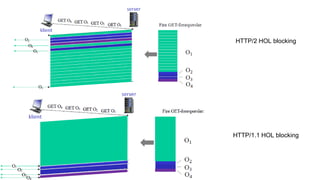
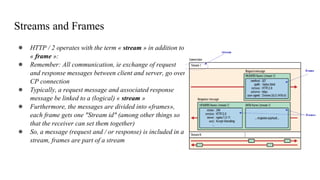
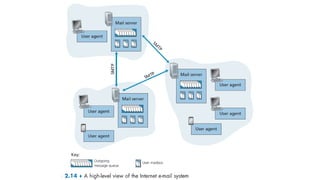
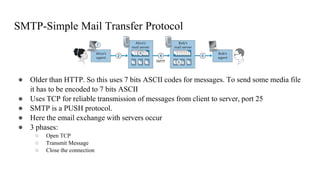
1. The document discusses network application architectures and the HTTP protocol.
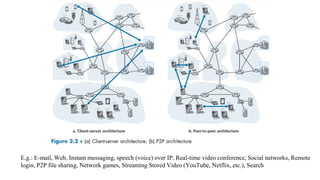
2. It describes two main application architectures - client-server and peer-to-peer - and examples of each.
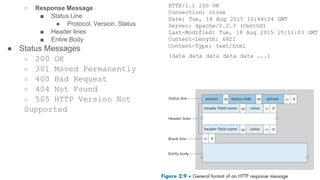
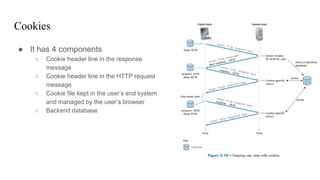
3. The document then provides an in-depth overview of the HTTP protocol, including features like persistent connections, cookies, caching, and new developments like HTTP/2.




![HTTP
● WWW was the first web application which brought internet to use in Public.
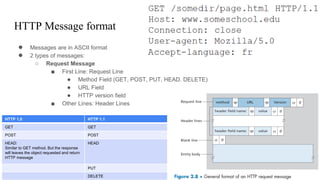
● HTTP is the web’s application layer protocol. [RFC 1945], [RFC 7230] and [RFC 7540].
● HTTP has
○ Client program
○ Server Program
● HTTP defines how Web clients request Web pages from Web servers and how servers transfer Web
pages to clients
● HTTP uses TCP
● HTTP is said to be a stateless protocol. Because it does not contain any information about the client.
(Client request or response)
● Types of connections in HTTP:
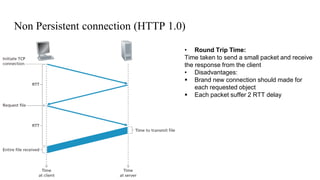
○ Non Persistent connection:
■ Request and Response sends over separate TCP connections
○ Persistent Connection
■ Request and Response sent over same TCP connection](https://image.slidesharecdn.com/applicationlayer-210905104410/85/Application-layer-8-320.jpg)