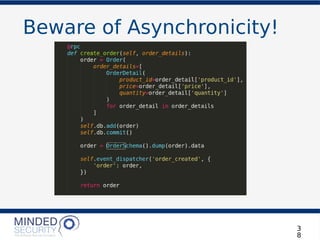
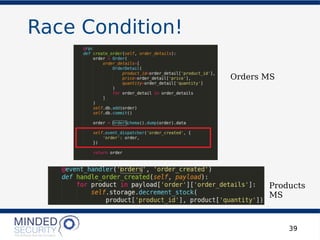
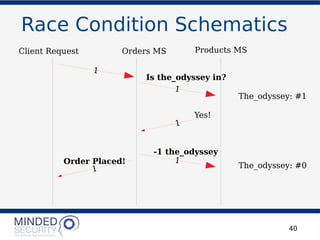
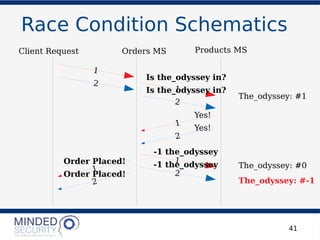
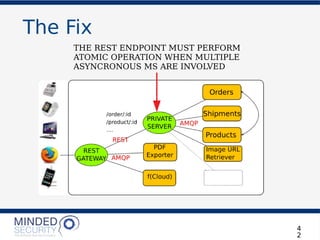
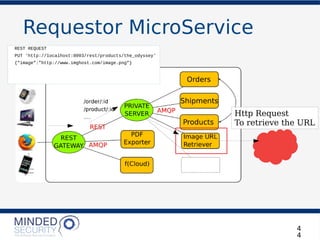
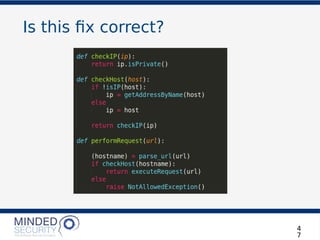
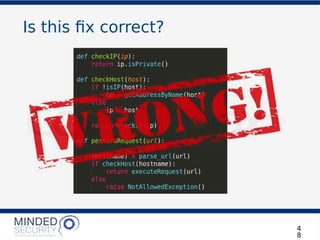
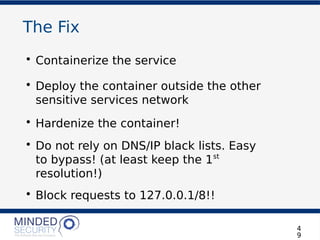
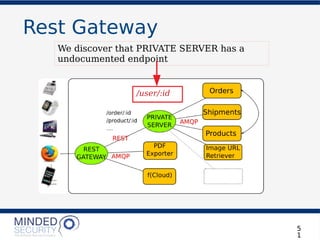
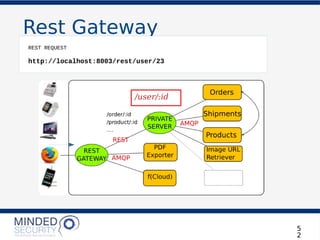
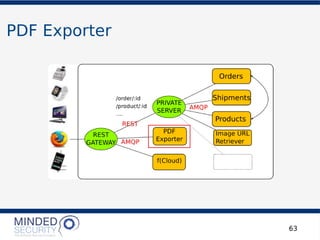
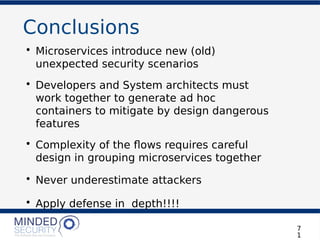
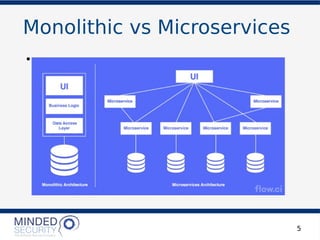
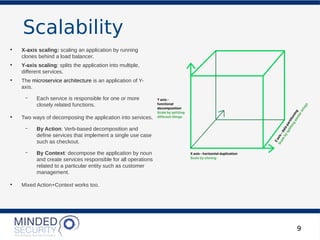
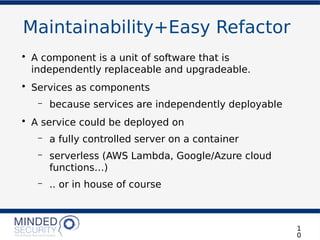
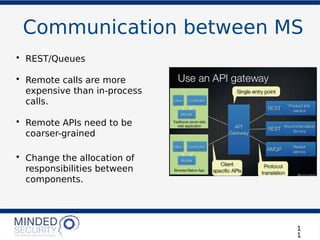
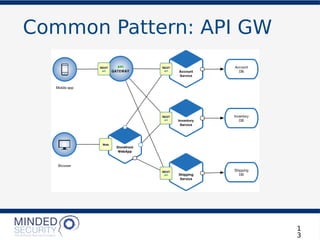
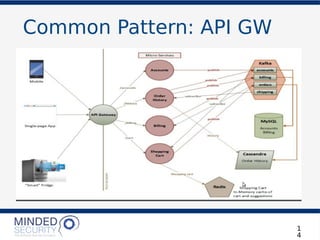
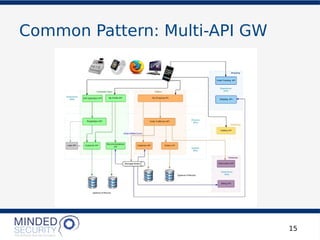
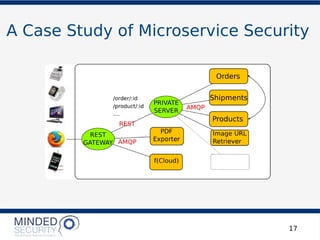
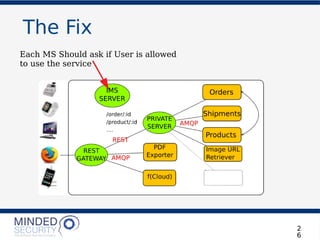
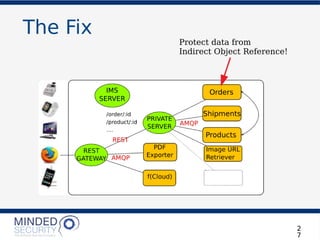
The document discusses the security challenges and best practices associated with microservices architectures, contrasting them with monolithic applications. It highlights common security issues, such as authorization flows and data protection, while emphasizing the importance of a defense-in-depth strategy. The need for careful design, effective communication between services, and specific mitigations to prevent vulnerabilities is underscored throughout the presentation.







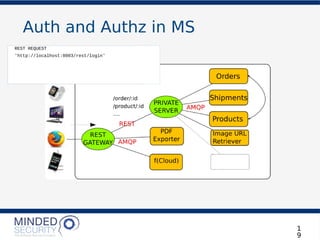
![Auth and Authz in MS
2
0
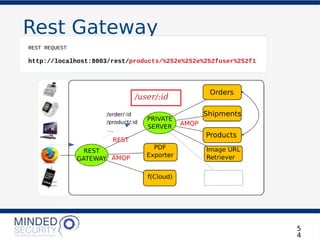
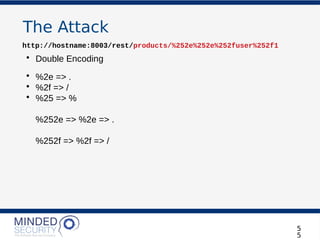
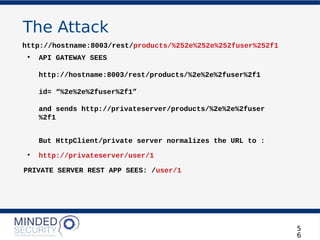
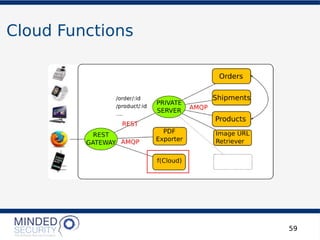
REST REQUEST
'http://localhost:8003/products/the_odyssey'
REST REQUEST
'http://localhost:8003/rest/login'
RESPONSE:
JWT:
{“user”:”stefano”,”id”: 22}.[CRYPTOGRAFICALLYSIGNED]](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-20-320.jpg)
![Auth and Authz in MS
2
1
REST REQUEST
'http://localhost:8003/products/the_odyssey'
REST REQUEST
'http://localhost:8003/rest/order/54252'
JWT: {“user”:”stefano”,”id”: 22}.
[CRYPTOGRAFICALLYSIGNED]
Is Logged In?](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-21-320.jpg)
![Auth and Authz in MS
2
2
Is Logged In?YES!
REST REQUEST
'http://localhost:8003/rest/order/54252'
JWT: {“user”:”stefano”,”id”: 22}.
[CRYPTOGRAFICALLYSIGNED]](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-22-320.jpg)
![Auth and Authz in MS
2
3
OKAY! GO ON!REST REQUEST
'http://localhost:8003/rest/order/54252'
JWT: {“user”:”stefano”,”id”: 22}.
[CRYPTOGRAFICALLYSIGNED]](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-23-320.jpg)
![Auth and Authz in MS
2
4
REST REQUEST
'http://localhost:8003/products/the_odyssey'
REST REQUEST
'http://localhost:8003/rest/order/54252'
JWT: {“user”:”stefano”,”id”: 22}.
[CRYPTOGRAFICALLYSIGNED]
OKAY! GO ON!](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-24-320.jpg)


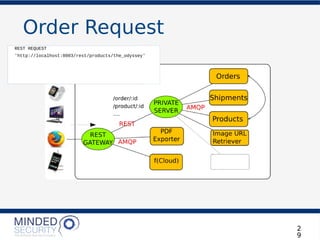
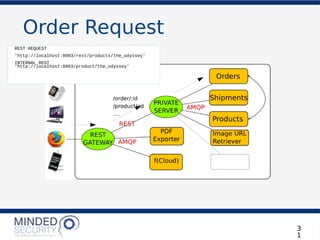
![Order Request
3
3
REST REQUEST
'http://localhost:8003/products/the_odyssey'
LET’S PLACE AN ORDER!
POST http://localhost:8003/orders
{
"order_details": [
{
"product_id": "the_odyssey",
"quantity": 1
}
]
}](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-33-320.jpg)
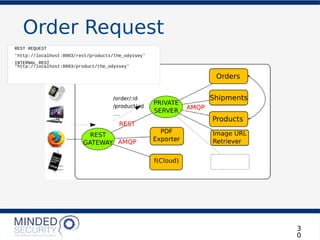
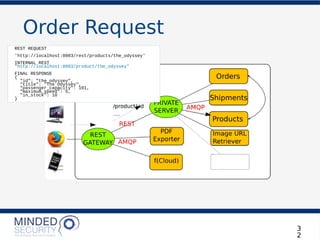
![Order Request
3
4
REST REQUEST
'http://localhost:8003/products/the_odyssey'
LET’S PLACE AN ORDER!
POST http://localhost:8003/orders
{
"order_details": [
{
"product_id": "the_odyssey",
"quantity": 1
}
]
}
DO WE HAVE ANY
the_odyssey?](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-34-320.jpg)
![Order Request
3
5
REST REQUEST
'http://localhost:8003/products/the_odyssey'
LET’S PLACE AN ORDER!
POST http://localhost:8003/orders
{
"order_details": [
{
"product_id": "the_odyssey",
"quantity": 1
}
]
}
DO WE HAVE ANY
the_odyssey?
YES!](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-35-320.jpg)
![Order Request
3
6
REST REQUEST
'http://localhost:8003/products/the_odyssey'
LET’S PLACE AN ORDER!
POST http://localhost:8003/orders
{
"order_details": [
{
"product_id": "the_odyssey",
"quantity": 1
}
]
}
OKAY!
-1 FOR the_odyssey!](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-36-320.jpg)
![Order Request
3
7
REST REQUEST
'http://localhost:8003/products/the_odyssey'
LET’S PLACE AN ORDER!
POST http://localhost:8003/orders
{
"order_details": [
{
"product_id": "the_odyssey",
"quantity": 1
}
]
}
RESPONSE : {"order_id": 2131}](https://image.slidesharecdn.com/microservicesdosdonts-180727081818/85/Microservices-Security-dos-and-don-ts-37-320.jpg)