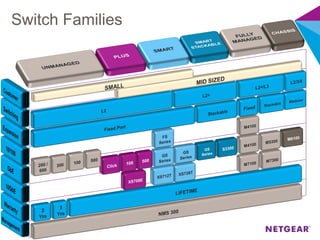
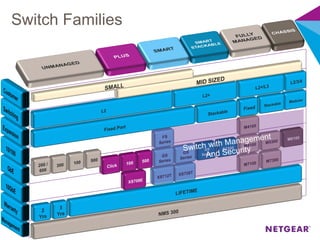
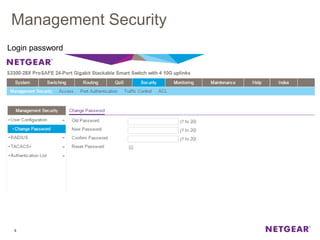
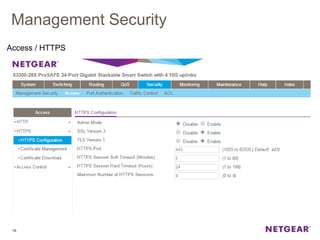
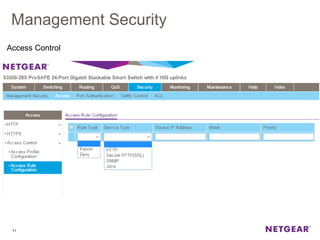
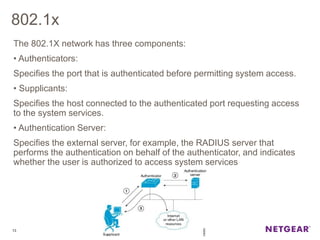
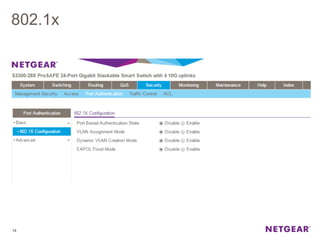
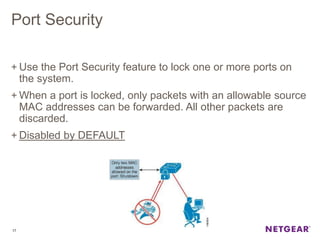
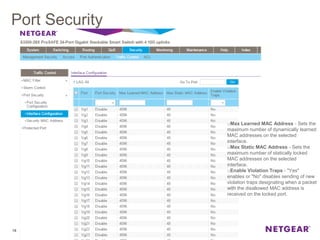
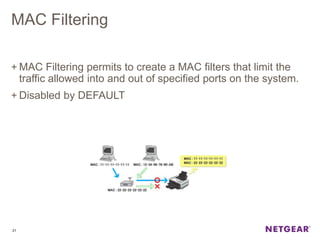
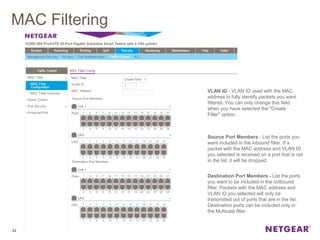
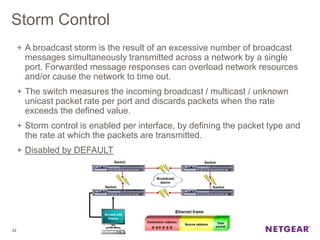
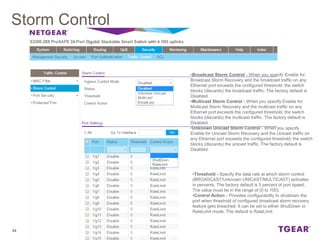
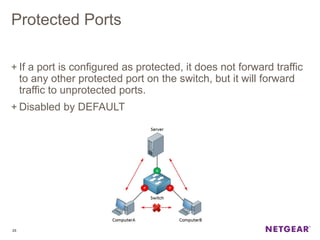
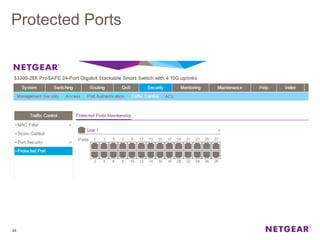
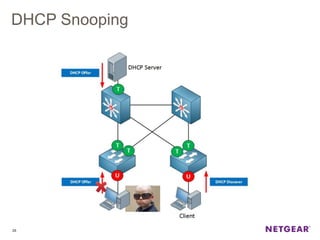
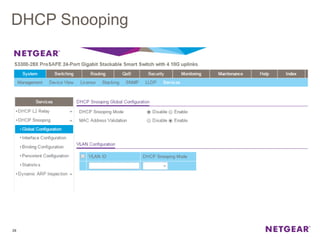
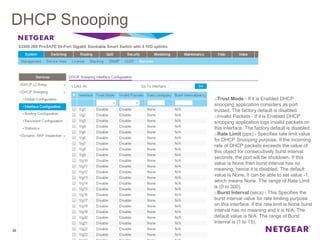
The document provides an overview of the features and functionalities of the Prosafe Switch series, emphasizing its security and traffic control measures. Key topics include management security, port-based authentication (802.1x), port security, mac filtering, storm control, and DHCP snooping, all designed to protect the LAN network. Each feature is detailed regarding its configuration, default settings, and operational guidelines to enhance network security and reliability.