The document discusses how Identity and Access Management (IAM) can be applied to Representational State Transfer (REST) web services and contrasts it with traditional SOAP-based services. It covers various aspects such as initial and federated authentication, single sign-on, and authorization in the context of RESTful services, highlighting the challenges and opportunities unique to this architectural style. Ultimately, it concludes that IAM for REST must cater to different types of clients and establish new methods to support the authentication and authorization needs inherent to RESTful applications.


![Answers – Employing IAM
Initial Authentication – Proprietary
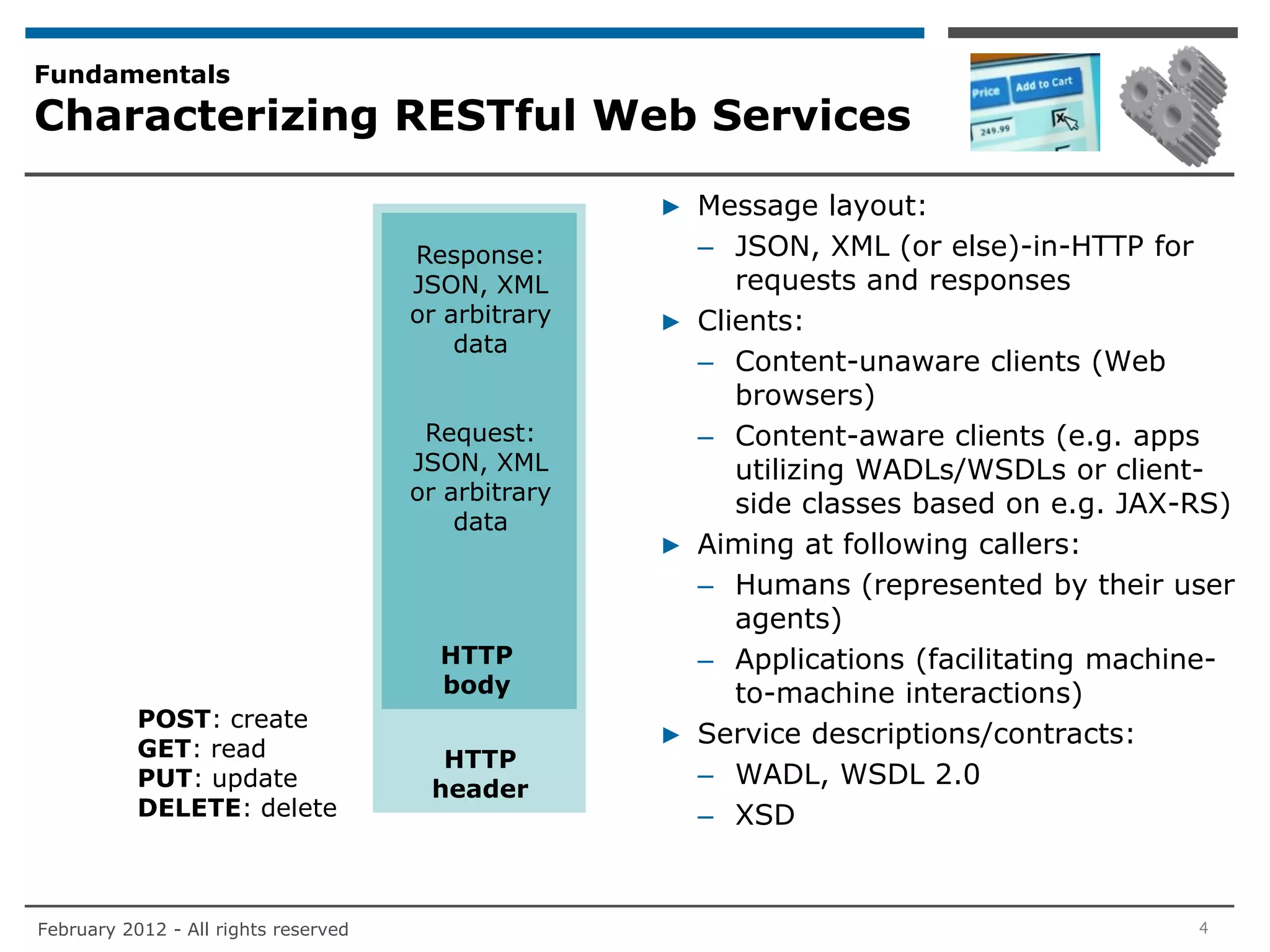
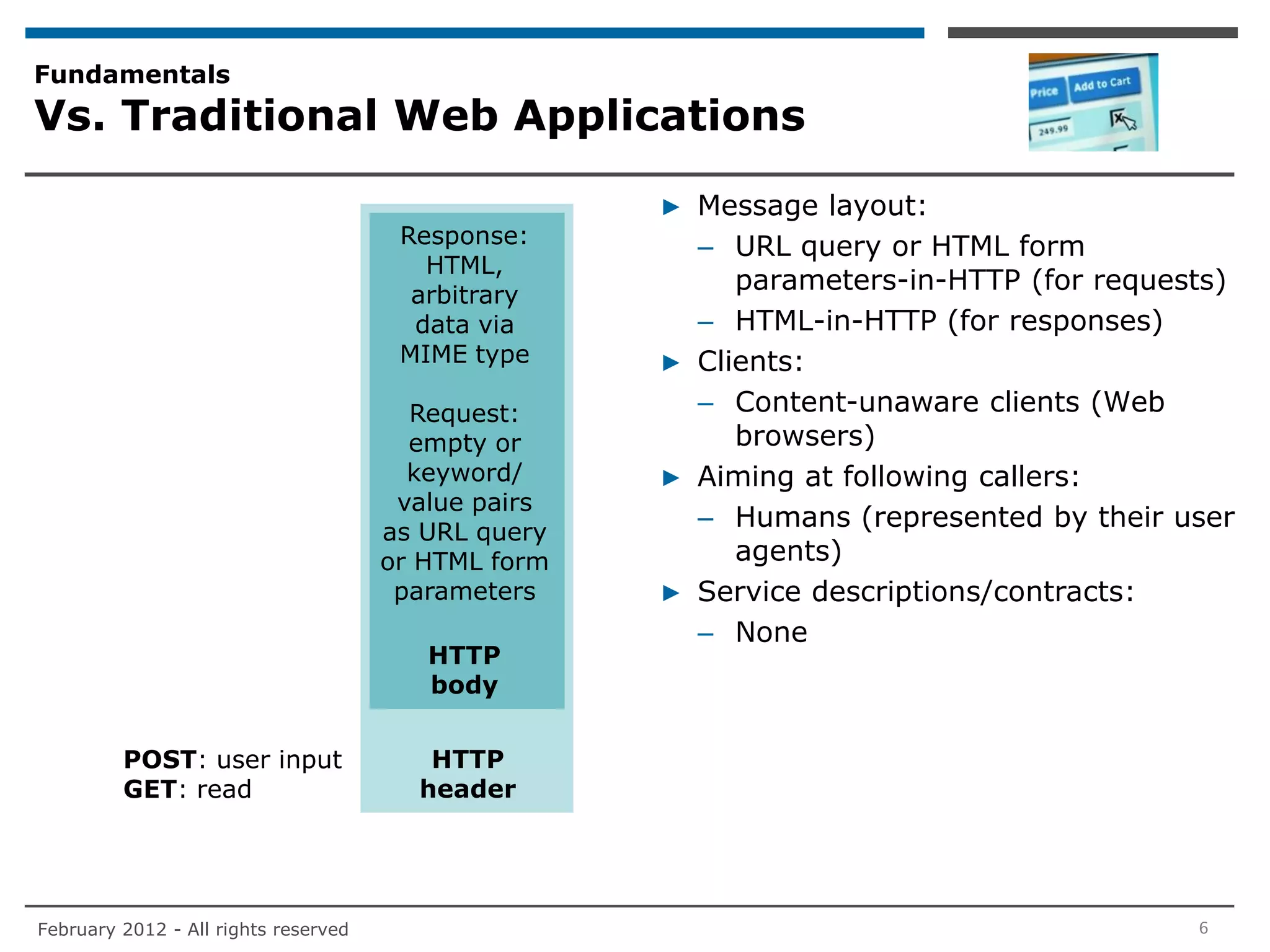
▶ The current practice for authenticating non-user requestors of RESTful Web
services is to establish ID/API key-tuples through a registration process.
– This is equivalent to username/password-tuples which are established for users
accessing traditional Web applications
▶ By default, the API keys are shared secrets. They are employed with HTTP Basic
or proprietary authentication schemes (in case there is a need to protect [a
subset] of the message contents through cryptographic checksums)
– HTTP Digest authentication also allows to protect some message contents
through cryptographic checksums but is not used in practice
▶ Proprietary schemes to authenticate REST API calls present an anti-pattern:
– It can be commonly found (quote: “Everyone feels the need to write a custom
authentication protocol”, cf. broadcast.oreilly.com/2009/12/principles-for-
standardized-rest-authentication.html)
– The MAC access authentication scheme for HTTP provides means to avoid this
anti-pattern in future:
• This scheme is currently being developed in the IETF (oauth working group)
• It evolves from OAuth but is not tightly bound to the native OAuth use case
of delegating authorization and can be used on a broader base.
February 2012 - All rights reserved 12](https://image.slidesharecdn.com/doesrestchangethegameforiam-120226145822-phpapp01/75/Does-REST-Change-the-Game-for-IAM-12-2048.jpg)
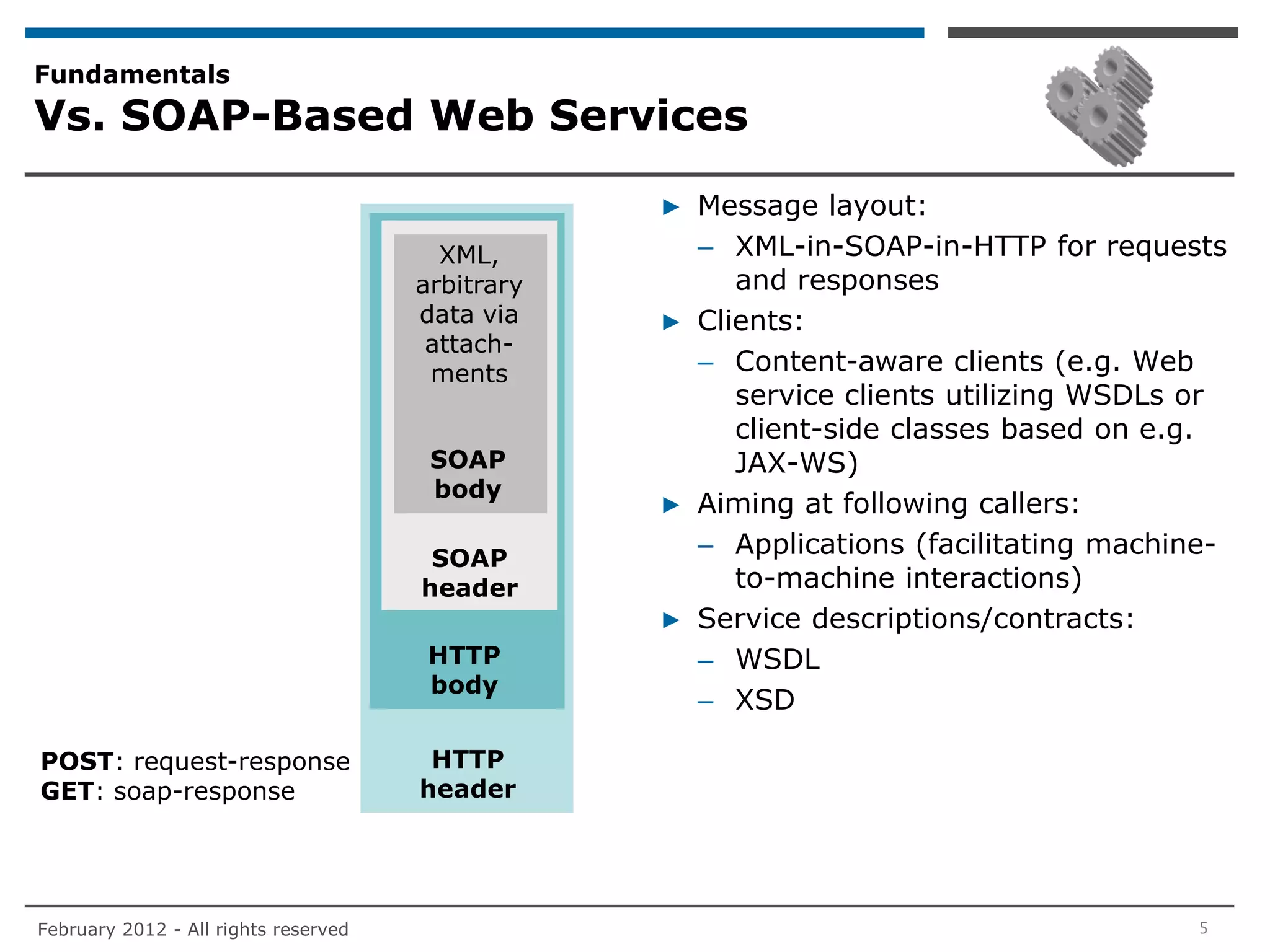
![Answers – Employing IAM
Authorization
▶ Authorization is a local matter of RESTful Web service providers. It does not add
further dependencies between consumers and producers of REST services (unless
specific use cases such as user consent [e.g. OAuth] are to be addressed).
▶ With PEPs (e.g. servlet-filters) that recognize request contents on the HTTP
header level only, access control can be achieved on following granularity:
– For RESTful Web services identifying resource instances in the URL path
• Create operation: requested resource class
o For example, the Group resource class in SCIM
(www.simplecloud.info/specs/draft-scim-core-schema-00.html) identified
by http(s)://hostname:port/Groups allowing to decide e.g. may John
Doe create a group (endpoint and type of operation)
• Read/update/delete operations: requested resource instance
o For example, the Group resource instance with id=01234-56789 in SCIM
identified as http(s)://hostname:port/Groups/01234-56789 allowing
to decide e.g. may John Doe delete this instance of group (endpoint, type
of operation, and instance of resource object)
▶ If further details of actual requests shall be considered in authorization decision
making, PEPs for RESTful Web services need to understand HTTP request bodies.
Such PEPs may reside in the actual business application or the REST stack.
February 2012 - All rights reserved 15](https://image.slidesharecdn.com/doesrestchangethegameforiam-120226145822-phpapp01/75/Does-REST-Change-the-Game-for-IAM-15-2048.jpg)