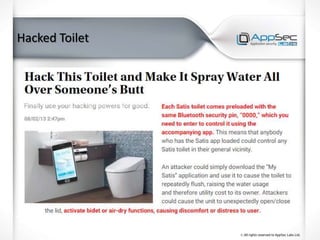
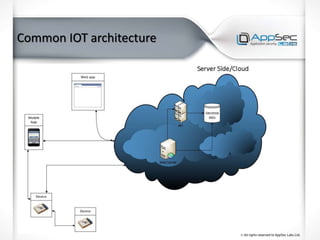
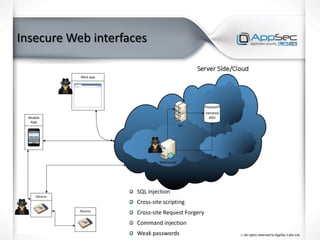
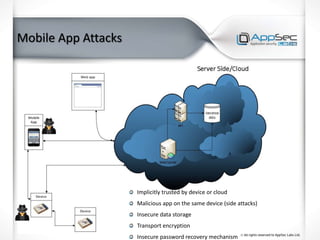
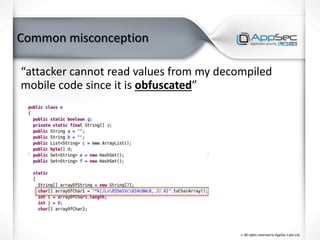
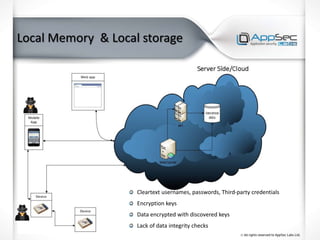
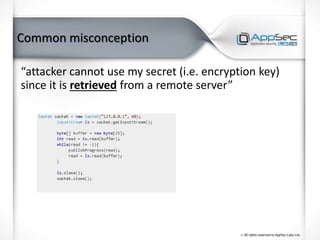
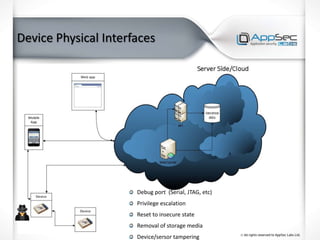
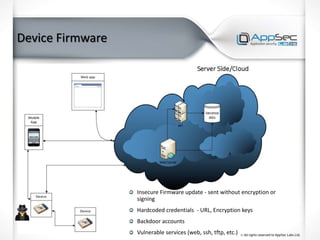
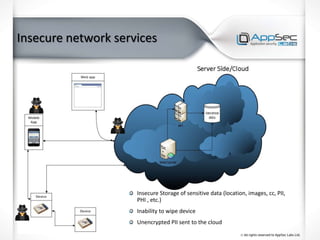
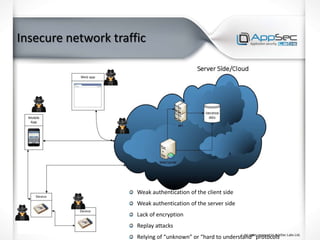
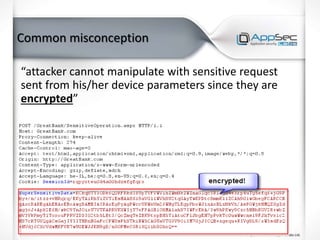
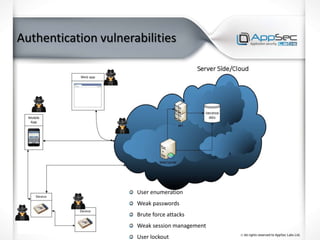
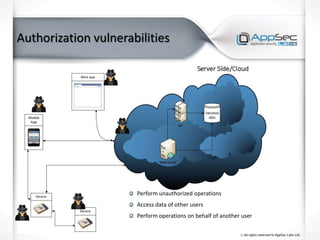
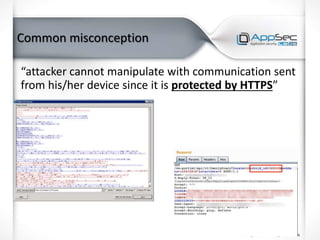
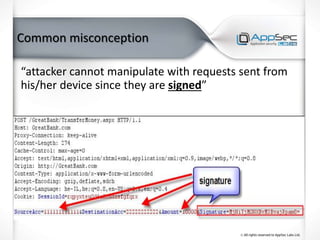
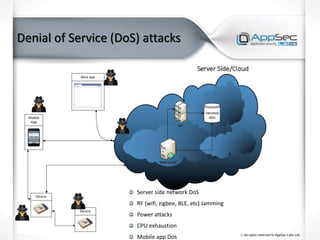
The document discusses common IoT security vulnerabilities and misconceptions. It outlines 10 top vulnerabilities: insecure web interfaces, SQL injection, cross-site scripting, cross-site request forgery, command injection, weak passwords, mobile app attacks, local memory and storage issues, device physical interfaces, and insecure device firmware. It also notes that IoT security requires covering all components, from the device to the cloud, and should not assume attackers cannot access devices, firmware, or decompiled apps. Common misconceptions about the limitations of attackers are also addressed.