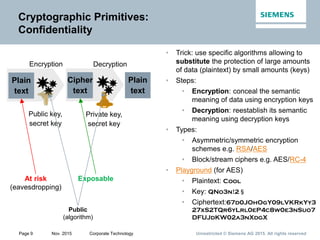
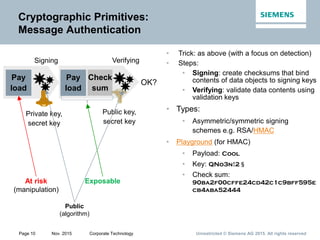
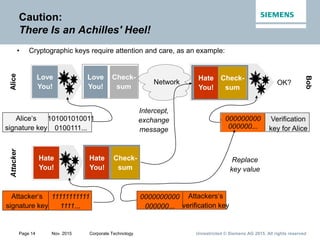
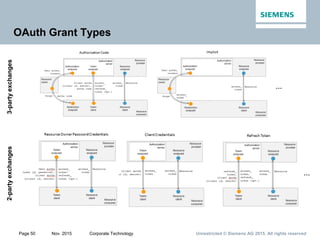
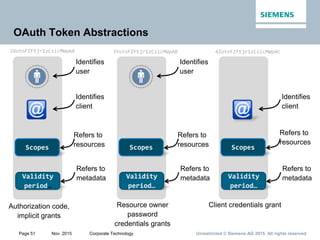
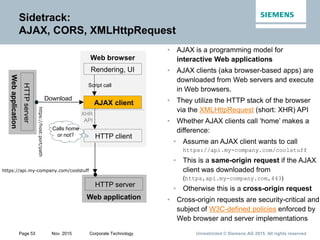
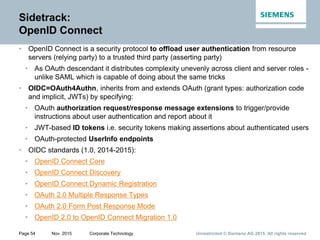
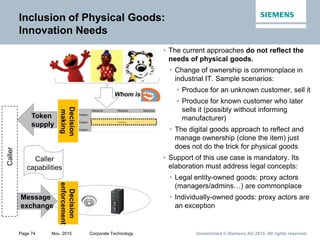
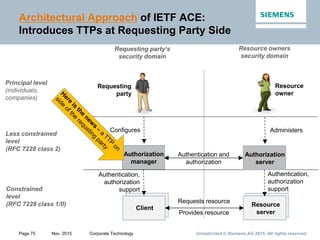
This document provides an overview of a lecture on security for the Web of Things. It discusses security building blocks including cryptographic primitives like encryption and signing, cryptographic objects that contain encrypted data and metadata, security tokens that make assessments about system actors, and security protocols for exchanging cryptographic objects. It emphasizes that while these techniques help secure distributed systems like the Web, cryptographic keys must also be carefully managed for security. The document provides background on distributed systems security and the dependencies between different security disciplines.










![Unrestricted © Siemens AG 2015. All rights reservedPage 28 Nov. 2015 Corporate Technology
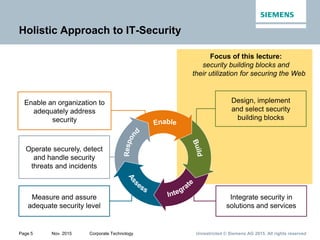
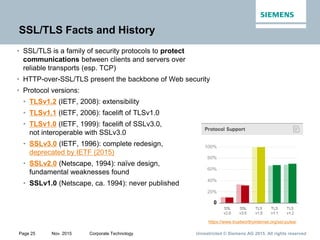
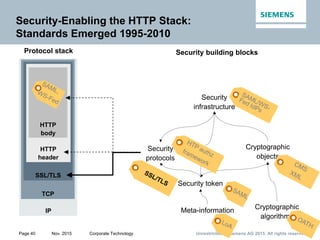
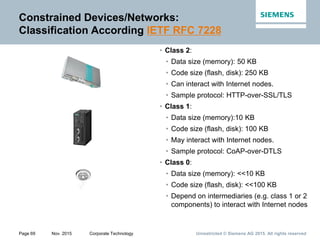
Record layer
data
Certificate*
ClientKeyExchange
CertificateVerify*
[ChangeCipherSpec]
Finished
Client identification*,
key exchange,
and authentication*
[ChangeCipherSpec]
Finished
FullTLShandshake
Server
authentication*
*: indicates optional
primitives and services
ClientHello
ServerHello
Certificate*
ServerKeyExchange*
CertificateRequest*
ServerHelloDone
Initialization,
cipher suite negotiation,
server identification*,
and key exchange*
SSL/TLS Handshake Layer
C
l
i
e
n
t
S
e
r
v
e
r](https://image.slidesharecdn.com/web-of-thingsandservicessecurity-151216090512/85/Web-of-Things-and-Services-Security-28-320.jpg)
![Unrestricted © Siemens AG 2015. All rights reservedPage 32 Nov. 2015 Corporate Technology
User Authentication:
Rationale for Trusted Third Parties
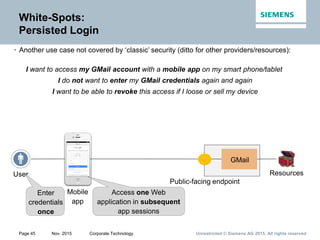
• User experience:
• SSO across multiple Web applications in a domain
• Uniform user registration/login for multiple Web applications in a domain
• Functional excellence:
• Accommodate multiple user populations incl. external populations
• Support dynamic, risk-based, adaptive authentication strategies cf. [5]
• System architecture:
• Shield business applications from authentication strategy/protocol/scheme complexity
• Decouple business applications from user store organization/location](https://image.slidesharecdn.com/web-of-thingsandservicessecurity-151216090512/85/Web-of-Things-and-Services-Security-32-320.jpg)















![Unrestricted © Siemens AG 2015. All rights reservedPage 78 Nov. 2015 Corporate Technology
More Information
[1] S. Bellovin: Web Security in the Real World. NIST Workshop on Improving Trust. in the
Online Marketplace, April 2013
[2] V. Bertocci: Authentication Protocols, Web UX and Web API. Blog, April 2014
[3] R. Fielding: Architectural Styles and the Design of Network-based Software Architectures.
PhD Thesis. University of California, Irvine, 2000
[4] K. Fu: Dos and Don’ts of Client Authentication on the Web. Proc. 10th USENIX Security
Symposium August 2001
[5] M. Hearn: An update on our war against account hijackers. Blog Feb 2013
[6] M. Jones: A JSON-Based Identity Protocol Suite. Information Standards Quarterly, vol. 26,
no. 3, 2014, pp. 19–22
[7] S. Kent, L. Millet (eds): Who Goes There? Authentication Through the Lens of Privacy.
The National Academies Press, Washington D.C., 2003
[8] C. Pautasso et al.: RESTful Web Services vs. “Big” Web Services: Making the Right
Architectural Decision. Proc. 17th International World Wide Web Conference, Bejing, 2008
[9] W3C WoT Interest Group: Security & Privacy Landscape for WoT. Wiki 2015 (work-in-
progress)
[10] S. Yegge: Stevey's Google Platforms Rant. Blog Oct. 2011](https://image.slidesharecdn.com/web-of-thingsandservicessecurity-151216090512/85/Web-of-Things-and-Services-Security-78-320.jpg)