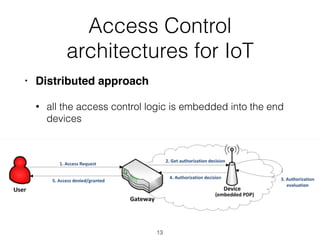
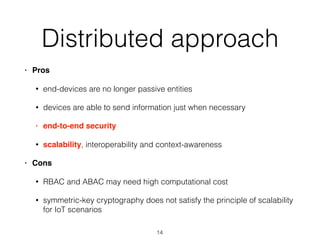
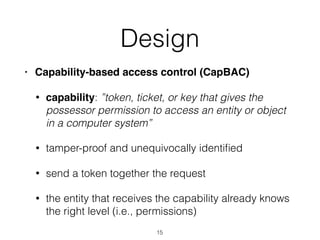
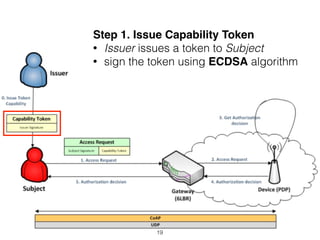
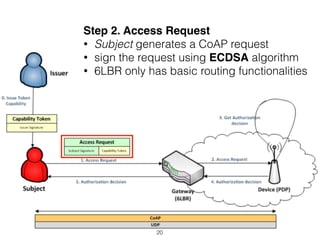
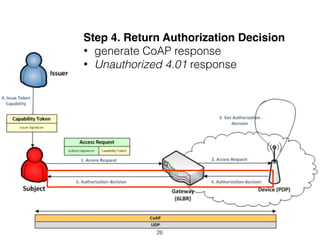
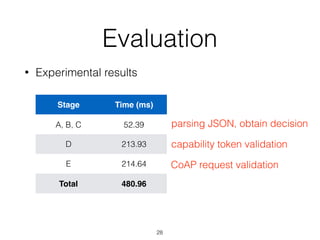
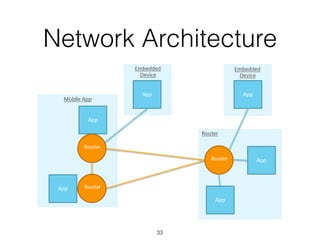
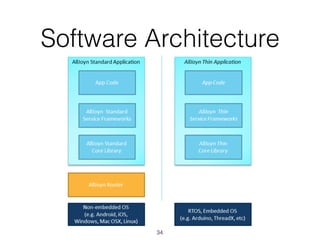
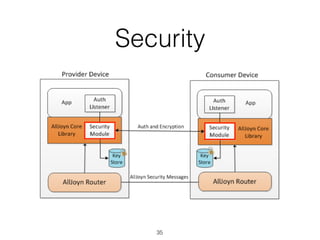
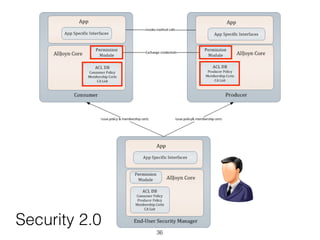
The document discusses distributed capability-based access control (CapBAC) as a security solution for the Internet of Things (IoT), highlighting its benefits in terms of scalability and end-to-end security compared to centralized approaches. It describes the processes involved in CapBAC, including the issuance and validation of capability tokens, and evaluates its implementation using experimental results from a testbed. Additionally, it contrasts CapBAC with centralized solutions like OM2M and AllJoyn, emphasizing the importance of local decision-making for enhanced security.






















![Discussion
• [paper] access rights on token
• flexible but difficult to manage
• private key leakage
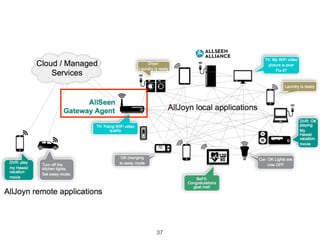
• [AllJoyn] access rights on device
• limitation on constrained device
• easy to manage
• [OM2M] access rights on GSCL/NSCL
• centralized approach
39](https://image.slidesharecdn.com/iotsecurity-170531074858/85/IoT-M2M-Security-40-320.jpg)
![Reference
• Why IoT Security Is So Critical, TechCrunch
• Distributed Capability-based Access Control for the
Internet of Things [2013]
• A decentralized approach for Security and Privacy
challenges in the Internet of Things [2014]
• OM2M, http://www.eclipse.org/om2m/
• AllJoyn, https://allseenalliance.org/](https://image.slidesharecdn.com/iotsecurity-170531074858/85/IoT-M2M-Security-41-320.jpg)
