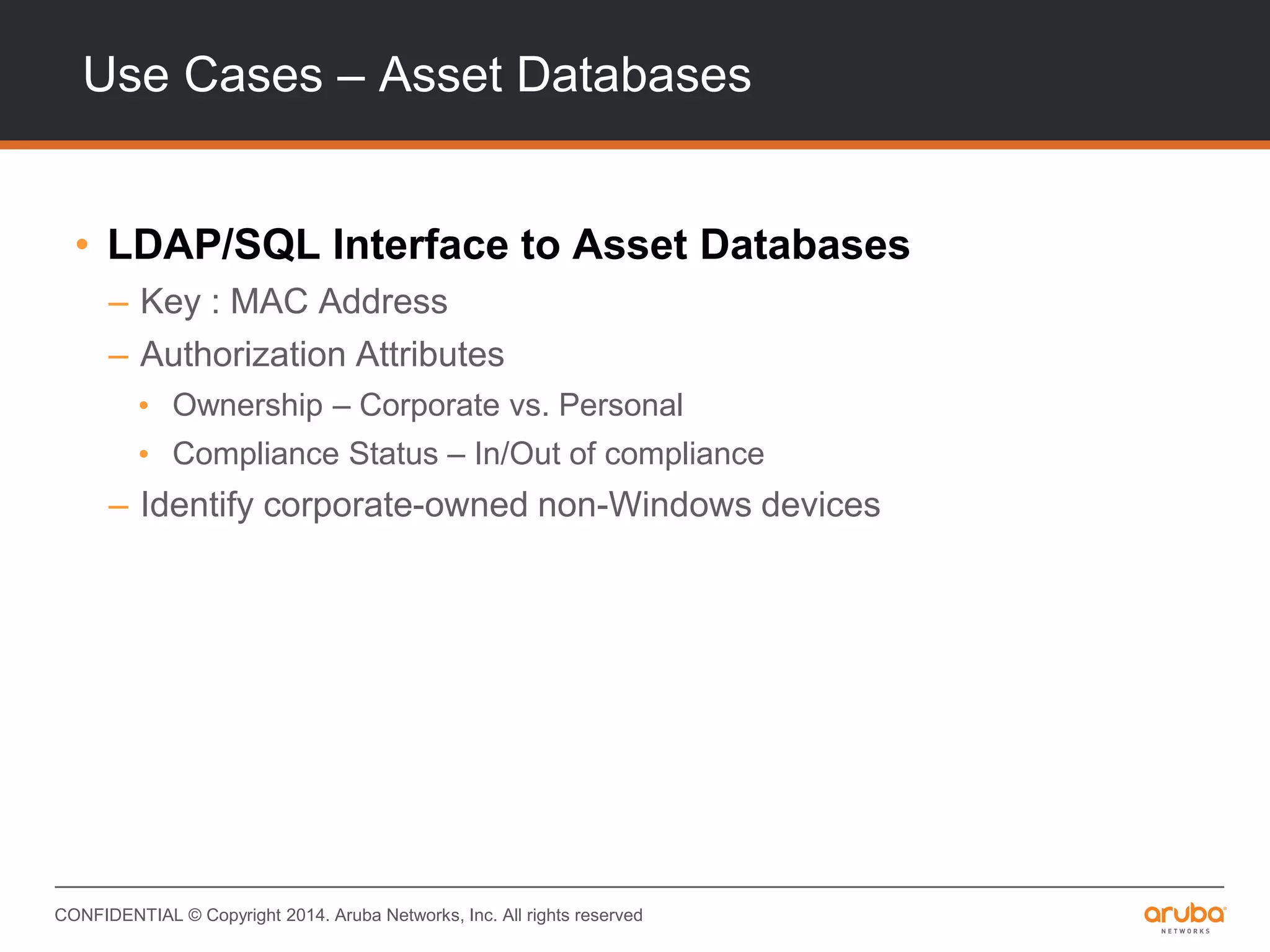
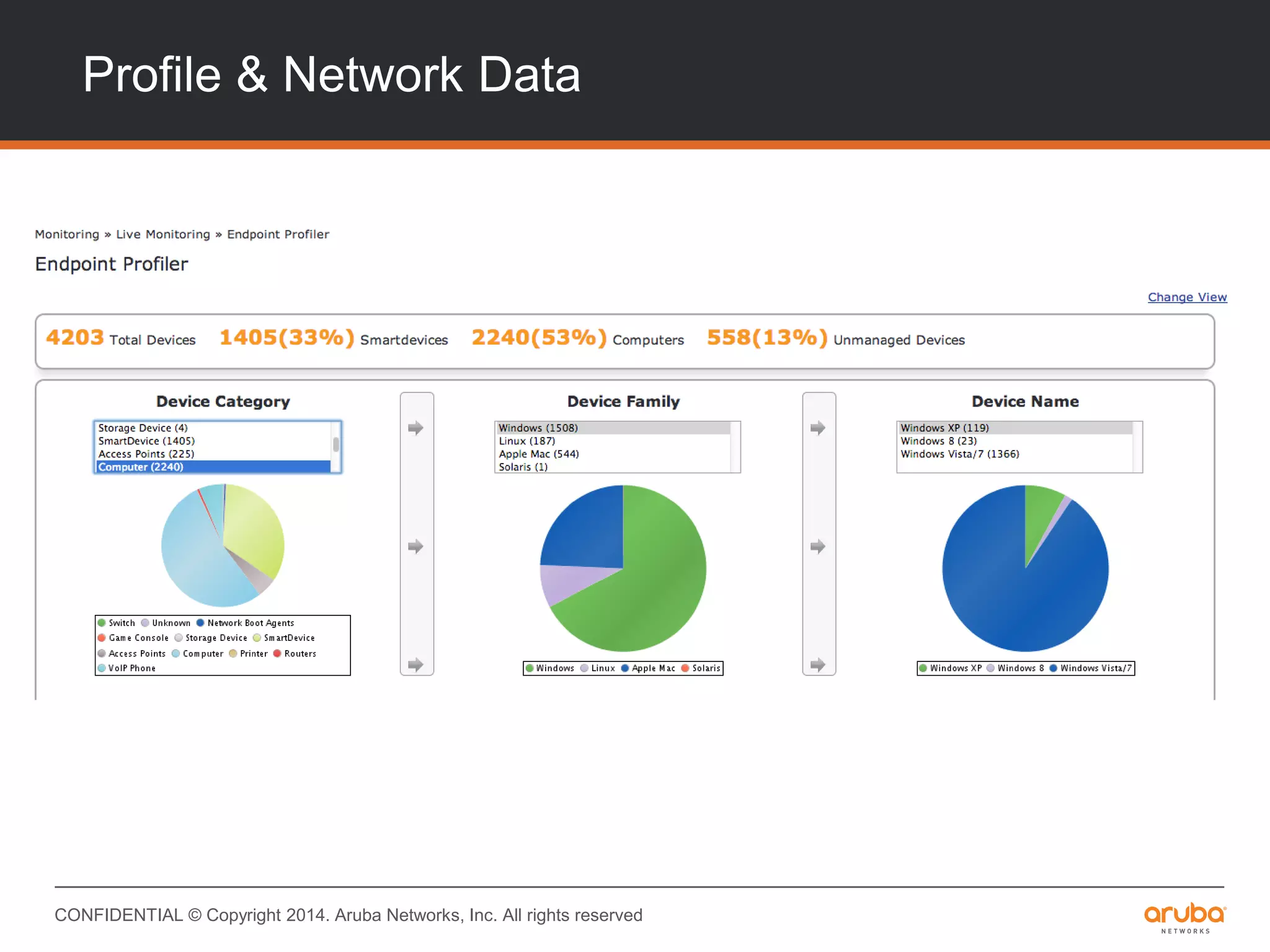
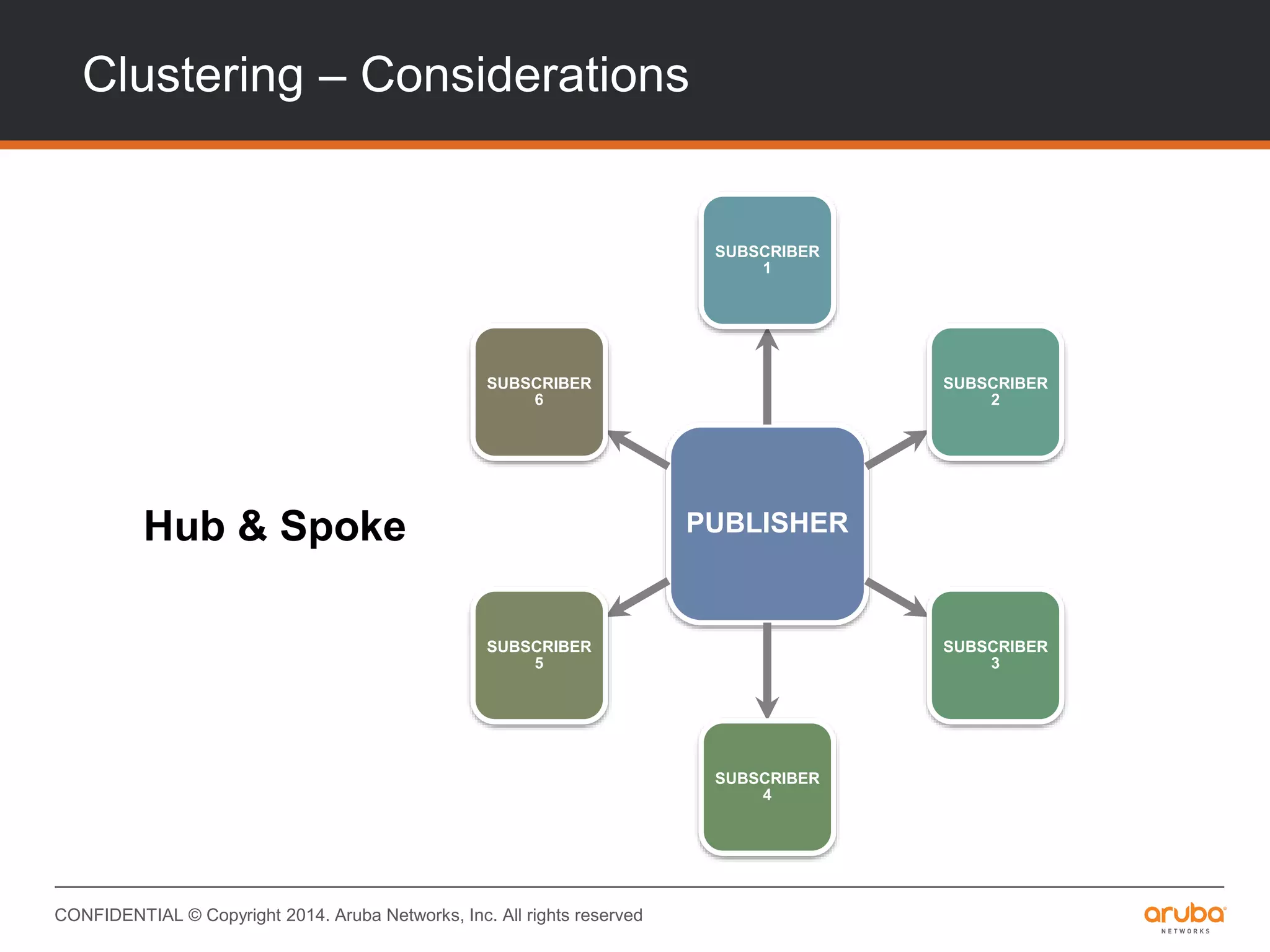
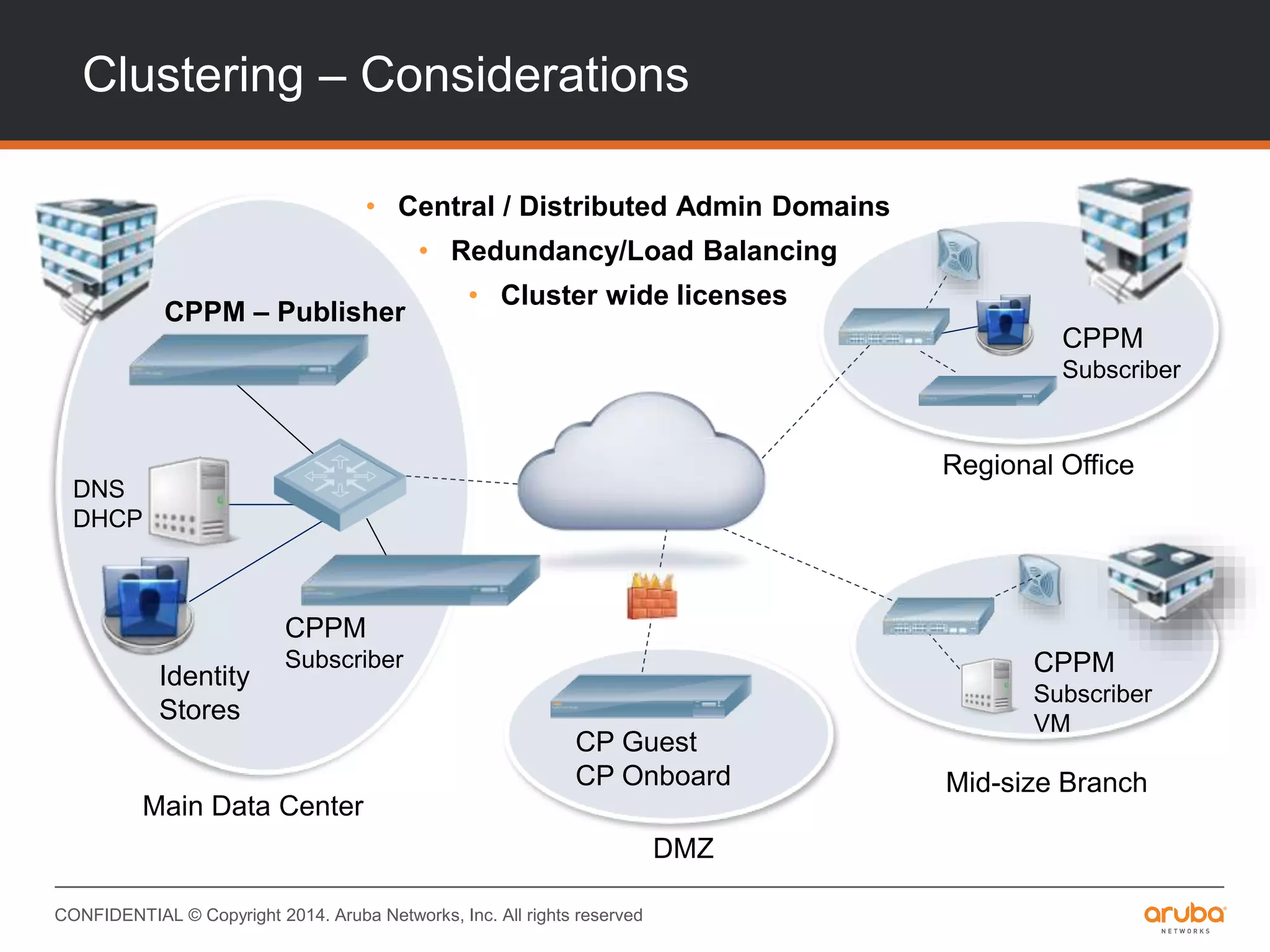
This document provides an overview of Aruba ClearPass and its access management capabilities. It discusses ClearPass' policy model and how it uses context such as identity, device, and location to enable granular, role-based access policies. It covers ClearPass' authorization features and how it profiles devices to incorporate that data into policies. The document also reviews ClearPass clustering functionality and considerations for deployment and operations.