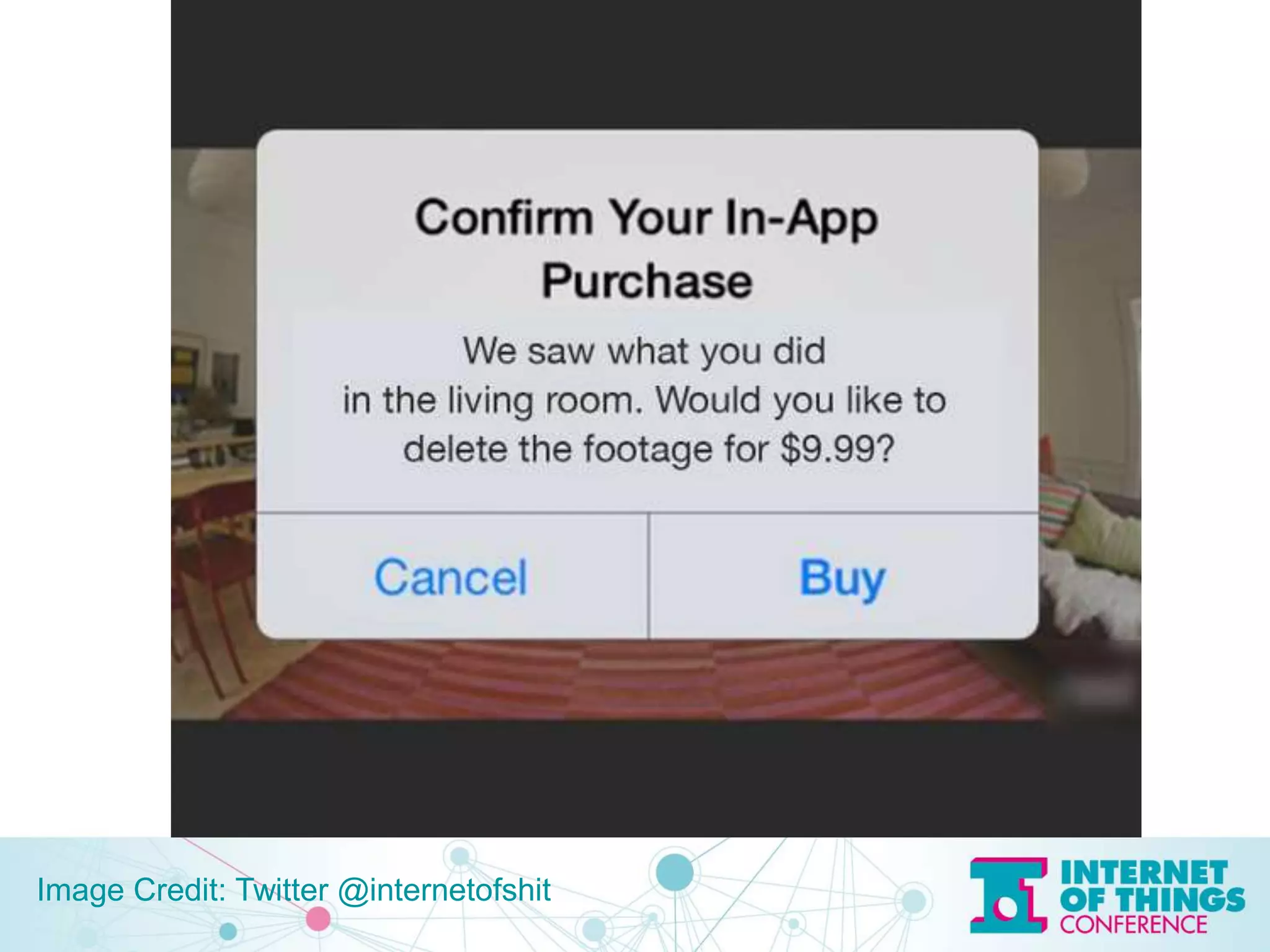
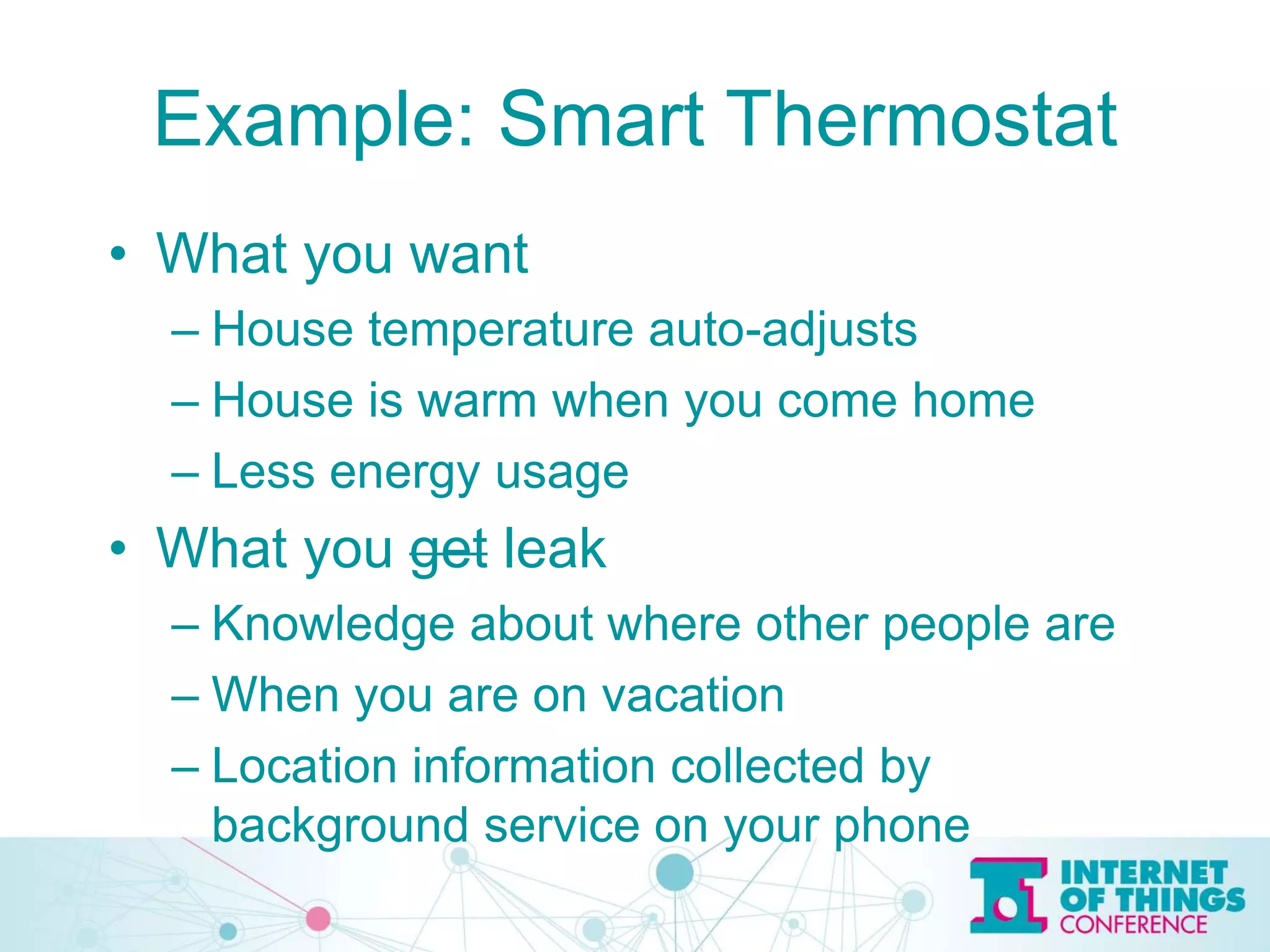
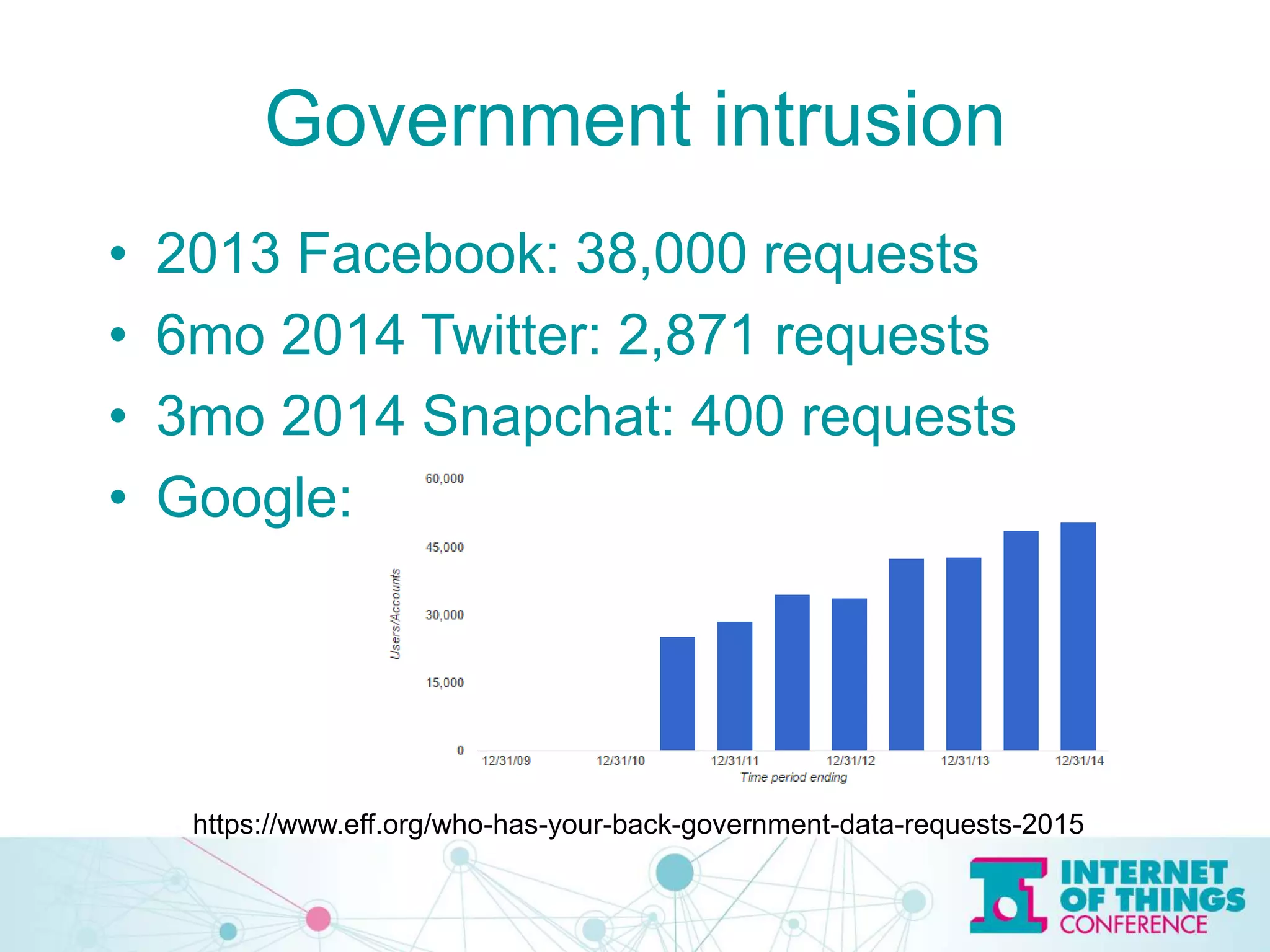
The document discusses privacy and security issues in the Internet of Things (IoT), emphasizing the importance of minimizing data collection and protecting user information. It highlights various examples of potential data leaks from smart technologies and the risks associated with government intrusion and corporate data sales. The speaker, Jeff Katz, advocates for strong encryption and proactive security measures to mitigate these challenges.