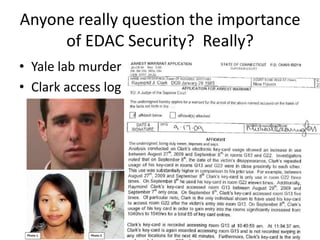
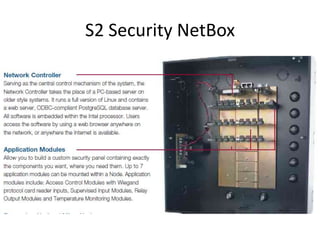
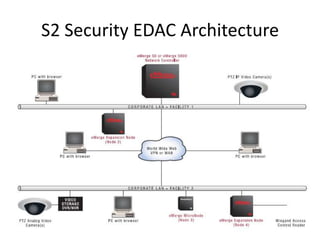
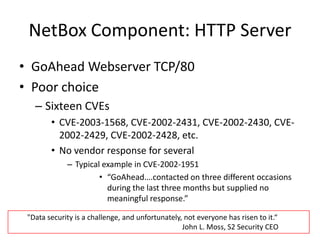
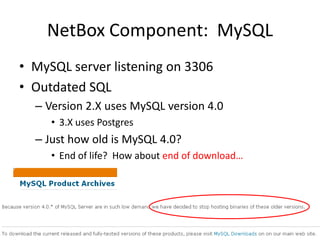
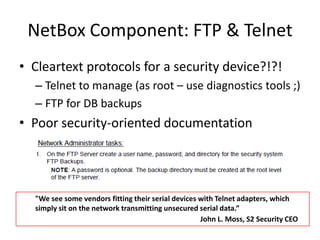
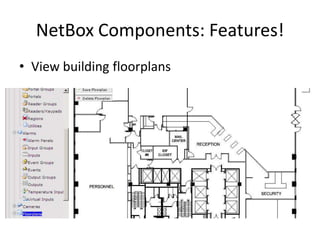
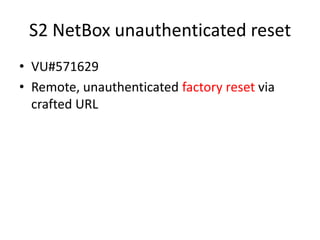
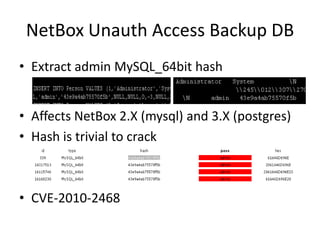
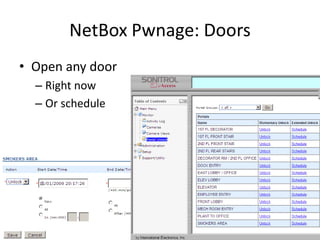
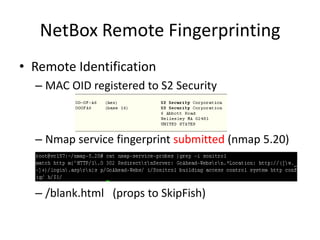
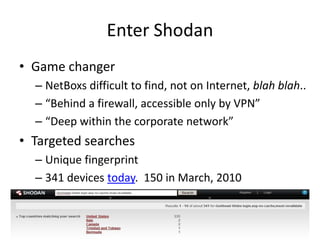
The document discusses the security vulnerabilities of electronic door access controllers (EDAC), emphasizing the need for better security and awareness in this area. It outlines common issues with various EDAC technologies, real-world vulnerabilities, and recommendations for improvement from manufacturers and users alike. Key insights include the importance of device management and the need for ethical hacking to identify and address these security flaws.