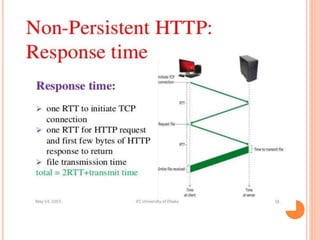
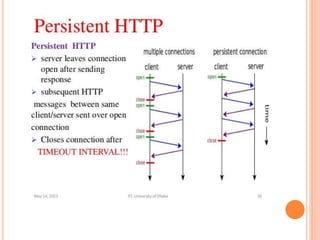
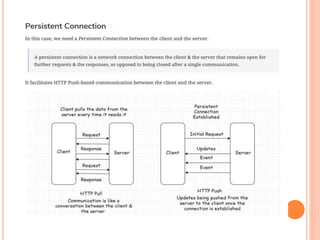
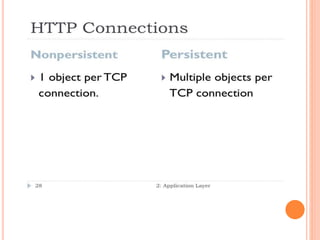
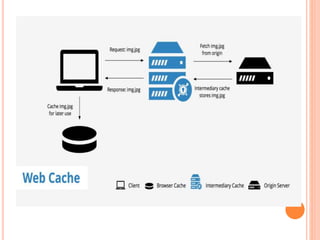
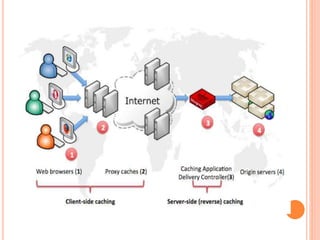
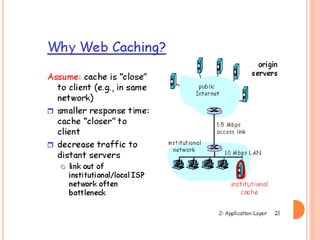
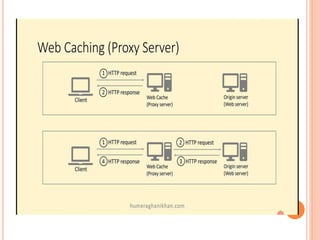
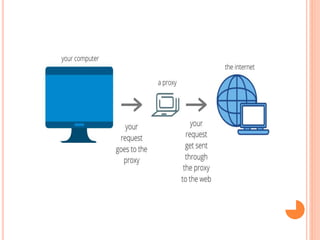
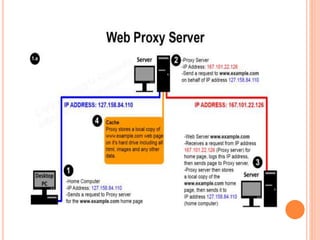
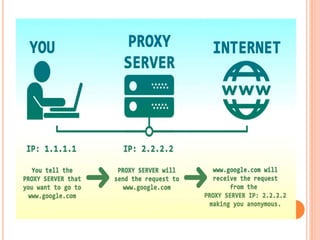
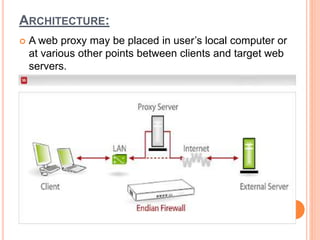
The document discusses web technologies including three-way and four-way handshaking for establishing client-server connections and contrasting non-persistent and persistent HTTP connections. It also covers web caching techniques to improve quality of service, the role of proxy servers in managing traffic, and cache consistency mechanisms for maintaining updated content. Additionally, it addresses the limitations of proxy servers regarding dynamically generated content and frequent updates.